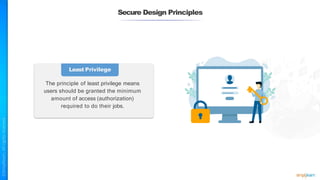
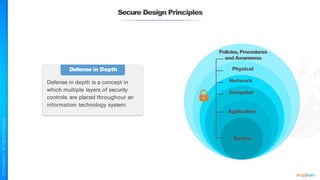
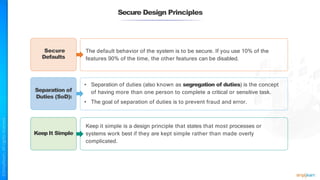
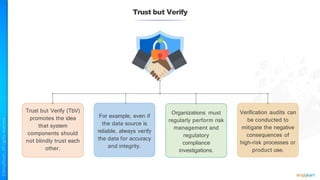
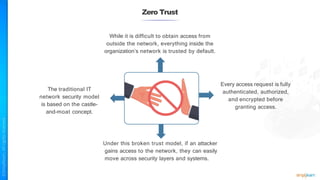
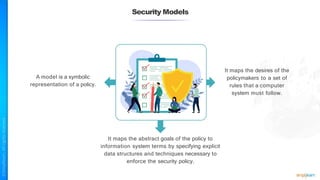
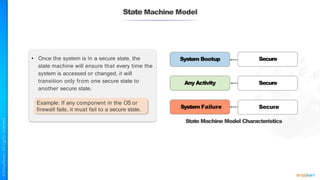
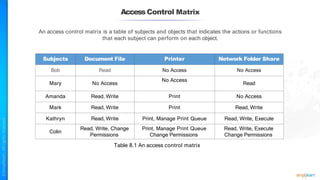
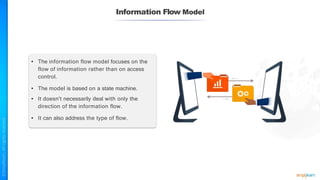
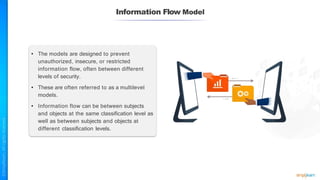
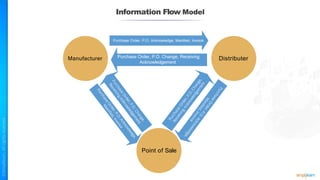
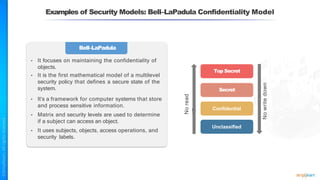
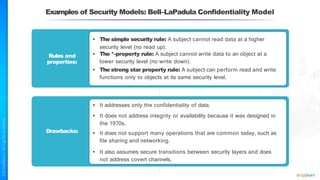
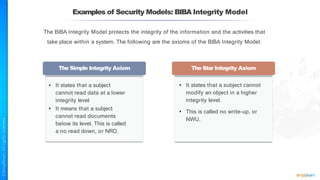
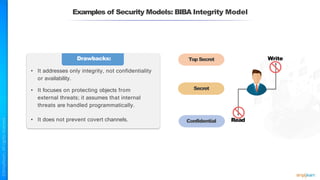
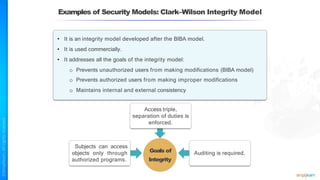
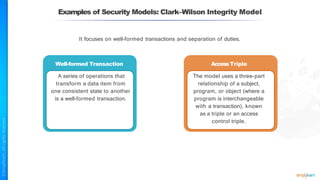
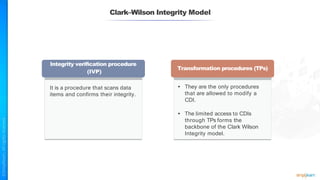
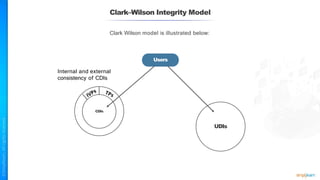
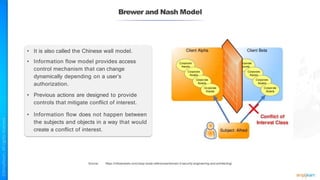
