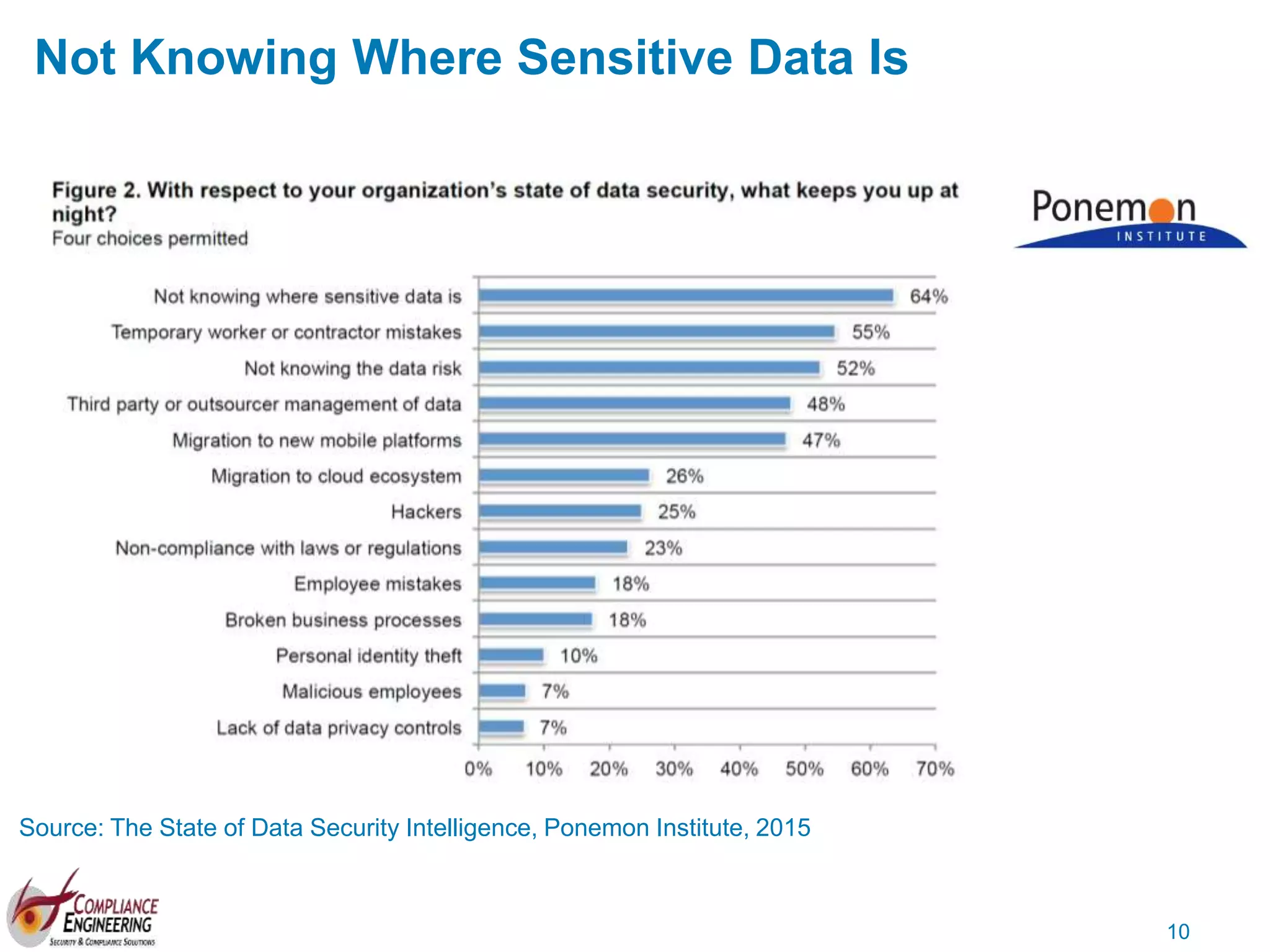
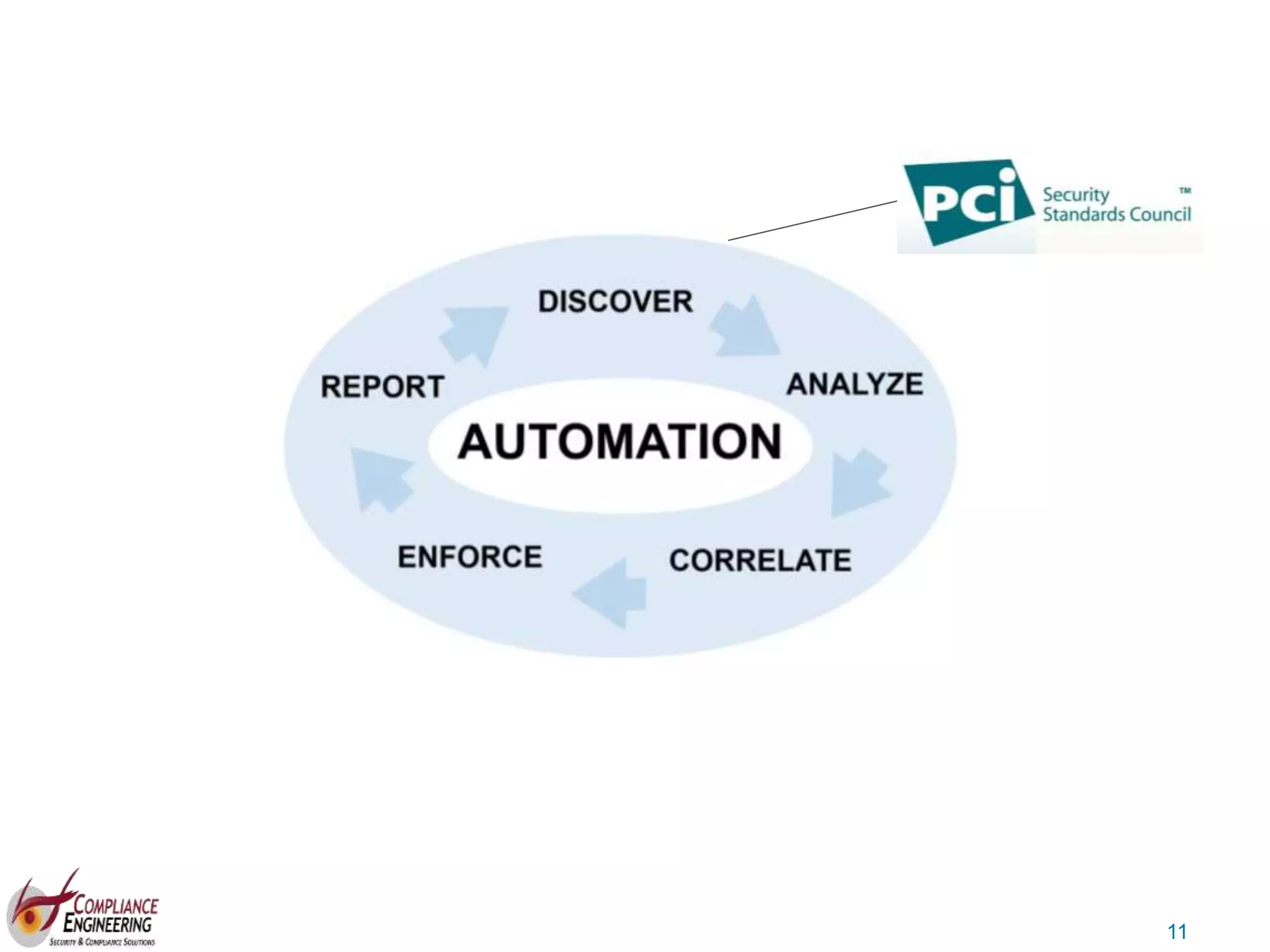
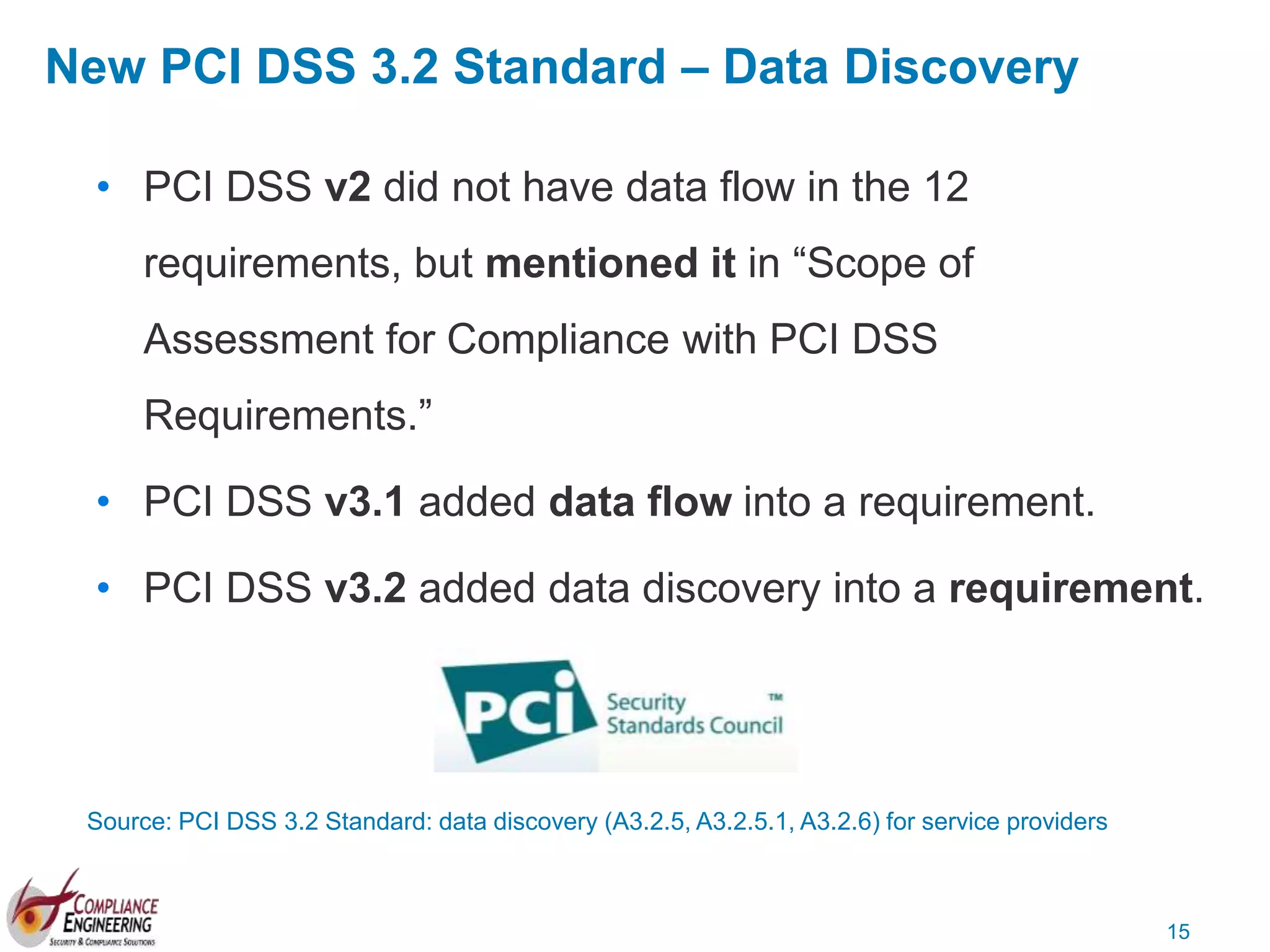
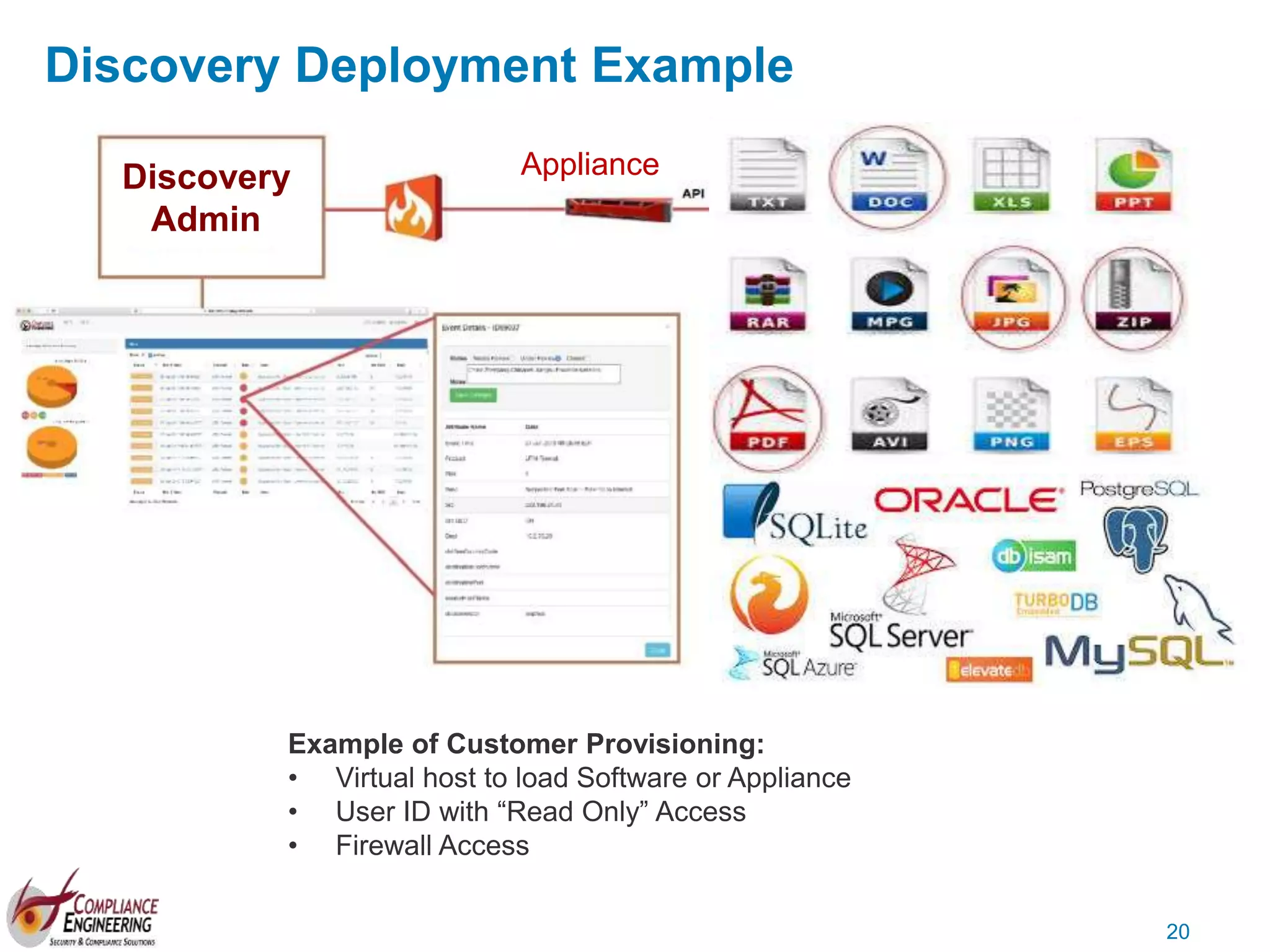
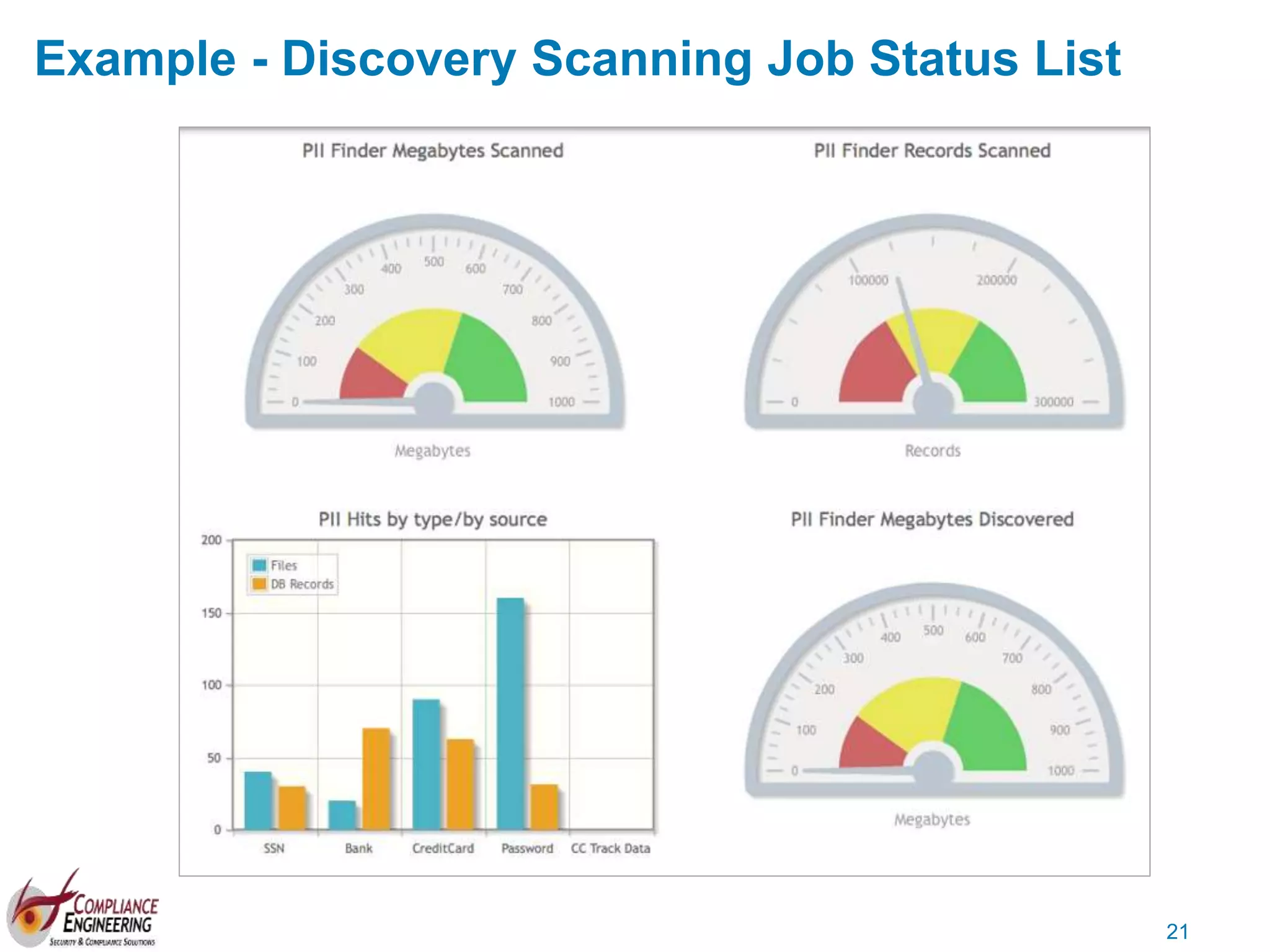
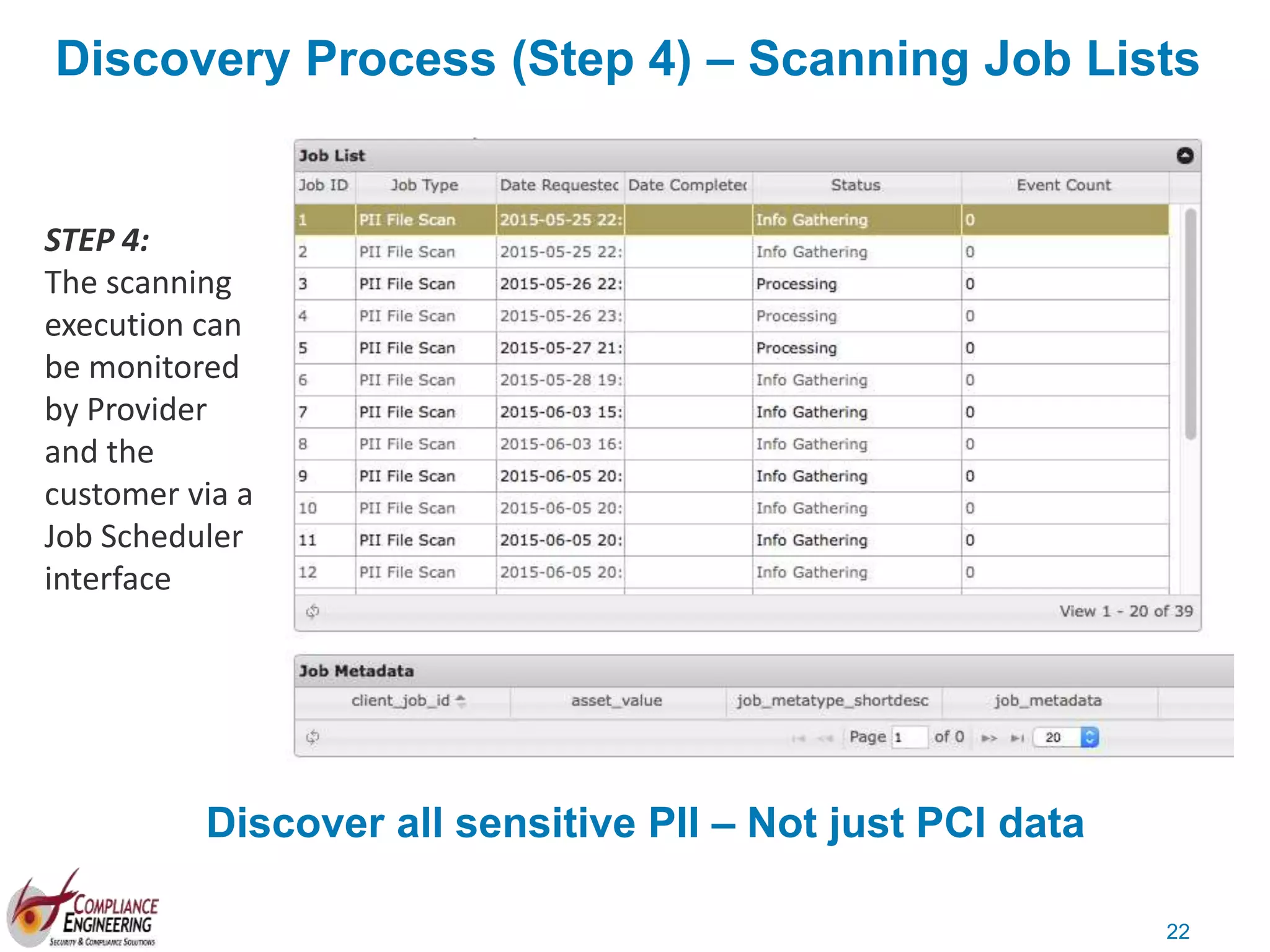
