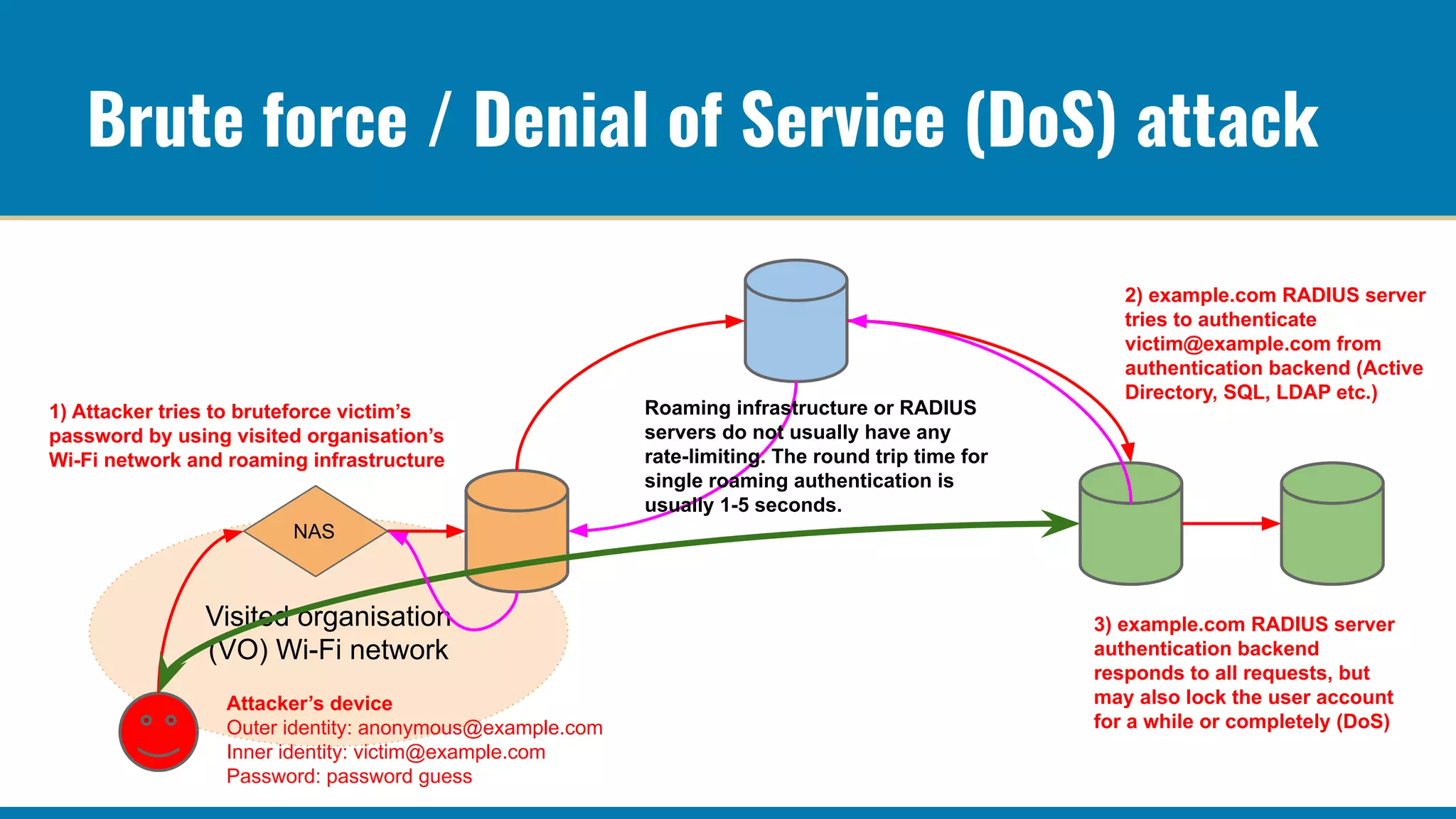
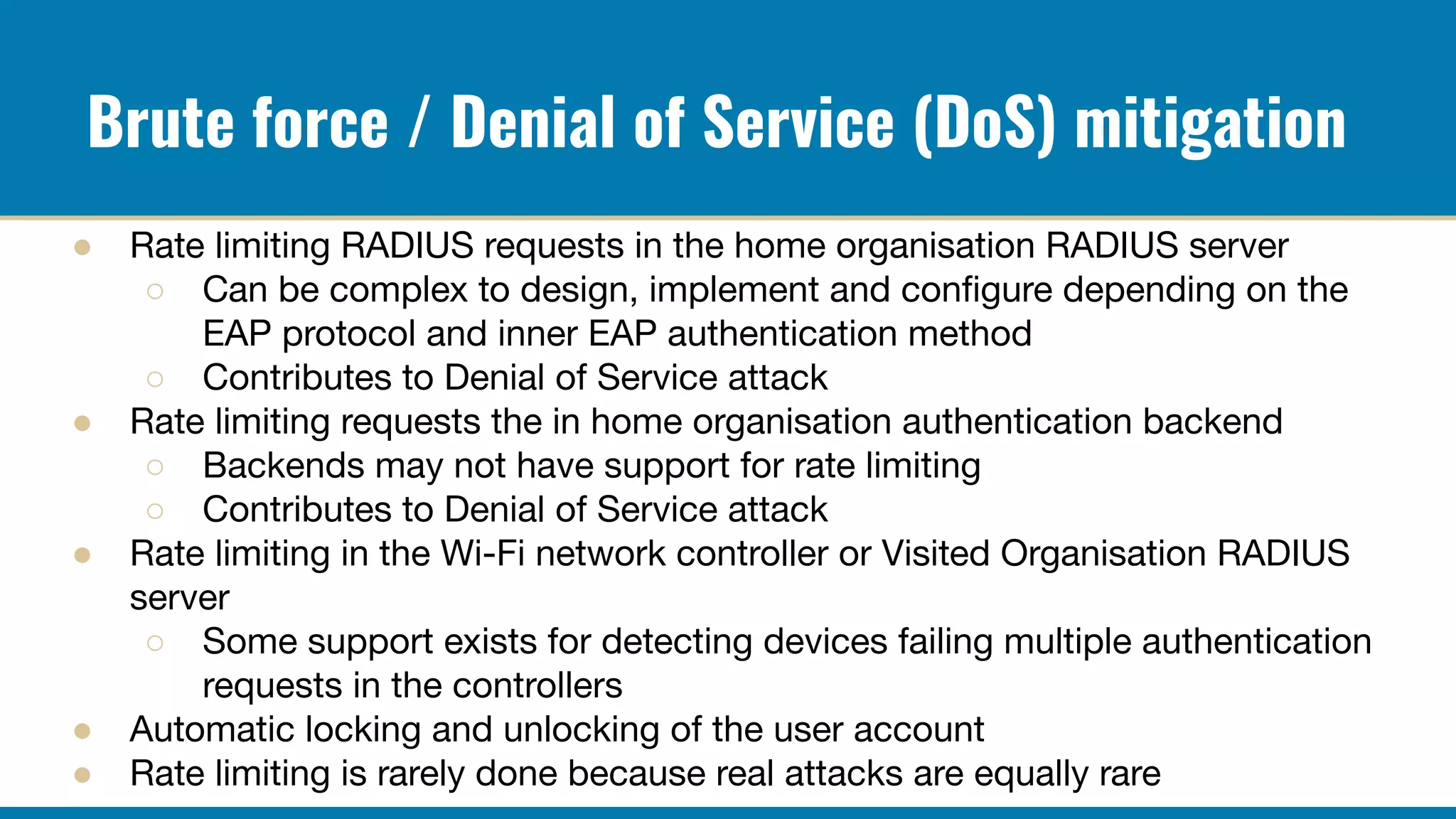
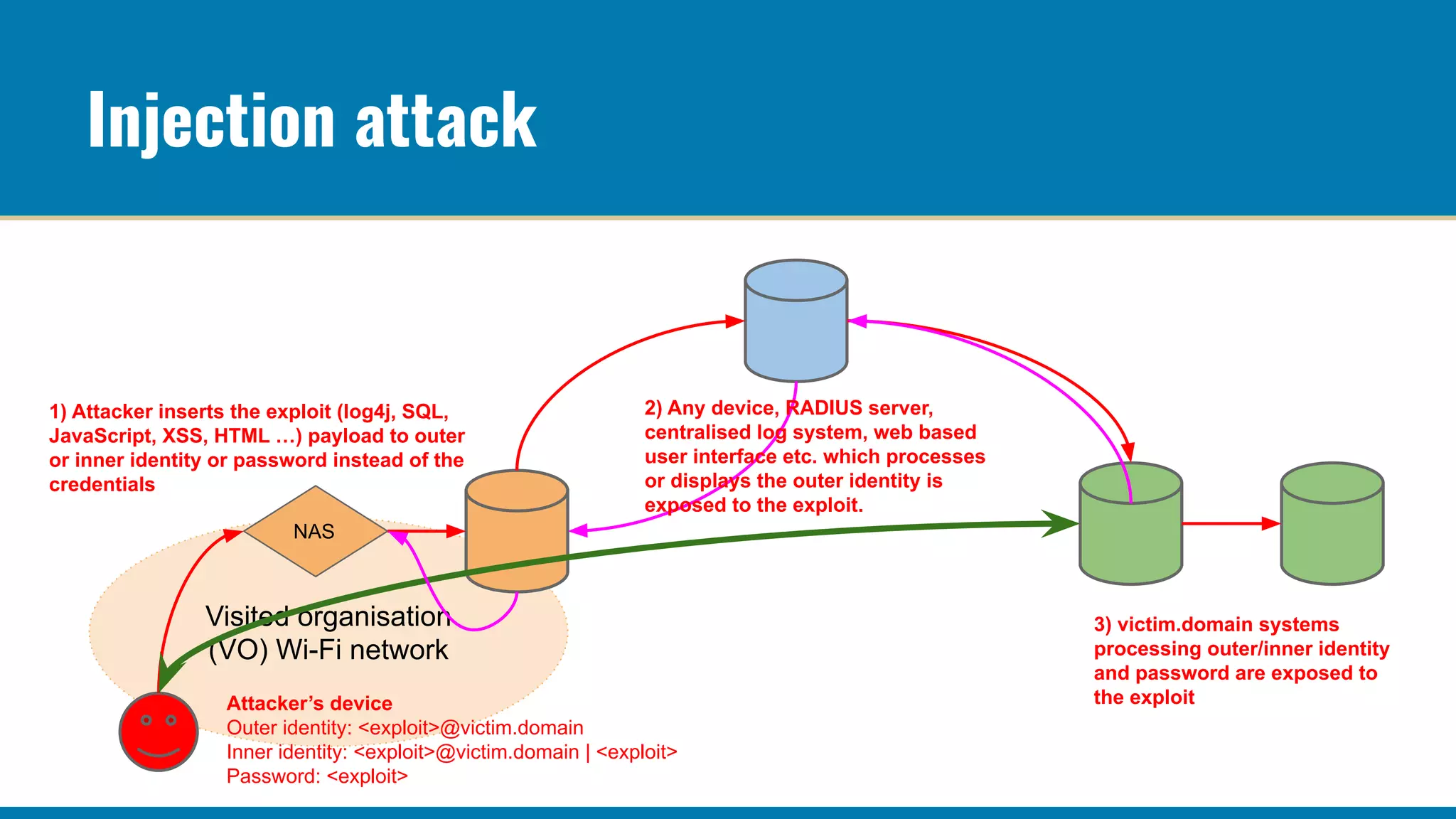
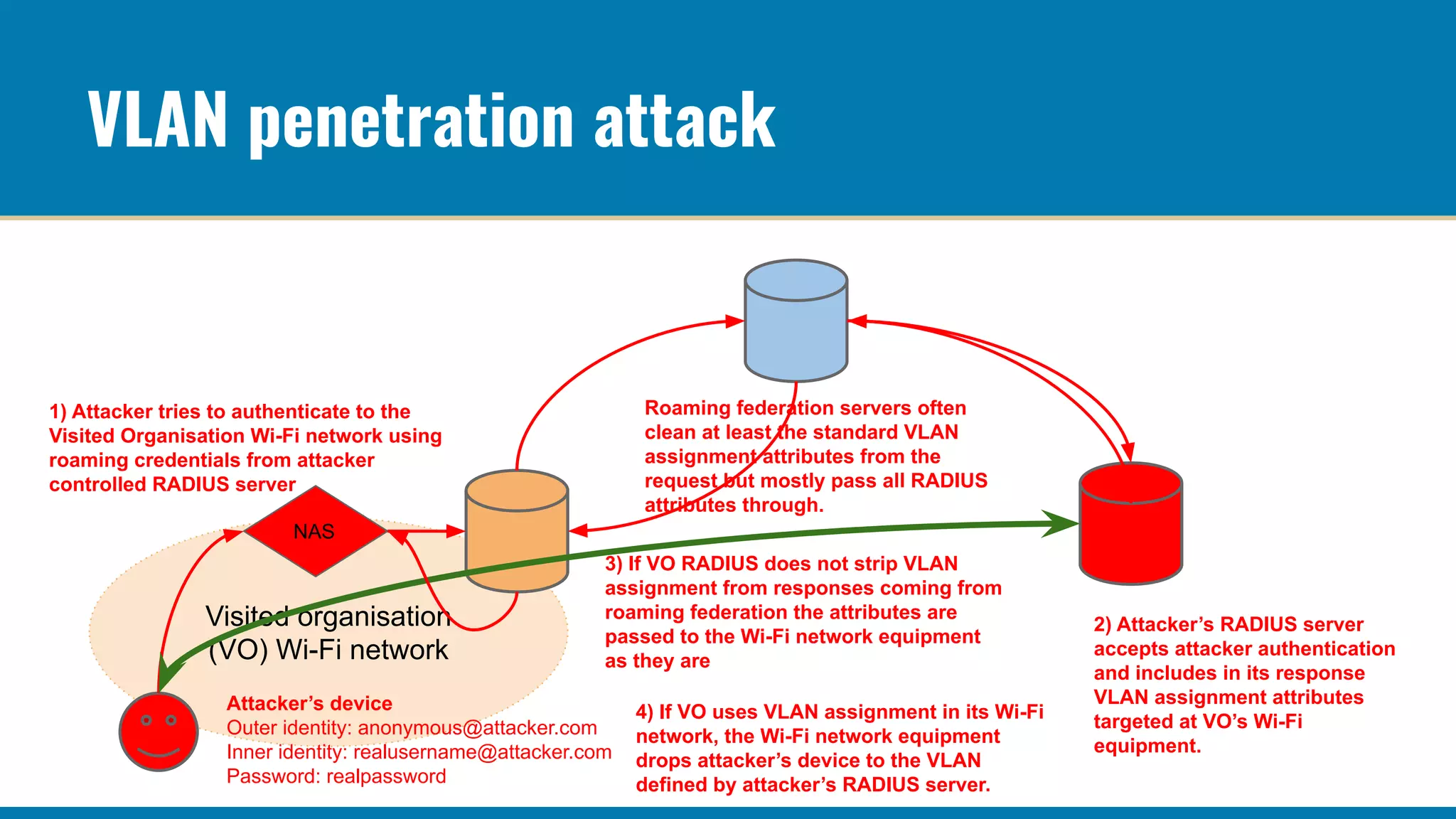
