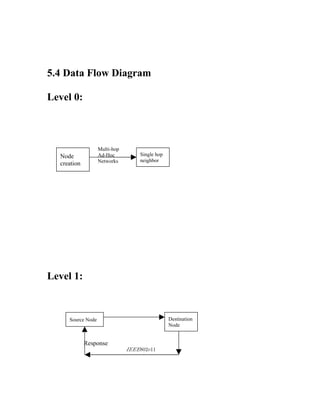
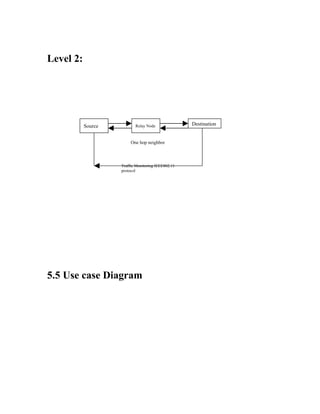
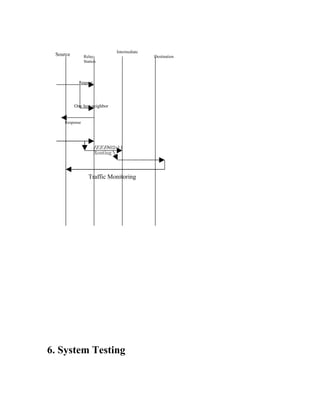
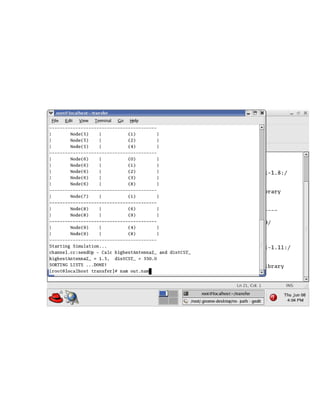
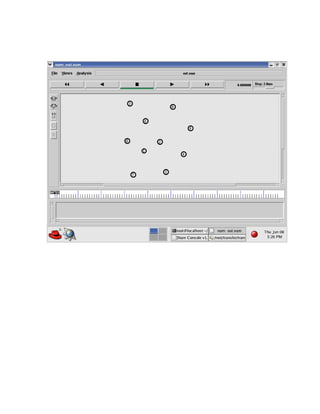
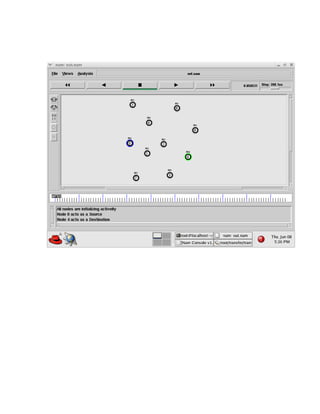
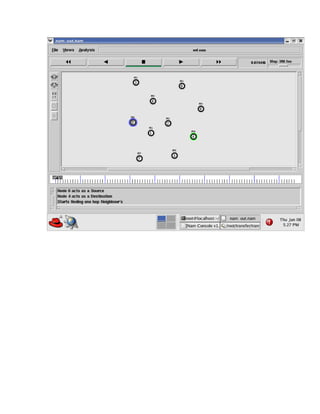
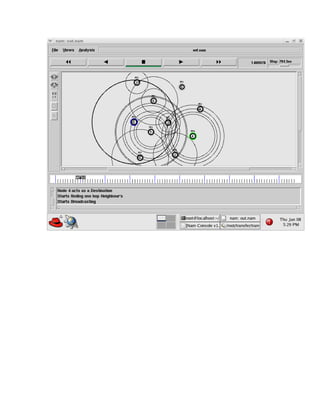
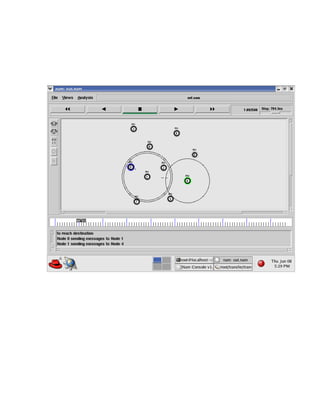
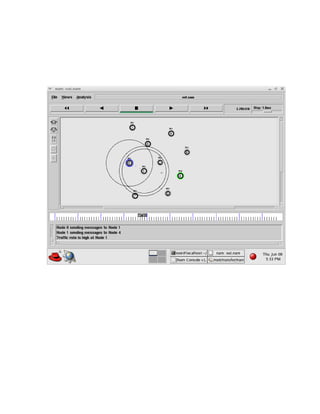
The document discusses securing query processing in cloud computing environments. It identifies three key requirements for secure query processing: 1) authenticating users and machines, 2) securing data transfer across machines, and 3) ensuring integrity of query results. The document also analyzes existing and proposed systems for wireless multi-hop networks, including analyzing performance under different conditions.

































