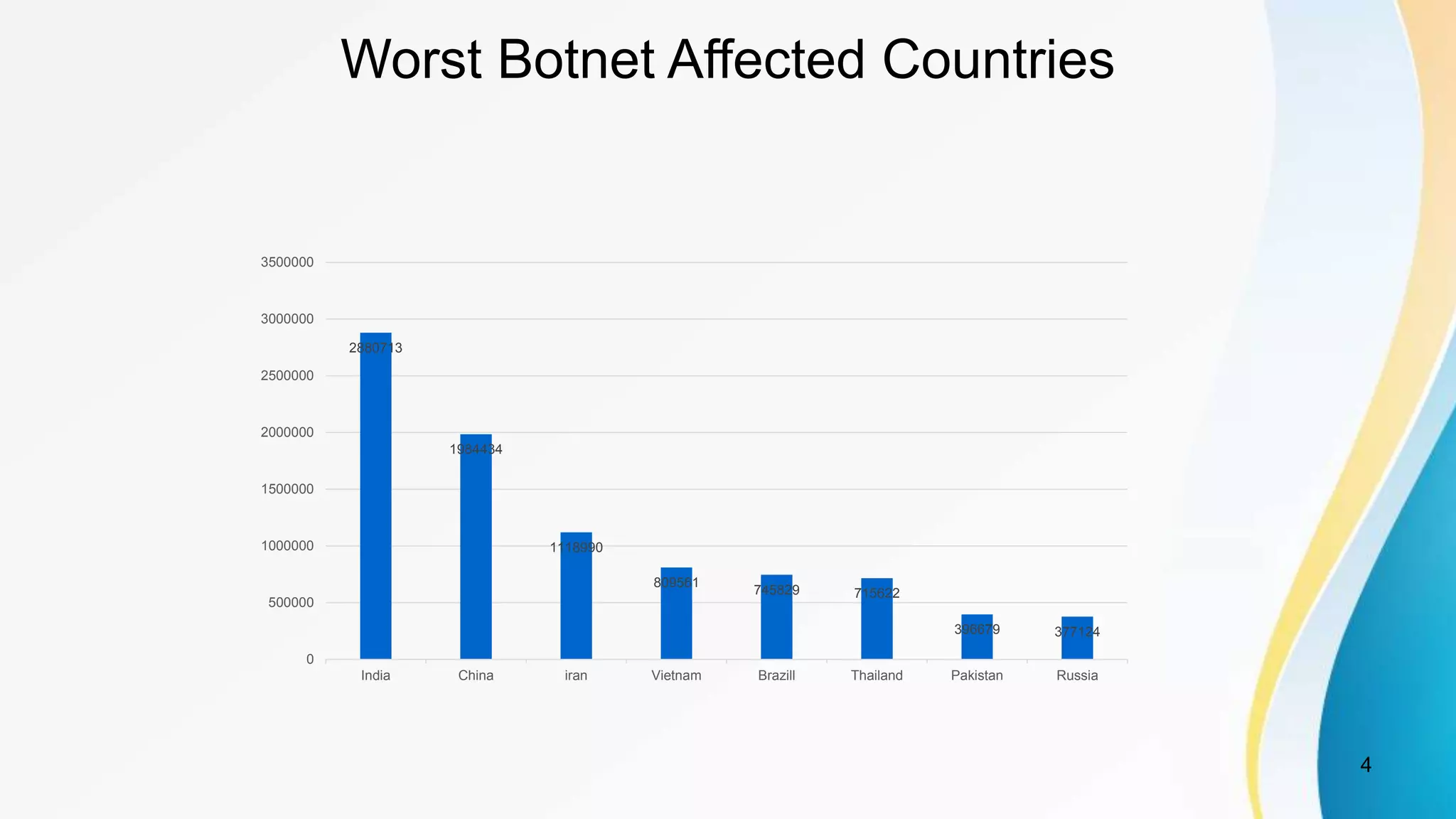
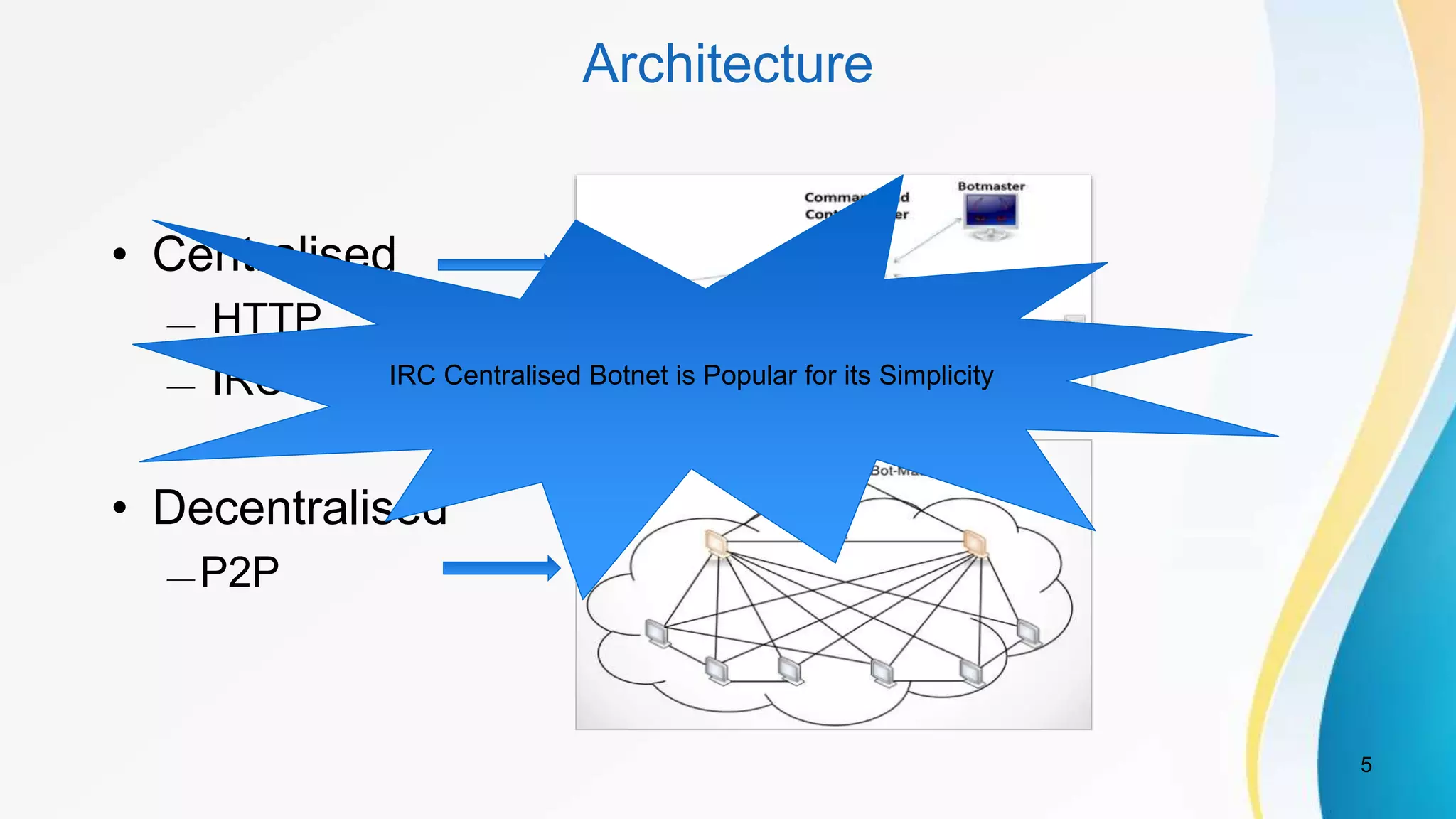
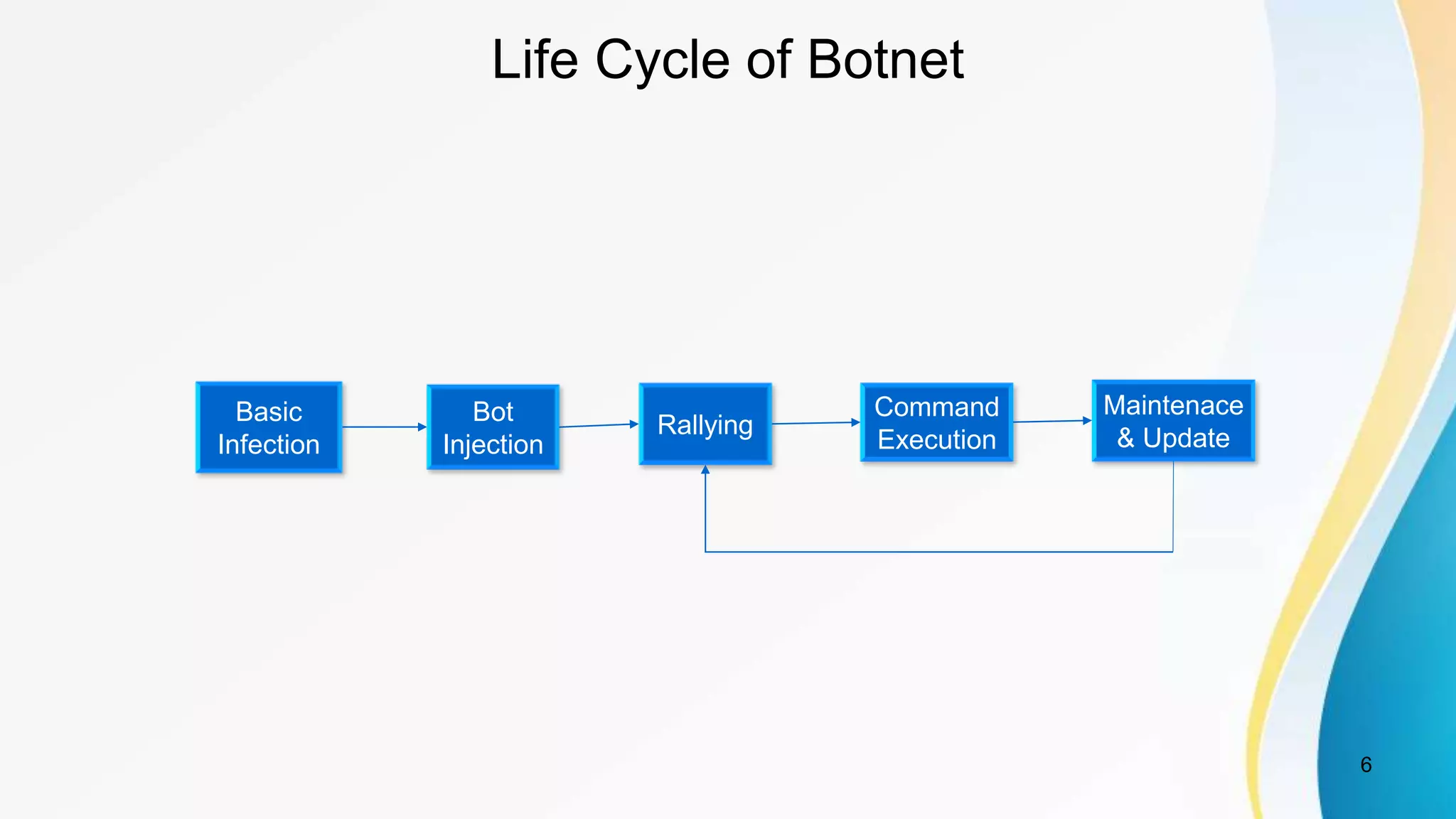