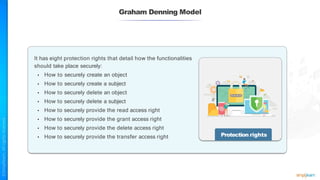
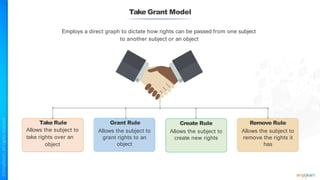
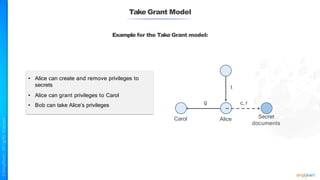
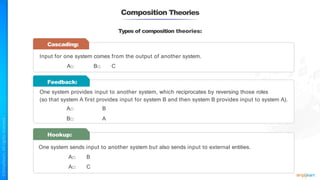
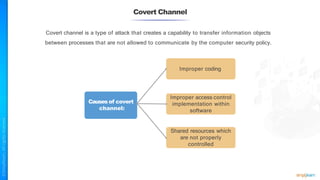
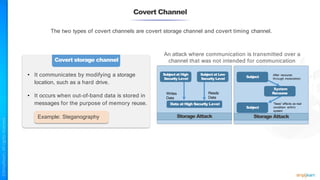
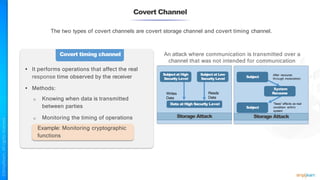
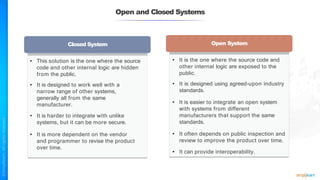
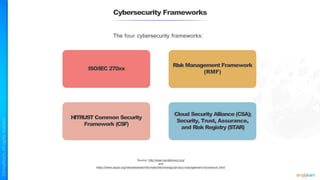
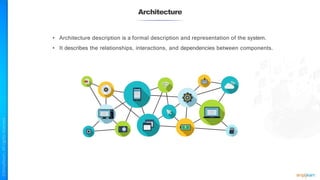
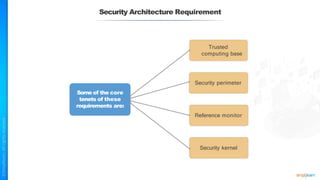
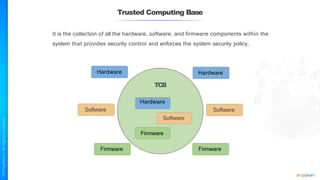
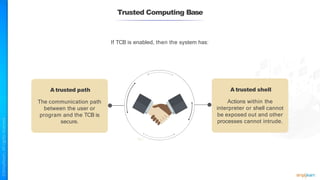
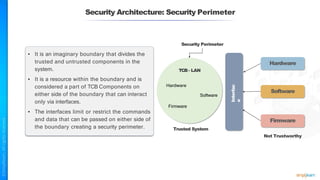
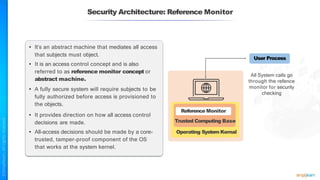
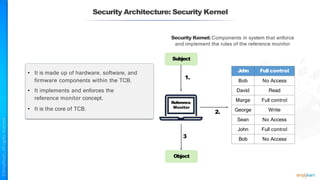
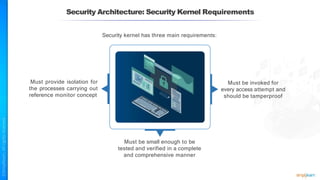
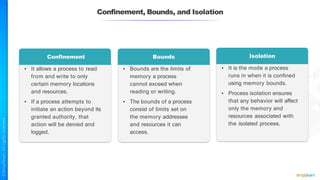
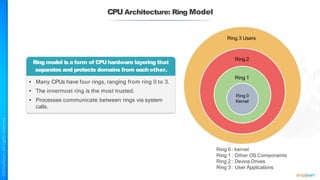
