Embed presentation




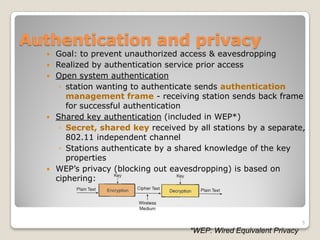
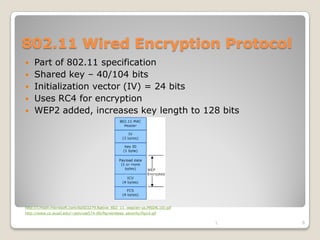

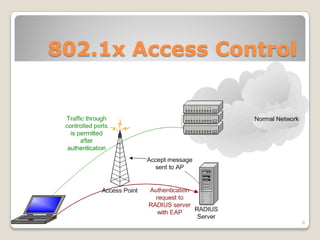


The document discusses how 802.11 wireless networking can be monetized through various business models like setting up hotspots, working with communities to provide free WiFi, and combining office networks. It then outlines the benefits of 802.11 including roaming freedom, real-time data updates, and high-speed data transmission compared to wired or dial-up options. Finally, it examines the security protocols within 802.11 like WEP, WPA, and 802.1x which provide authentication, encryption, and access control to prevent unauthorized access.








