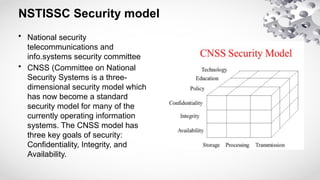
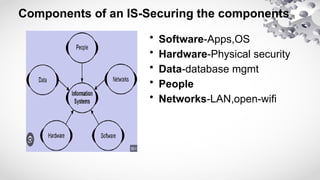
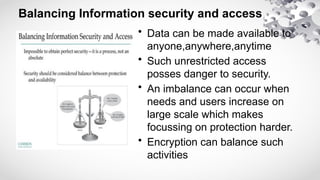
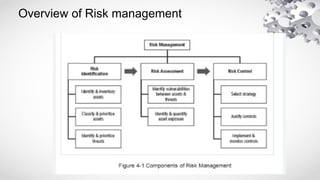
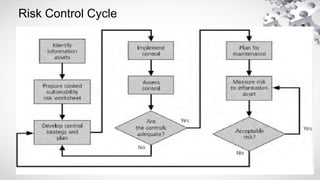
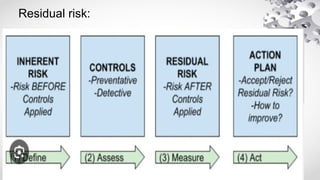
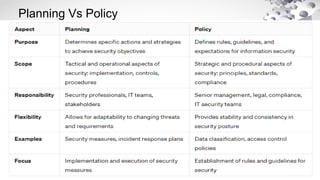
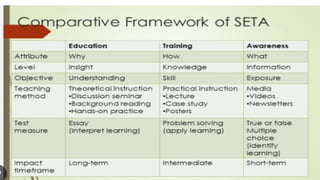
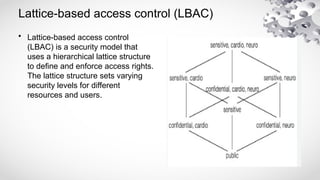
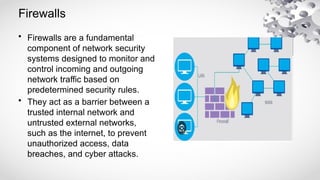
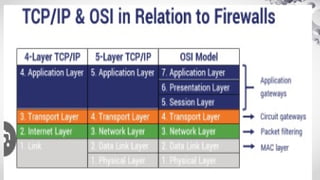
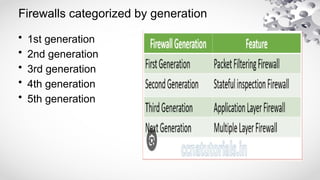
The document provides an extensive overview of information security, detailing its critical components including the CIA triangle of confidentiality, integrity, and availability. It also covers the historical evolution of information security, the need for legal and ethical considerations, risk management strategies, and the importance of a structured policy and planning framework for effective security measures. Furthermore, it discusses various access control methods and the security architecture necessary for safeguarding organizational assets against potential threats.