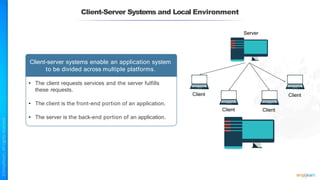
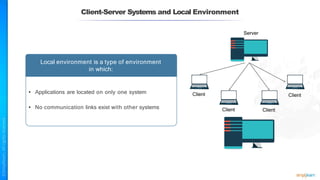
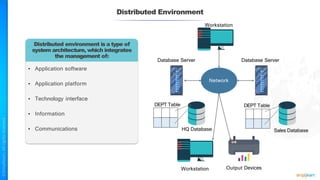
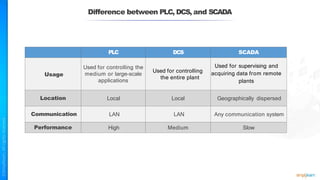
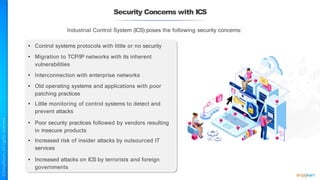
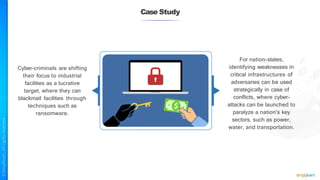
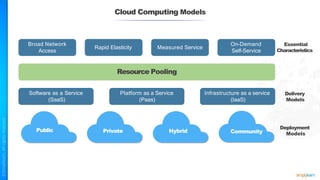
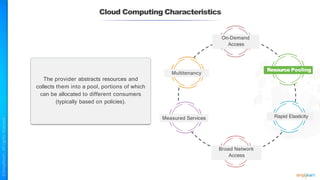
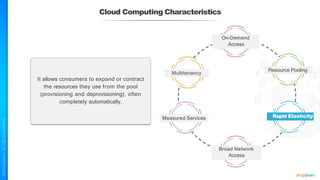
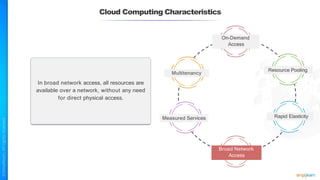
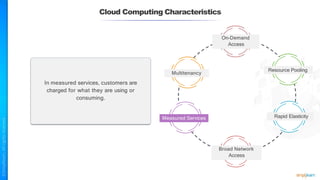
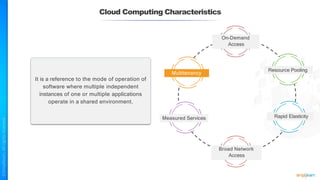
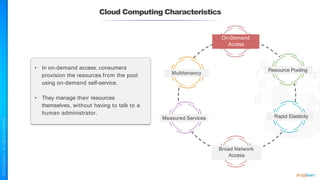
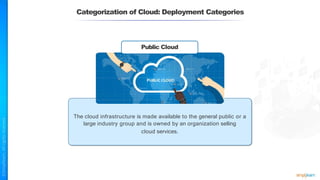
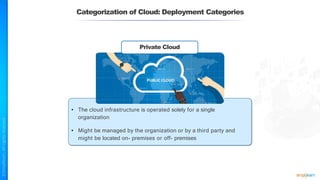
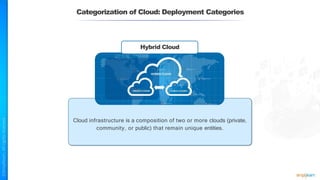
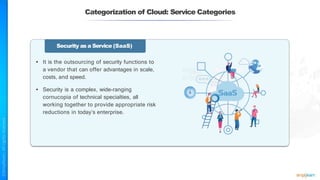
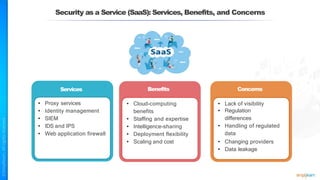
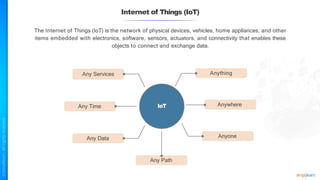
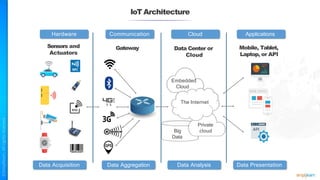
