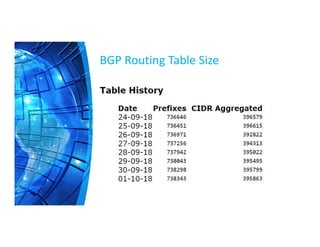
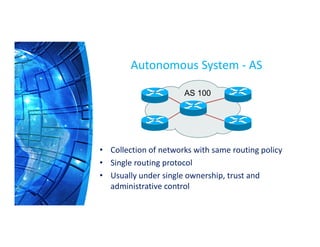
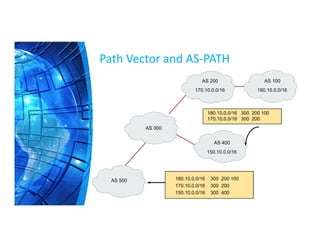
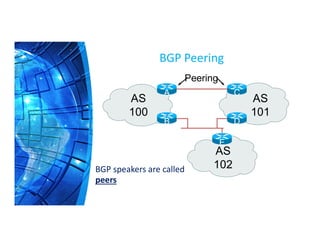
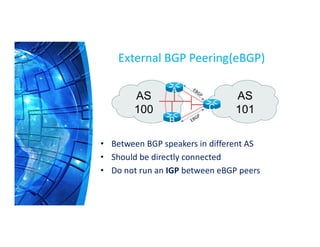
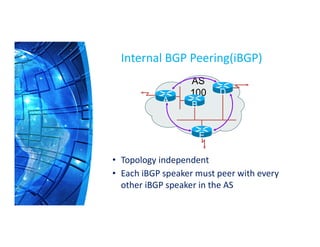
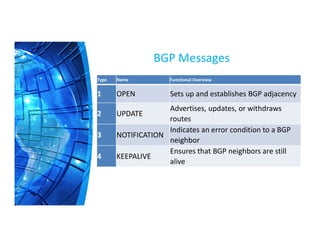
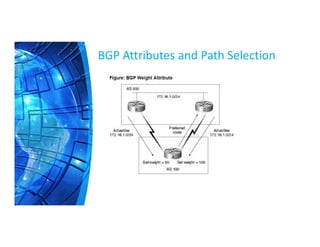
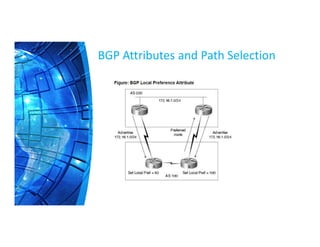
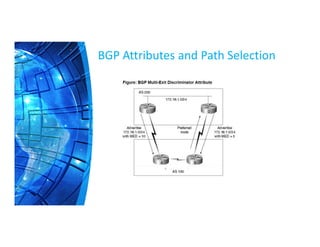
The Border Gateway Protocol (BGP) is a crucial routing protocol that enables communication between different networks on the internet by exchanging network reachability information. It operates with autonomous system (AS) numbers and employs path vector mechanisms for route selection and loop detection, facilitating efficient and resilient data traffic routing. BGP supports both external and internal peering configurations and incorporates various attributes to optimize path selection for route management within and across networks.