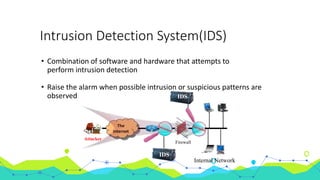
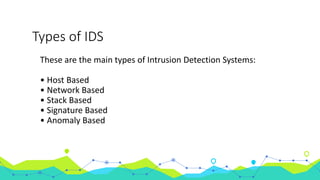
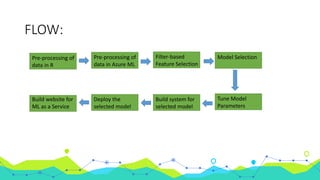
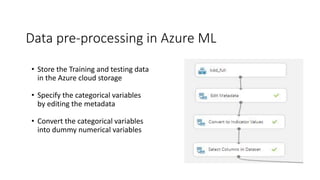
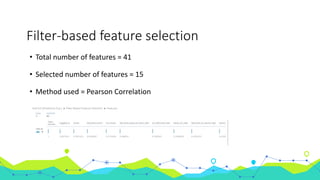
This document discusses using machine learning for intrusion detection. It begins by explaining what an intrusion detection system (IDS) is and why they are needed. It then describes the main types of IDS, including host-based, network-based, signature-based, and anomaly-based. It introduces the KDD Cup 99 dataset, which is used to train and evaluate machine learning models for intrusion detection. The document outlines the process used, including pre-processing the data in R and Azure ML, feature selection, model selection and parameter tuning, and building and deploying a boosted decision tree model as a web service for intrusion detection.