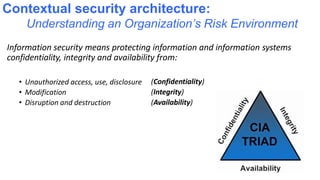
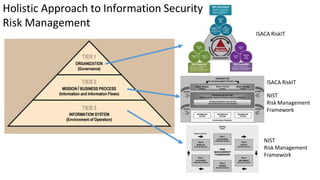
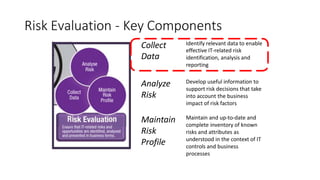
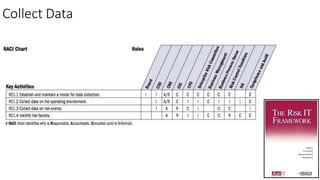
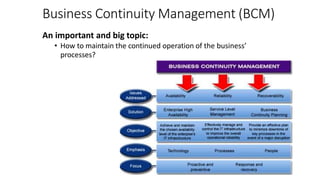
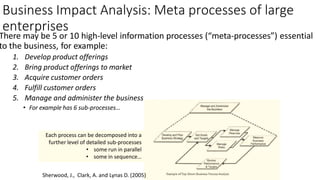
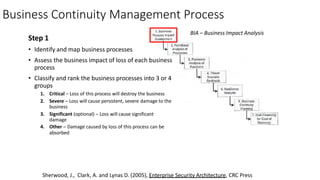
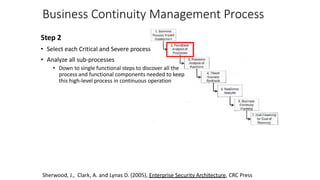
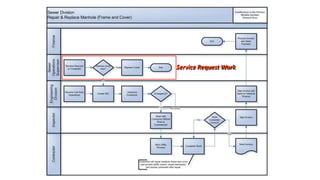
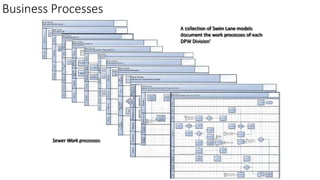
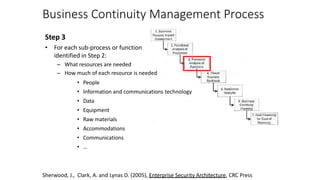
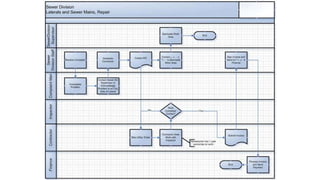
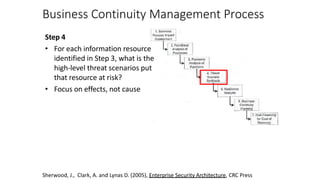
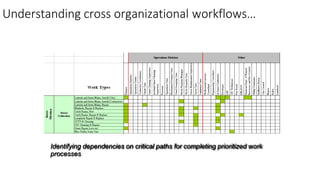
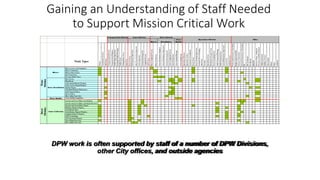
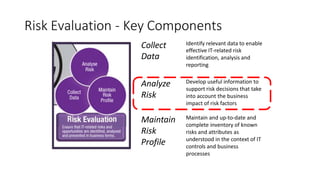
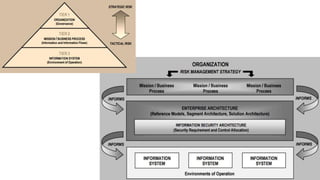
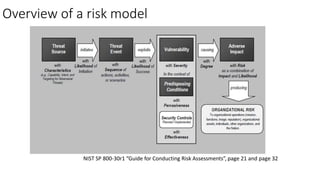
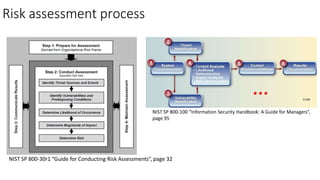
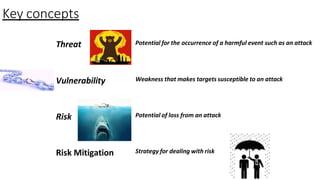
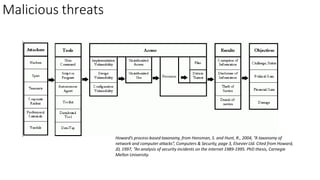
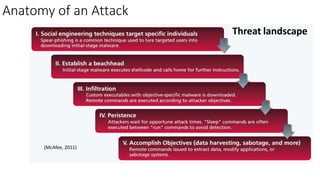
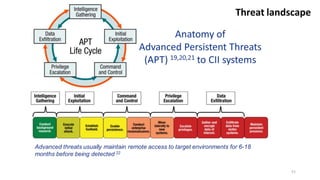
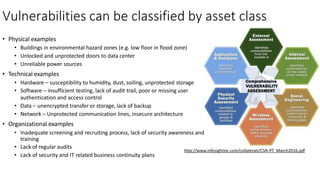
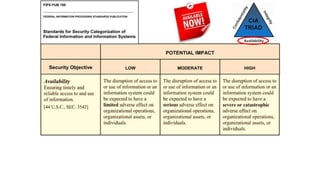
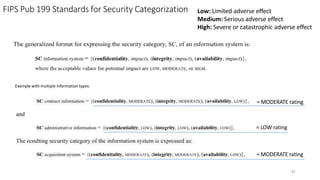
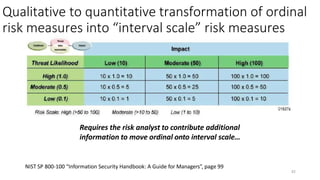
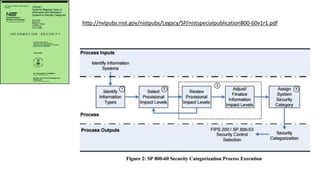
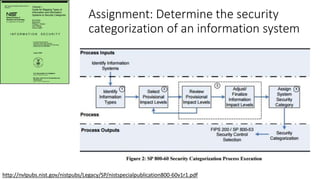
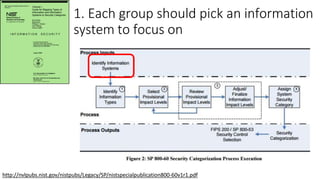
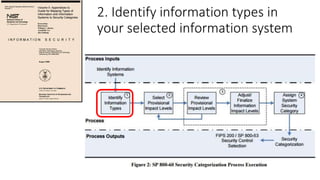
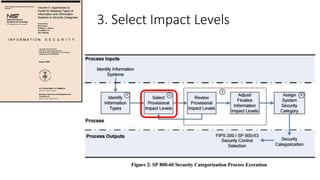
Understanding an organization's risk environment involves taking a holistic approach to information security risk management. This includes identifying the organization's business processes, resources, threats, vulnerabilities and risks through techniques such as business impact analysis and risk evaluation. Risk evaluation aims to identify risk scenarios and their potential business impacts by collecting relevant data, analyzing risks while considering business impacts, and maintaining an up-to-date risk profile. Understanding an organization's business processes, dependencies, resources and the risks that could disrupt them are key to developing and implementing effective security and business continuity strategies.