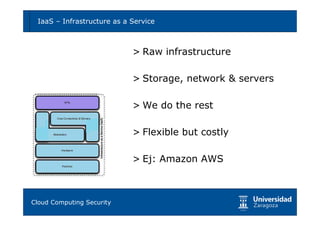
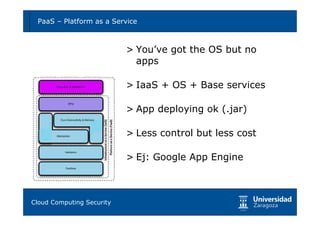
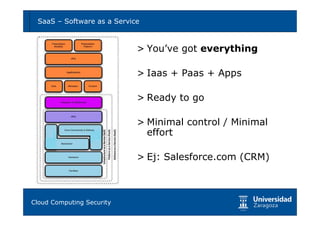
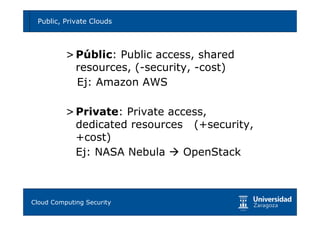
Cloud computing provides opportunities for scalability, availability, and performance but also poses risks if not implemented securely. Key risks include vendor lock-in, lack of governance and control, non-compliance, and various technical risks around isolation faults, data leaks, network attacks, and provider compromises. Migrating to the cloud requires carefully analyzing requirements, evaluating cloud models and providers, defining security controls, and having business continuity plans to mitigate risks. With proper planning and risk mitigation, cloud computing can be implemented securely.



![“Cloud computing is a model for
enabling ubiquitous, convenient,
on-demand network access to a
shared pool of configurable
computing resources (e.g.,
networks, servers, storage,
applications, and services) that can
be rapidly provisioned and
released with minimal management
effort or service provider
interaction”
[*First & last boring slide. Promise]](https://image.slidesharecdn.com/cloudcomputingsecurity-120424153916-phpapp02/85/Cloud-computing-security-5-320.jpg)