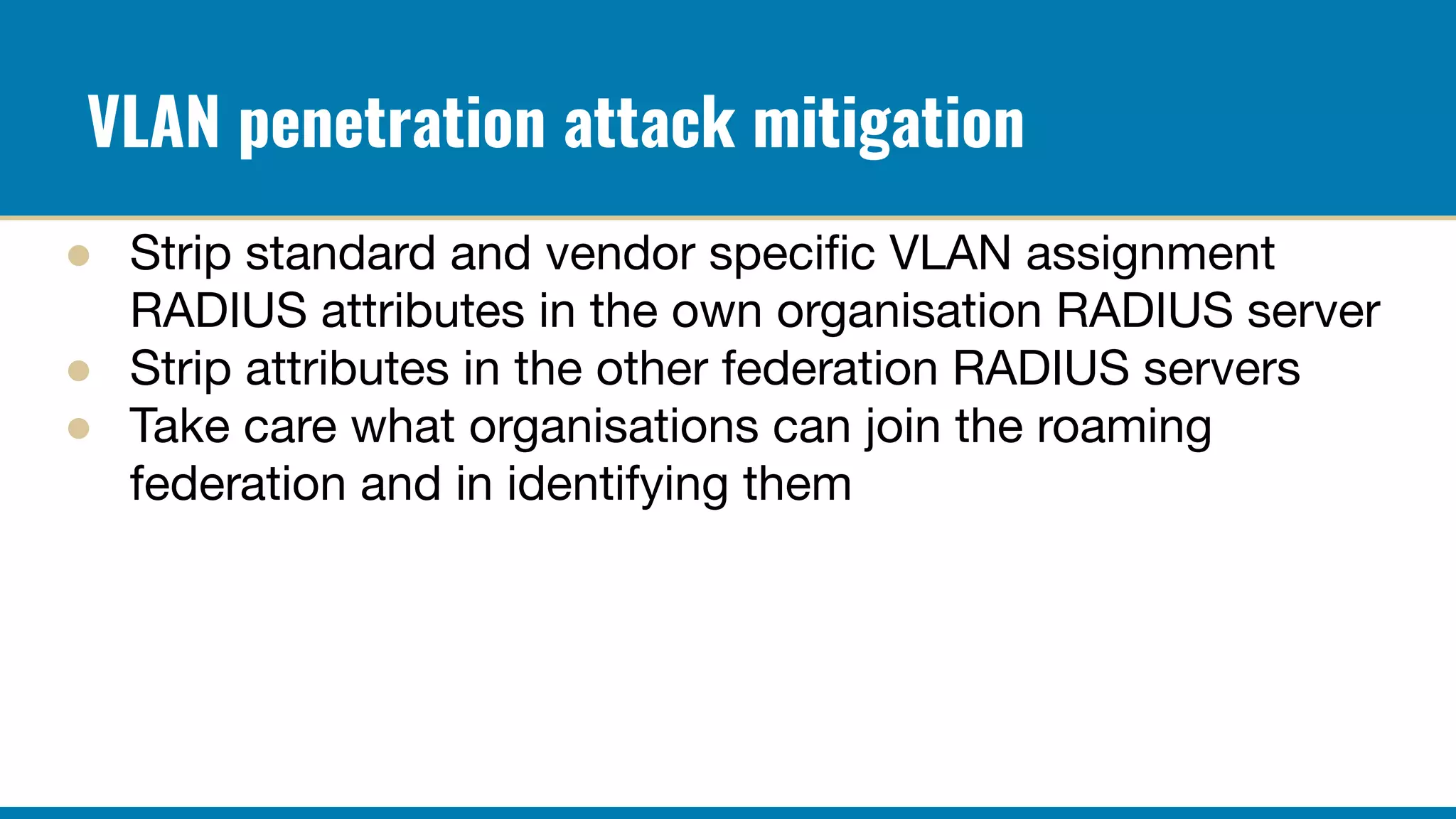
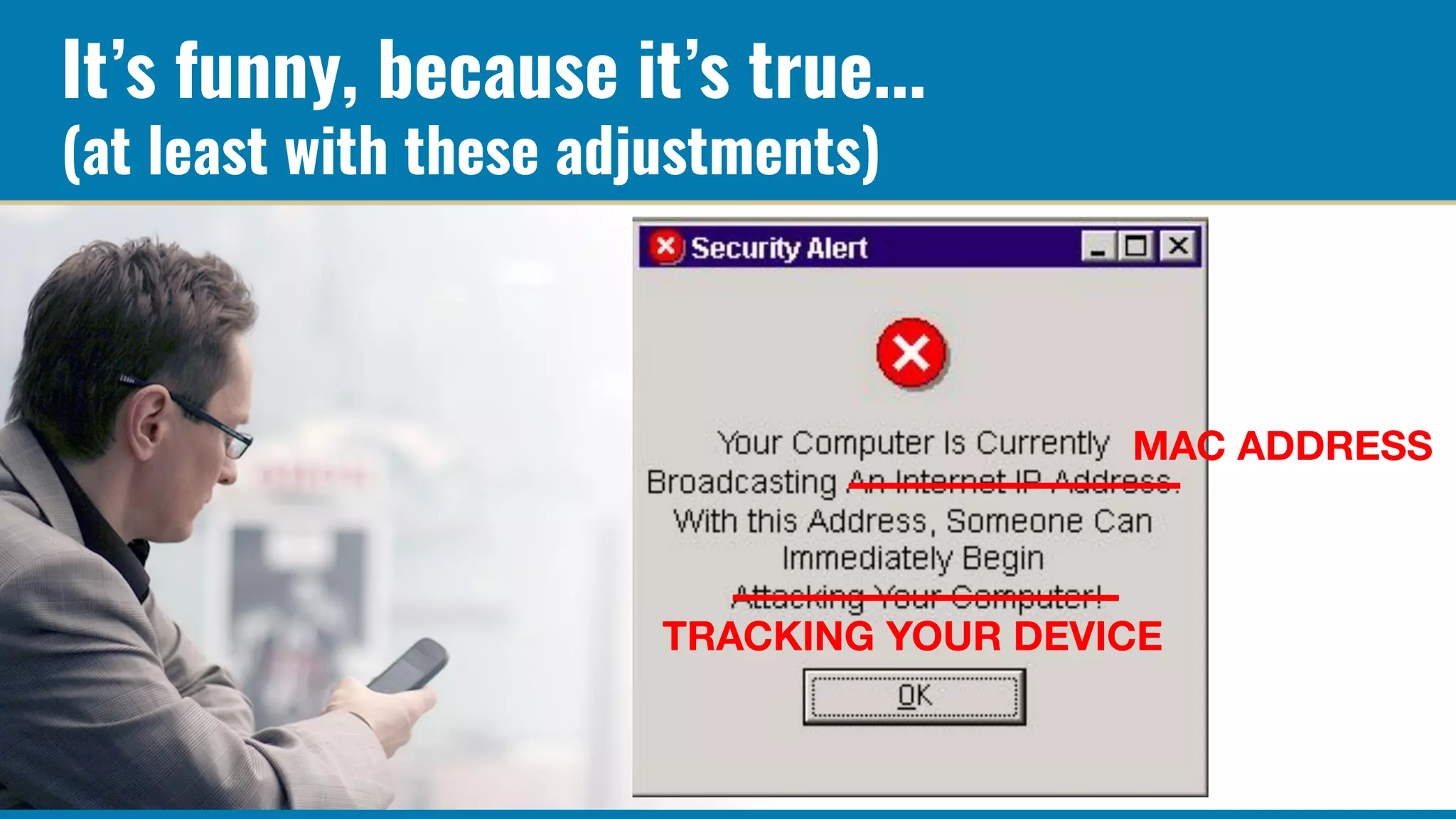
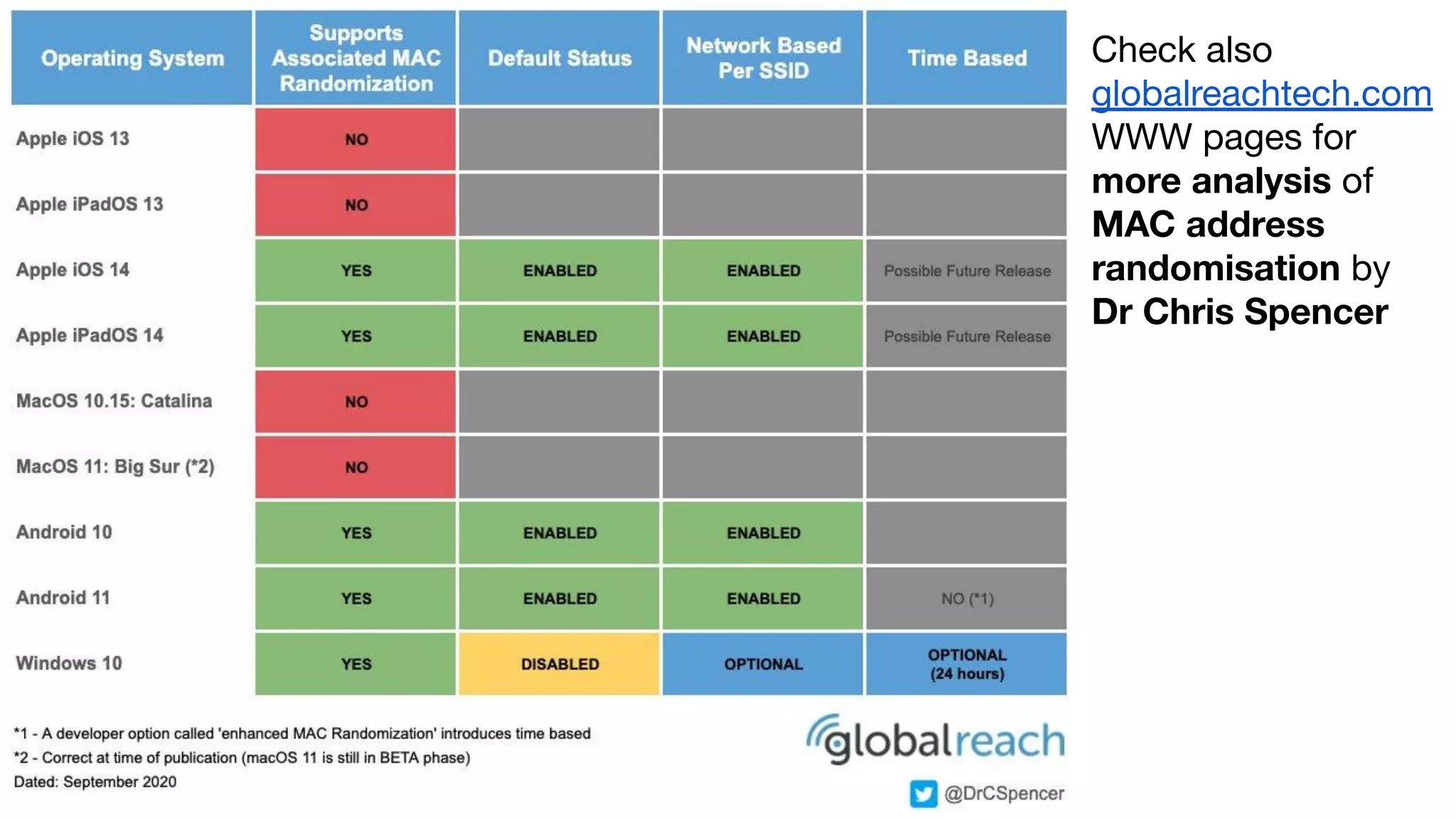
