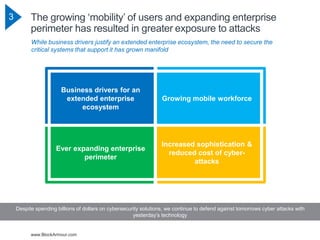
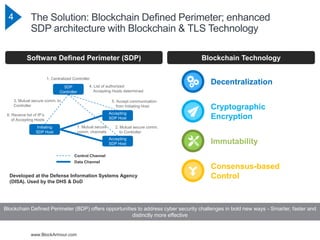
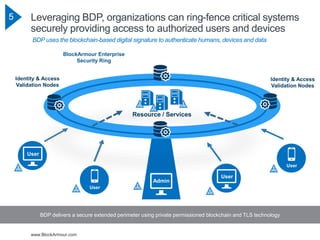
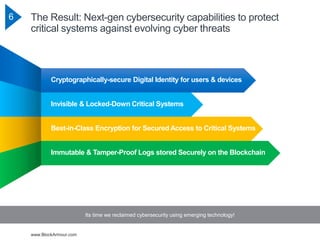
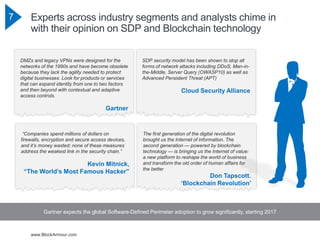
The document discusses the rising cybersecurity challenges amidst increasing incidents and evolving attack strategies, emphasizing the inadequacy of existing solutions. It introduces the Blockchain Defined Perimeter (BDP) as a transformative approach that leverages blockchain technology for securing critical systems and enhancing cybersecurity measures. BDP offers benefits such as cryptographic security, immutable logging, and tailored access control, positioning itself as a modern solution to safeguard against sophisticated cyber threats.