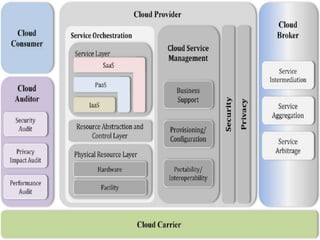
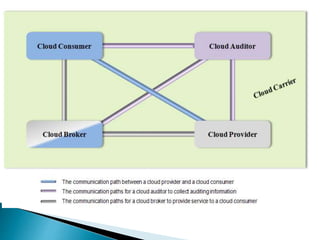
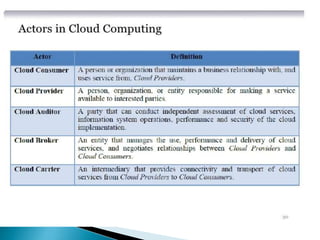
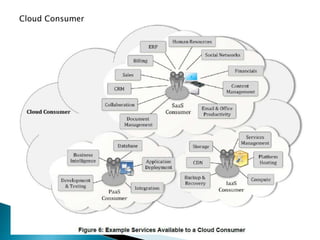
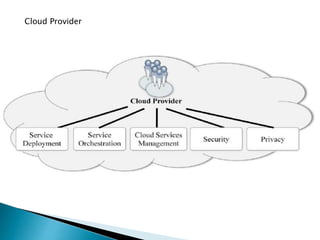
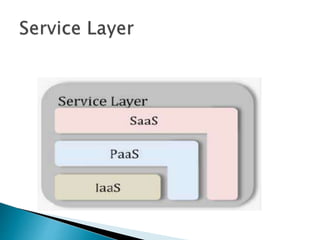
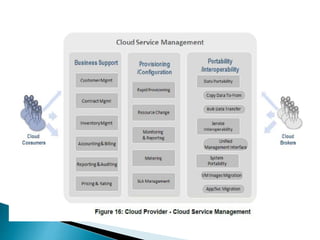
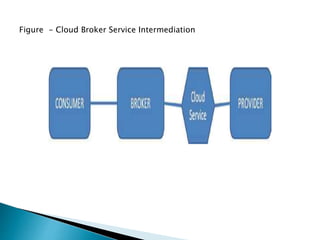
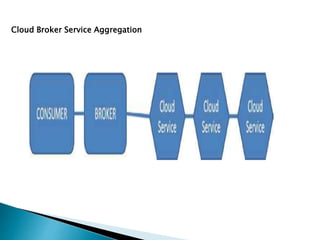
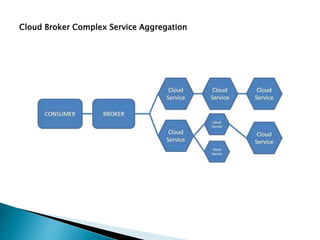
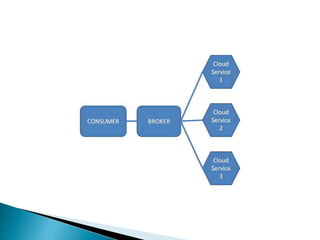
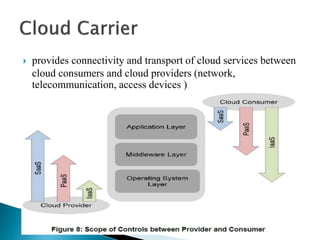
The document outlines the key aspects of cloud service models (SaaS, PaaS, IaaS), focusing on deployment methods, service orchestration, and the interaction between cloud providers and consumers. It emphasizes the importance of service management, security, privacy, and the roles of cloud brokers and auditors in delivering and evaluating cloud services. Additionally, it discusses the need for interoperability, data portability, and effective customer relationship management in cloud environments.