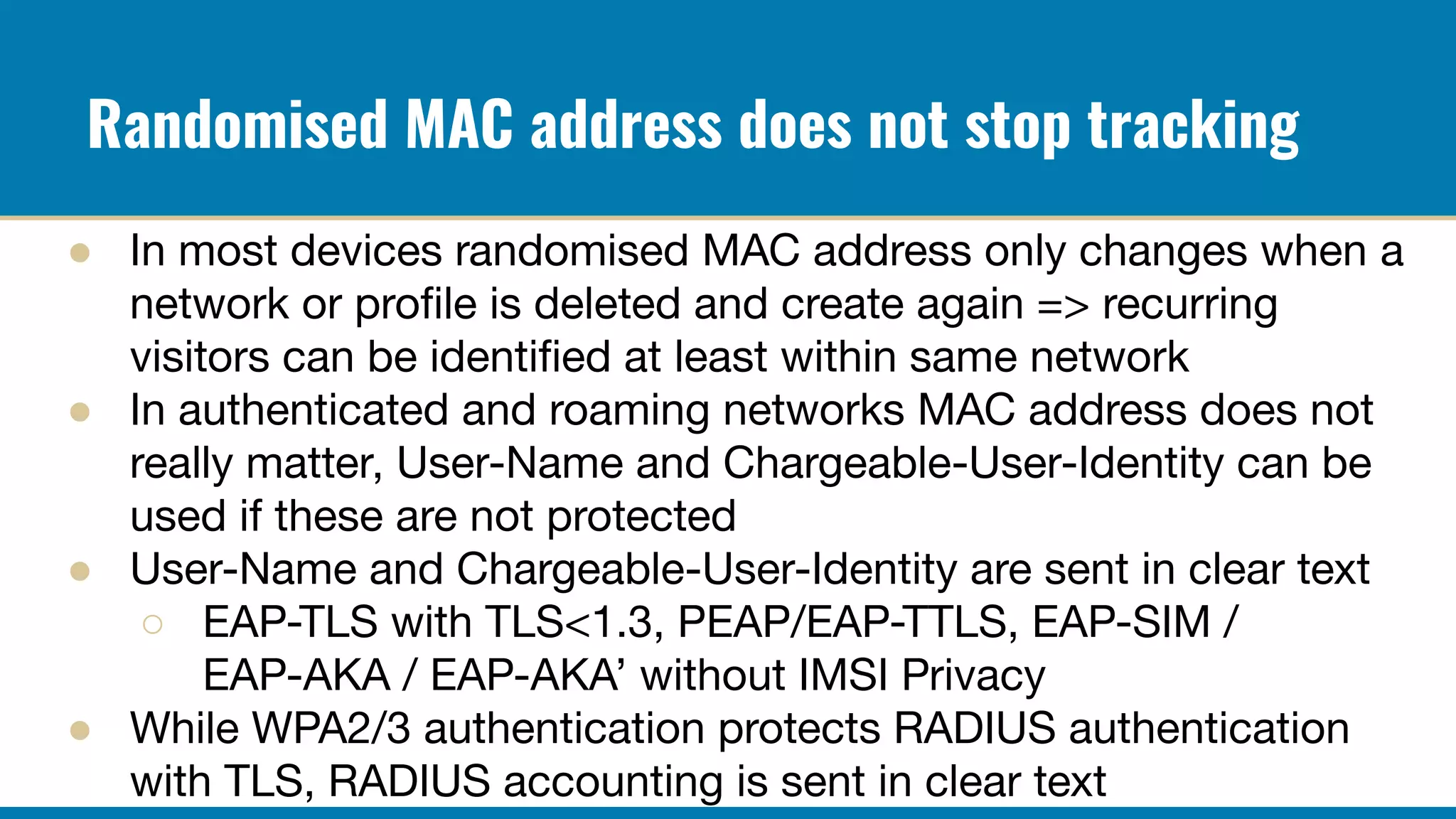
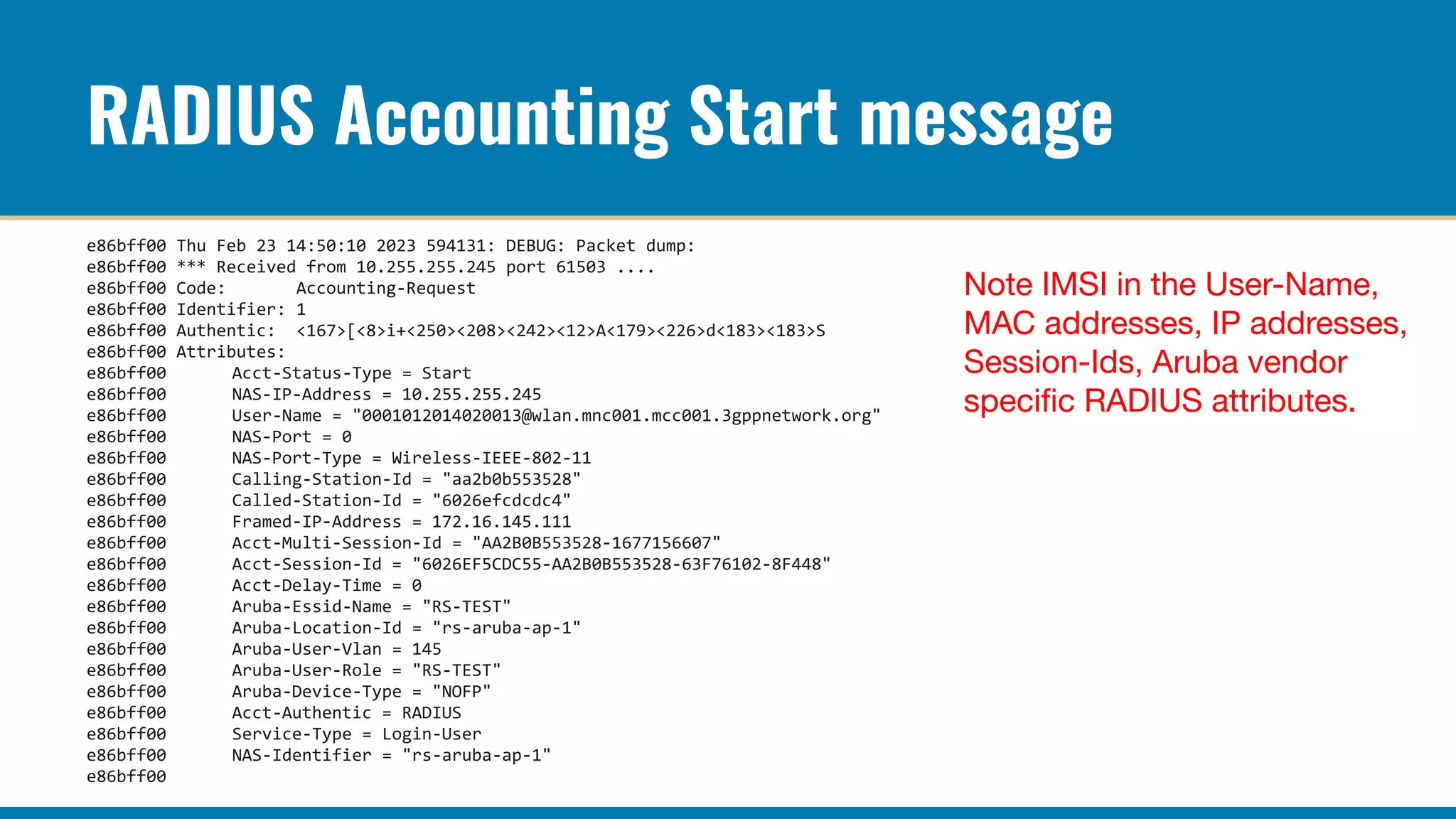
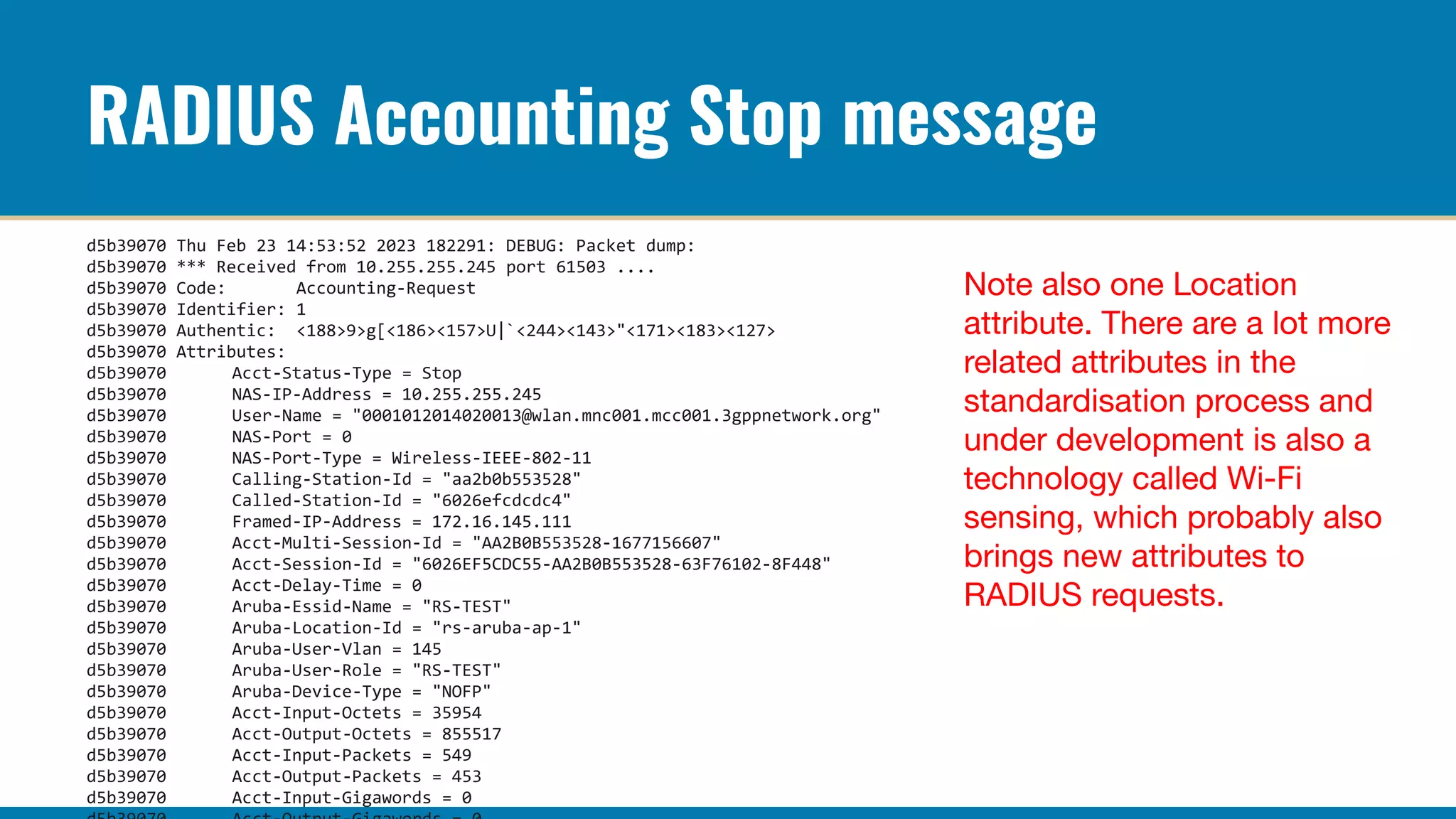
The RADIUS accounting messages contain