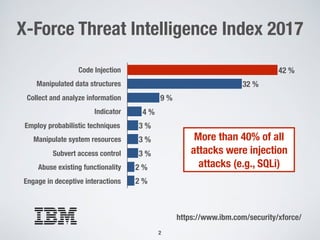
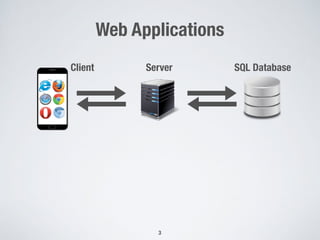
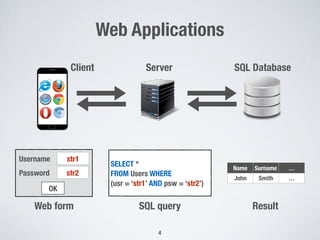
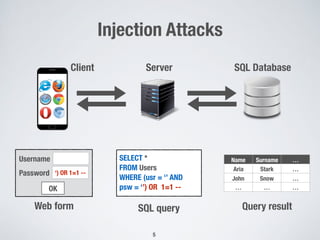
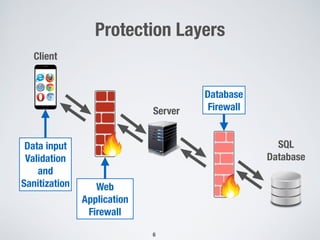
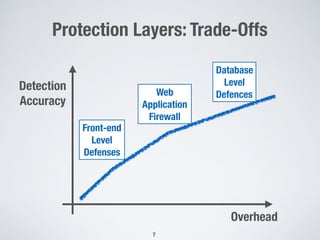
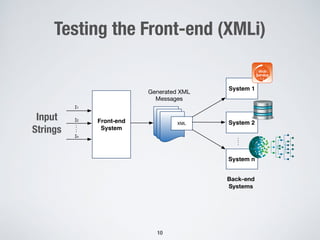
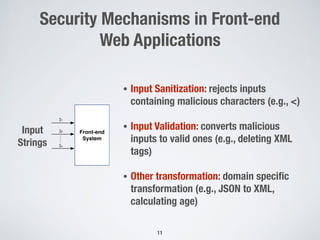
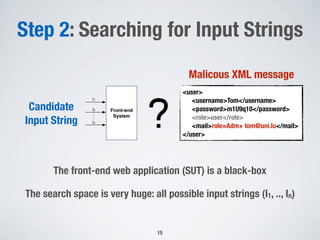
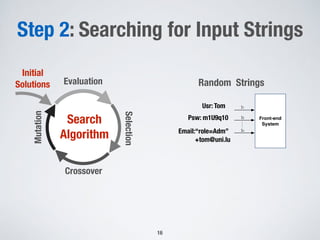
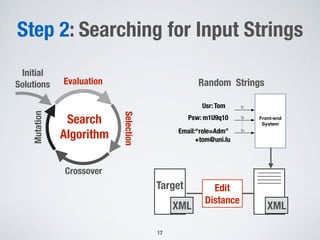
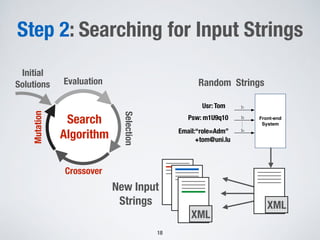
The document discusses automated vulnerability testing of web applications using machine learning and metaheuristic search. It discusses three key areas:
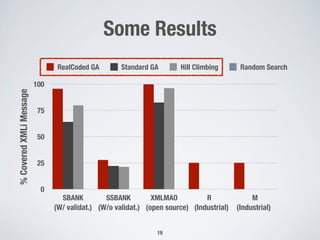
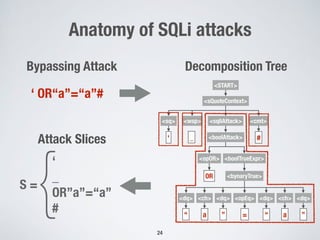
1. Testing front-end web applications for XML injection vulnerabilities by automatically generating malicious XML messages and using search-based techniques to find input strings that allow the generation of these messages.