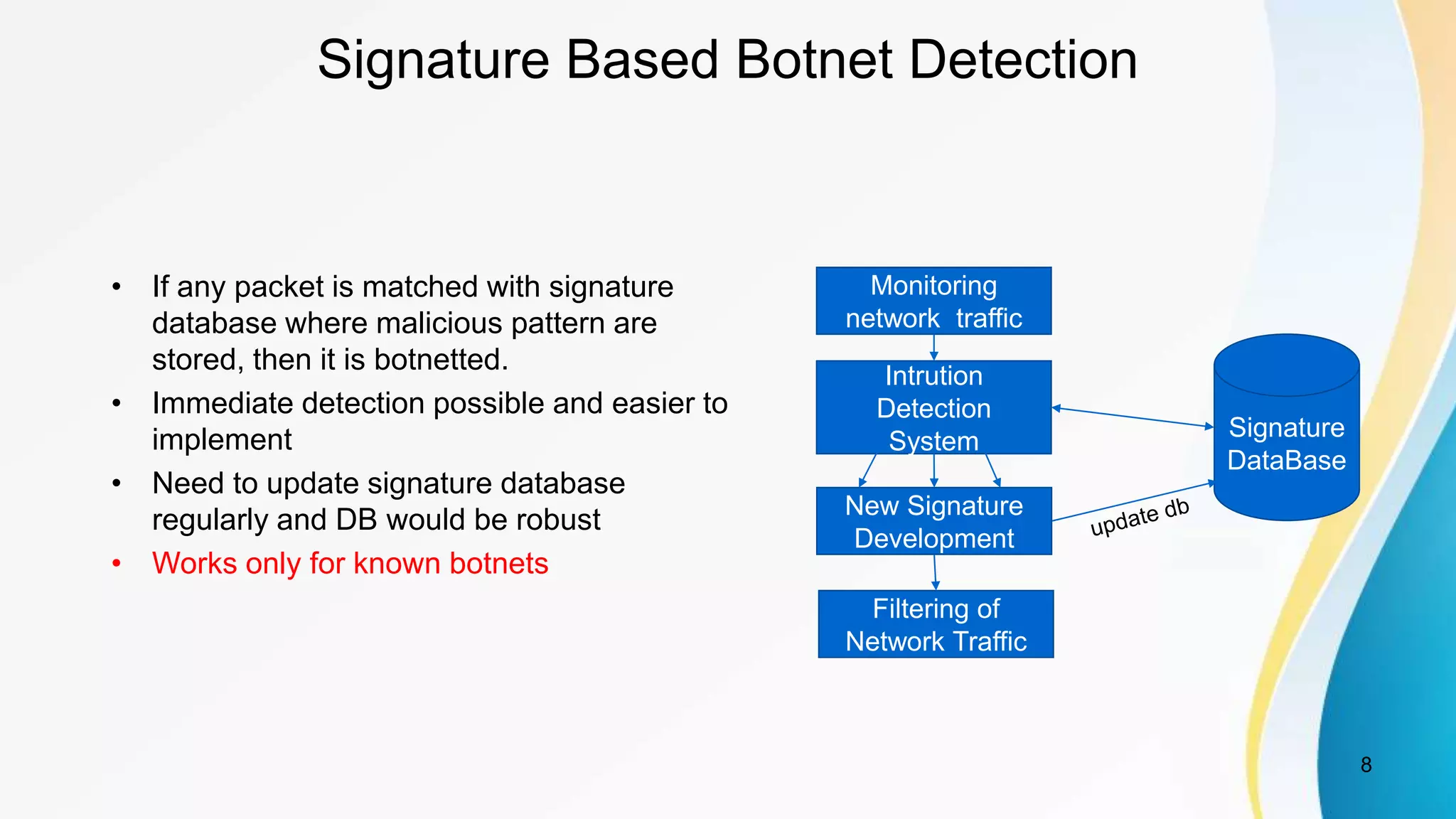
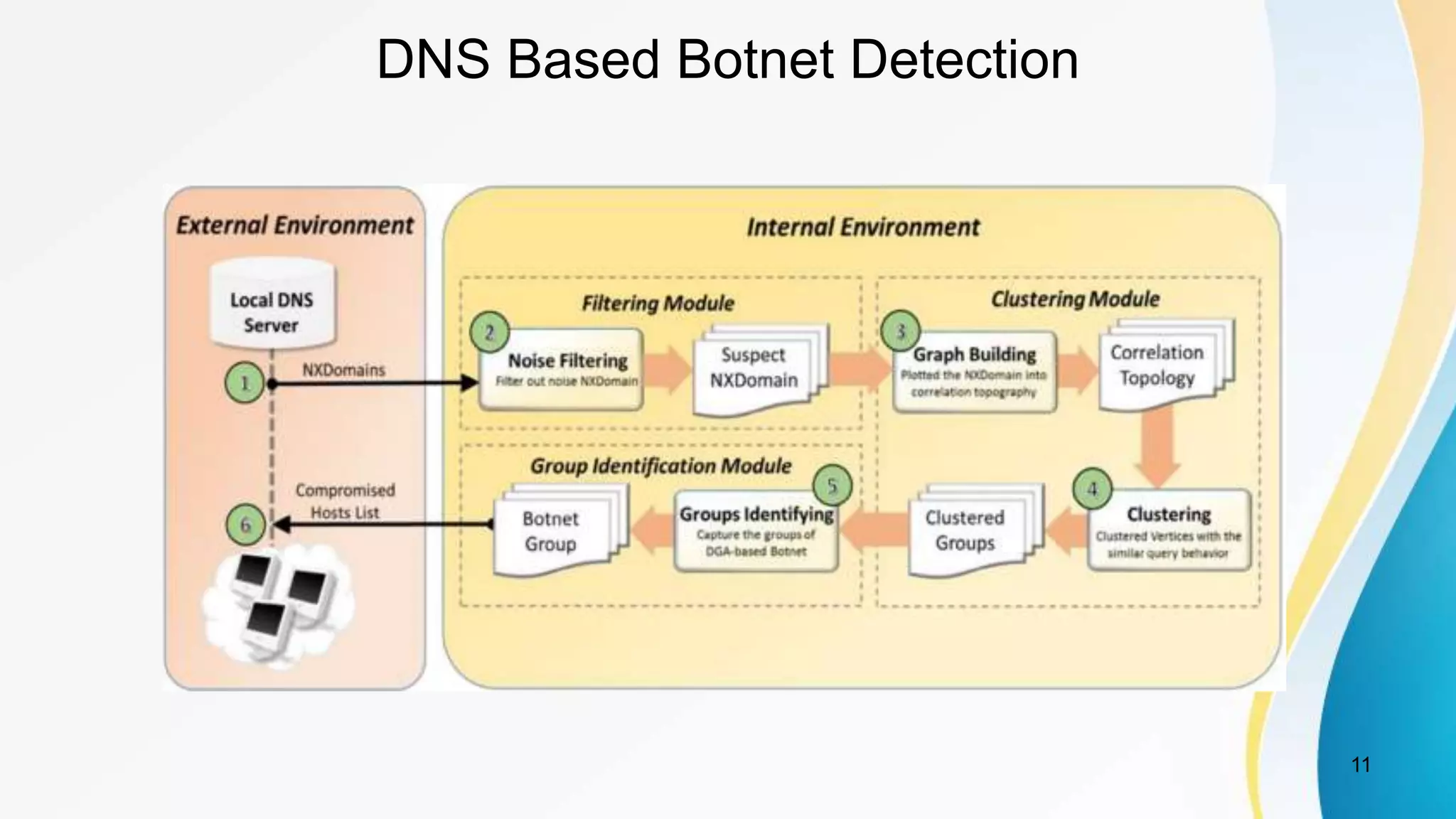
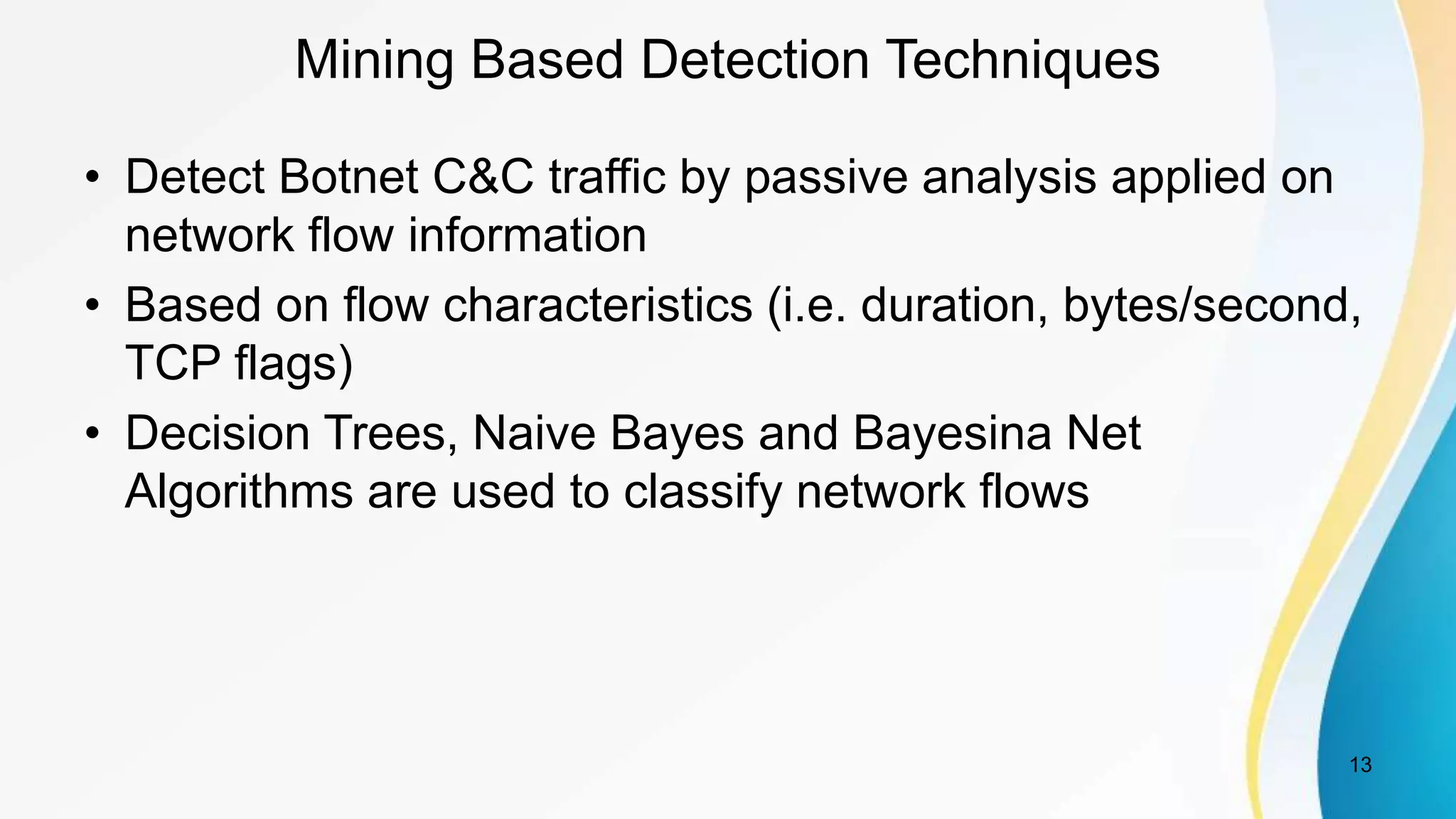
