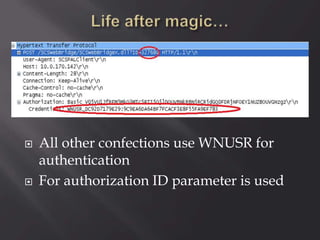
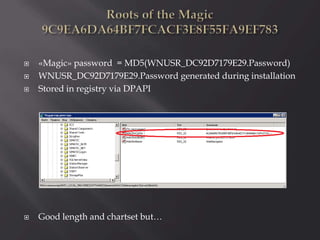
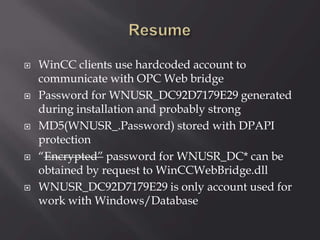
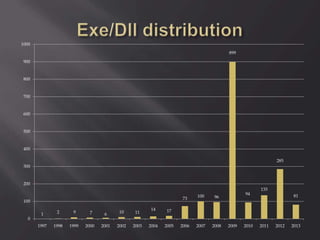
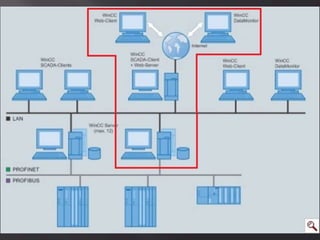
This document contains information from a group of security researchers focused on assessing industrial control systems and SCADA platforms. Their goals are to automate security assessments, understand systems, assess security features, and create audit guides. It discusses engineering tools, SCADA/HMI software, PLCs, and vulnerabilities found like buffer overflows and injection issues. The researchers aim to advance understanding and help organizations prioritize patches through responsible disclosure of vulnerabilities.












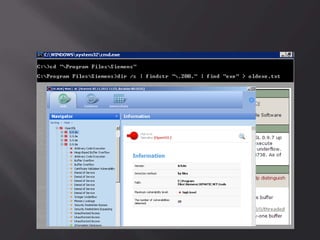
















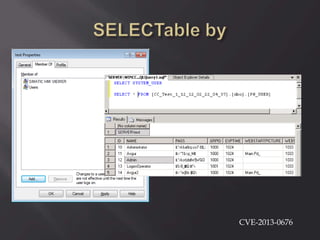
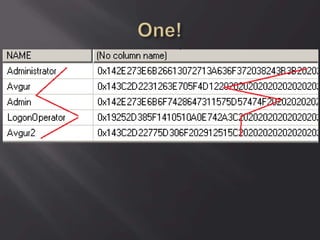
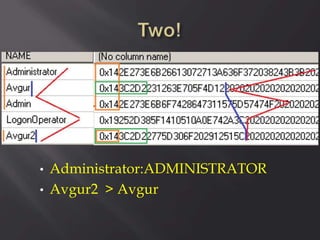
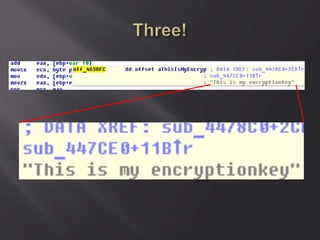






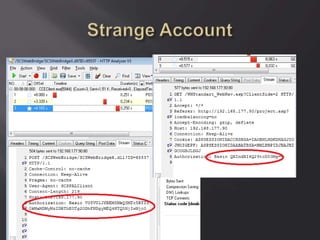

![Oh! En/c(r)ypt[10]n!
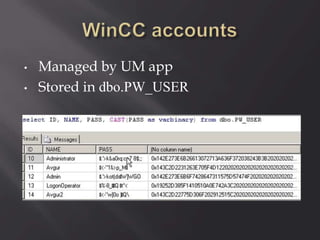
ServerID = Base64(RC2(pass, key)), were key
= MD5(dll hardcode)](https://image.slidesharecdn.com/scadastrangelove-130607032612-phpapp01/85/Scada-strange-love-54-320.jpg)