cleartext user identity and device identifiers that can be used to track users even if the authentication traffic is encrypted. Some ways to mitigate this are:
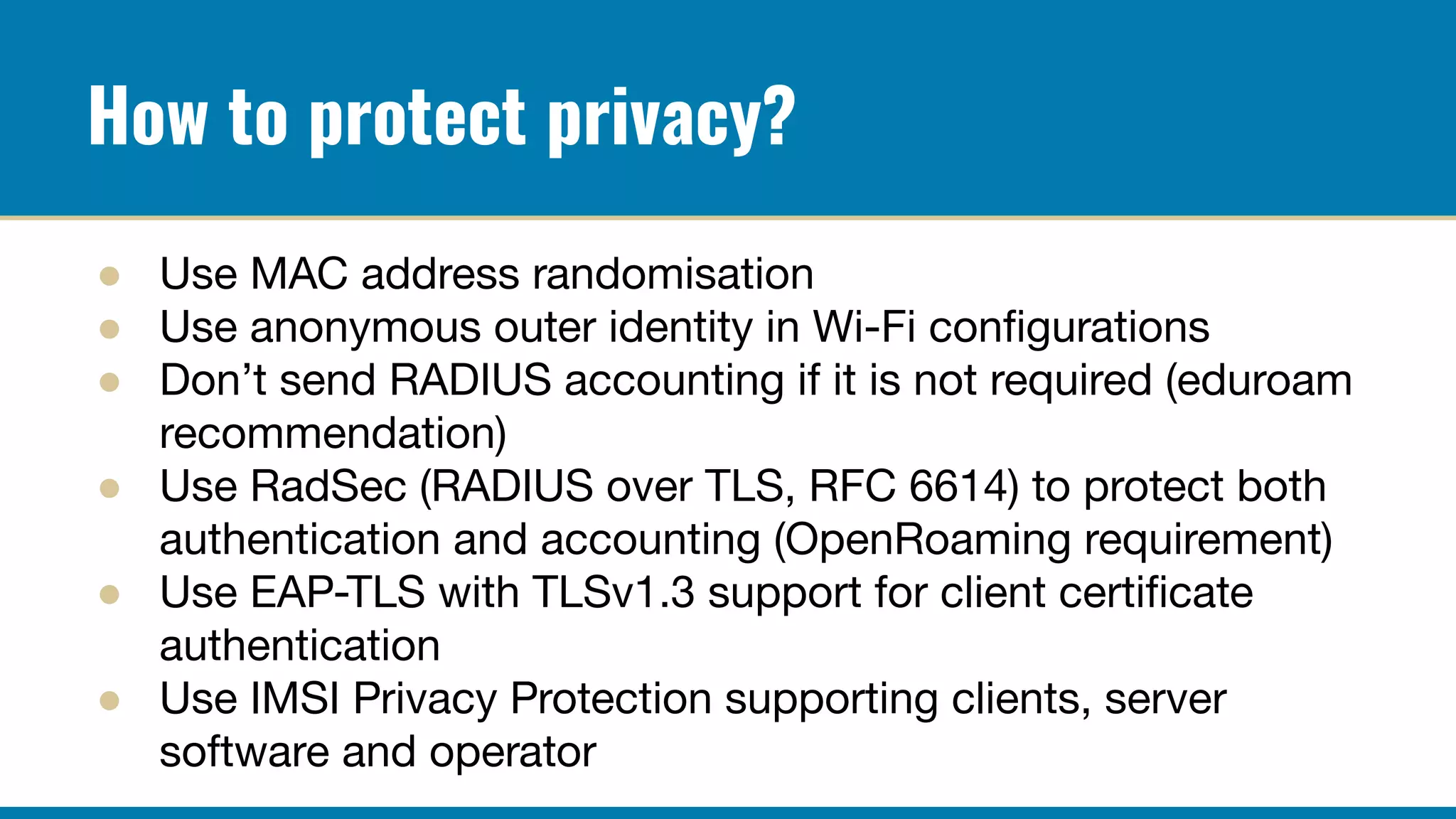
- Use EAP-TLS or EAP-PWD authentication to avoid sending IMSI or username in cleartext
- Enable IMSI privacy in EAP-SIM/EAP-AKA methods
- Tunnel or encrypt RADIUS accounting messages to prevent eavesdropping of user identities
- Use temporary identifiers instead of permanent ones in accounting messages
Proper configuration of authentication and accounting privacy features can help prevent user tracking via network monitoring of 802.1X and RADIUS traffic. However, complete anonymity is difficult to achieve in centralized network authentication systems