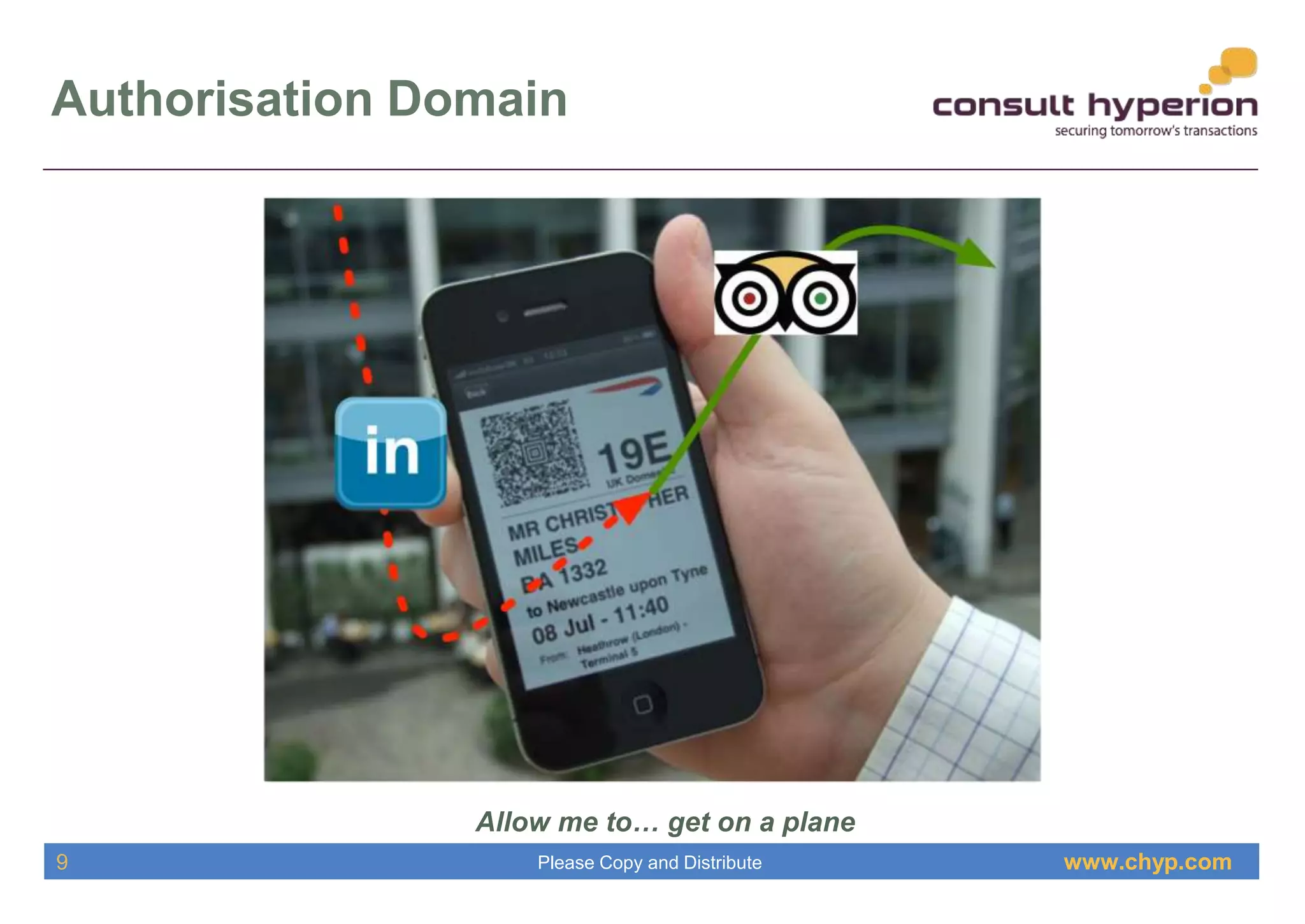