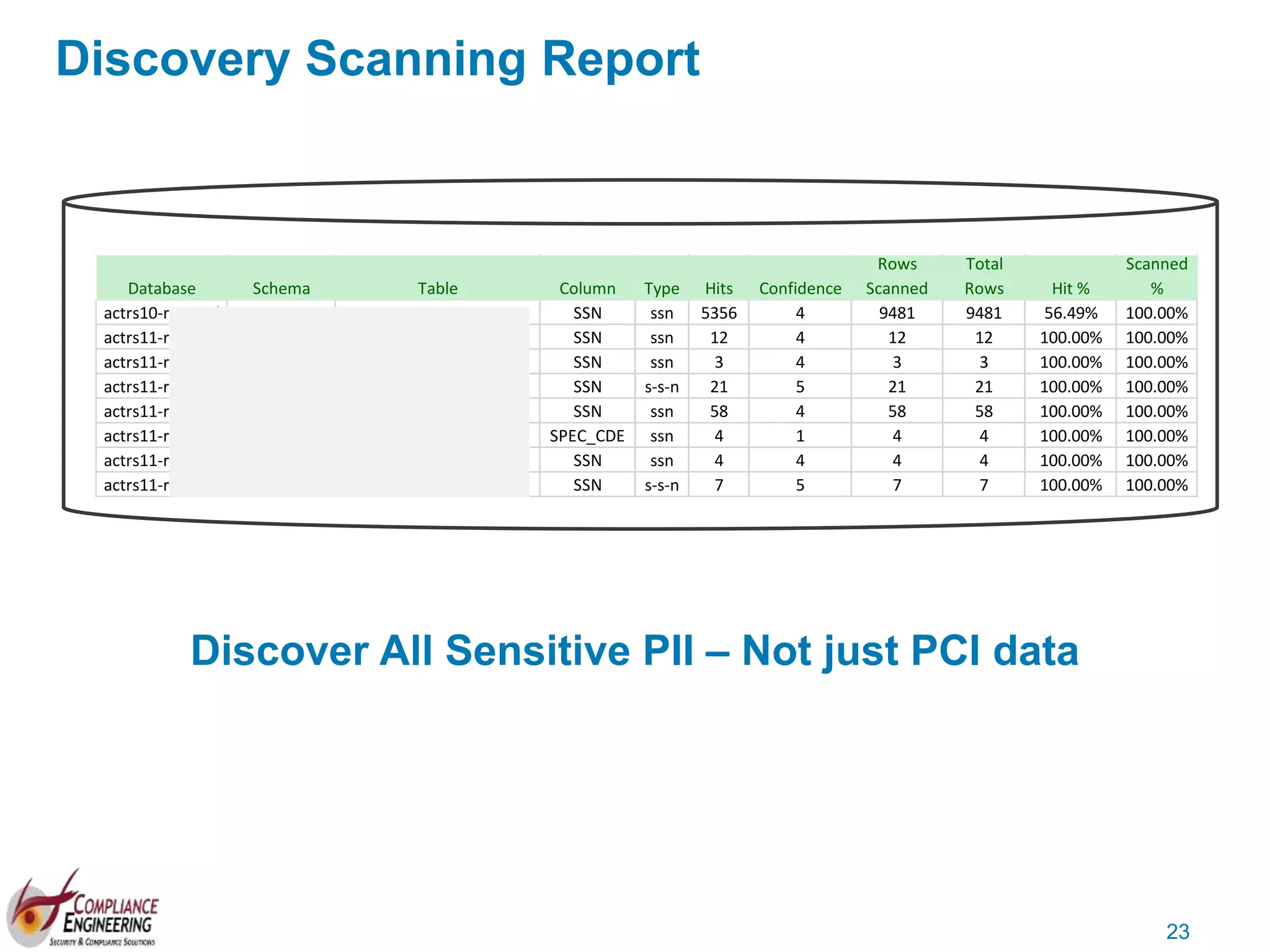
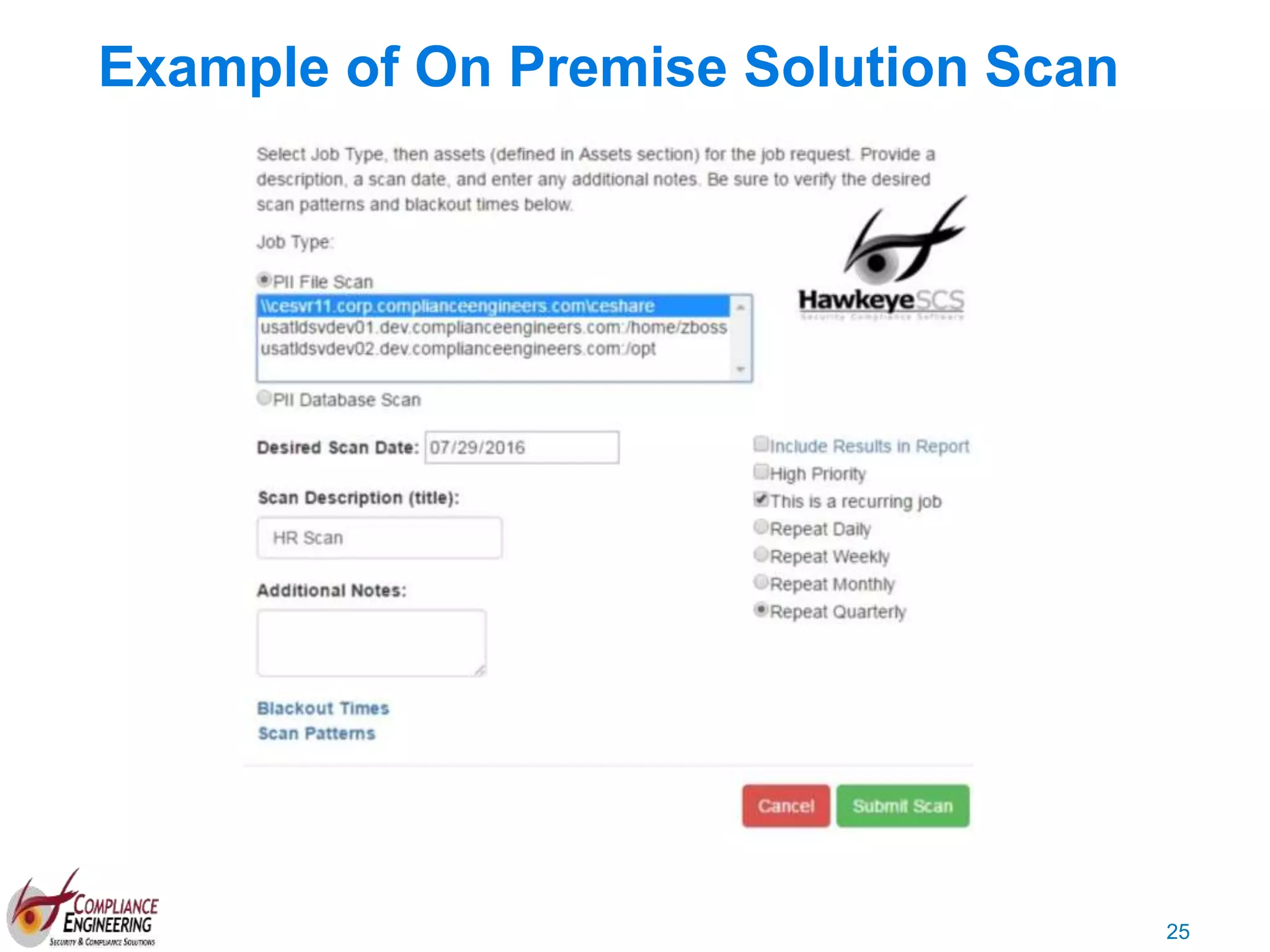
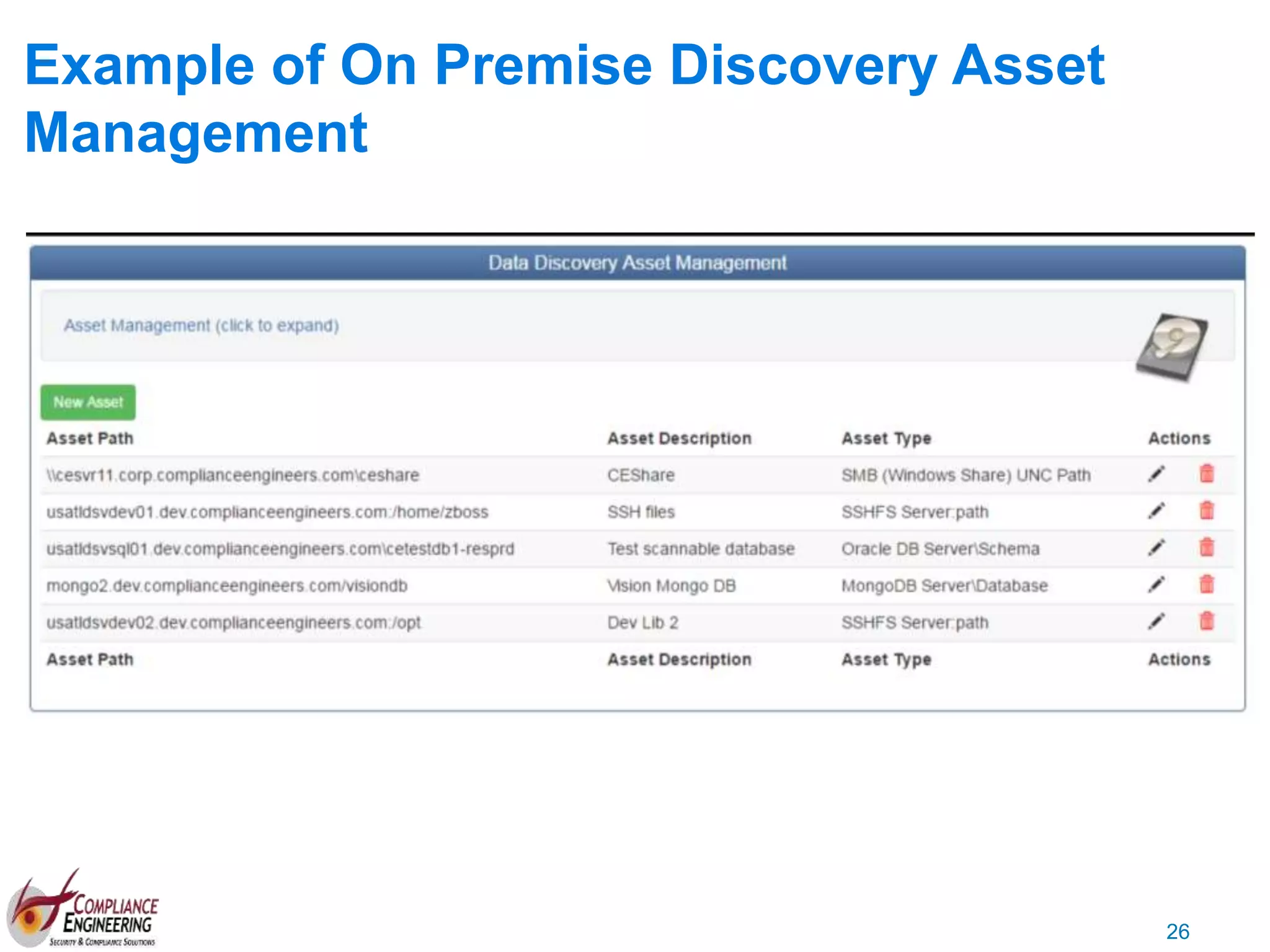
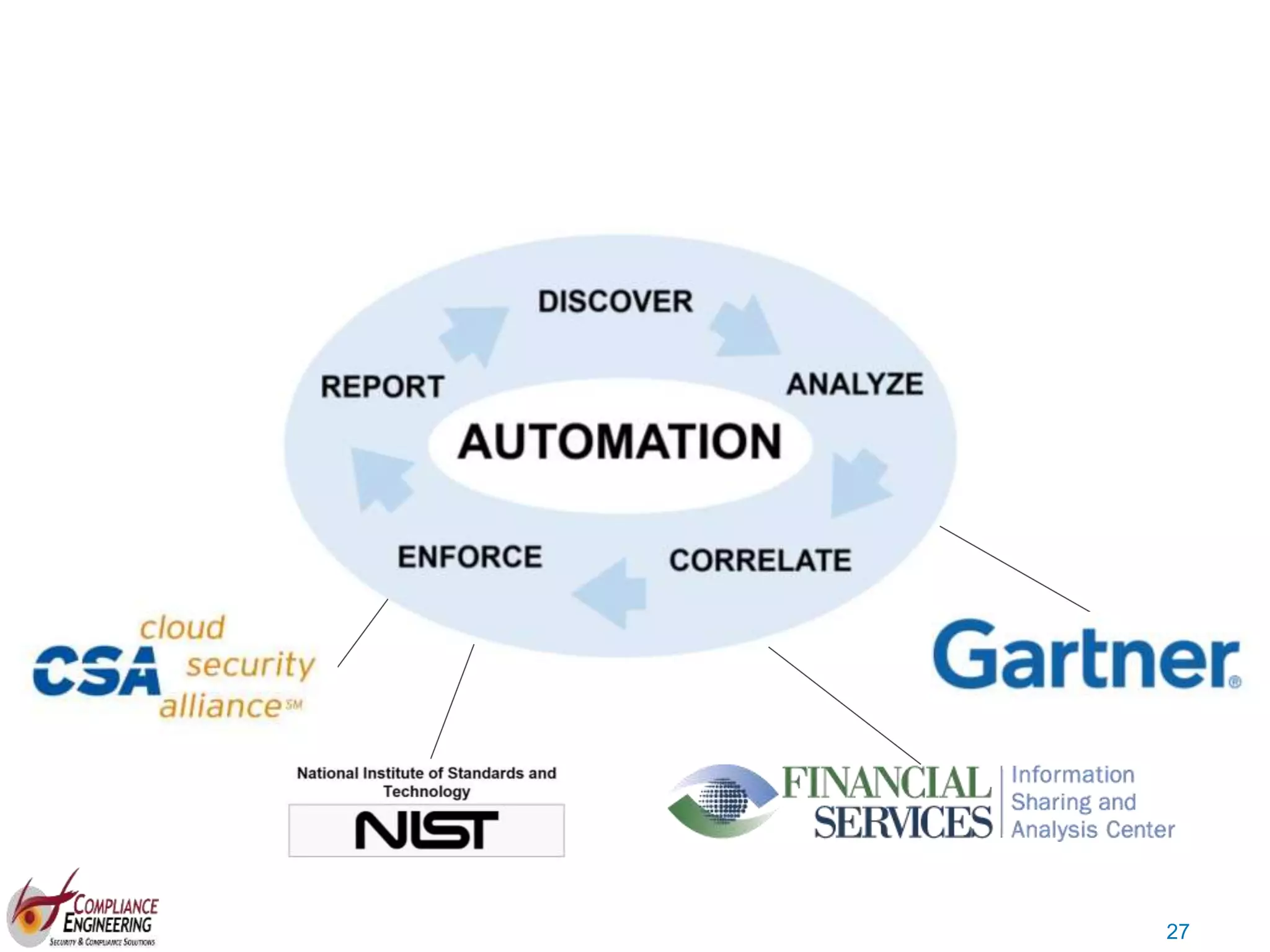
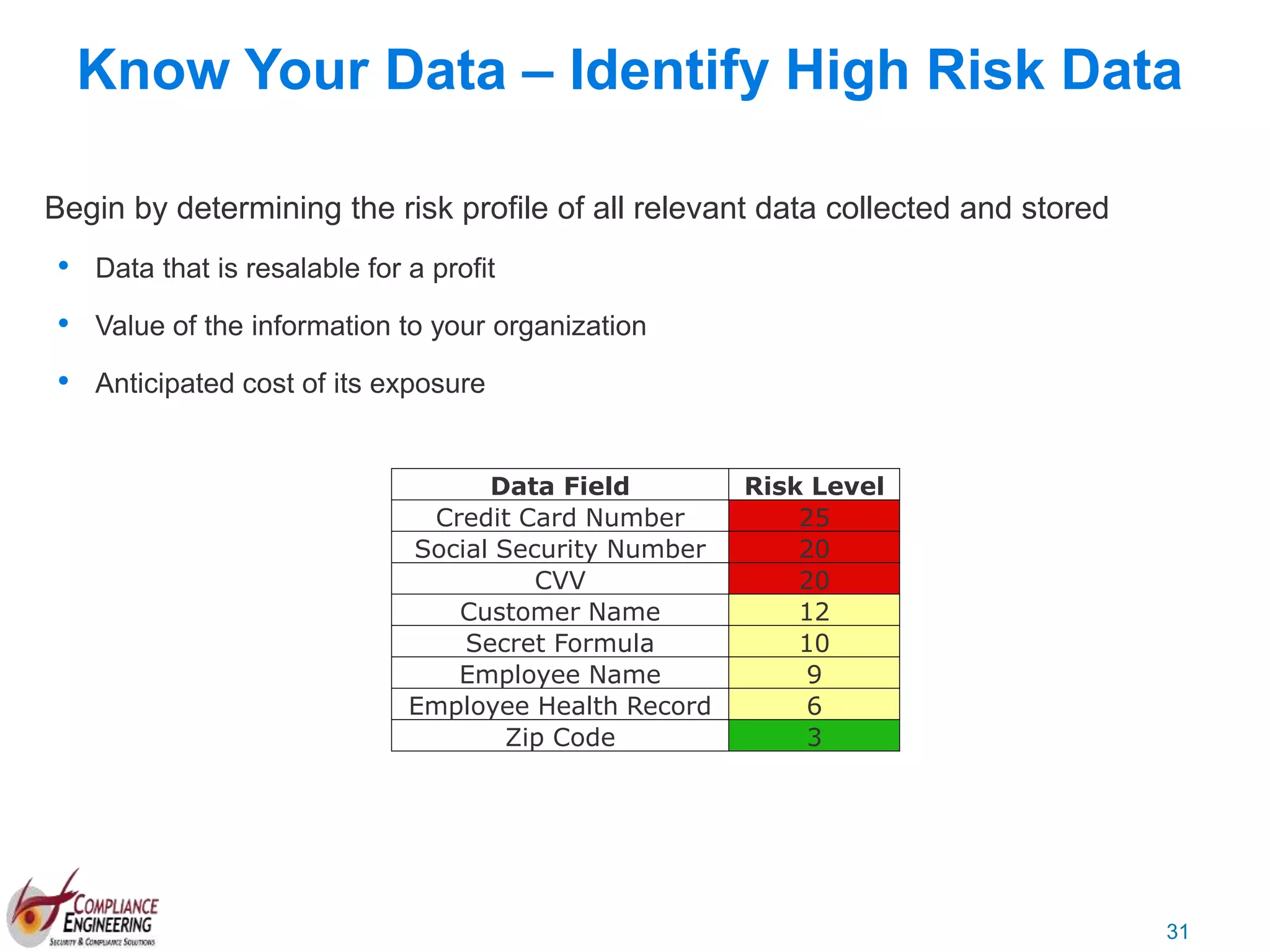
