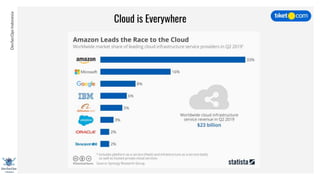
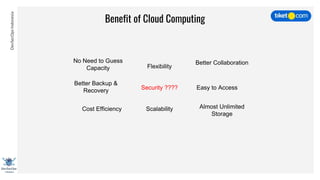
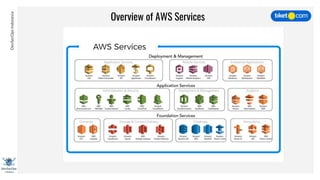
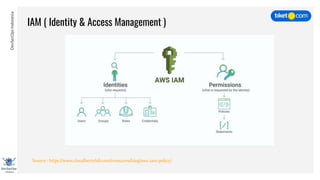
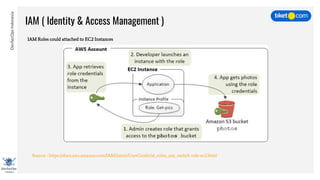
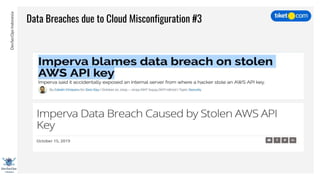
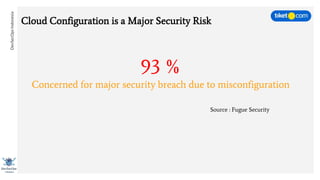
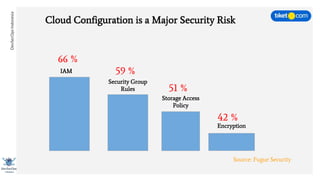
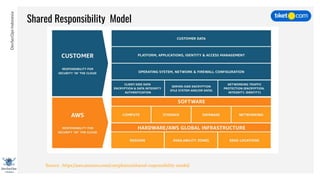
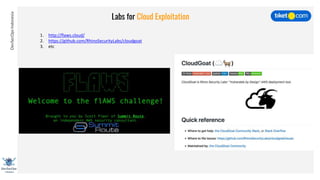
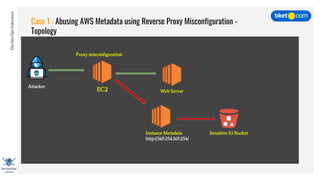
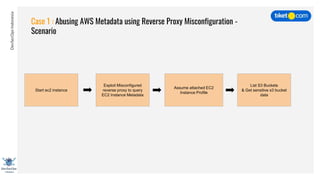
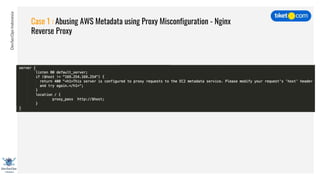
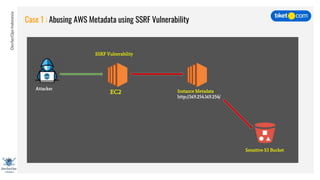
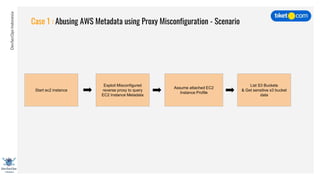
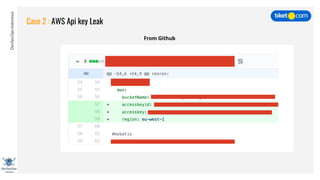
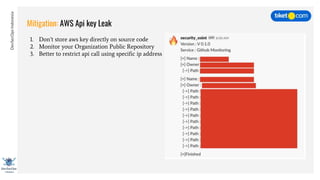
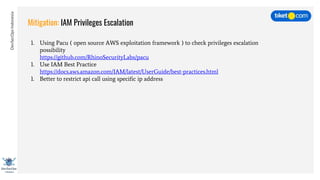
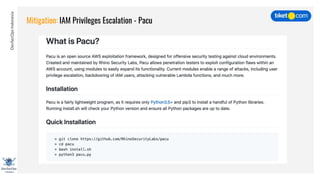
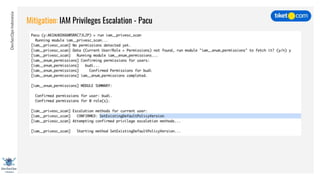
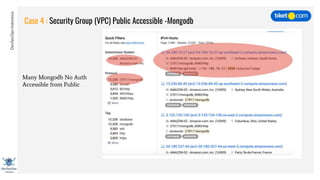
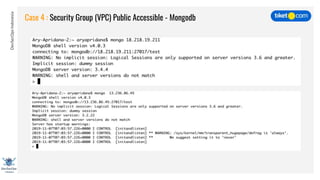
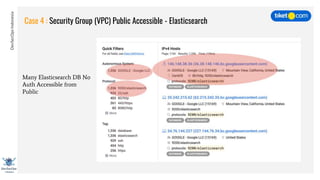
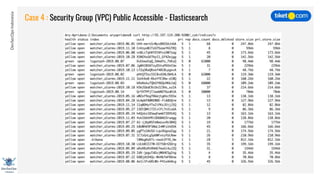
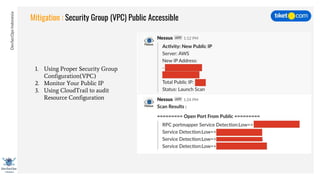
This document discusses cloud vulnerabilities and threats. It begins with an introduction to cloud computing benefits and AWS services. It then discusses common misconfigurations that can lead to data breaches, including issues with IAM, security groups, and storage access policies. Specific cases examined include exploiting metadata APIs, leaking API keys, and escalating IAM privileges. The document concludes with recommendations for securing services, restricting access, monitoring configurations, and using tools like Security Monkey and ScoutSuite to automate security checks.