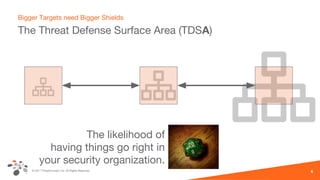
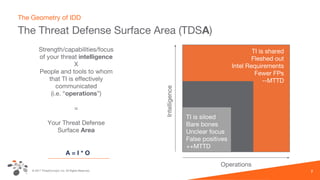
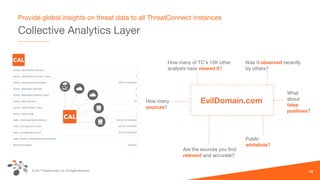
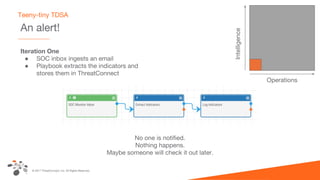
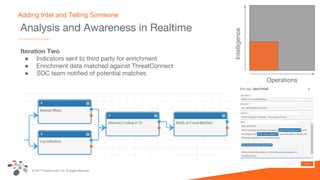
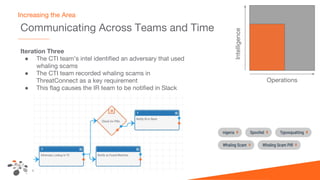
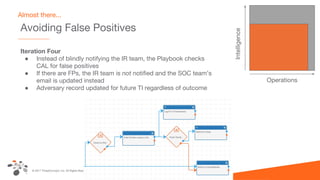
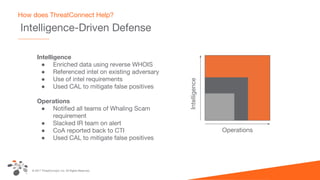
The document discusses intelligence-driven defense (IDD) and how ThreatConnect supports it. IDD means increasing a team's threat defense surface area by sharing threat intelligence (TI) across security operations and analysts. ThreatConnect provides automated playbooks, a collective analytics layer, and tools to connect intelligence and operations teams. This allows indicators from alerts to be enriched, potential matches to be flagged for analysts based on known adversaries, and feedback loops to update intelligence and close investigation loops.