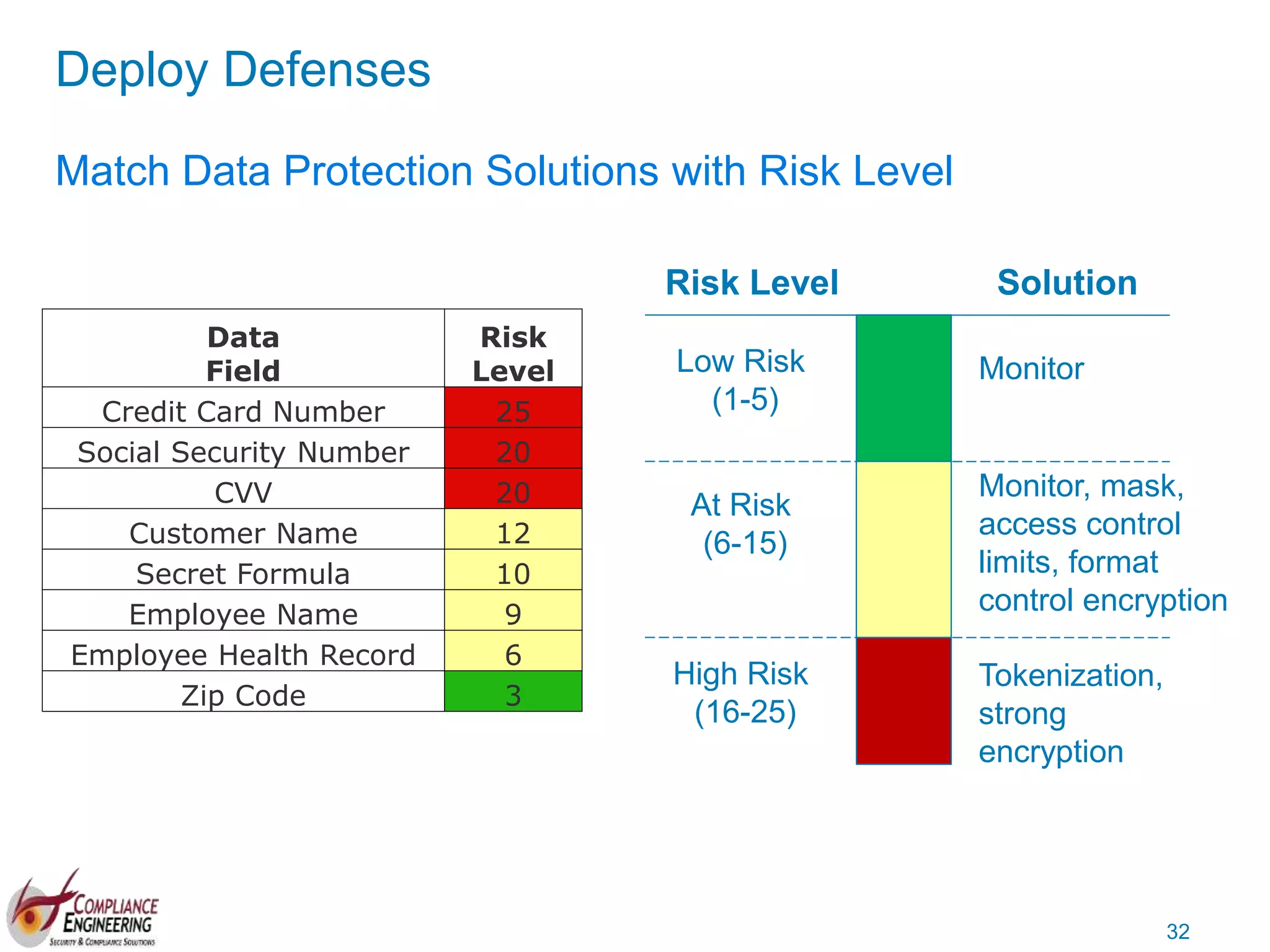
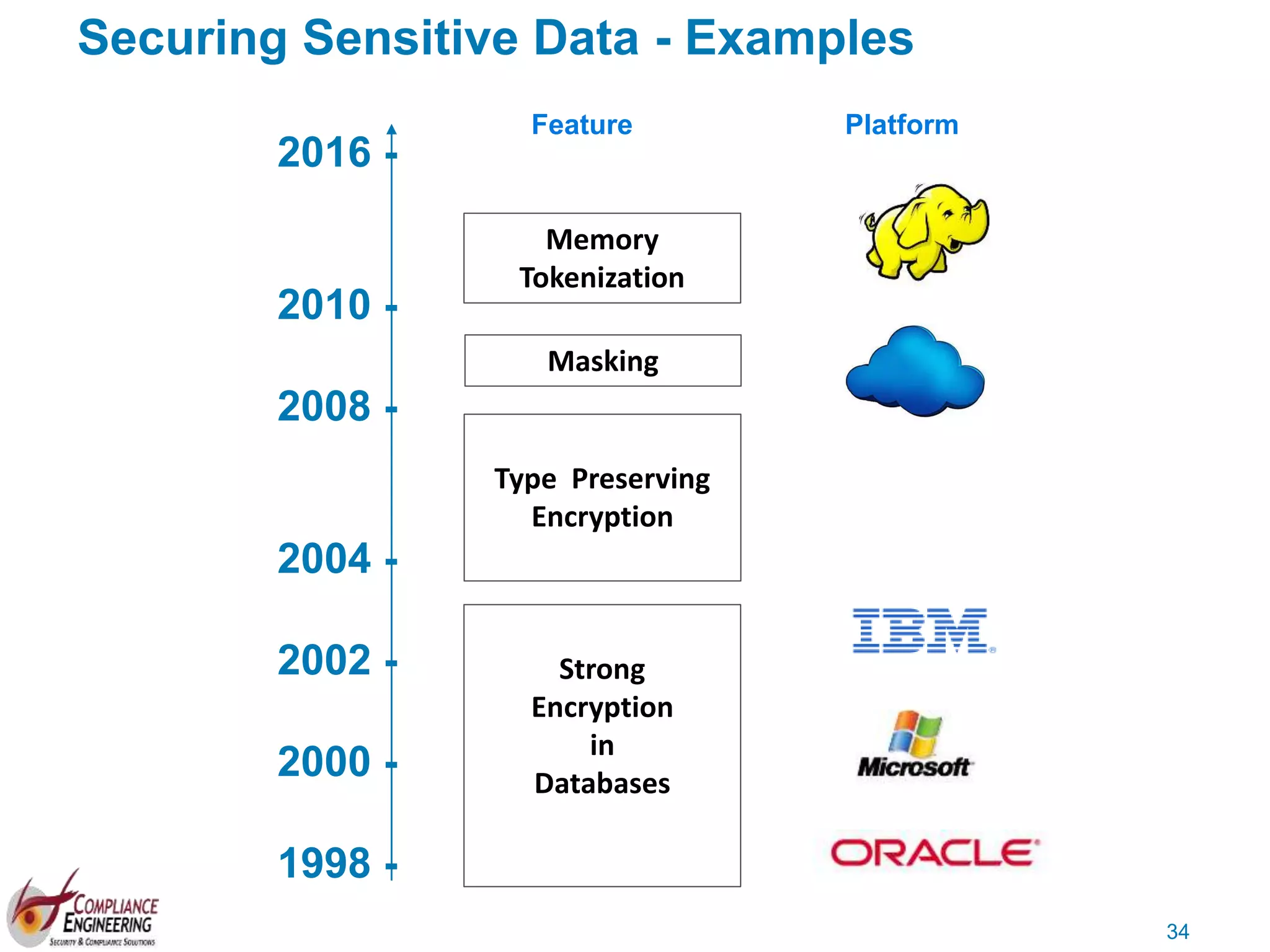
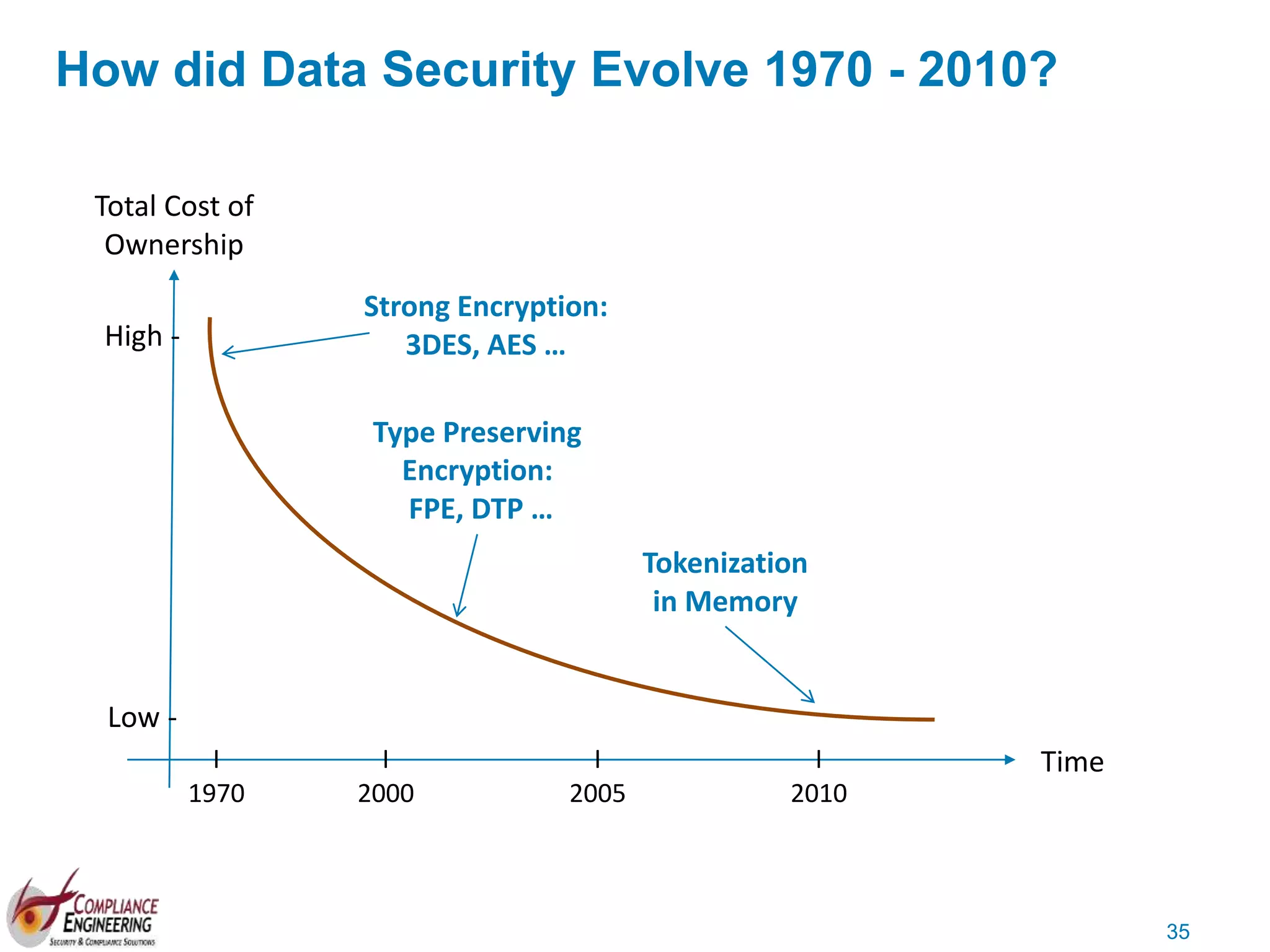
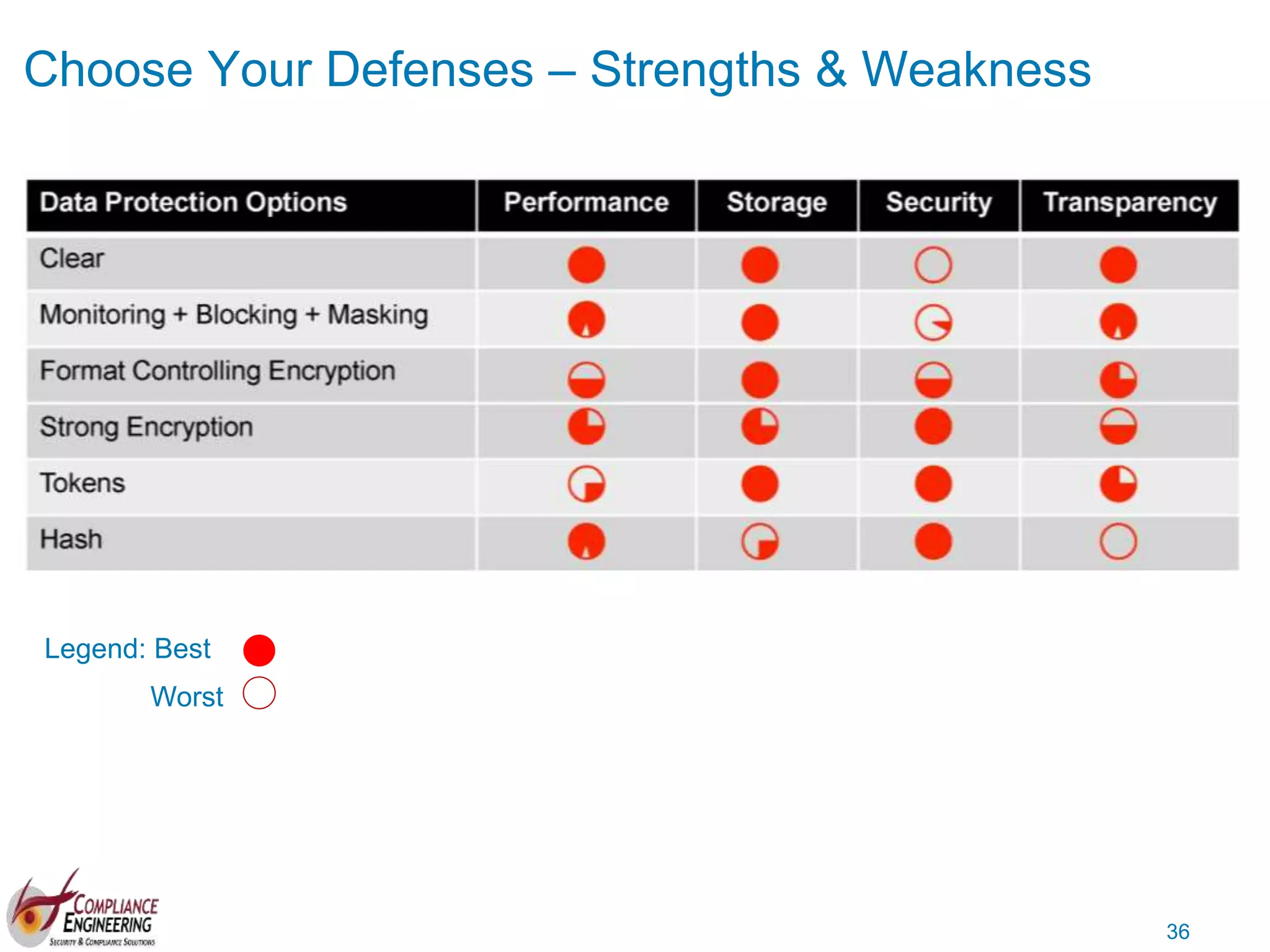
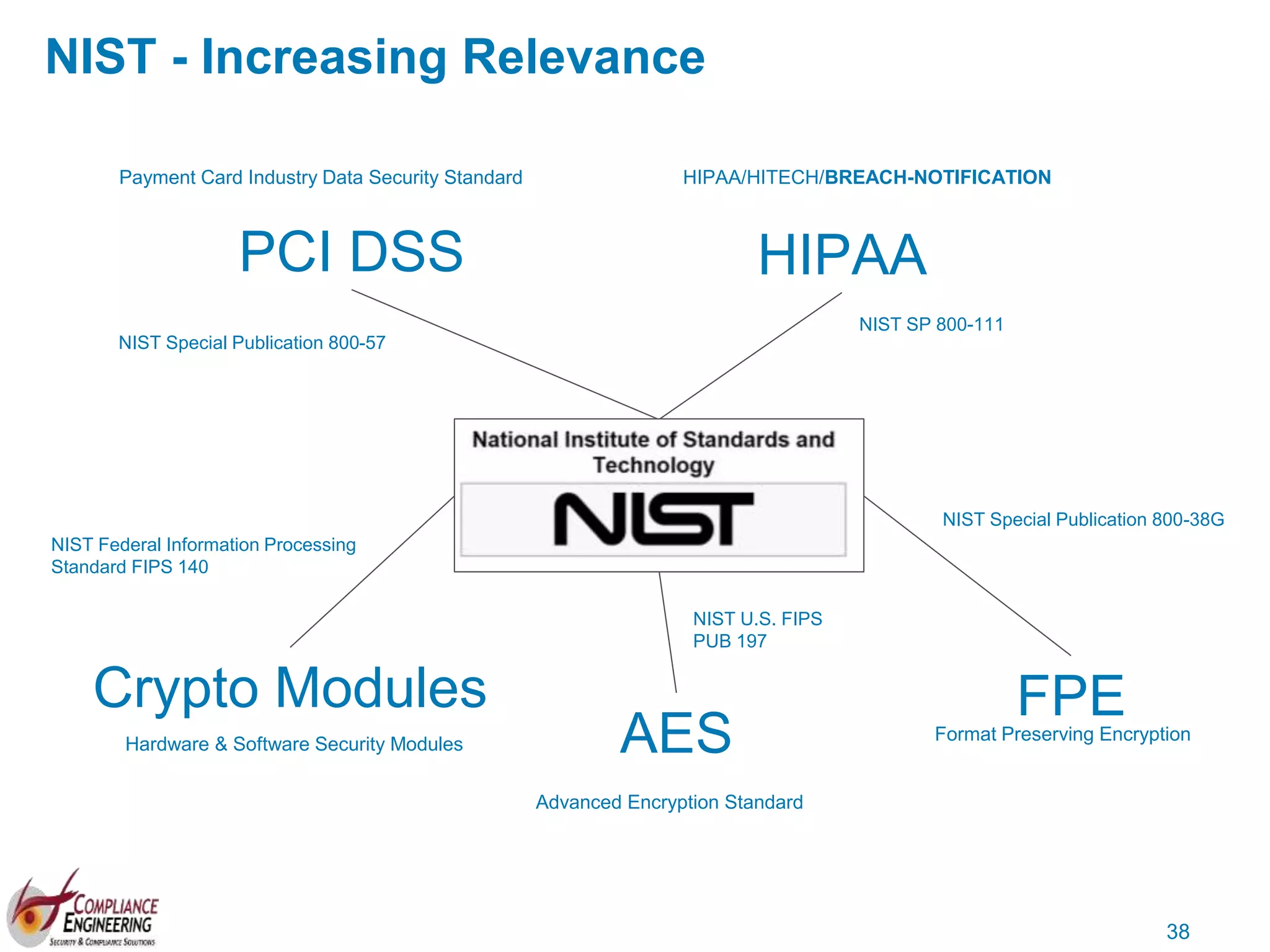
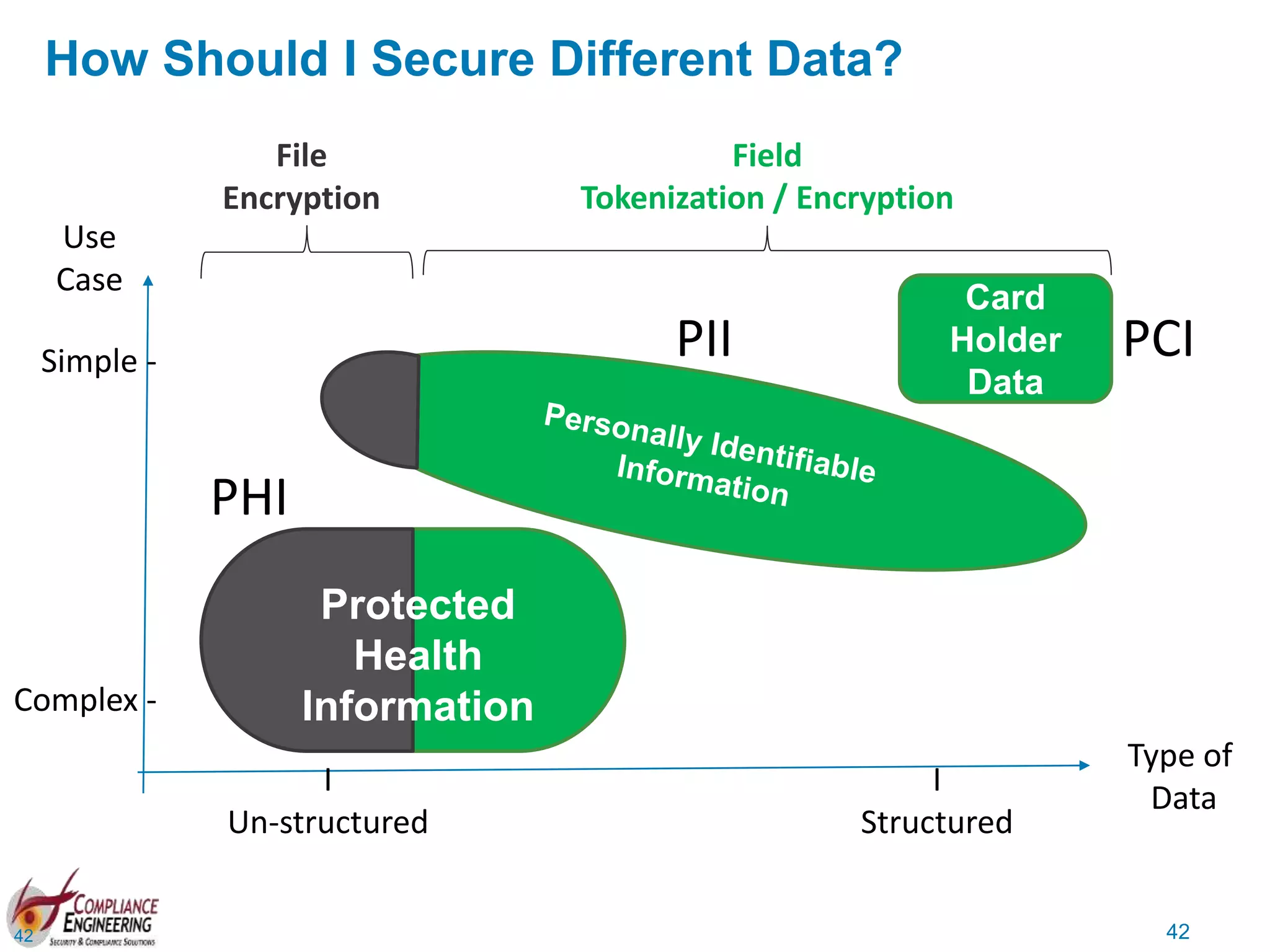