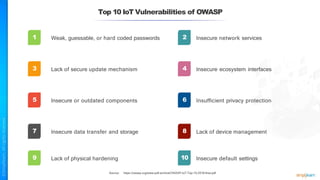
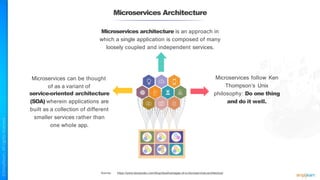
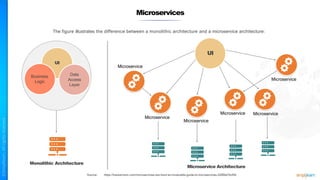
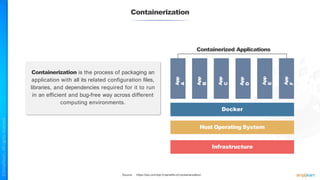
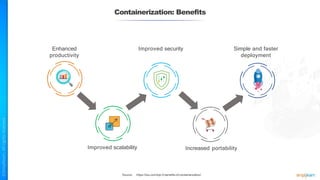
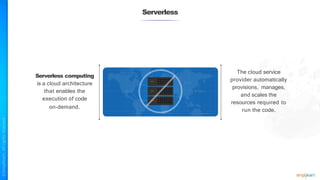
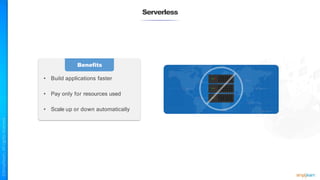
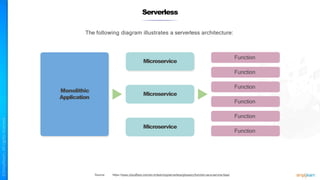
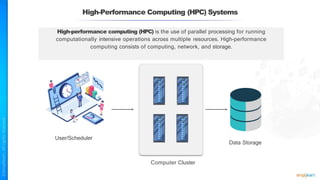
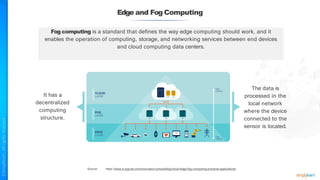
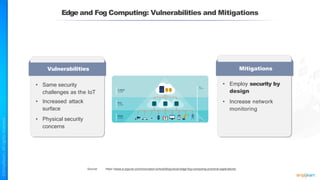
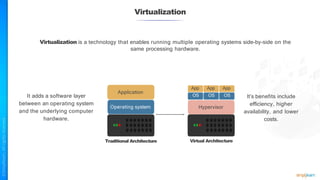
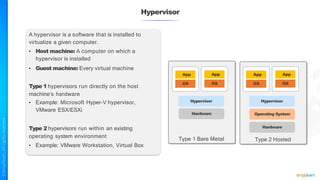
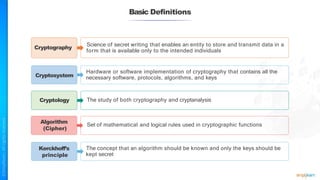
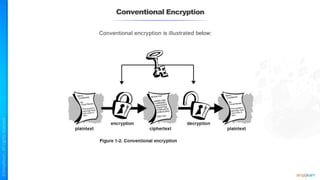
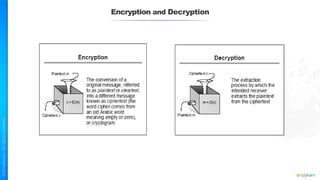
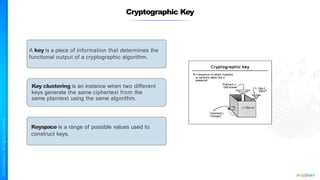
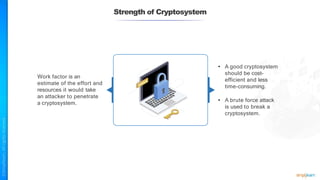
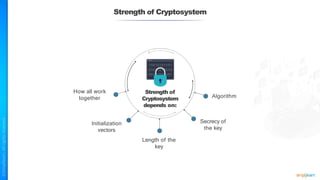
