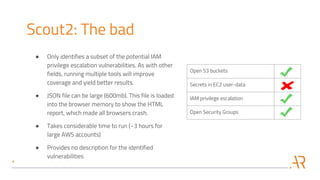
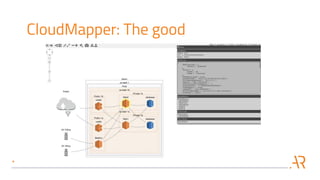
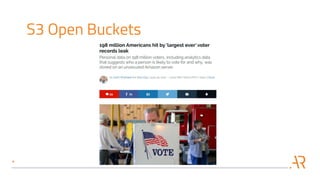
This document discusses performing automated security assessments of AWS cloud environments. It outlines some of the most common vulnerabilities found in AWS accounts, such as open S3 buckets, secrets in EC2 user-data, IAM privilege escalation, and open security groups. The document then evaluates several open source tools for identifying these vulnerabilities, including Scout2, Prowler, Pacu, and CloudMapper, noting their strengths, weaknesses, and limitations. It stresses that while these tools provide a starting point, expert review is still required due to incomplete vulnerability coverage and potential for incorrect findings. The document concludes by urging readers to perform periodic security assessments and implement basic security practices like storing backups in separate accounts and using Trusted Advisor.

















![IAM privilege escalation
AWS users, roles and groups have
associated IAM policies which
describe which AWS APIs can be
consumed.
The example policy allows the
associated principal to start and stop
instances which are tagged with his
username.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:StartInstances",
"ec2:StopInstances"
],
"Resource": "arn:aws:ec2:*:*:instance/*",
"Condition": {
"StringEquals": {
"ec2:ResourceTag/Owner": "${aws:username}"
}
}
}
]
}](https://image.slidesharecdn.com/automatedsecurityanalysisofawscloudsv1-191020032602/85/Automated-security-analysis-of-aws-clouds-v1-0-20-320.jpg)
![IAM privilege escalation
An attacker with access to AWS
account credentials with permissions
to run the iam:PassRole and
ec2:RunInstances actions can create a
new EC2 instance and associate an
arbitrary role with high privileges to it.
The attacker then connects to the new
instance using SSH and requests the
AWS access keys from the EC2
instance metadata.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"iam:PassRole",
"ec2:RunInstances"
],
"Resource": "*"
}
]
}](https://image.slidesharecdn.com/automatedsecurityanalysisofawscloudsv1-191020032602/85/Automated-security-analysis-of-aws-clouds-v1-0-21-320.jpg)