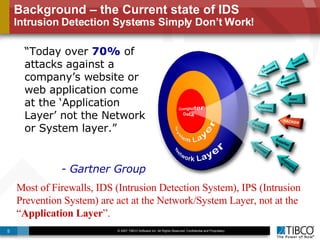
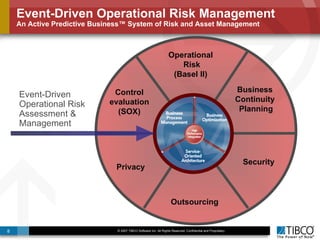
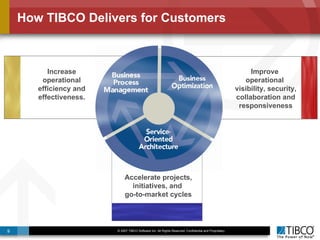
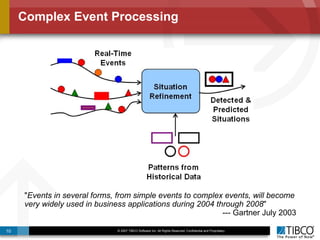
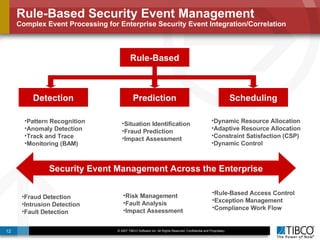
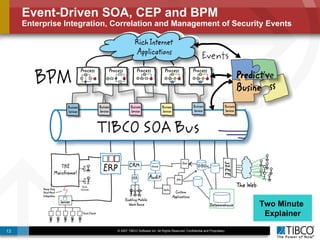
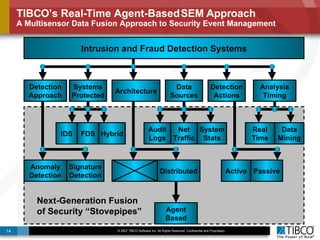
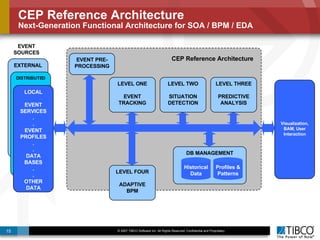
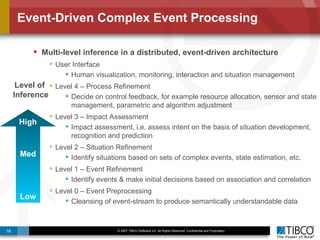
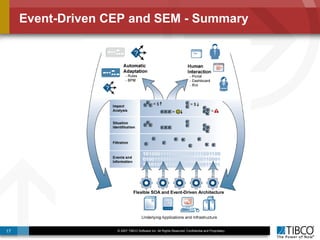
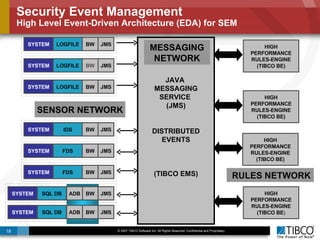
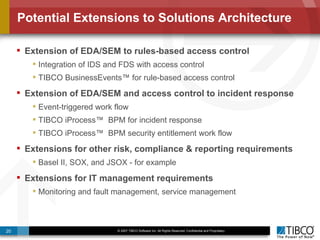
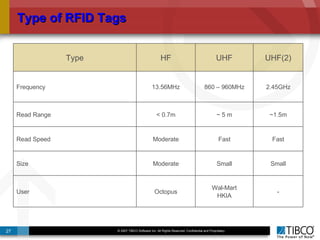
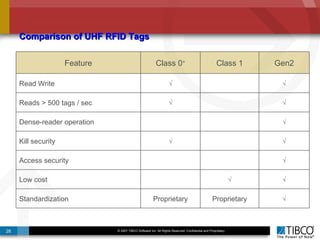
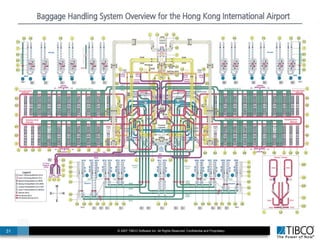
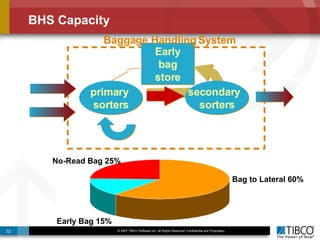
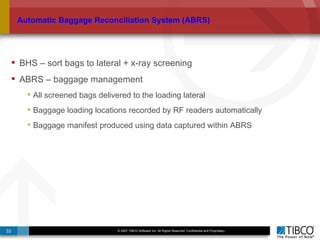
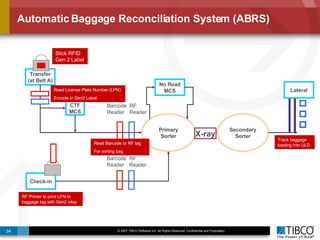
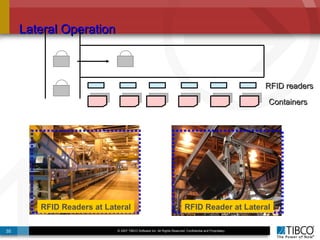
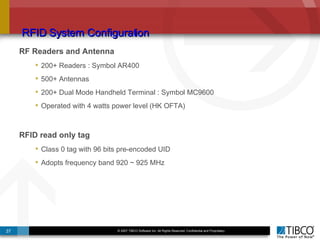
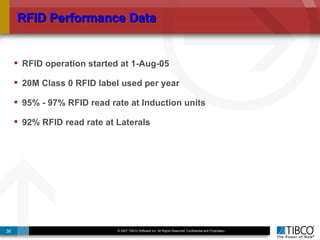
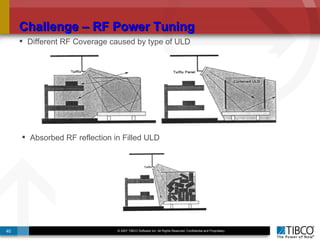
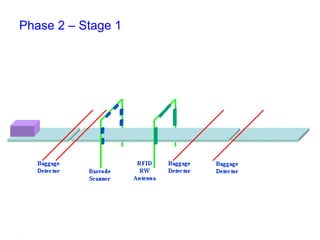
The document outlines an open event-driven architecture for risk management in financial services, detailing the importance of integrating diverse event sources across enterprises for improved security and compliance. It discusses TIBCO's solutions for complex event processing (CEP) and security event management, emphasizing the need for real-time analytics and adaptive controls to address security breaches. Additionally, it highlights industry drivers, market trends, and challenges within the realm of network security and compliance management.