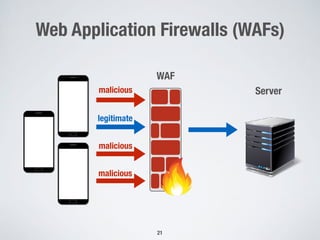
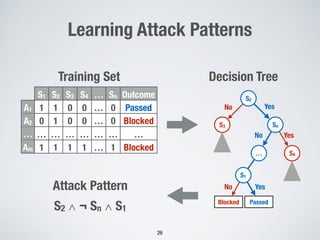
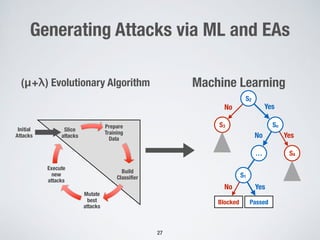
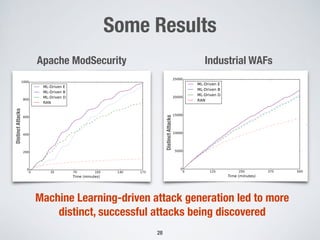
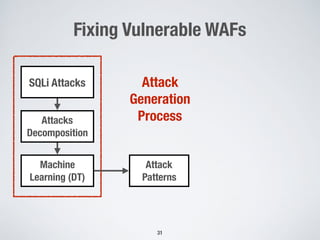
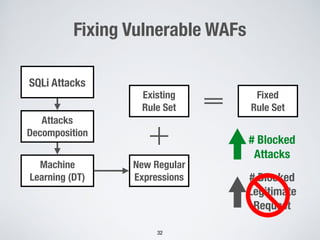
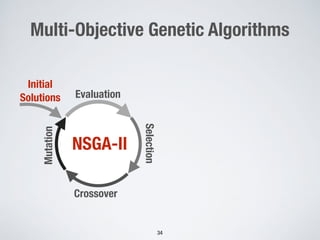
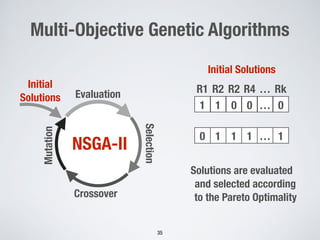
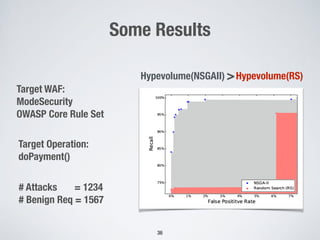
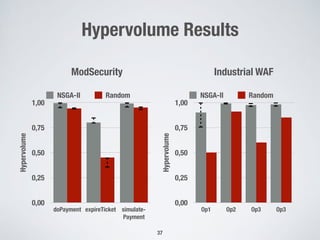
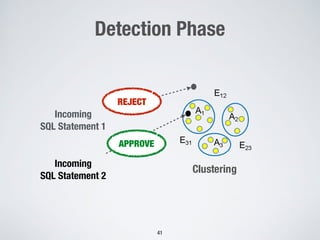
2. Testing web application firewalls (WAFs) using machine learning to learn attack patterns from successful and blocked attacks to generate new attacks, and a multi-objective genetic algorithm to automatically repair vulnerable WAF rule sets.
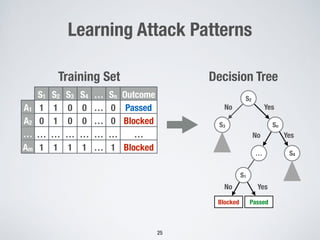
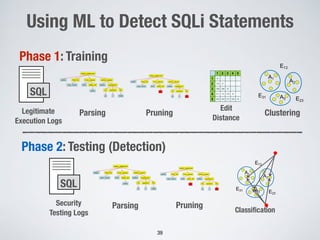
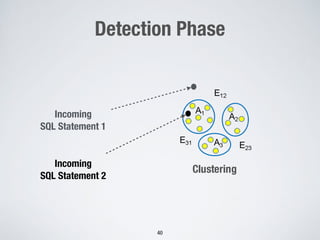
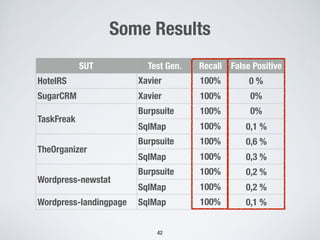
3. Using machine learning to detect malicious SQL statements at the database level by training on legitimate and attack SQL logs and classifying new statements as legitimate or attacks.