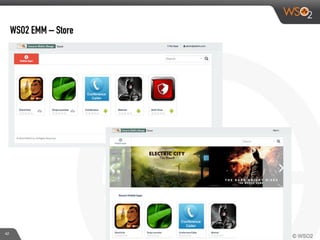
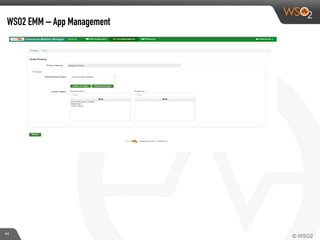
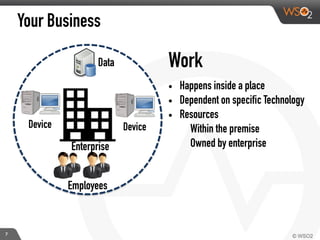
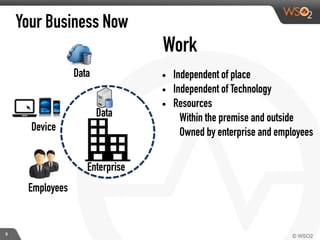
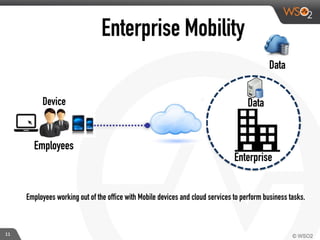
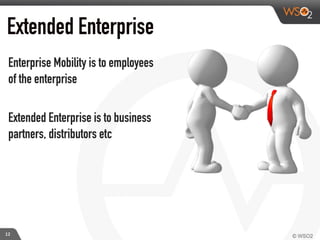
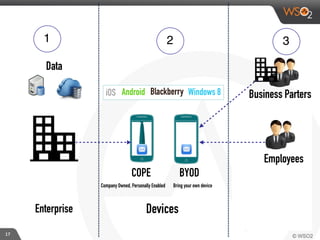
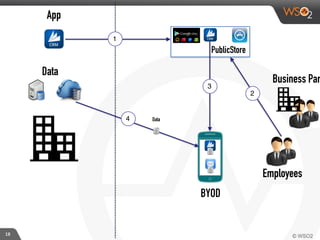
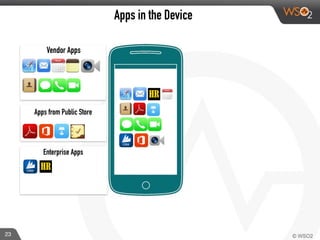
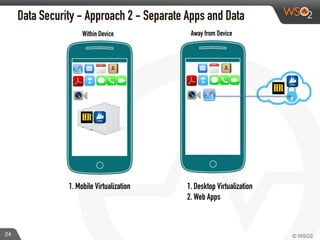
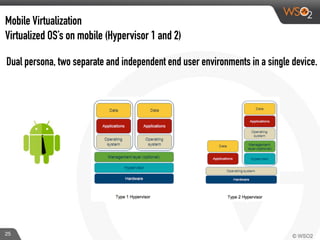
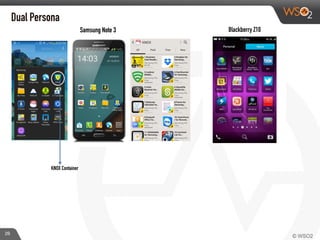
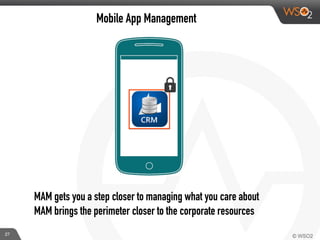
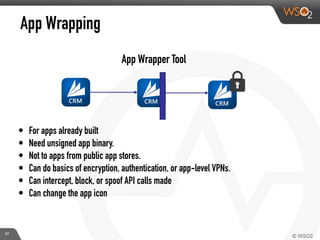
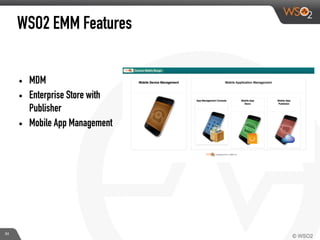
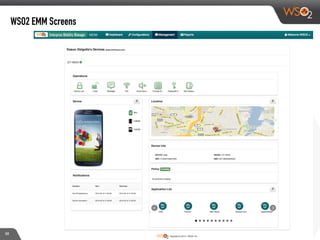
This document discusses enabling BYOD (bring your own device) programs in businesses using WSO2 Enterprise Mobility Manager (EMM). It begins with an introduction of the presenter and WSO2. It then discusses how businesses have evolved from employees working solely from the office to increasing mobility. This brings benefits like increased productivity but also risks around data security if devices are lost or apps are malicious. EMM tools like mobile device management (MDM) and mobile application management (MAM) can help secure devices and control apps/data. WSO2 EMM is highlighted as an open source solution that provides MDM, an enterprise app store, and MAM features to securely enable BYOD programs while balancing usability






















![• Supports multiple platforms
• Android
• Native, Hybrid Application (.apk)
• Web Application
• Market Place Application (Google Play) [Free]
• iOS (iPhone, iPad)
• Native, Hybrid Application (.ipa) - Need to have enterprise developer account
• Web Application
• Apple Store Application [Free]
• VPP Application (Next Release)
Publisher
40](https://image.slidesharecdn.com/wso2emmbyodnow-140410030257-phpapp02/85/BYOD-for-your-business-with-WSO2-Enterprise-Mobility-Manager-40-320.jpg)