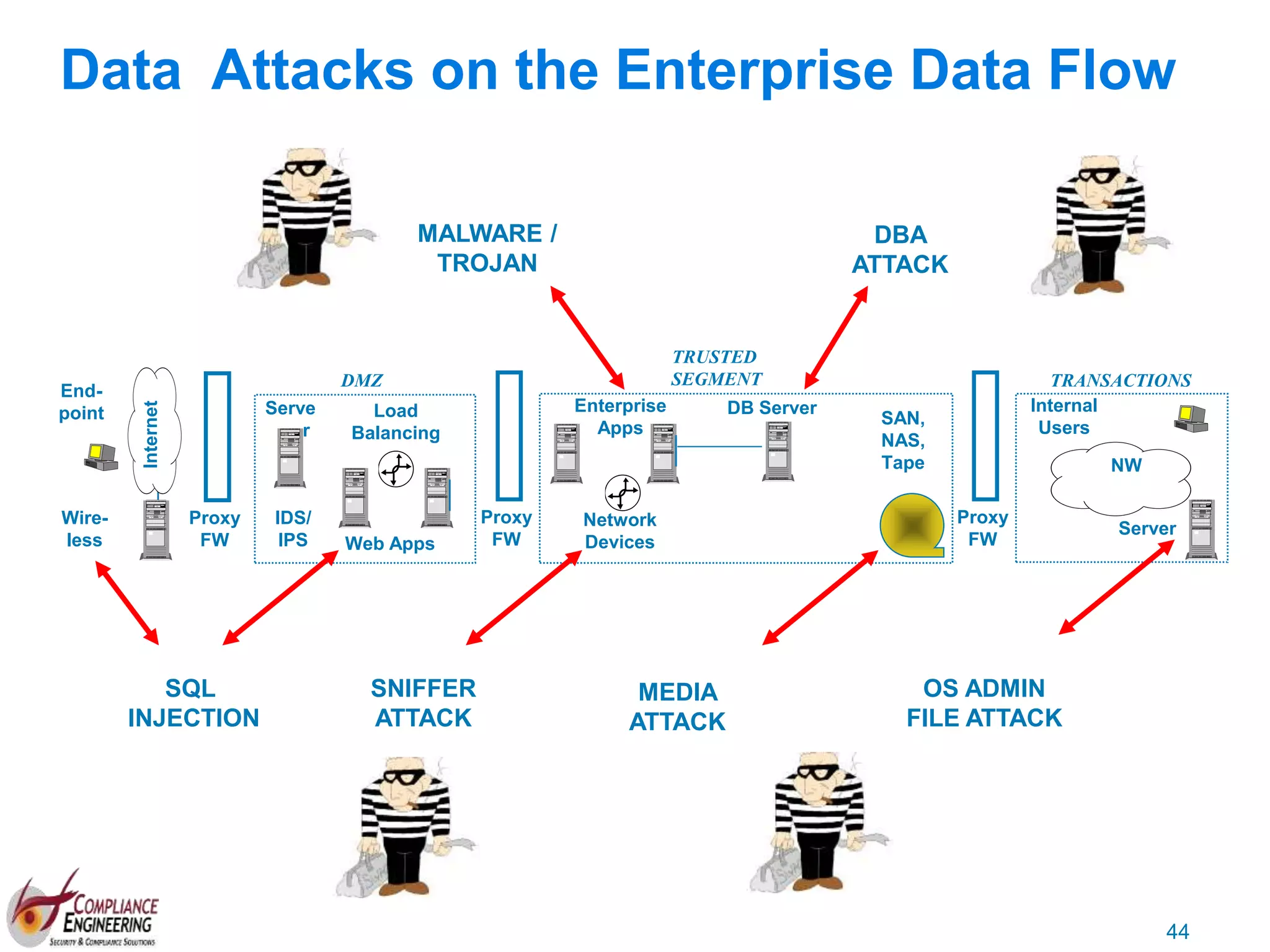
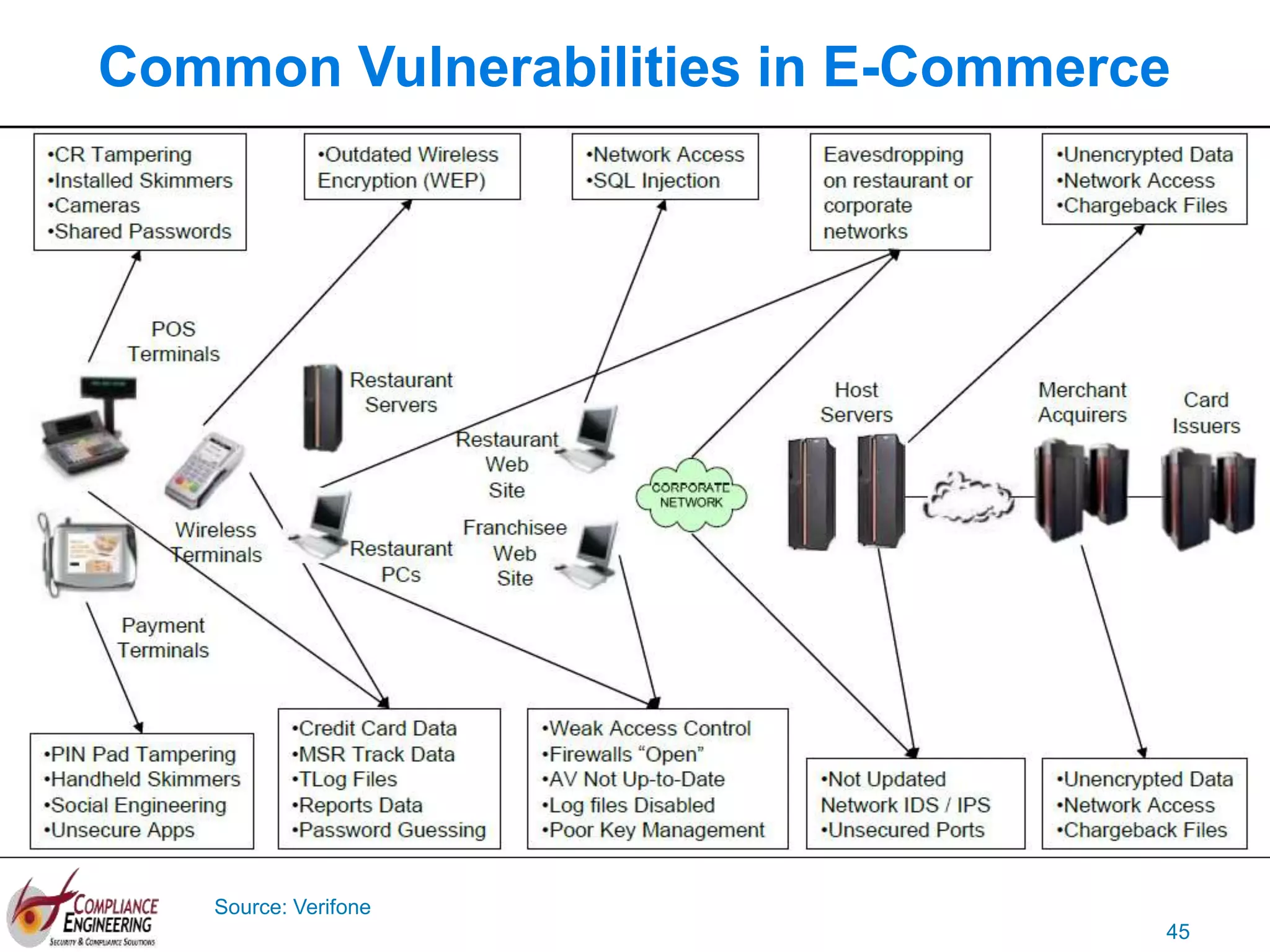
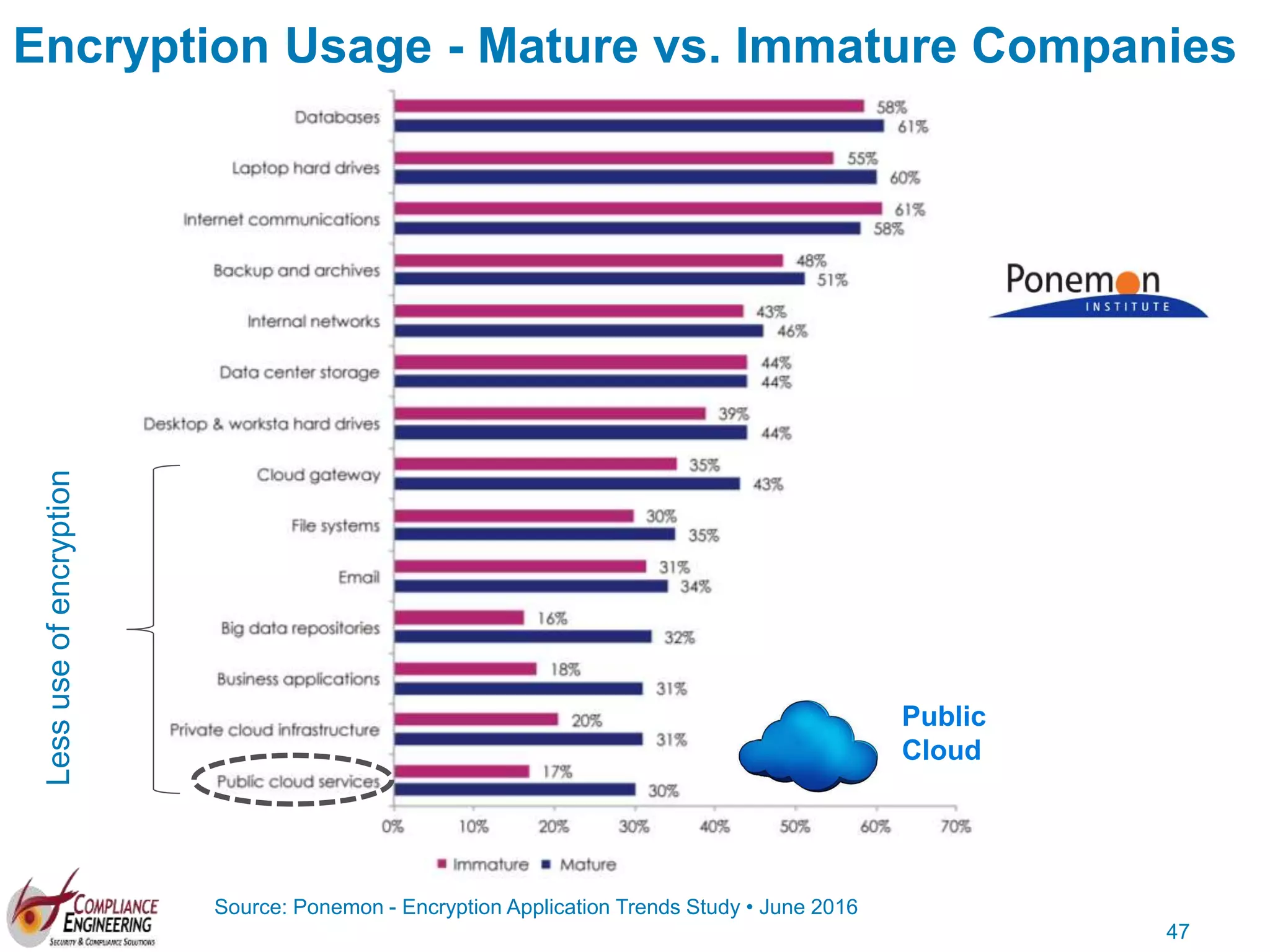
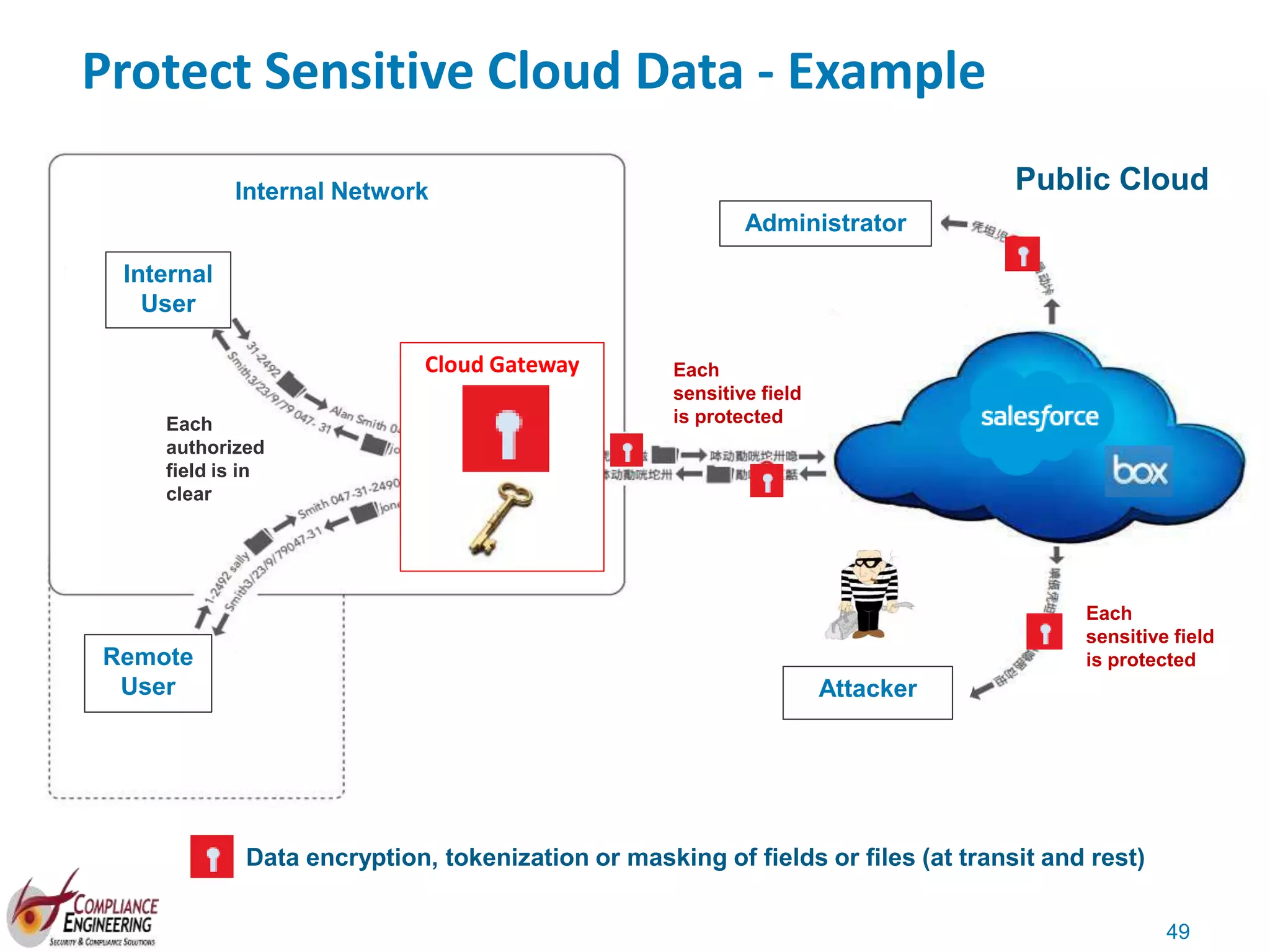
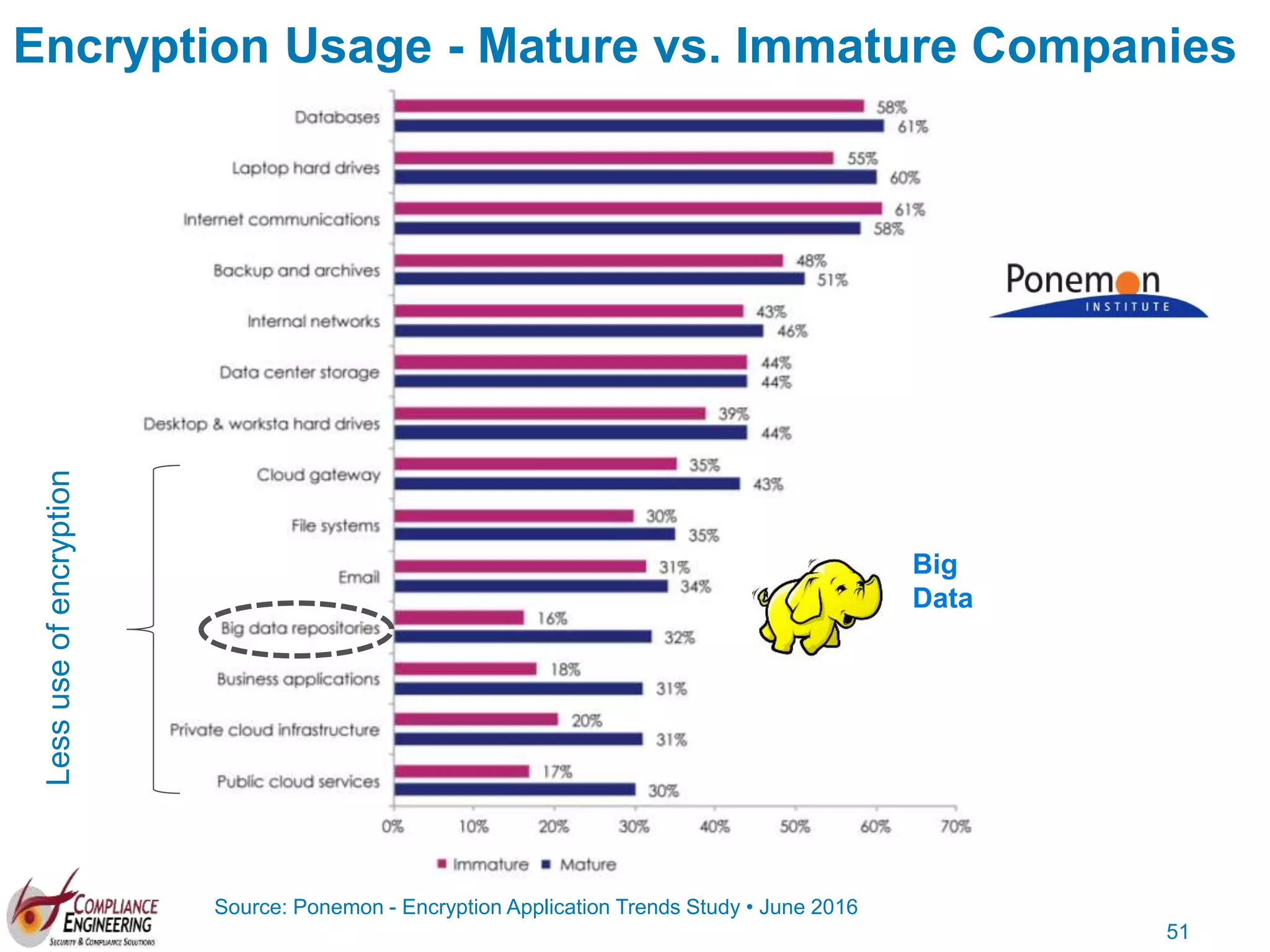
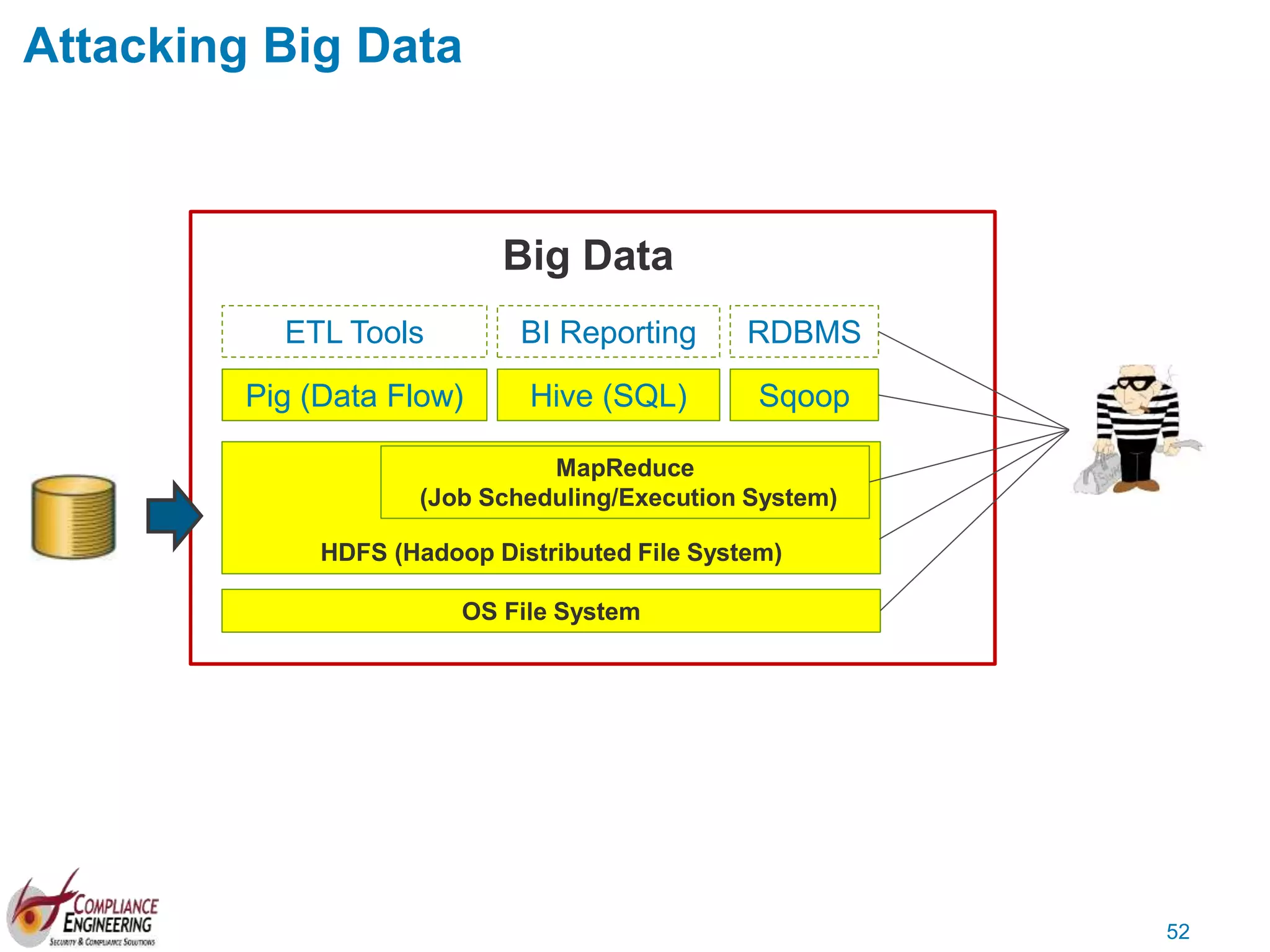
