1. The document discusses 10 reasons why organizations may be ready for a secure managed cloud service, including wanting built-in security capabilities, customized service, and a proactive partner.
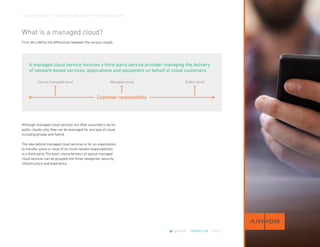
2. It describes what a managed cloud service entails and differentiates secure managed cloud services from typical cloud services. Secure managed cloud services take on more security responsibilities.
3. The best secure managed cloud services provide benefits like 24/7 monitoring and maintenance of cloud workloads, reduced costs, faster deployment times, unique capabilities, lower risk, and assistance with compliance requirements.