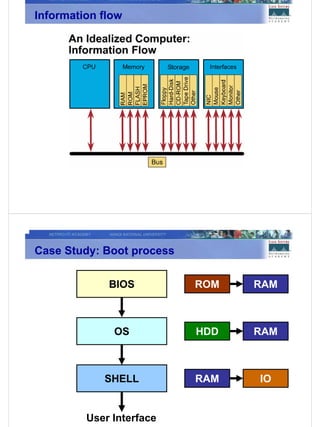
Module 1 of the CCNA curriculum covers fundamental networking concepts including:
1) The physical and logical requirements for connecting a computer to the Internet using network interface cards or modems.
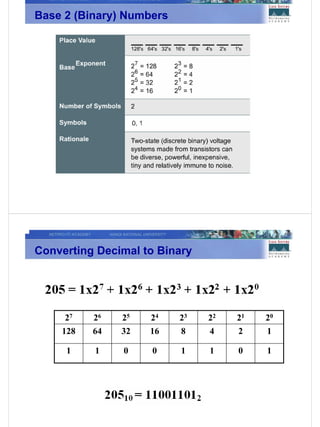
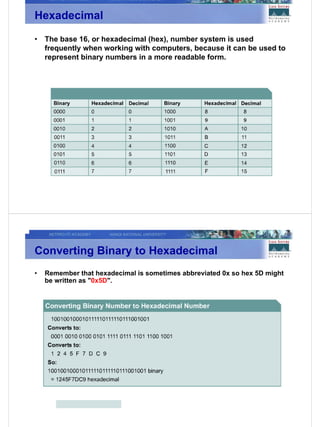
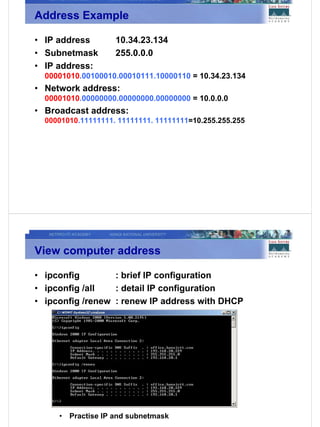
2) Binary number systems and how to convert between binary, decimal, and hexadecimal representations which is important for IP addressing.
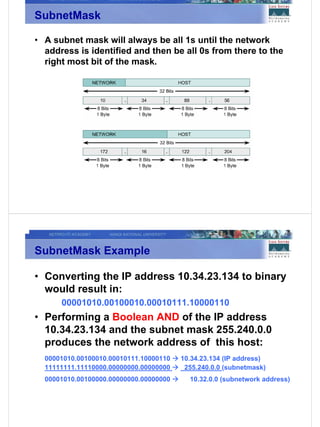
3) Key networking technologies like TCP/IP, IP addressing, subnet masks, and how to represent and calculate network addresses from a device's IP and subnet mask.