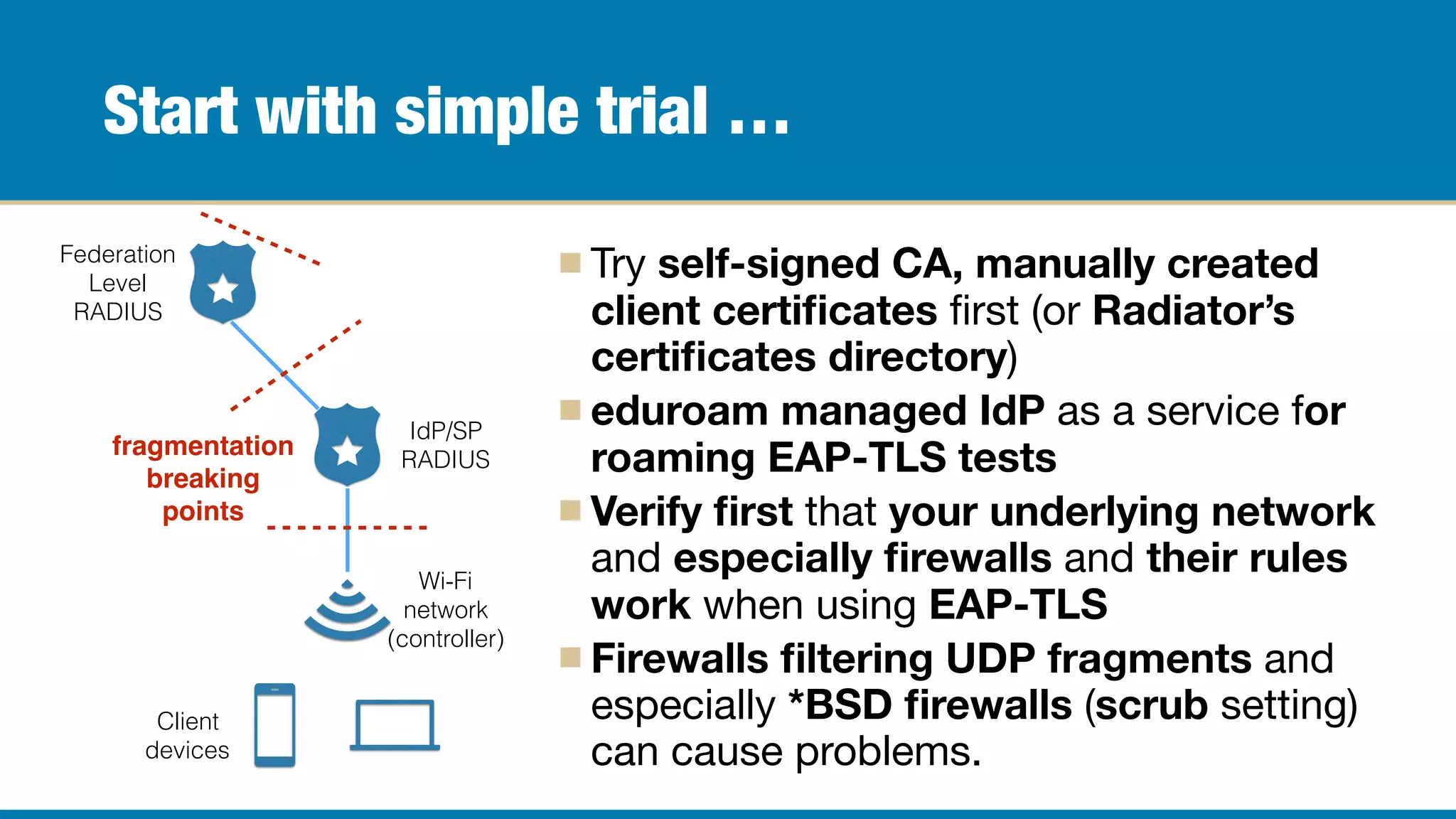
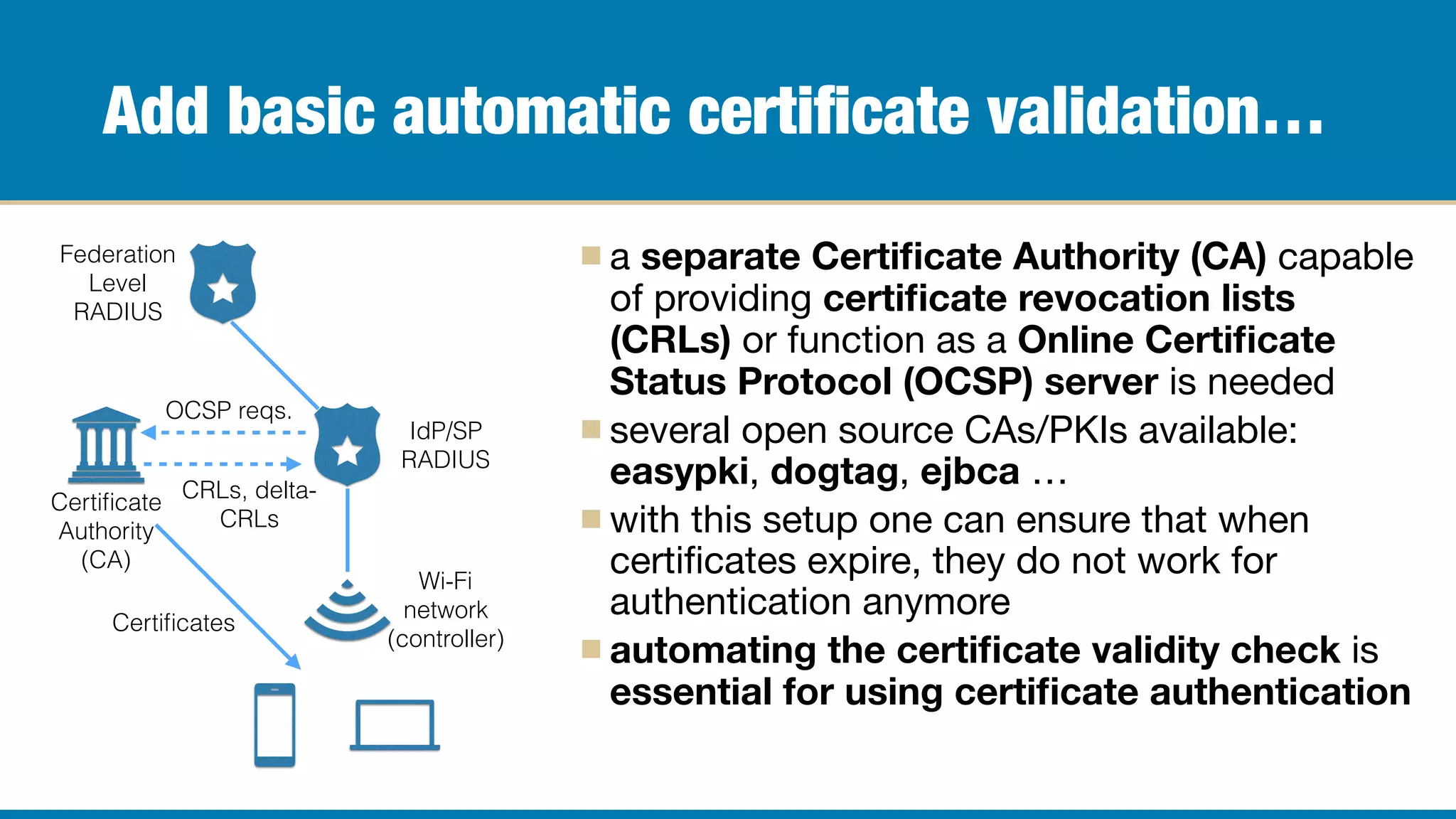
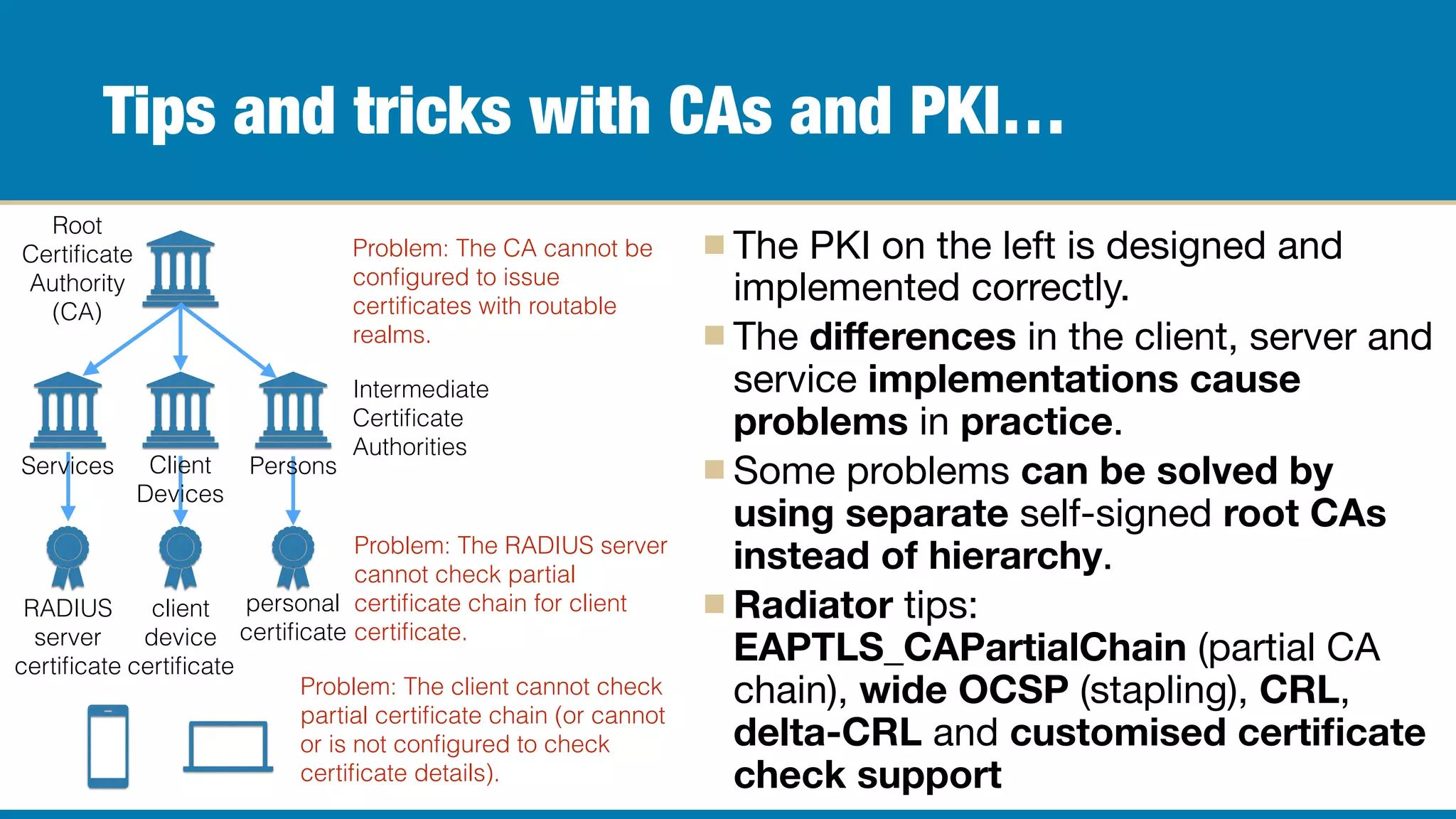
The document outlines the journey of Karri Huhtanen and Radiator Software Oy in developing RADIUS-based roaming solutions, focusing on EAP-TLS as a method for wireless authentication. It emphasizes the complexities of deploying EAP-TLS, including the need for proper configuration of certificates, management of a public key infrastructure (PKI), and integration with authorization databases. Key takeaways include the necessity of thorough testing, understanding of network configurations, and support from infrastructure vendors to ensure successful implementation.