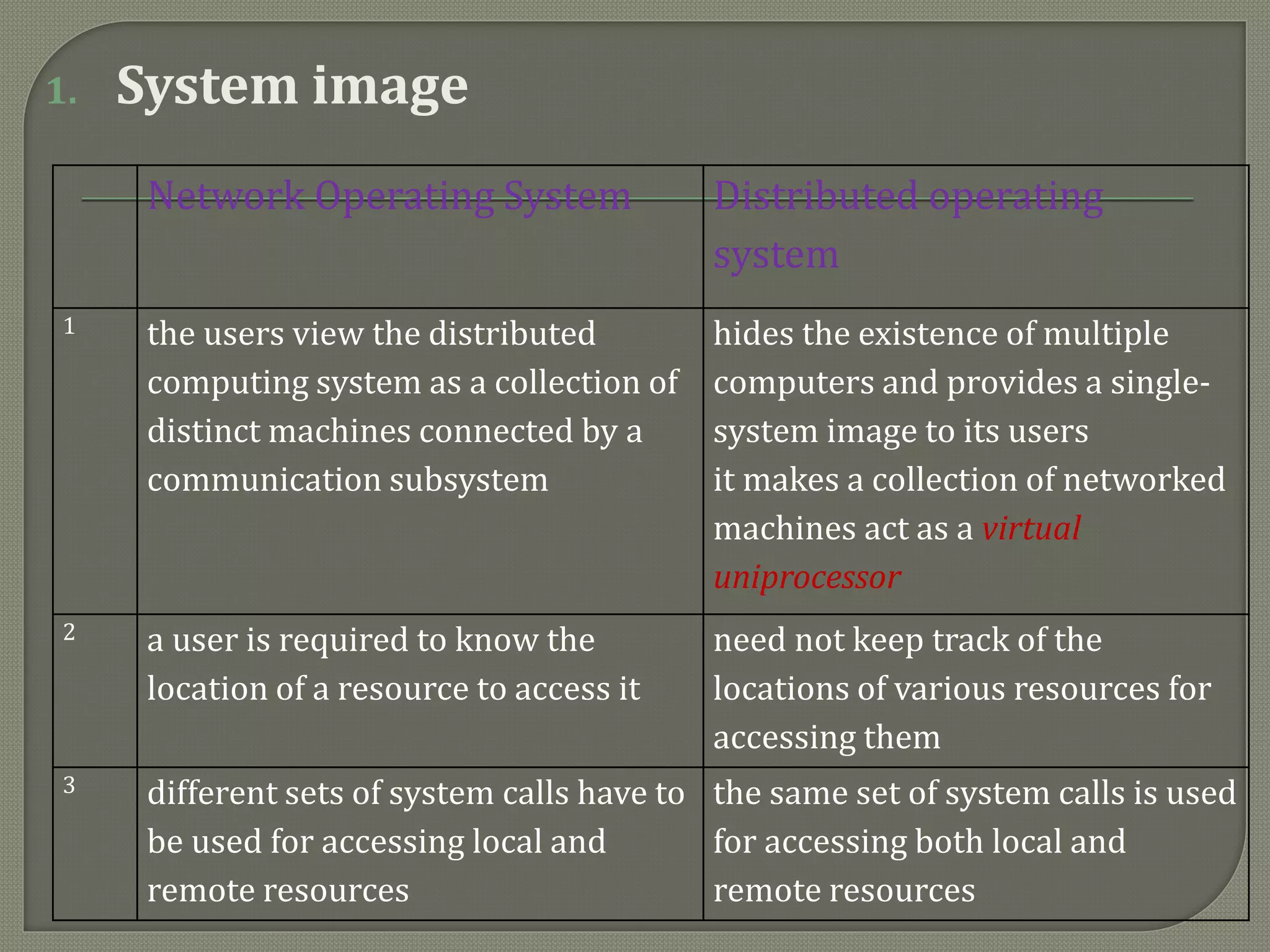
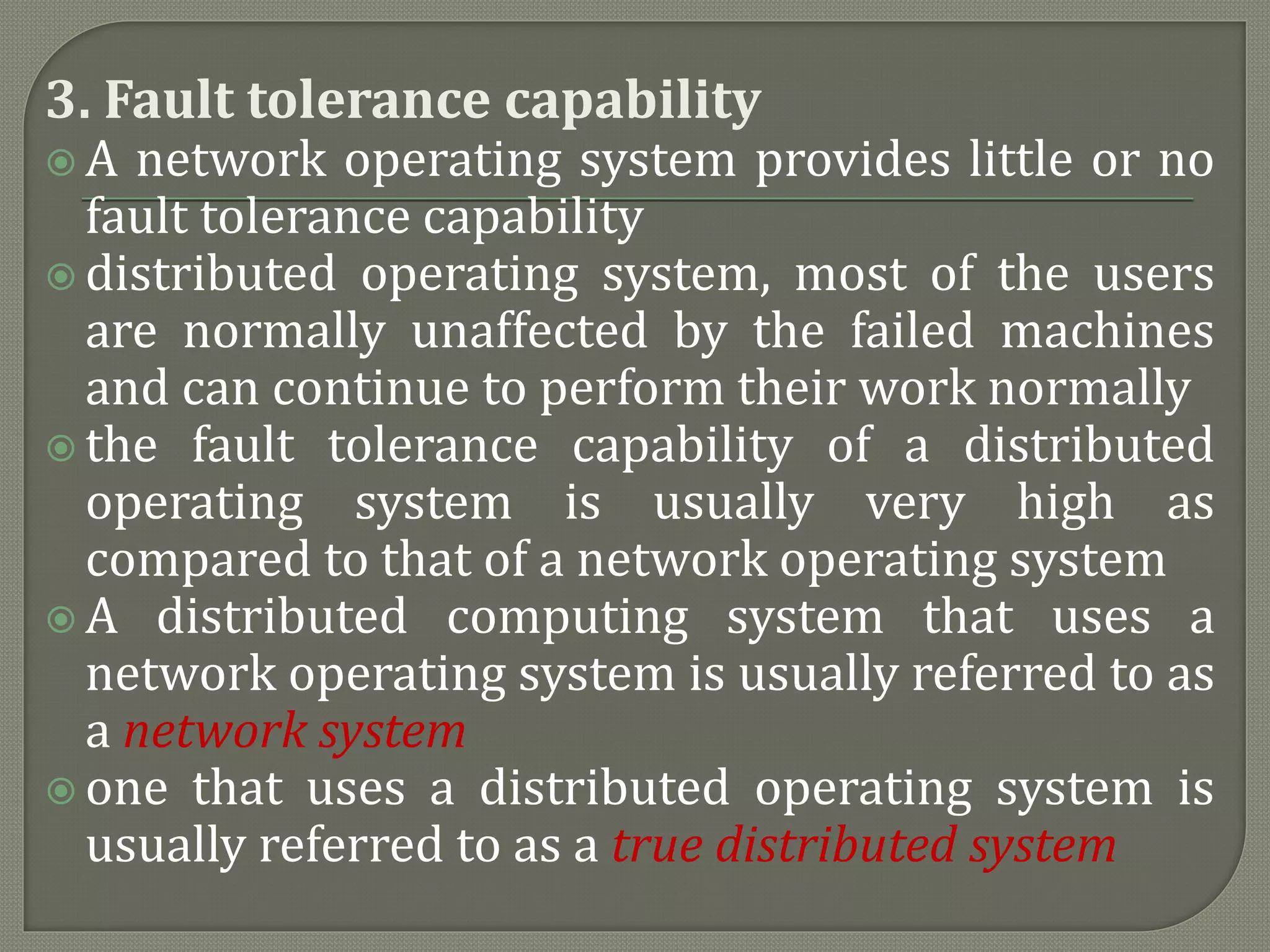
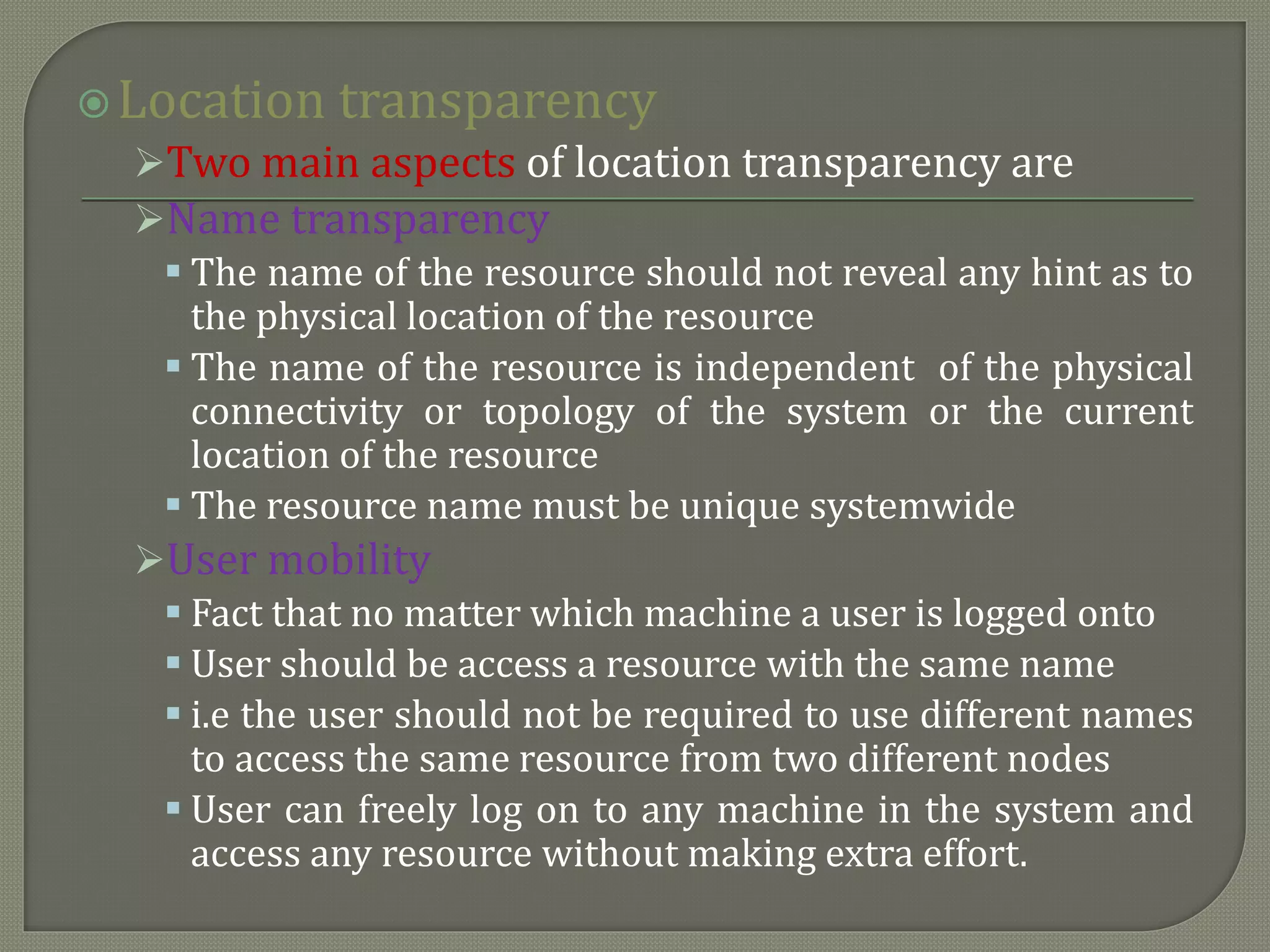
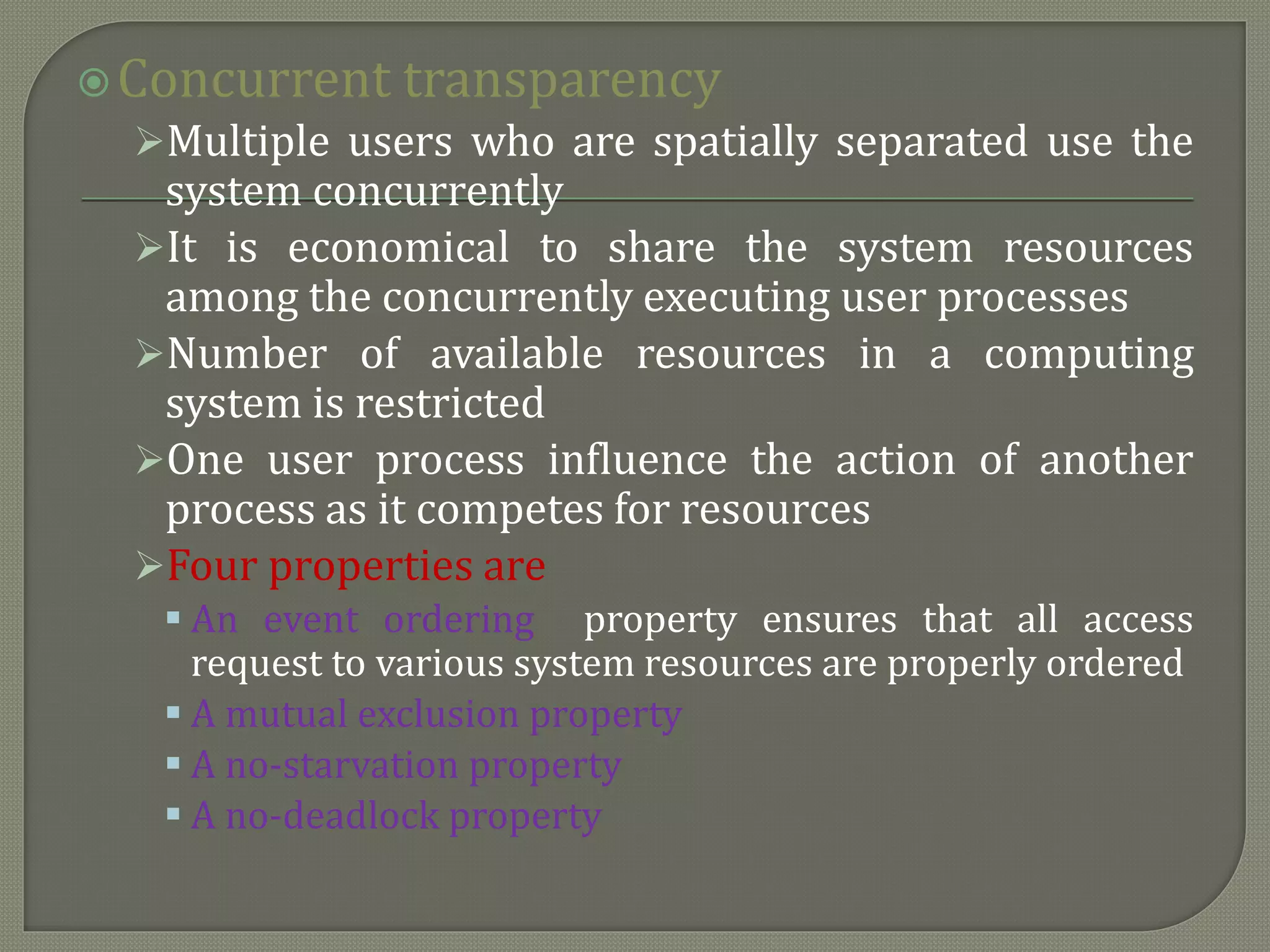
The document discusses distributed computing systems, highlighting their inherent nature and requirements, such as information sharing, resource sharing, and improved performance metrics over centralized systems. It explains various aspects like reliability, extensibility, and flexibility, comparing network and distributed operating systems based on features like transparency and fault tolerance. The content also addresses the importance of scalability and performance optimization principles in the design of distributed systems.