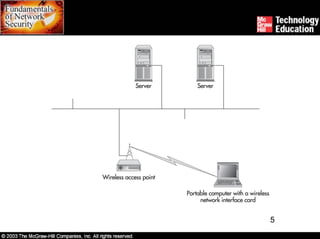
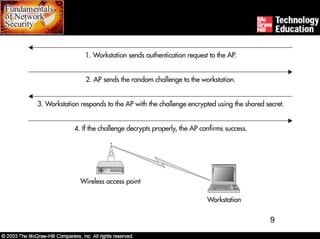
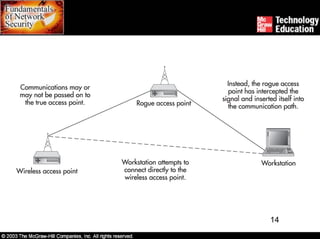
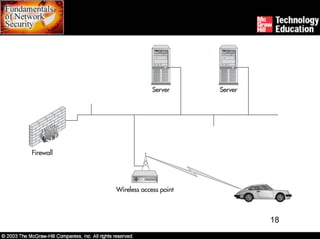
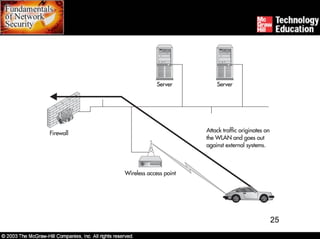
Wireless networks introduce security risks like eavesdropping and internal attacks. The 802.11x standards define wireless transmission and authentication using options like SSID, MAC address, WEP, and 802.1x. Deploying wireless safely involves securing access points, transmissions, workstations, and the entire site through measures such as encryption, firewalls, and intrusion detection.