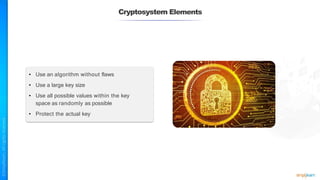
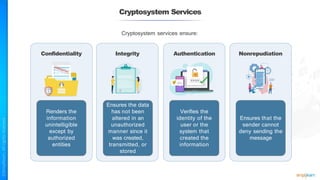
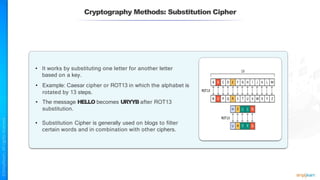
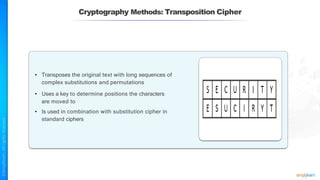
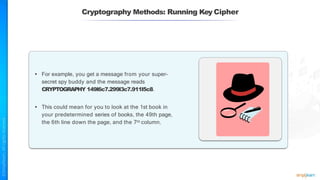
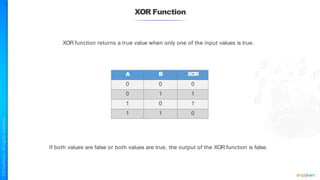
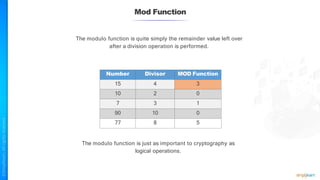
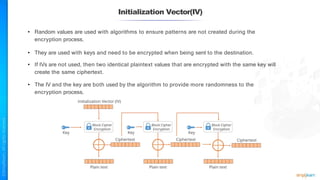
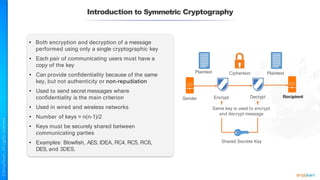
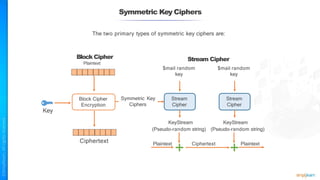
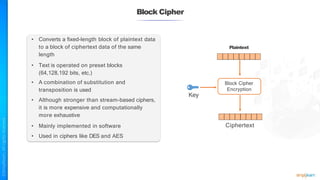
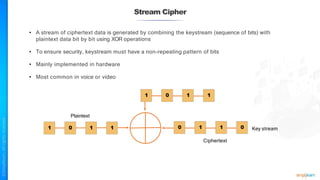
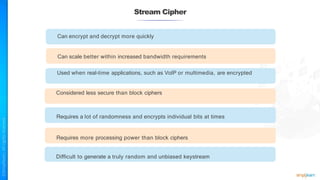
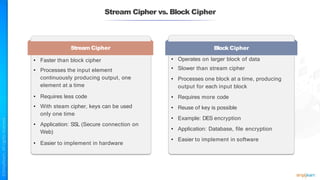
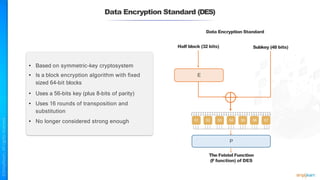
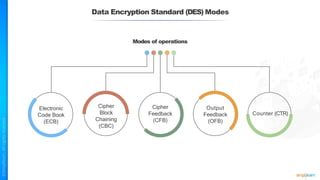
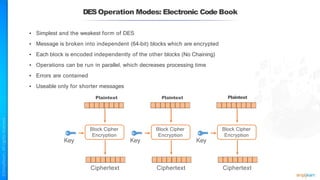
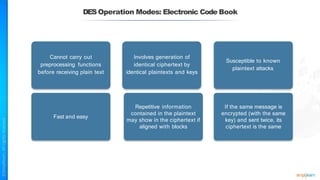
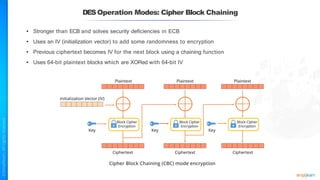
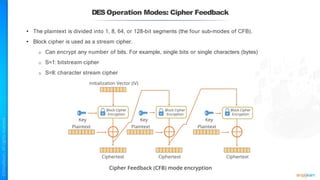
