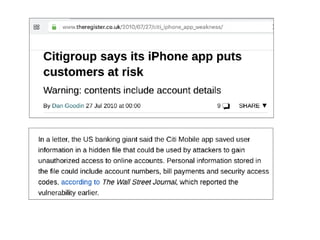
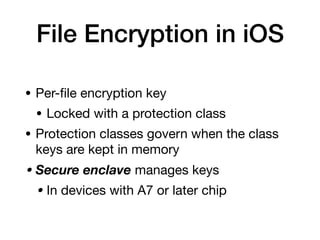
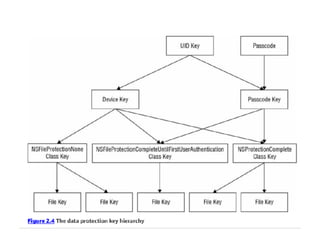
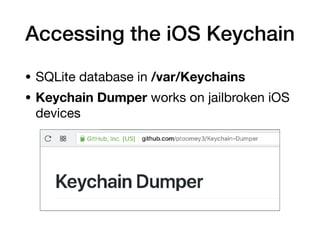
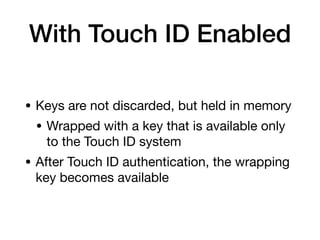
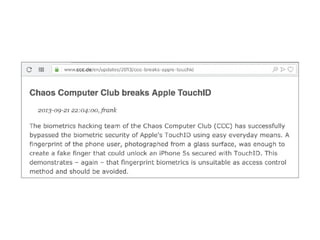
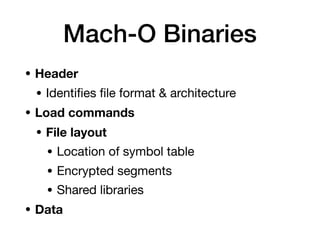
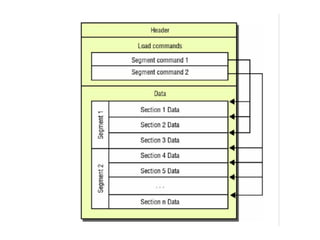
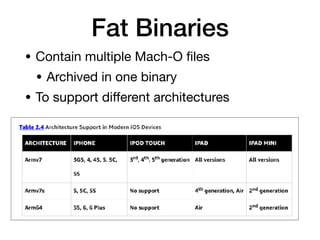
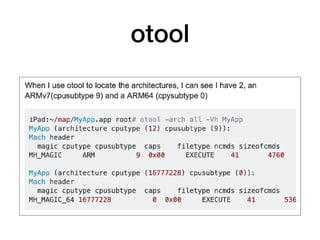
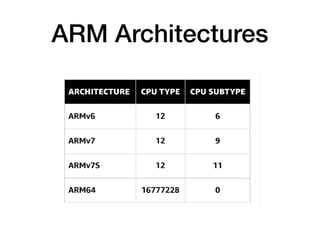
The document provides an overview of security features in iOS apps, covering the Data Protection API, keychain protection classes, and Touch ID mechanisms. It also discusses reverse engineering of iOS binaries, including the structure of Mach-O files, security features like position-independent executable, and techniques for decrypting app store binaries. Additionally, tools for inspecting and analyzing decrypted applications are mentioned.