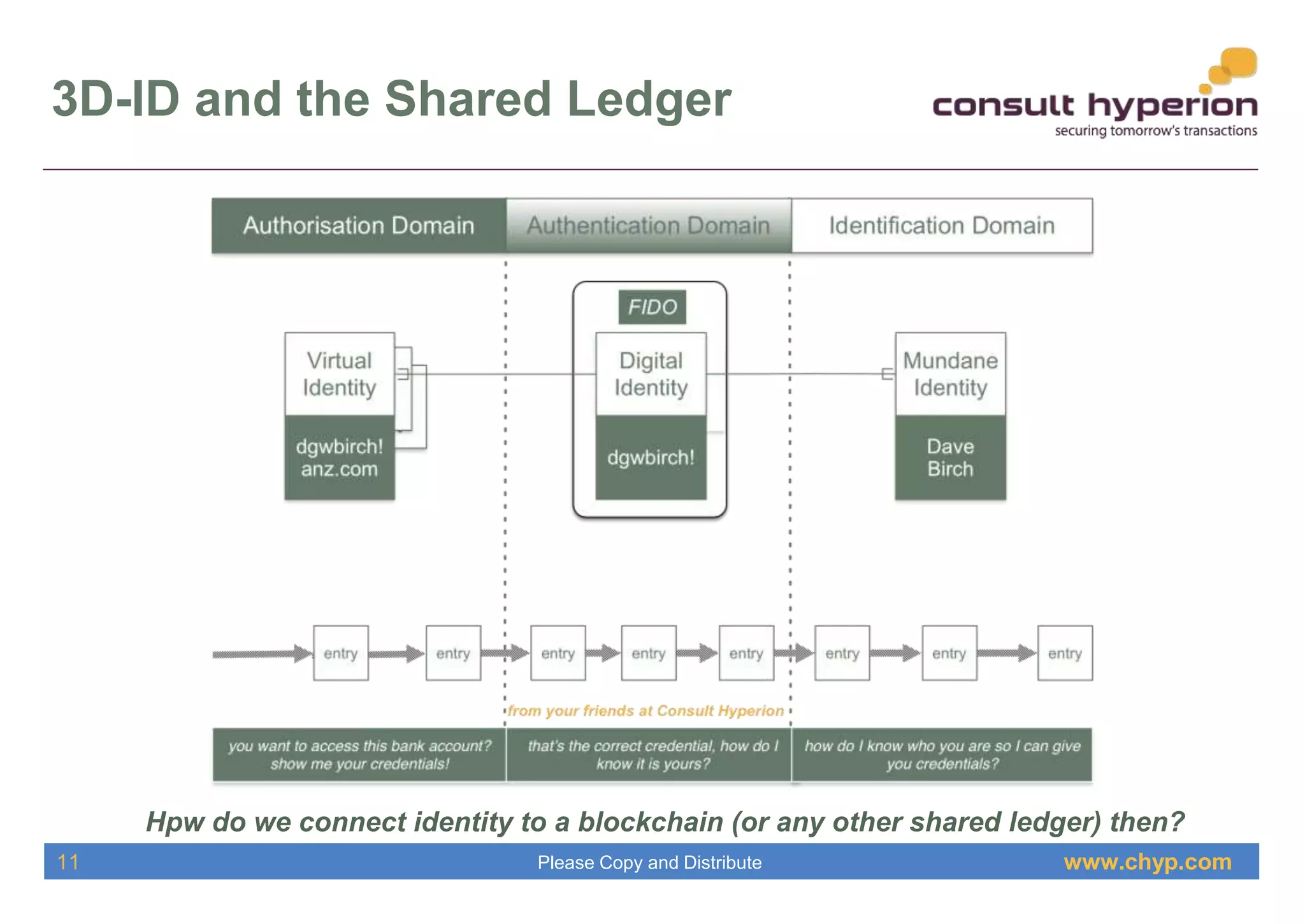
