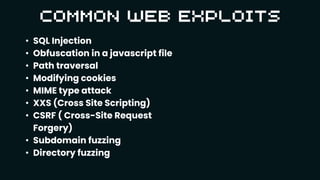
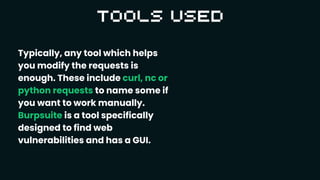
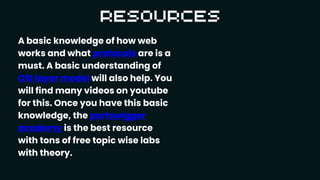
Capture the Flag (CTF) competitions are educational exercises in information security, where participants solve various tasks to exploit vulnerabilities in software and hardware, earning points by submitting 'flags.' CTFs cover different categories like web exploitation, forensics, reversing, pwn, cryptography, and OSINT, each requiring specific skills and tools. The challenges aim to enhance participants' knowledge of secure coding practices, scripting, and essential tech skills while fostering a global community of learners.