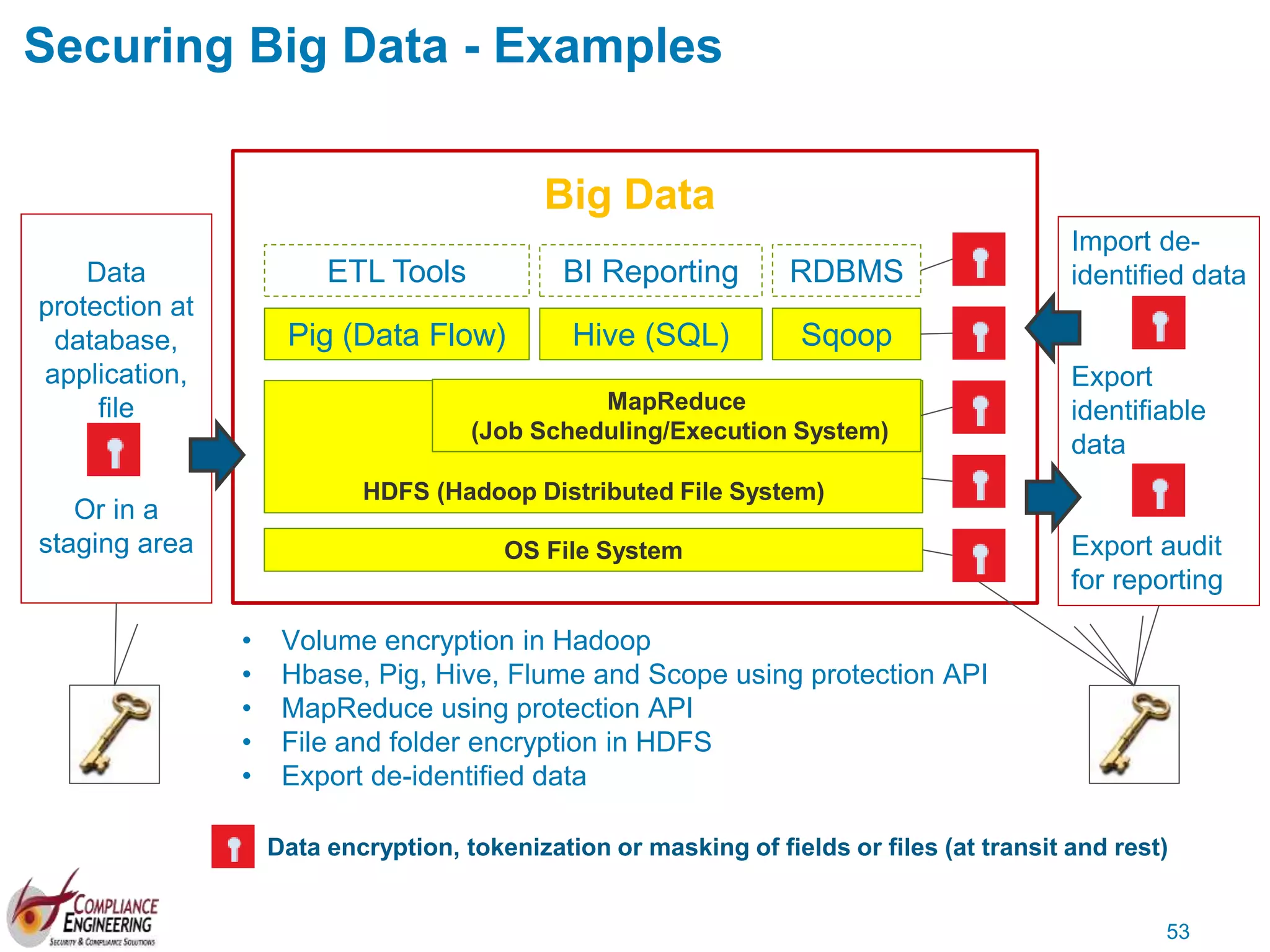
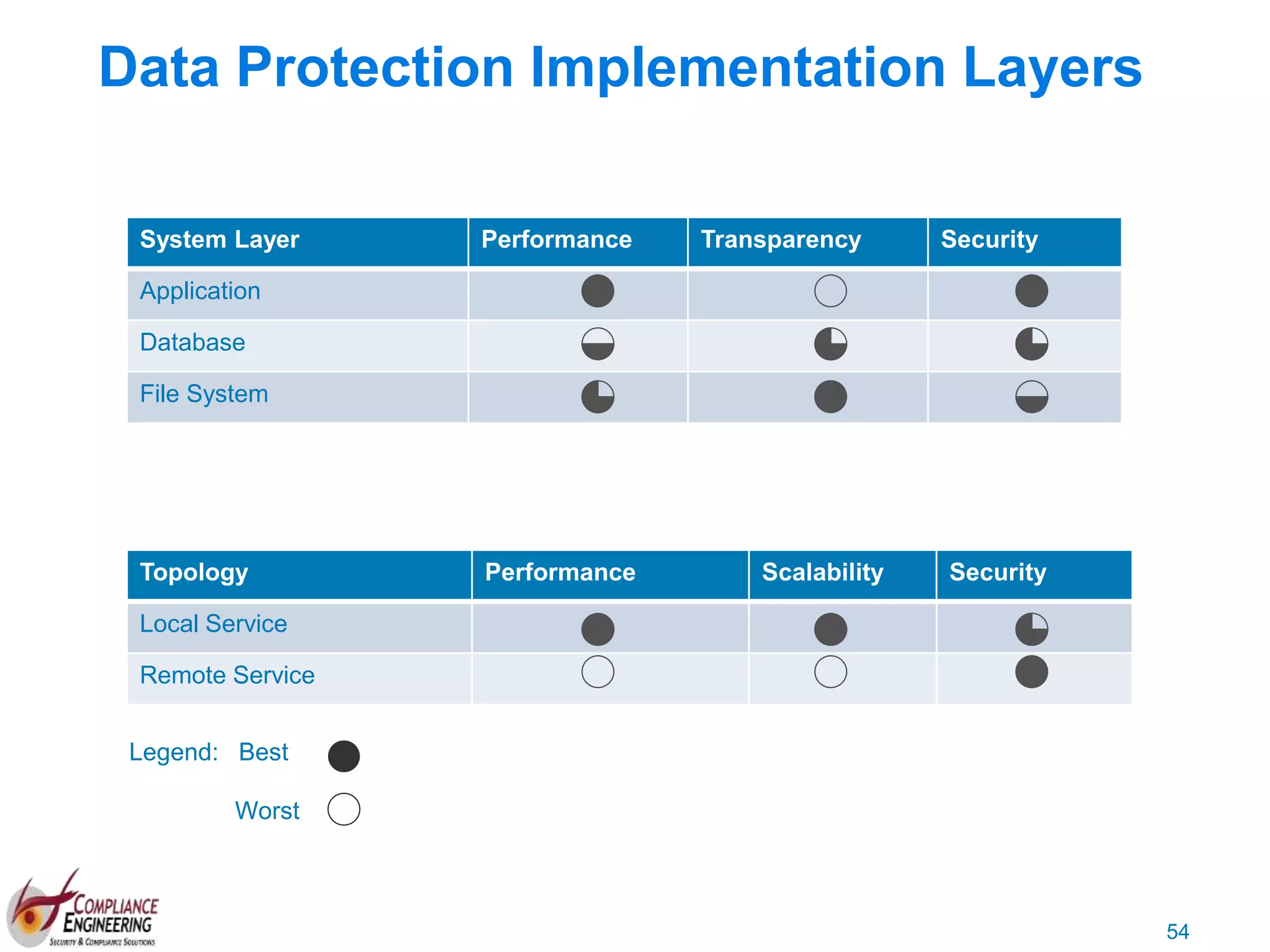
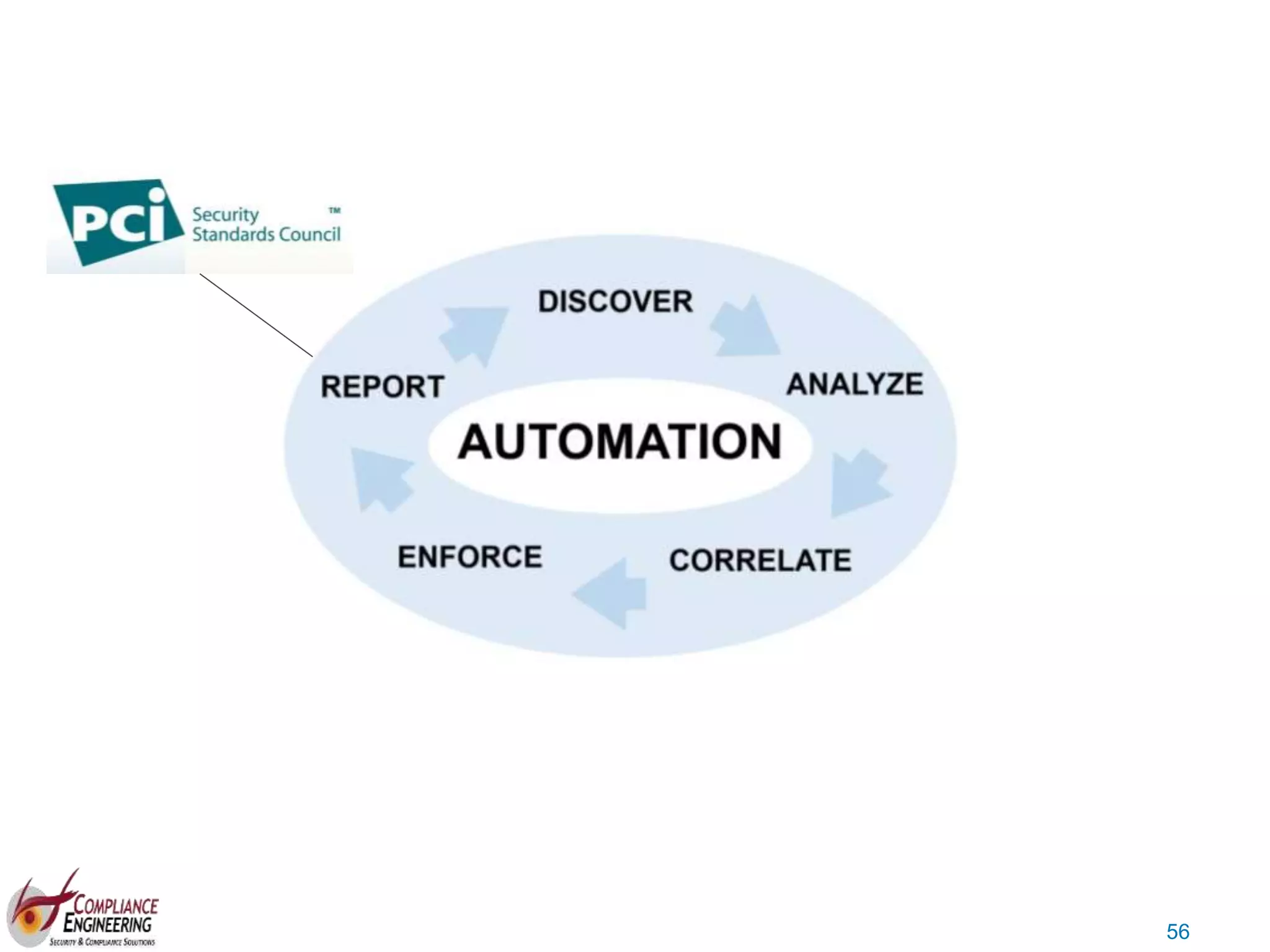
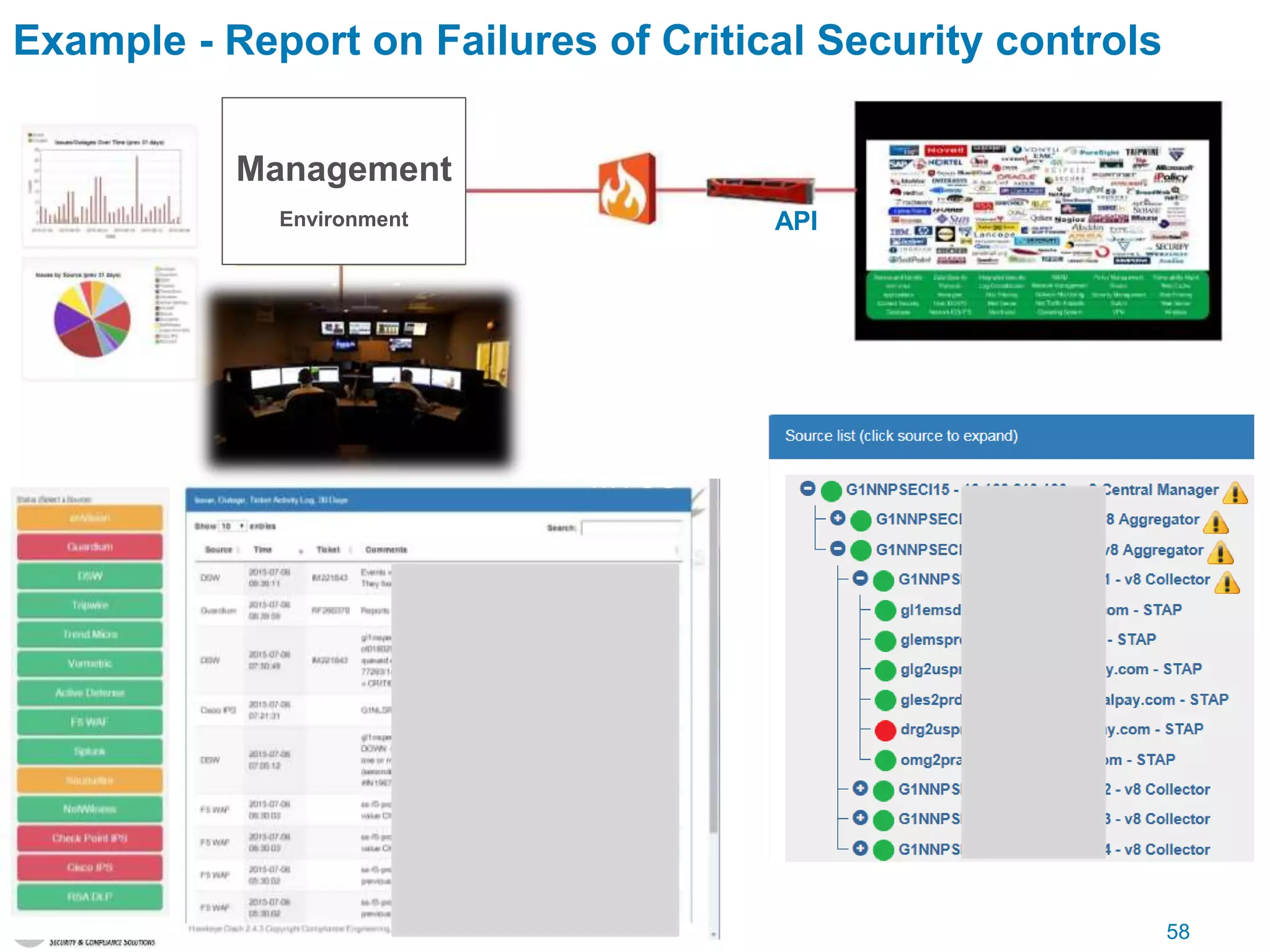
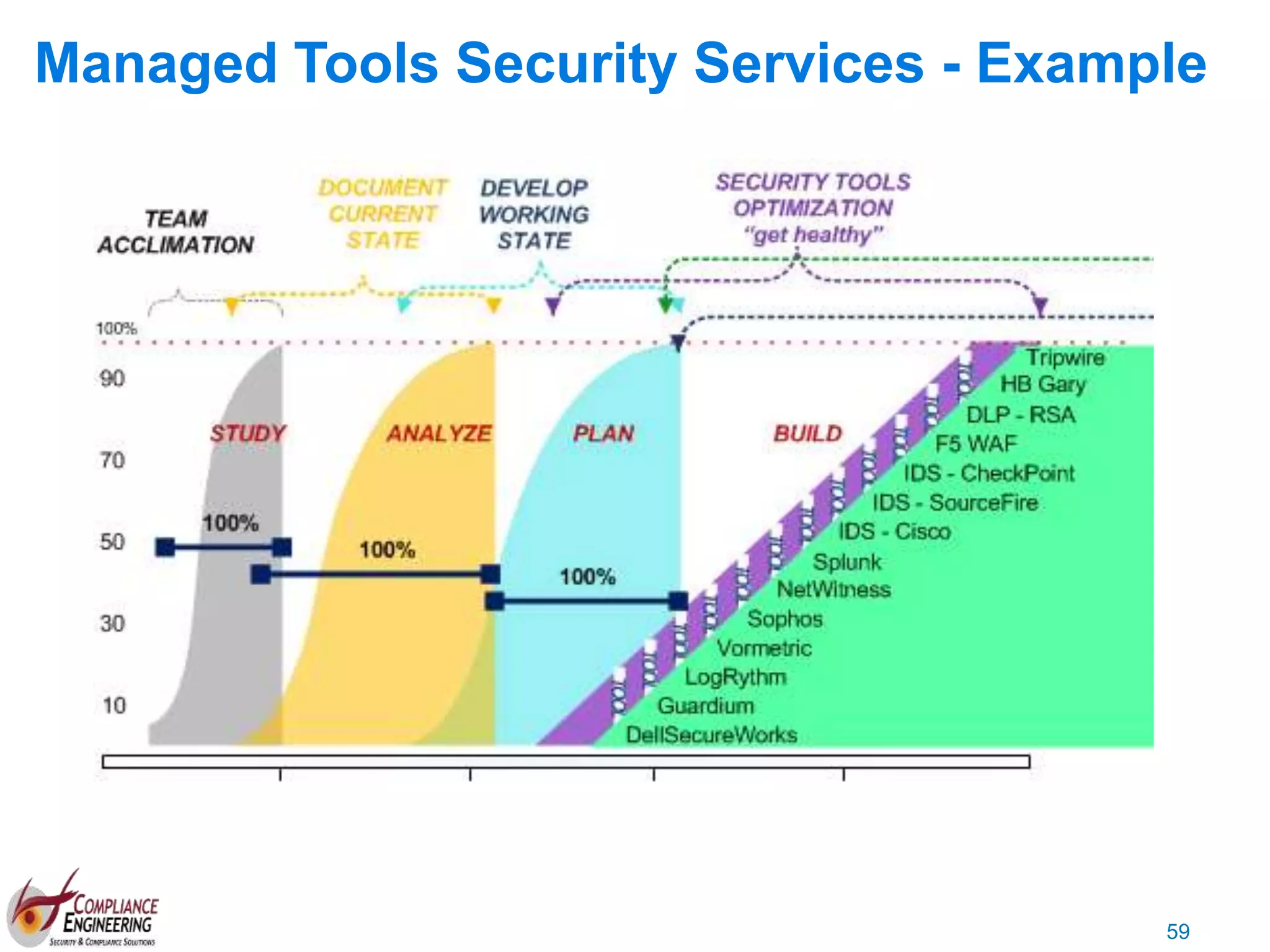
