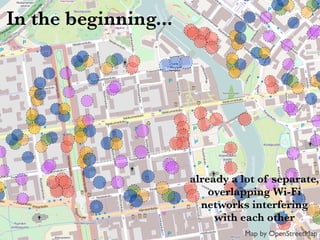
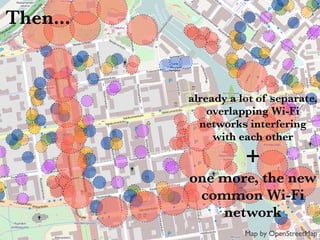
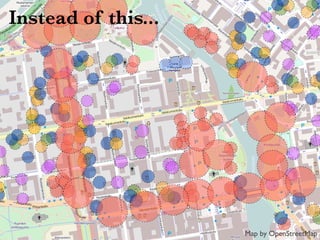
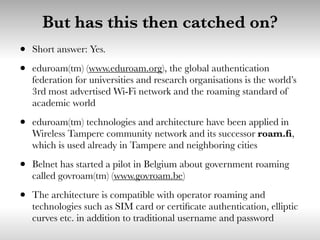
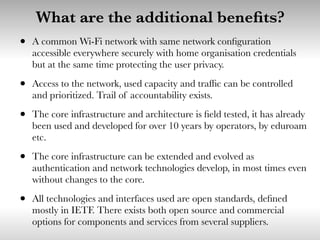
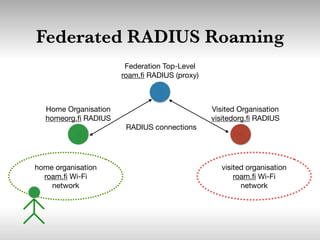
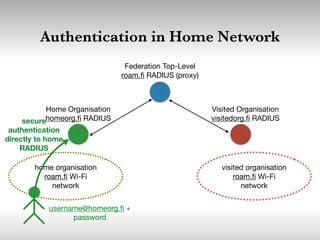
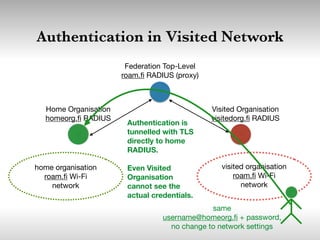
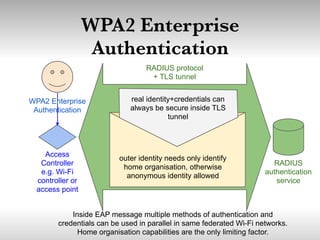
This document discusses building cooperative Wi-Fi networks through federated authentication. It outlines two options: an "easy" option of using a common network name without encryption or authentication, and a "proper" option of using WPA2 Enterprise encryption and authentication across networks. The "proper" option has been successfully implemented in networks like eduroam and roam.fi and provides benefits like secure roaming access and network control while protecting user privacy. Technical details of federated RADIUS authentication are also covered.