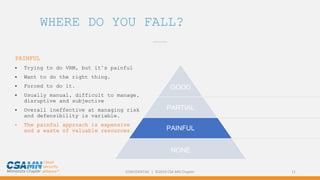
The document outlines effective approaches to managing third-party vendor risk, emphasizing the necessity of conducting vendor risk assessments before signing cloud hosting contracts. It presents statistics highlighting the prevalence of security breaches caused by vendors and illustrates various methods for evaluating and categorizing vendor risks. The key takeaway is to simplify the risk management process through standardization and defensibility, ensuring thorough assessment and contract evaluation to mitigate potential risks.