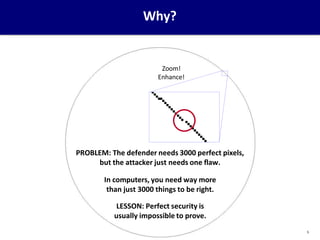
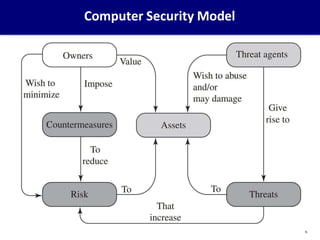
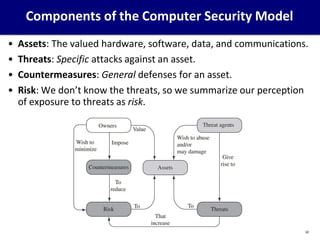
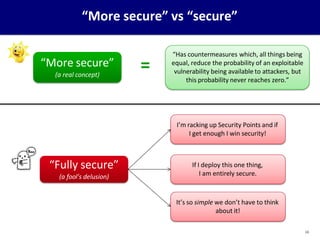
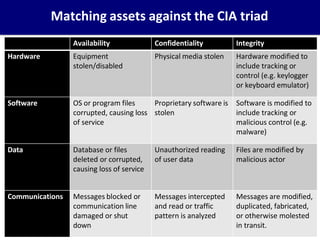
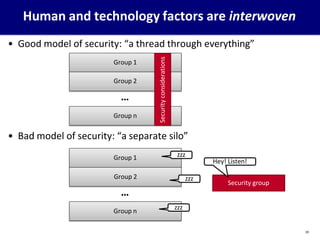
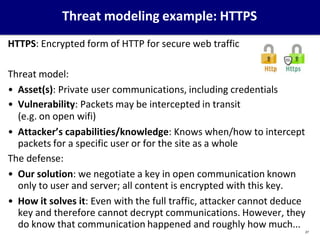
This document provides an overview of computer security concepts. It defines information security using the CIA triad of confidentiality, integrity and availability. It describes the computer security model involving assets, vulnerabilities, threats and countermeasures. It discusses classes of threats and examples of each. Design principles for secure software engineering are outlined, including least privilege and complete mediation. The importance of threat modeling and the security strategy of specification, implementation and evaluation are emphasized. The goal is to promote systematic thinking to reduce vulnerabilities and the likelihood of missed threats.