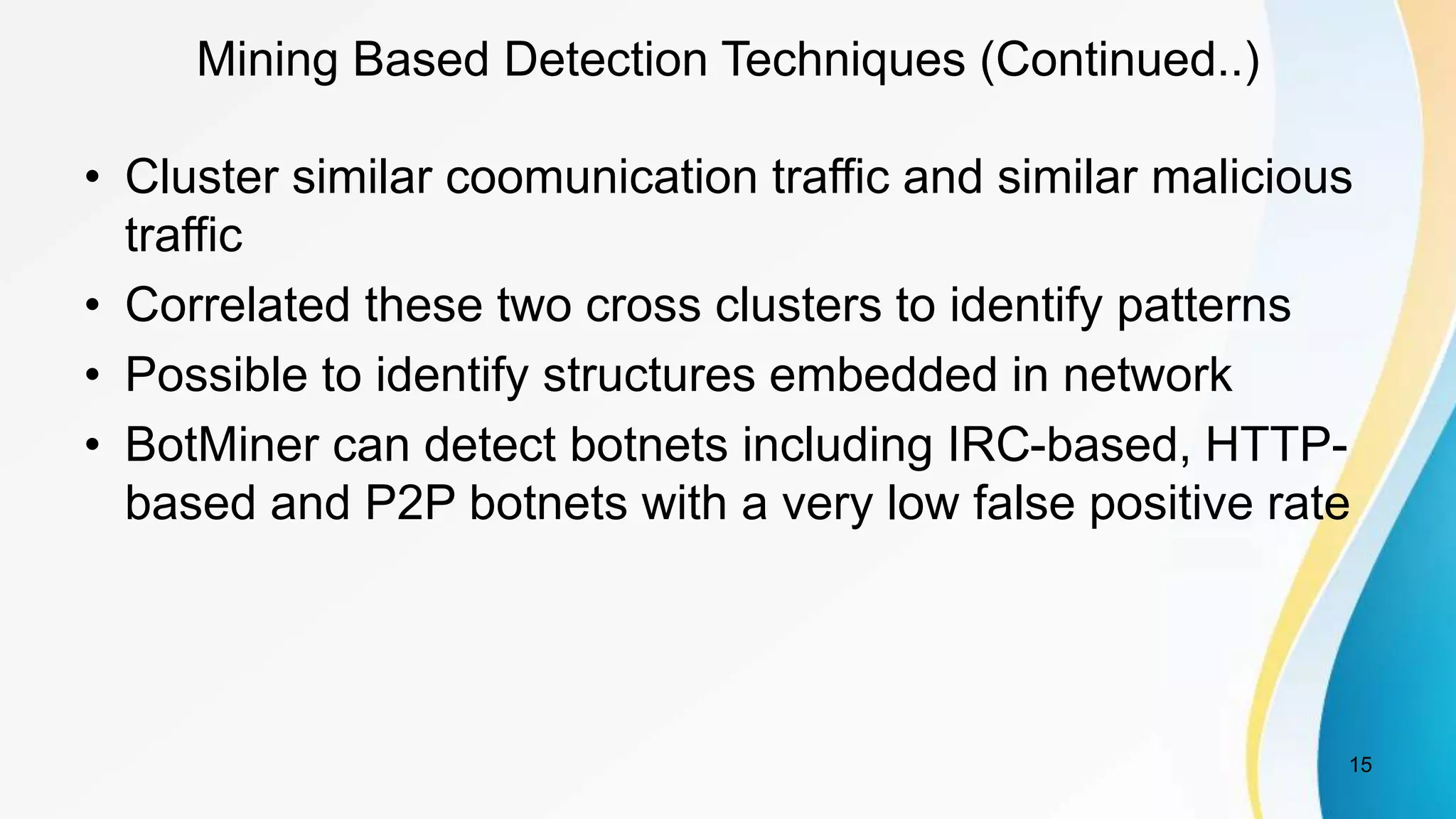
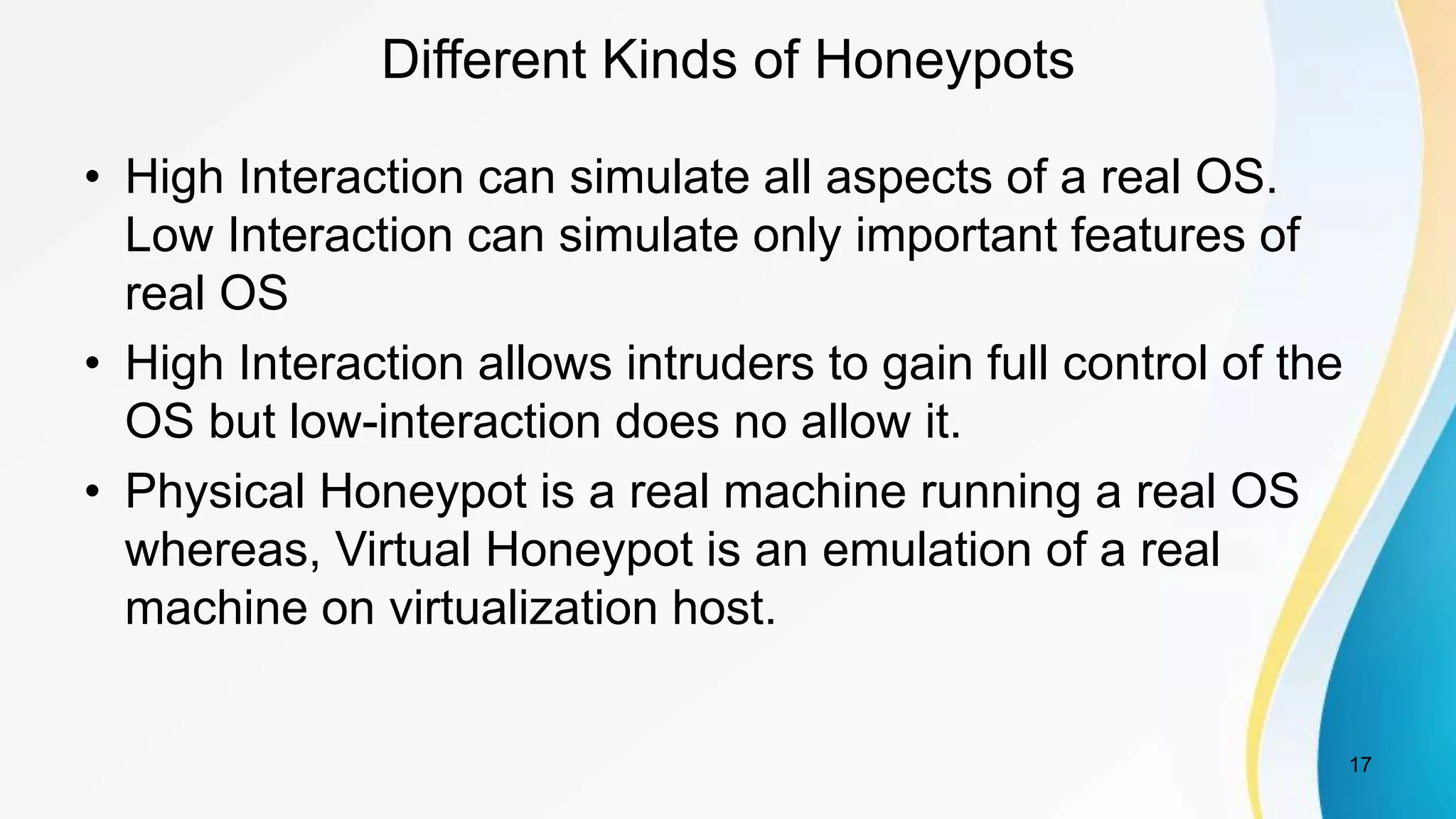