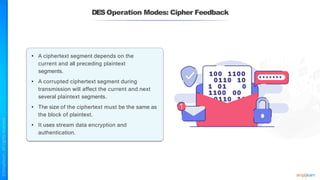
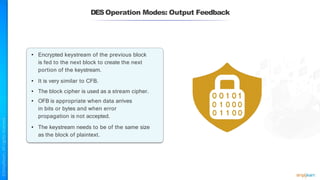
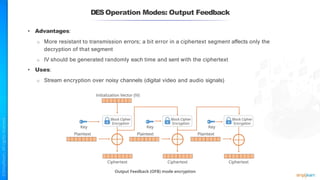
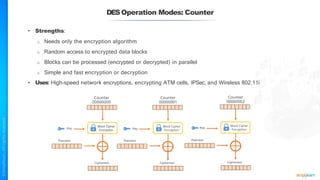
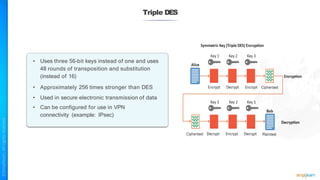
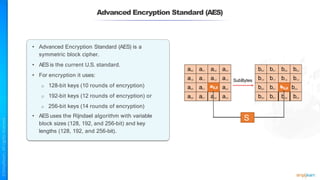
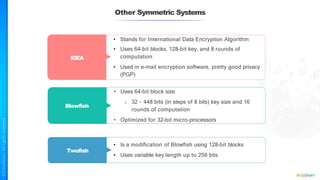
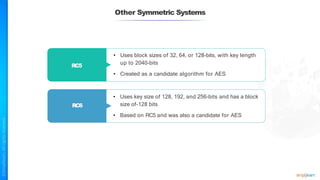
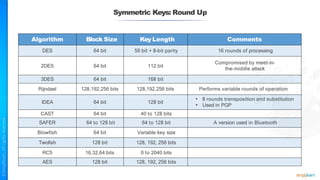
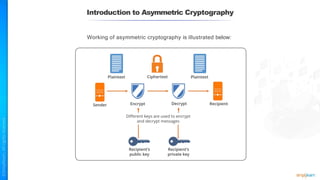
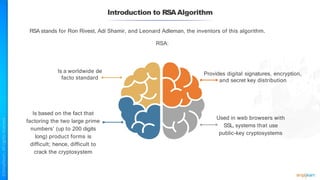
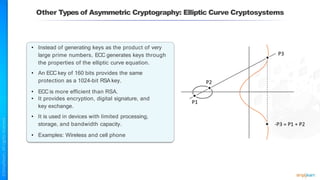
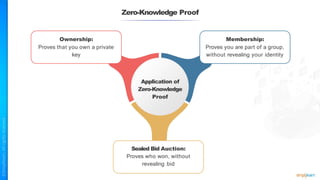
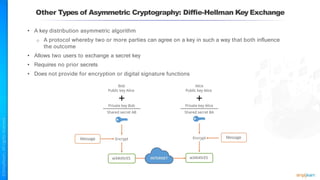
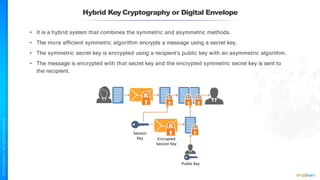
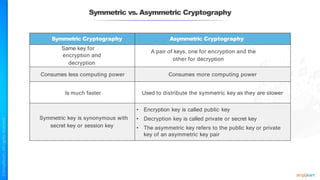
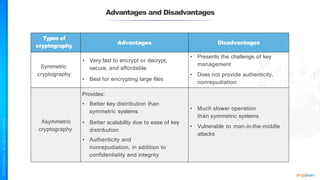
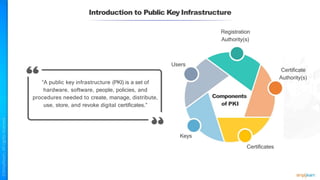
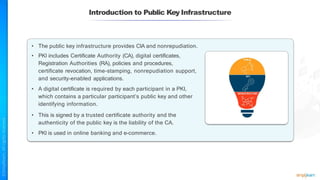
