This document discusses several key principles of information security:
- The principle of least privilege states that a subject should only be given access privileges necessary to complete its task and no more.
- The principle of economy of mechanism states that security mechanisms should be as simple as possible to minimize errors.
- The principle of complete mediation requires that all access to objects be checked to ensure they are allowed.
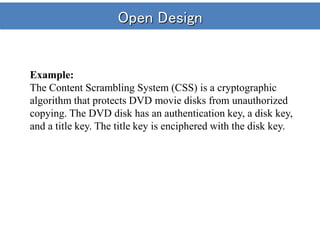
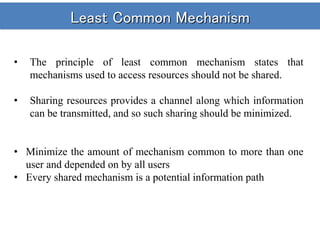
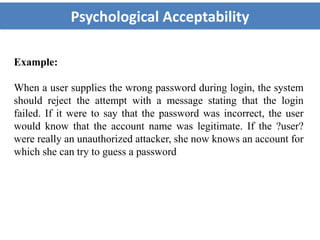
- Several other principles like open design, separation of privilege, least common mechanism, psychological acceptability, and fail-safe defaults are also discussed.