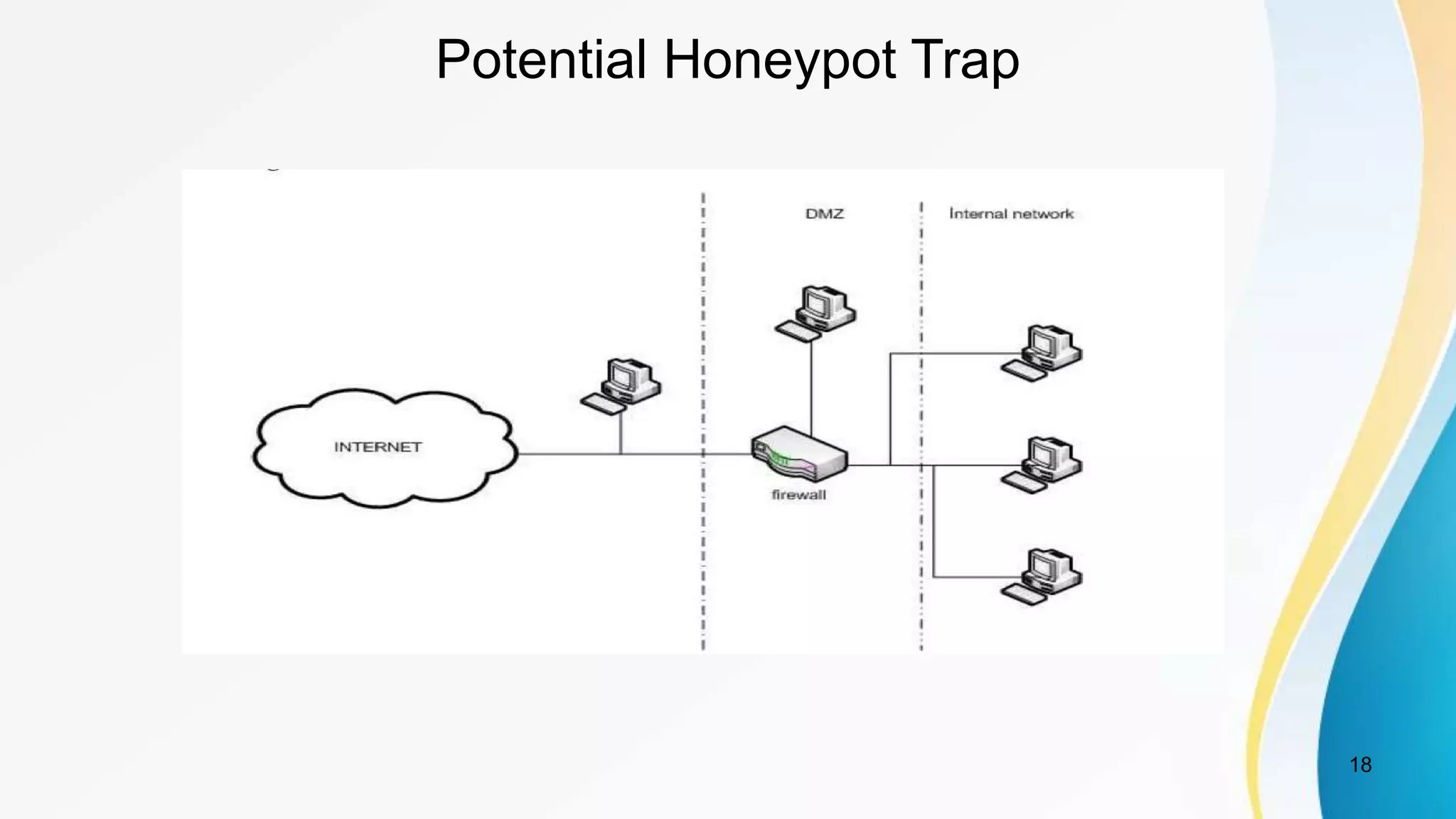
This document discusses botnet detection techniques. It begins by defining what a botnet is and how botnets are used to conduct cybercrimes. It then outlines several botnet detection methods including signature-based detection, anomaly-based detection, DNS-based detection, mining-based detection, and using honeypots and honeynets. Specific examples of botnets and worst affected countries are also provided. The document concludes by emphasizing the threat posed by botnets and importance of detecting and preventing botnet attacks.