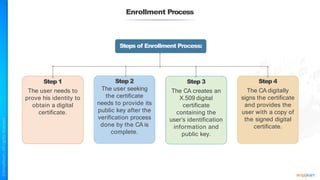
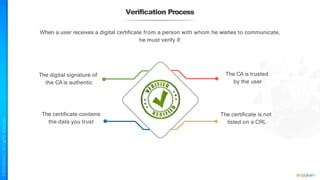
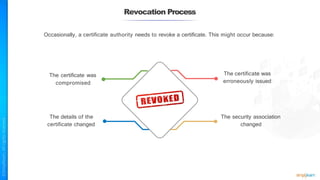
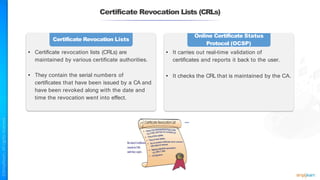
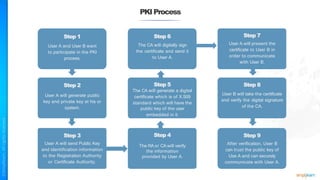
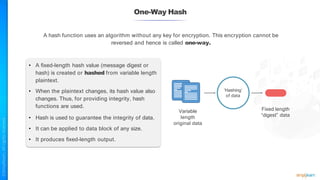
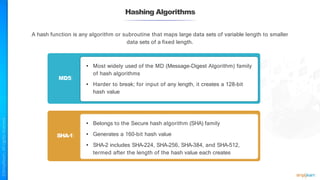
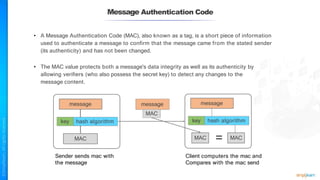
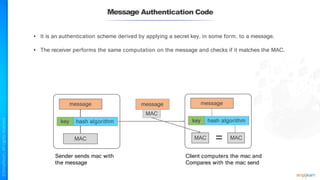
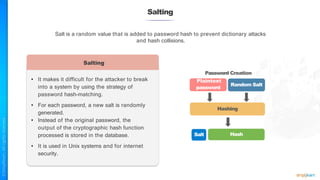
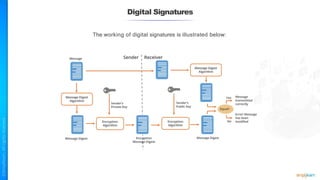
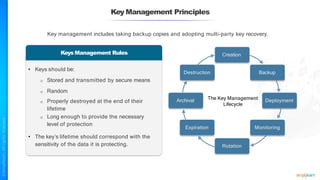
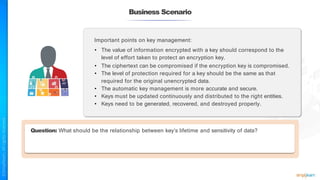
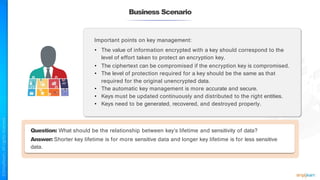
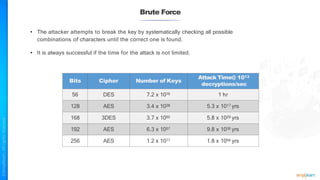
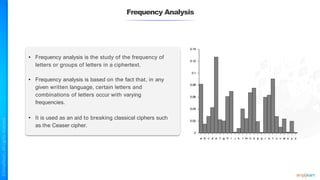
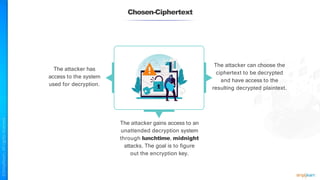
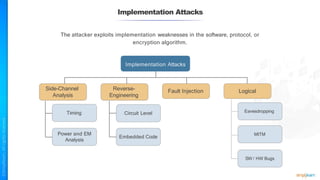
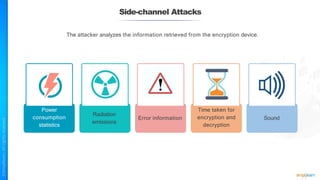
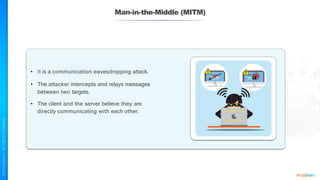
