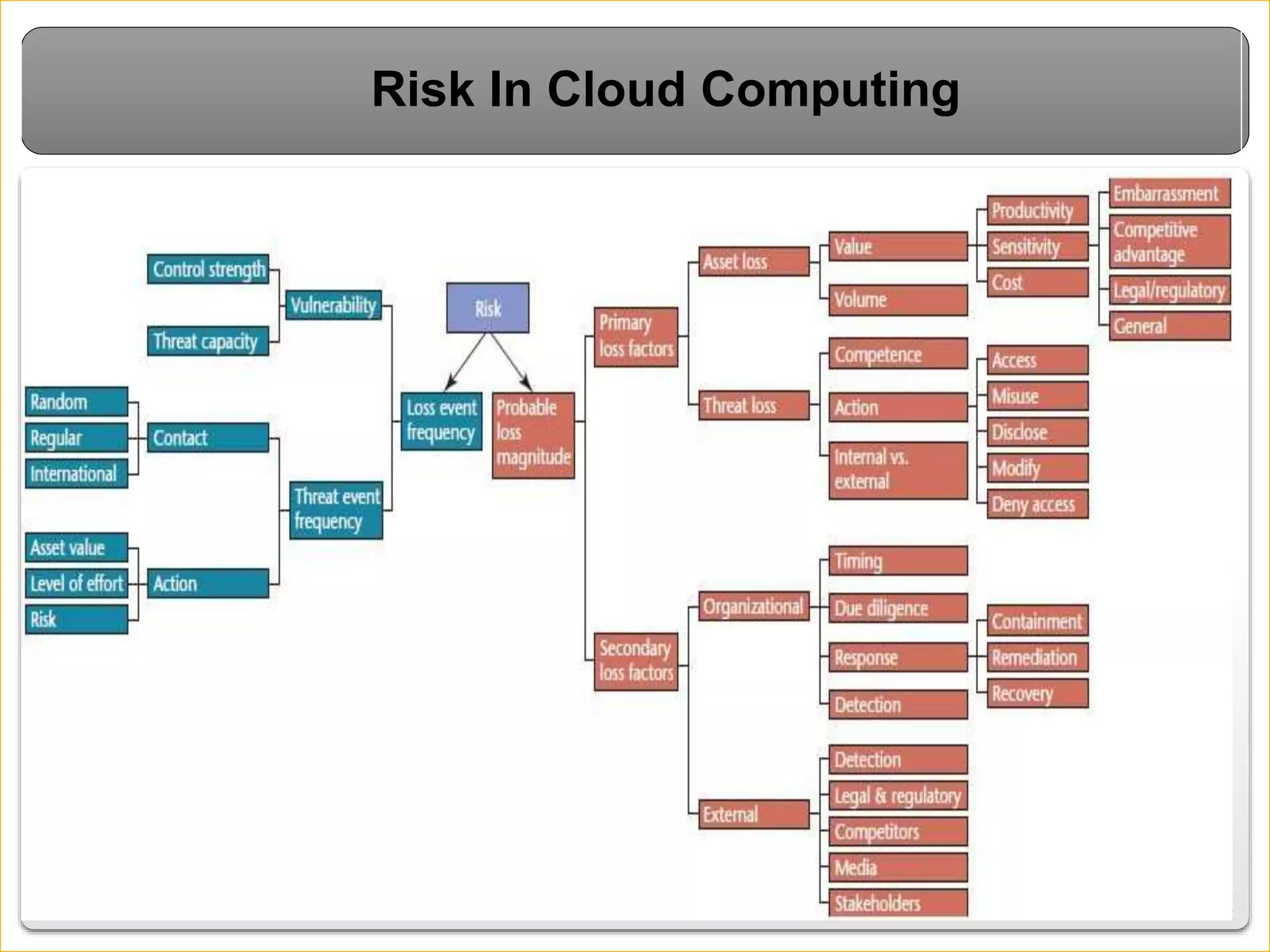
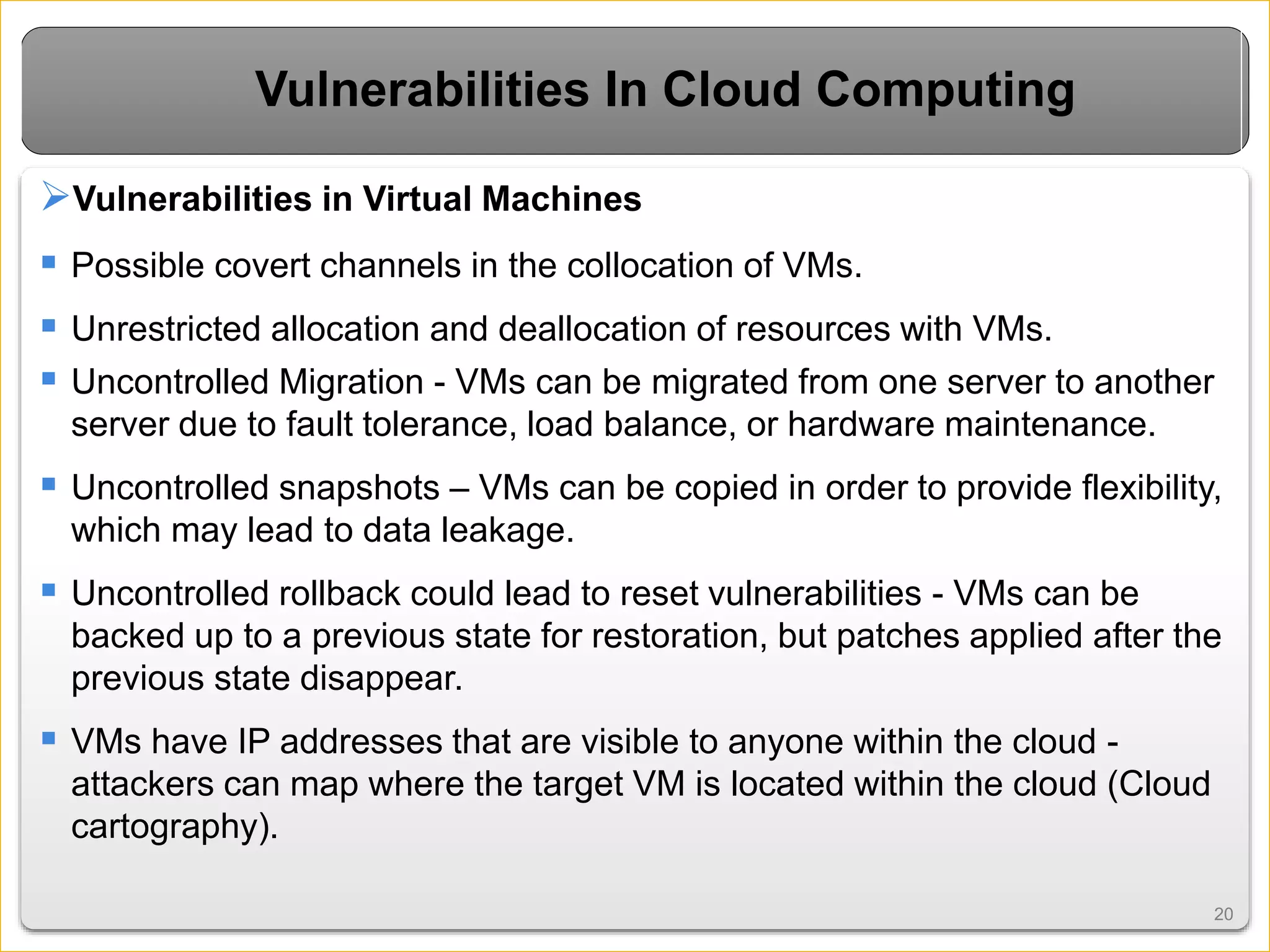
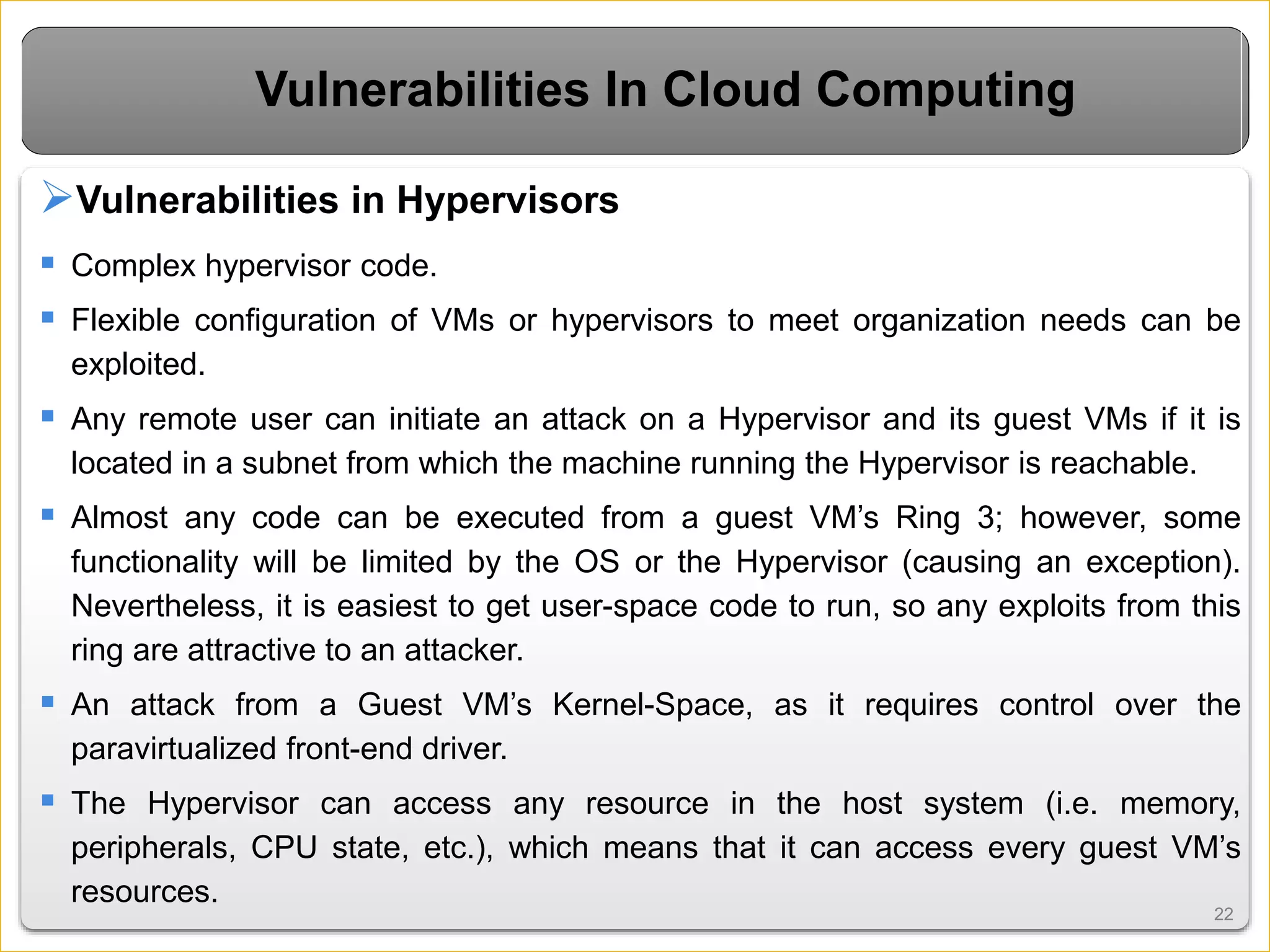
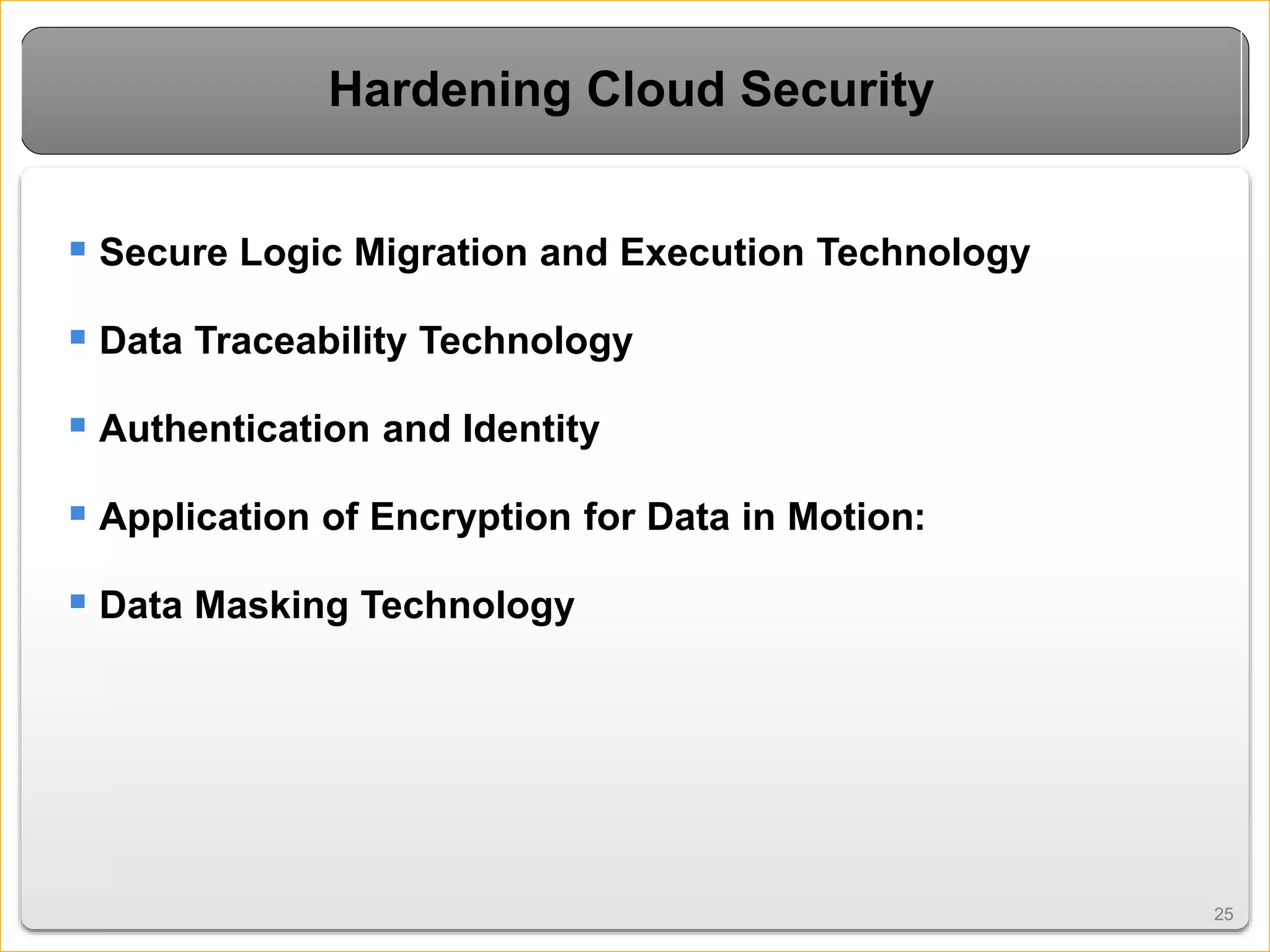
