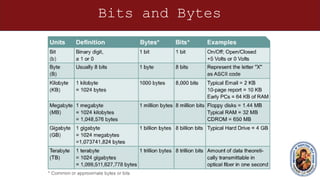
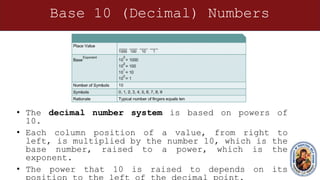
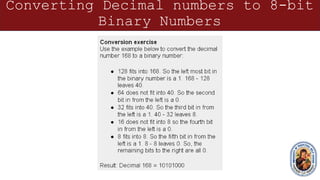
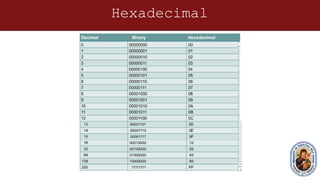
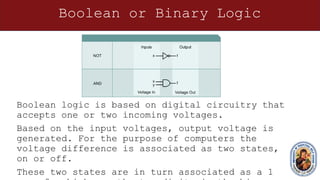
This document provides an overview of networking concepts and components. It discusses the physical and logical connections required for internet access, including modems and network interface cards. It also describes the basic components of a computer like the motherboard, processor, expansion slots, and how transistors and integrated circuits work. The document then covers networking topics like TCP/IP, ping testing, web browsers, troubleshooting, binary and hexadecimal number systems, IP addressing and network masks. The overall purpose is to help students understand the basic elements needed to connect a computer to the internet and communicate on a network.