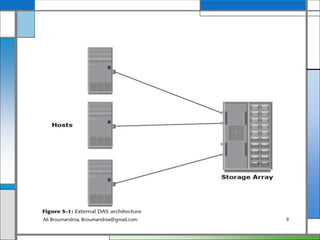
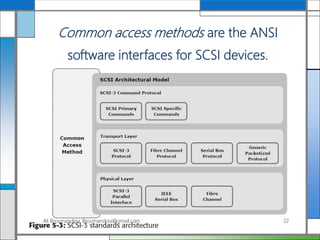
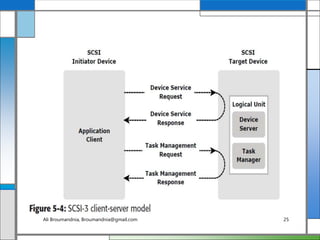
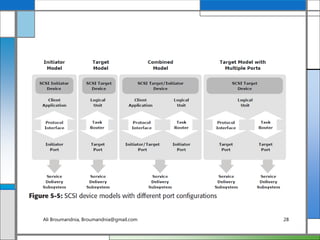
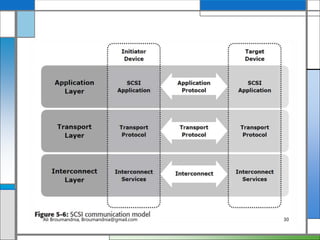
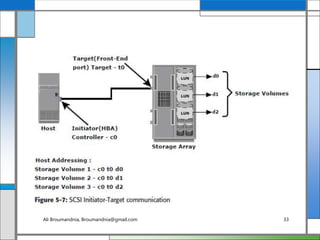
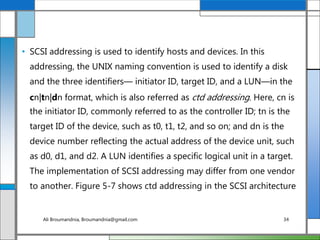
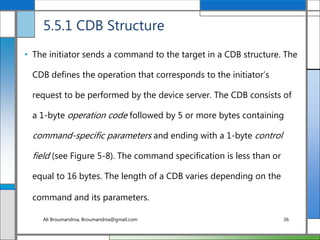
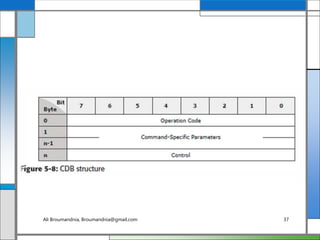
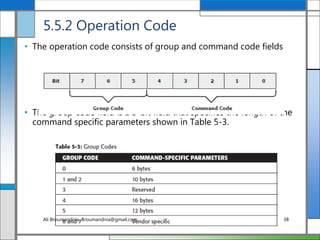
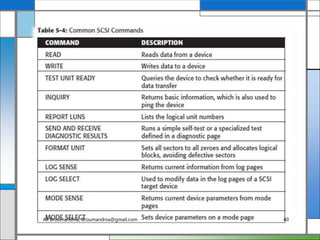
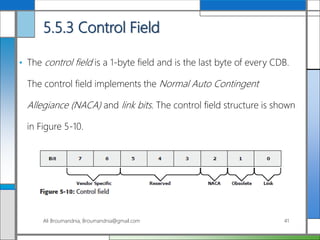
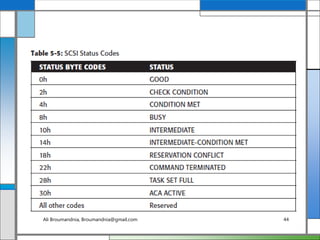
The document discusses storage networking technologies and virtualization. It covers direct-attached storage (DAS) and introduces the Small Computer System Interface (SCSI) standard. Chapter 5 details the two types of DAS (internal and external), their benefits and limitations, and disk drive interfaces like IDE/ATA, SATA, SAS, SCSI, and Fibre Channel. It also provides an introduction to parallel SCSI, including its evolution and architecture.