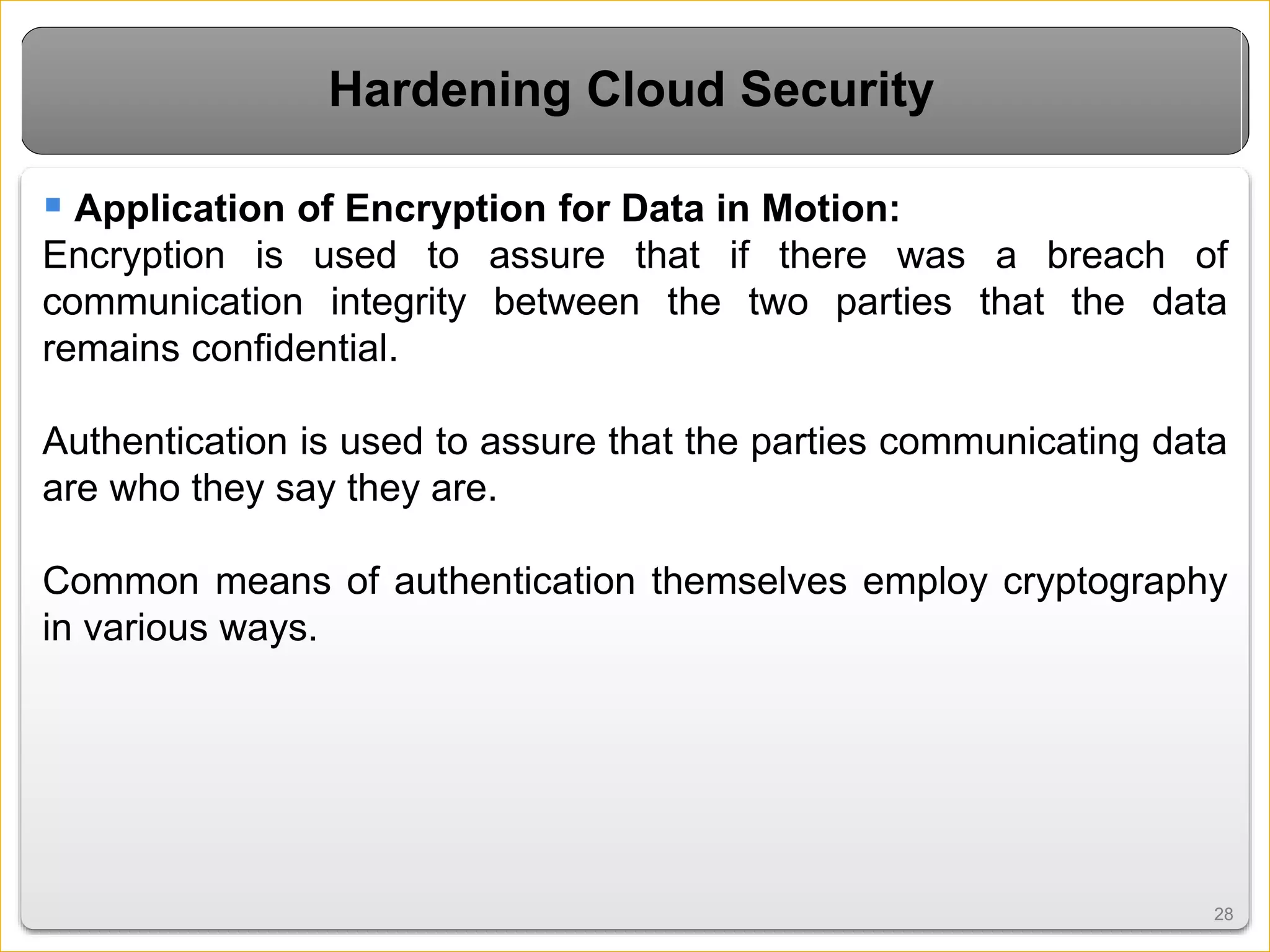
Cloud computing introduces new risks that must be addressed. It relies on sharing resources over the internet rather than local servers. This introduces vulnerabilities like insecure APIs, data leaks when data is shared on virtual machines, and issues with the virtual networks. However, cloud security can be improved through measures like encryption, access control, data tracing, and masking sensitive data. Overall cloud computing improves accessibility and scalability but also requires secure virtualization and clear responsibility over data protection.