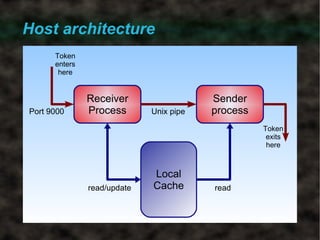
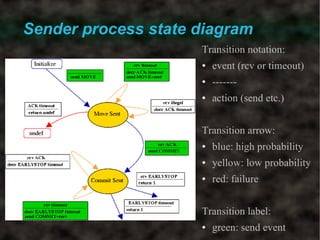
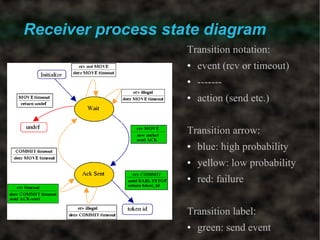
The document discusses a secure token passing protocol implemented at the application level, focusing on its requirements and operational aspects, particularly using UDP datagrams. It emphasizes the importance of ensuring token authenticity, preventing duplication, and maintaining performance stability within a full mesh topology for token circulation. Experimental validation of the protocol demonstrated its effectiveness in both real and simulated environments, confirming its robustness against token loss and network failures.