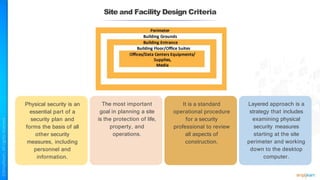
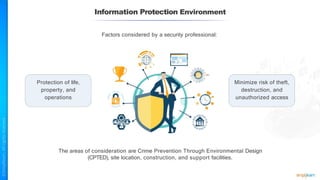
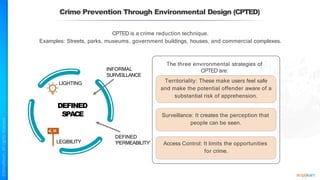
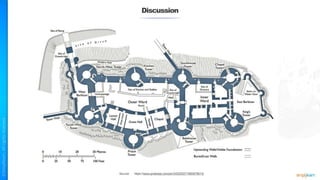
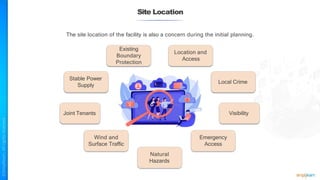
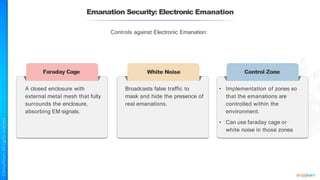
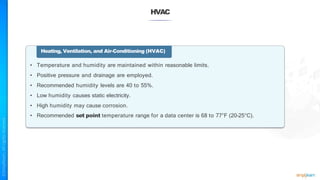
The document outlines a training course for the CISSP certification, focusing on security architecture and engineering principles. Key learning objectives include implementing secure design principles such as least privilege, fail secure, and zero trust, as well as understanding various security models like the Bell-LaPadula confidentiality model and the Biba integrity model. It also discusses the importance of privacy by design, risk management, and the shared responsibility model in cloud security.