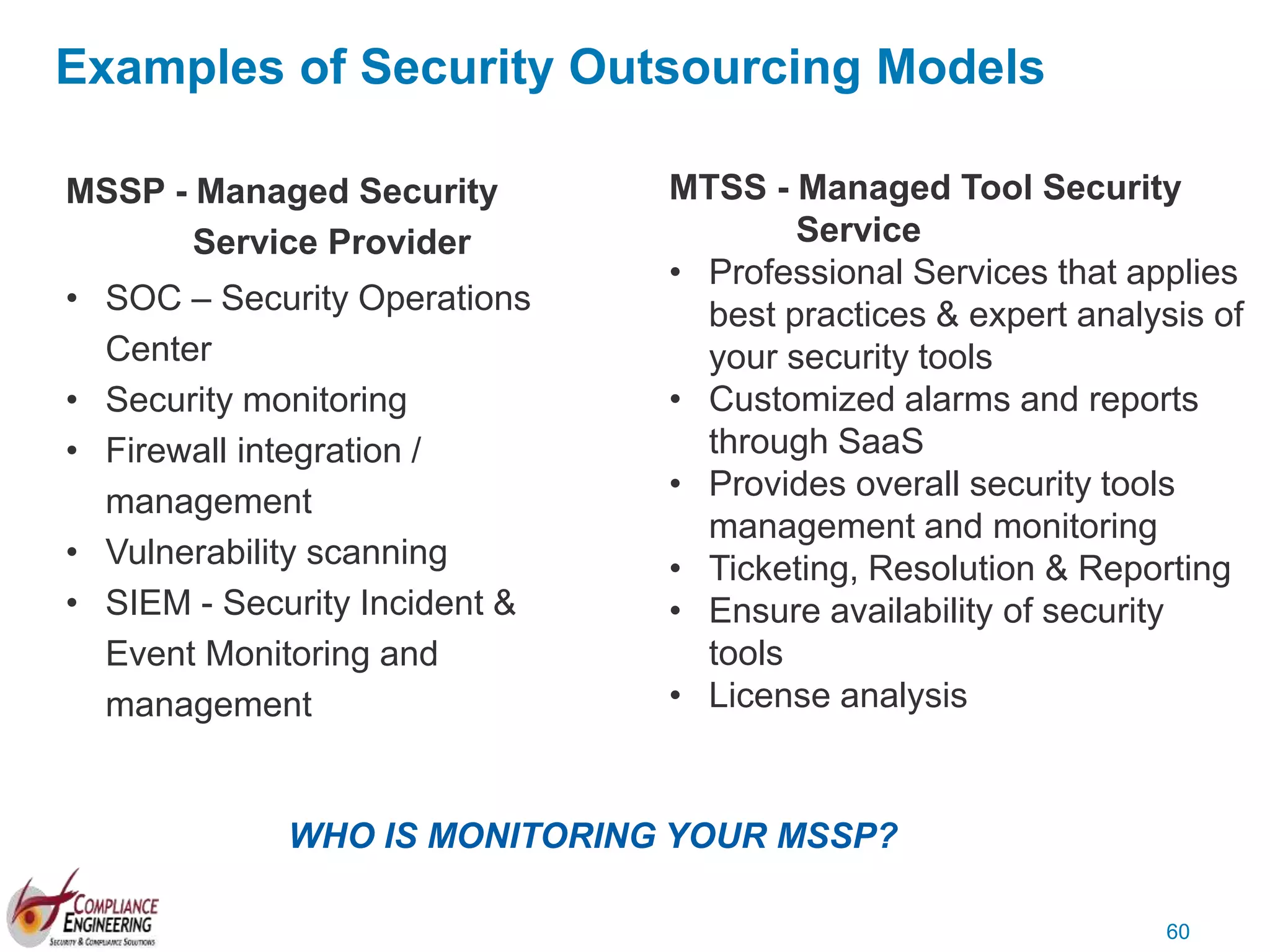
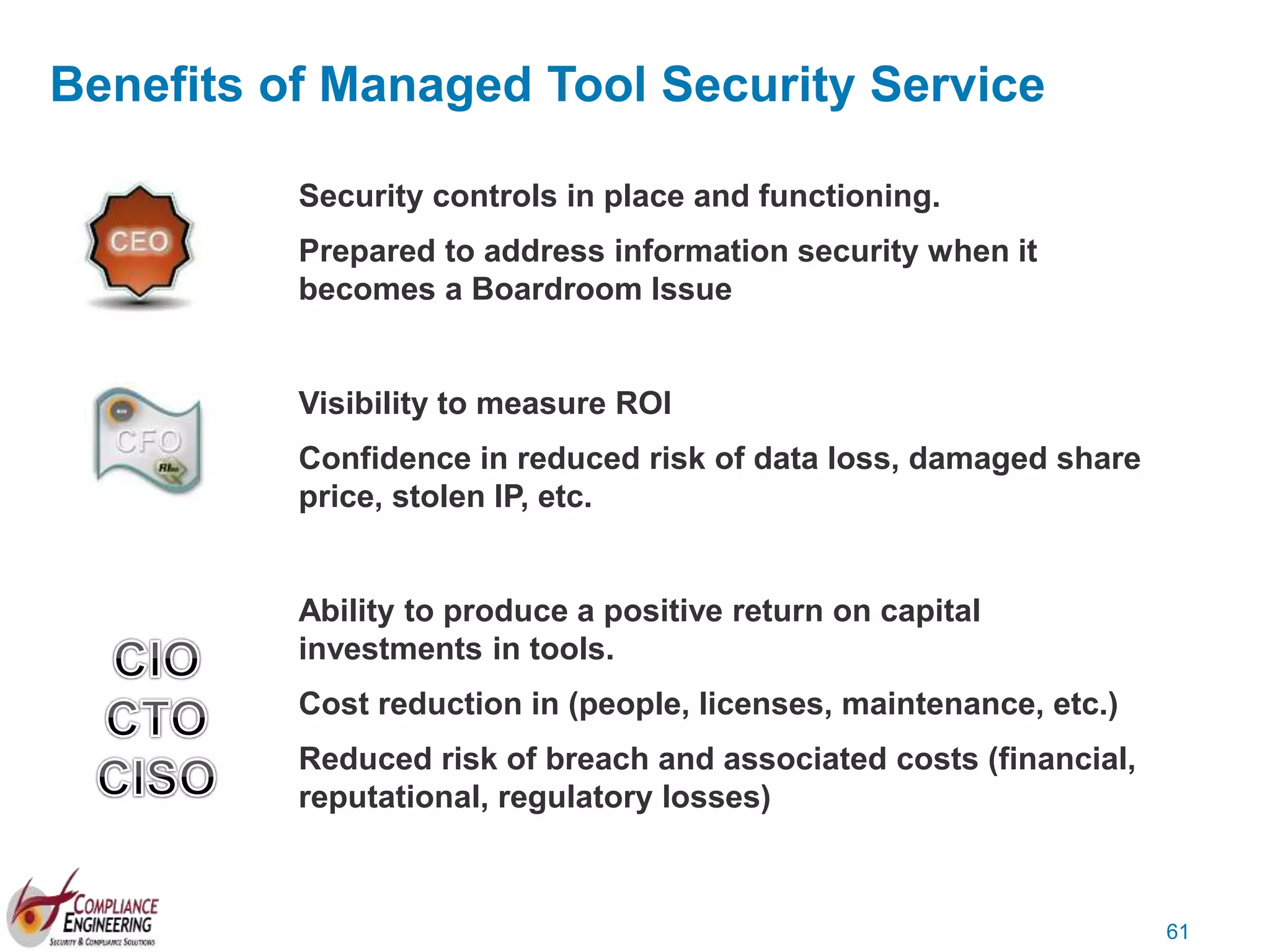
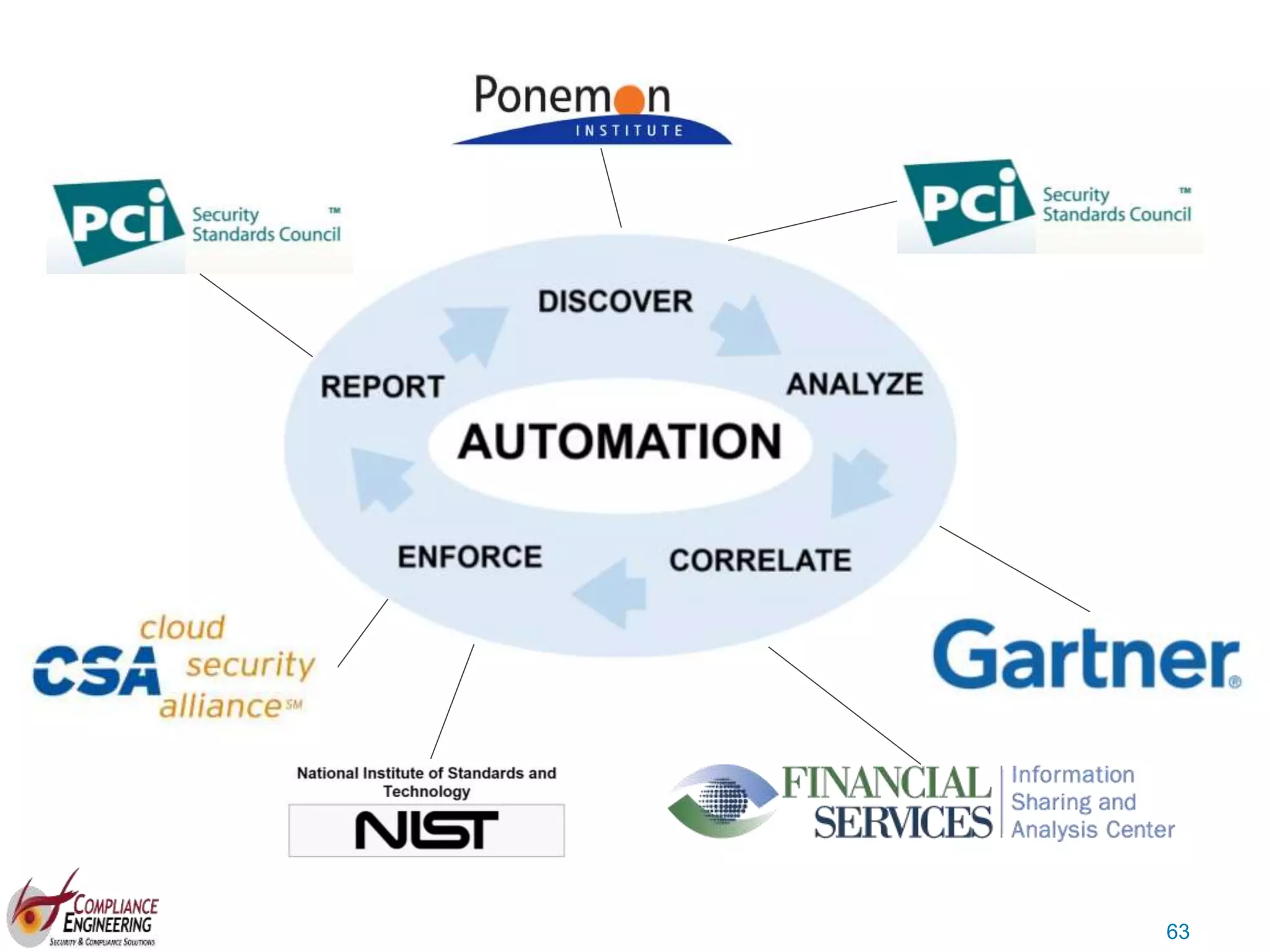
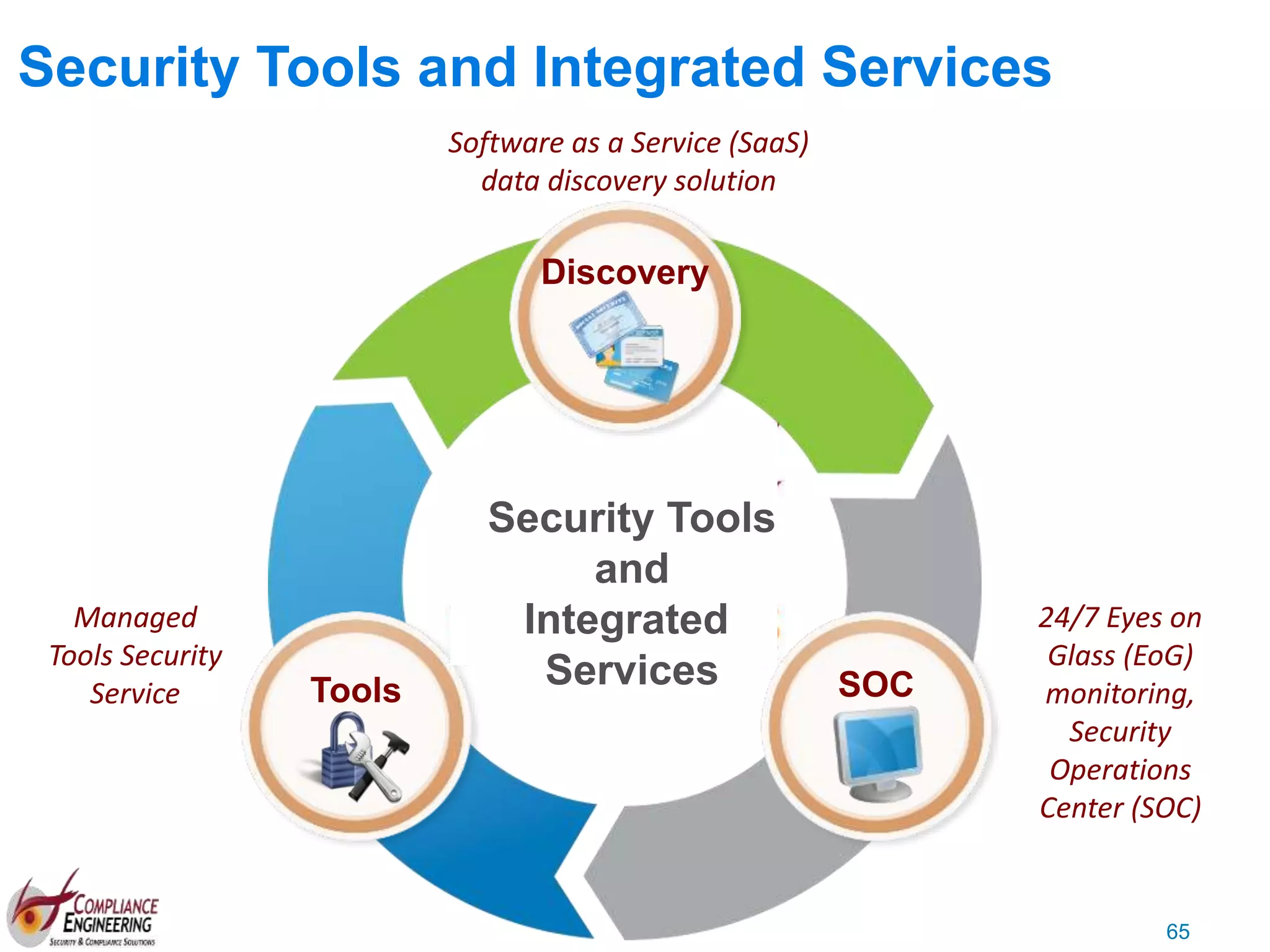
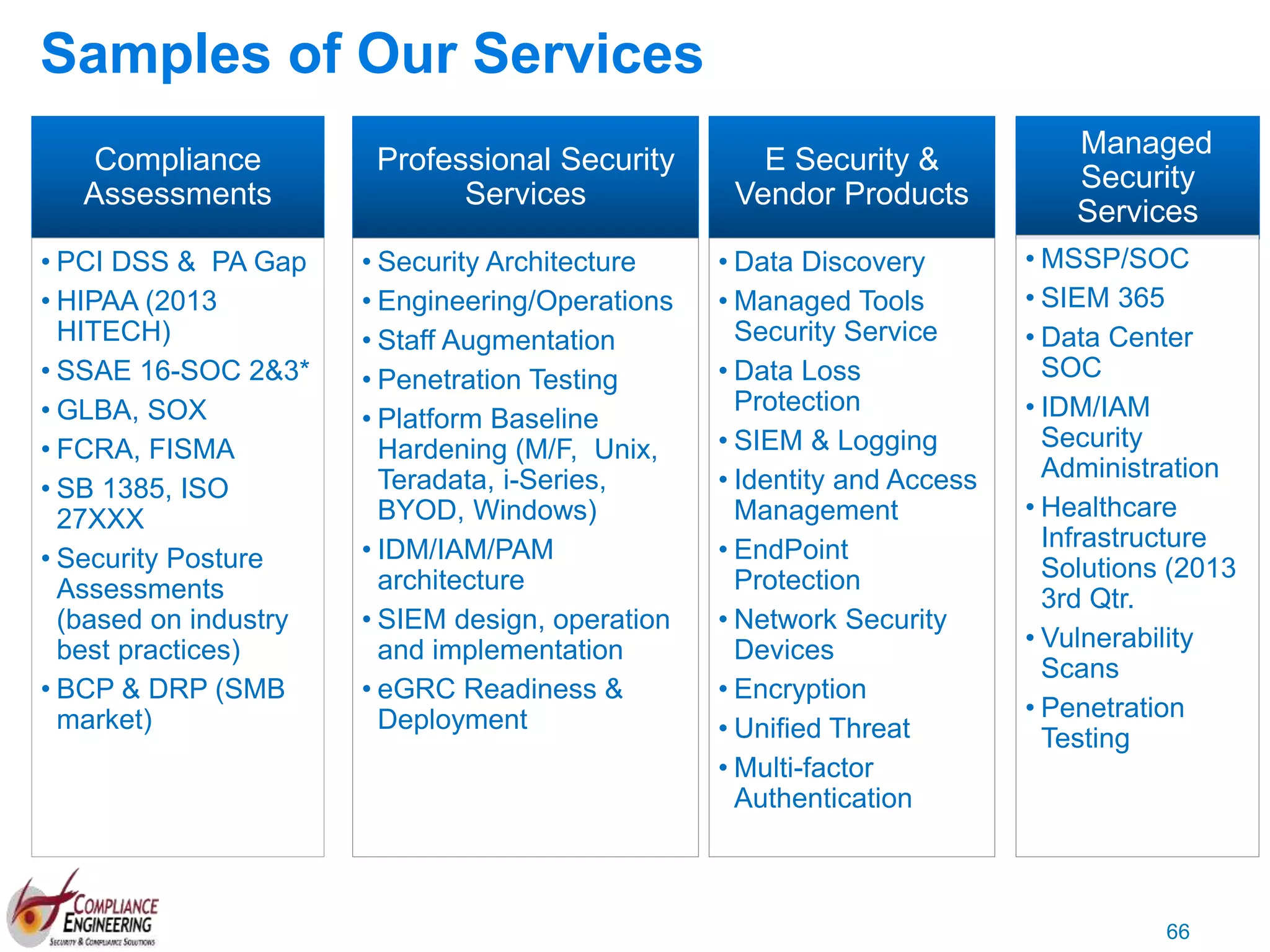
The document discusses data security and compliance, highlighting the importance of identifying and managing sensitive data assets within organizations. It emphasizes the updated requirements of PCI-DSS v3.2, focusing on data discovery, risk assessment, and the necessity for improved detection and response strategies in cybersecurity. It also outlines the challenges organizations face in maintaining compliance and the shifting landscape towards a more proactive approach in data protection.