![set ns_ [new Simulator]
set topo [new Topography]
set tracefd [open out.tr w]
set namtrace [open out.nam w]
$ns_ trace-all $tracefd
$ns_ namtrace-all-wireless $namtrace $val(x) $val(y)
$topo load_flatgrid $val(x) $val(y)
set god_ [create-god $val(nn)]
$ns_ node-config -adhocRouting AODV
-llType $val(ll)
-macType $val(mac)
-ifqType $val(ifq)
-ifqLen $val(ifqlen)
-antType $val(ant)](https://image.slidesharecdn.com/clouddatamanagement-120715135113-phpapp01/85/Cloud-data-management-37-320.jpg)
![-propType $val(prop)
-phyType $val(netif)
-channelType $val(chan)
-topoInstance $topo
-agentTrace ON
-routerTrace ON
-macTrace ON
for {set i 0} {$i < $val(nn) } {incr i} {
set node_($i) [$ns_ node]
}
set X1(0) 130.32
set X1(1) 235.55
set X1(2) 336.499
set X1(3) 147
set X1(4) 488.23
set X1(5) 374.881
set X1(6) 246.766
set X1(7) 167.161
set X1(8) 419.979
set X1(9) 532.0
set Y1(0) 539.172](https://image.slidesharecdn.com/clouddatamanagement-120715135113-phpapp01/85/Cloud-data-management-38-320.jpg)

![}
for {set i k} {$i < $val(nn) } {incr i} {
$ns_ at $val(stop).0 "$node_($i) reset";
}
puts "-----------------------------------------------"
puts "Routing table"
puts "-----------------------------------------"
puts "|Node | one hop neighbour|"
puts "-----------------------------------------"
for {set i 0} {$i < $val(nn) } {incr i} {
for {set j 0} {$j < $val(nn) } {incr j} {
set a [ expr $X1($j)-$X1($i)]
set b [ expr $a*$a]
set c [ expr $Y1($j)-$Y1($i)]
set d [ expr $c*$c]
set e [ expr $b+$d]](https://image.slidesharecdn.com/clouddatamanagement-120715135113-phpapp01/85/Cloud-data-management-40-320.jpg)
![set f 0.5
set g [expr pow($e,$f)]
if {$g <= 200 && $i != $j} {
puts "| Node($i) | ($j) |"
}
}
puts "-----------------------------------------"
}
set udp_(0) [new Agent/UDP]
$ns_ attach-agent $node_(0) $udp_(0)
set null1_(0) [new Agent/Null]
$ns_ attach-agent $node_(4) $null1_(0)
set cbr1_(0) [new Application/Traffic/CBR]
$cbr1_(0) set packetSize_ 1000
$cbr1_(0) set interval_ 0.01
$cbr1_(0) set random_ 1
$cbr1_(0) set maxpkts_ 1000
$cbr1_(0) attach-agent $udp_(0)](https://image.slidesharecdn.com/clouddatamanagement-120715135113-phpapp01/85/Cloud-data-management-41-320.jpg)


![REFERENCES
[1] Y. D. Barowski and S. Biaz, “The performance analysis of ieee-802.11
under unsaturated traffic conditions,” Tech. Rep. CSSE04-09, Auburn
University, Aug. 2004.
[2] V. Bharghavan, A. Demers, S. Shenker, and L. Zhang, “MACAW: A
media access protocol for wireless LANs,” in ACM SIGCOMM, London,
U.K, pp. 212–225, Oct. 1994.
[3] G. Bianchi, “Performance analysis of the IEEE802.11 distributed
coordination function,” IEEE Journal in Selected Areas: Communication,
vol. 18, pp. 535–547, March 2000.
[4] L. Bononi, M. Conti, and L. Donatiello, “A distributed mechanism for
power saving in IEEE 802.11 wireless lans,” Mobile Networks and
Applications, vol. 6, no. 3, pp. 211–222, 2001.
[5] F. Cali, M. Conti, and Gregori, “IEEE802.11 wireless lan: Capacity
analysis and protocol enhancement,” in INFOCOM ’98 Seventeenth Annual
Joint Conference of the IEEE Computer and Communications Societies.
Proceedings. IEEE, 1998.](https://image.slidesharecdn.com/clouddatamanagement-120715135113-phpapp01/85/Cloud-data-management-52-320.jpg)
![[6] M. M. Carvalho and J. J. Garcia-Luna-Aceves, “Delay analysis of the
IEEE802.11 in single-hop networks,” in 11th IEEE International Conference
on Network Protocols (ICNP’03), Atlanta, Georgia, USA, Nov. 2003.
[7] H. S. Chhaya and S. Gupta, “Performance modeling of asynchronous
data transfer methods of IEEE802.11 mac protocol,” Wirel. Netw., vol. 3,
no. 3, pp. 217–234, 1997.
[8] D. S. J. De Couto, D. Aguayo, B. A. Chambers, and R. Morris,
“Performance of multihop wireless networks: Shortest path is not enough,”
in Proceedings of the First Workshop on Hot Topics in Networks (HotNets-
I), (Princeton, New Jersey), ACM SIGCOMM, October 2002.
[9] L. M. Feeney and M. Nilsson, “Investigating the energy consumption
of a wireless network interface in an ad hoc networking environment,” in
IEEE INFOCOM, Anchorage, AK, USA, 2001.
[10] L. Huang and T.-H. Lai, “On the scalability of IEEE802.11 ad hoc
networks,” in Proceedings of the 3rd ACM international symposium on
Mobile ad hoc networking & computing, pp. 173–182, ACM Press, 2002](https://image.slidesharecdn.com/clouddatamanagement-120715135113-phpapp01/85/Cloud-data-management-53-320.jpg)