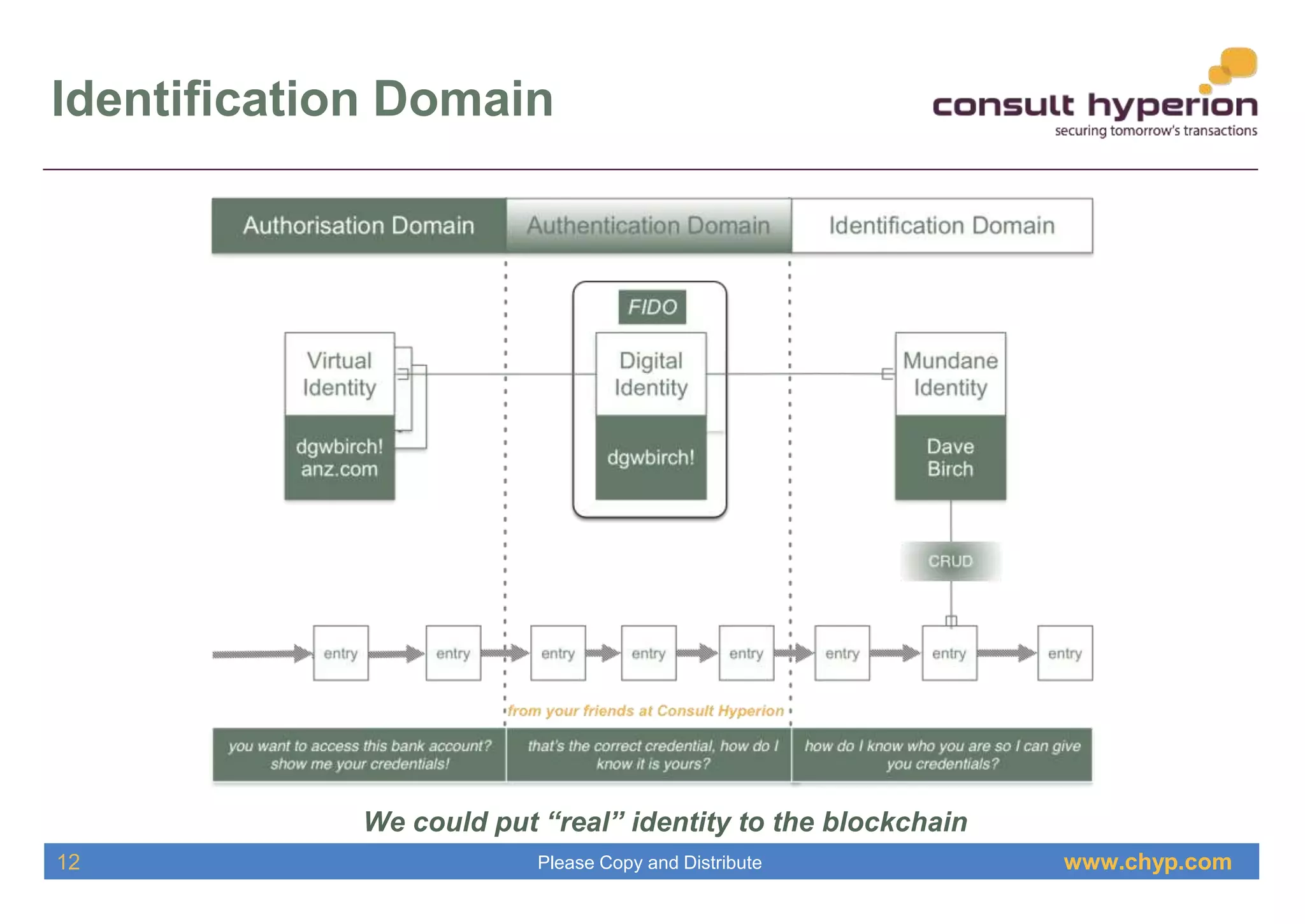
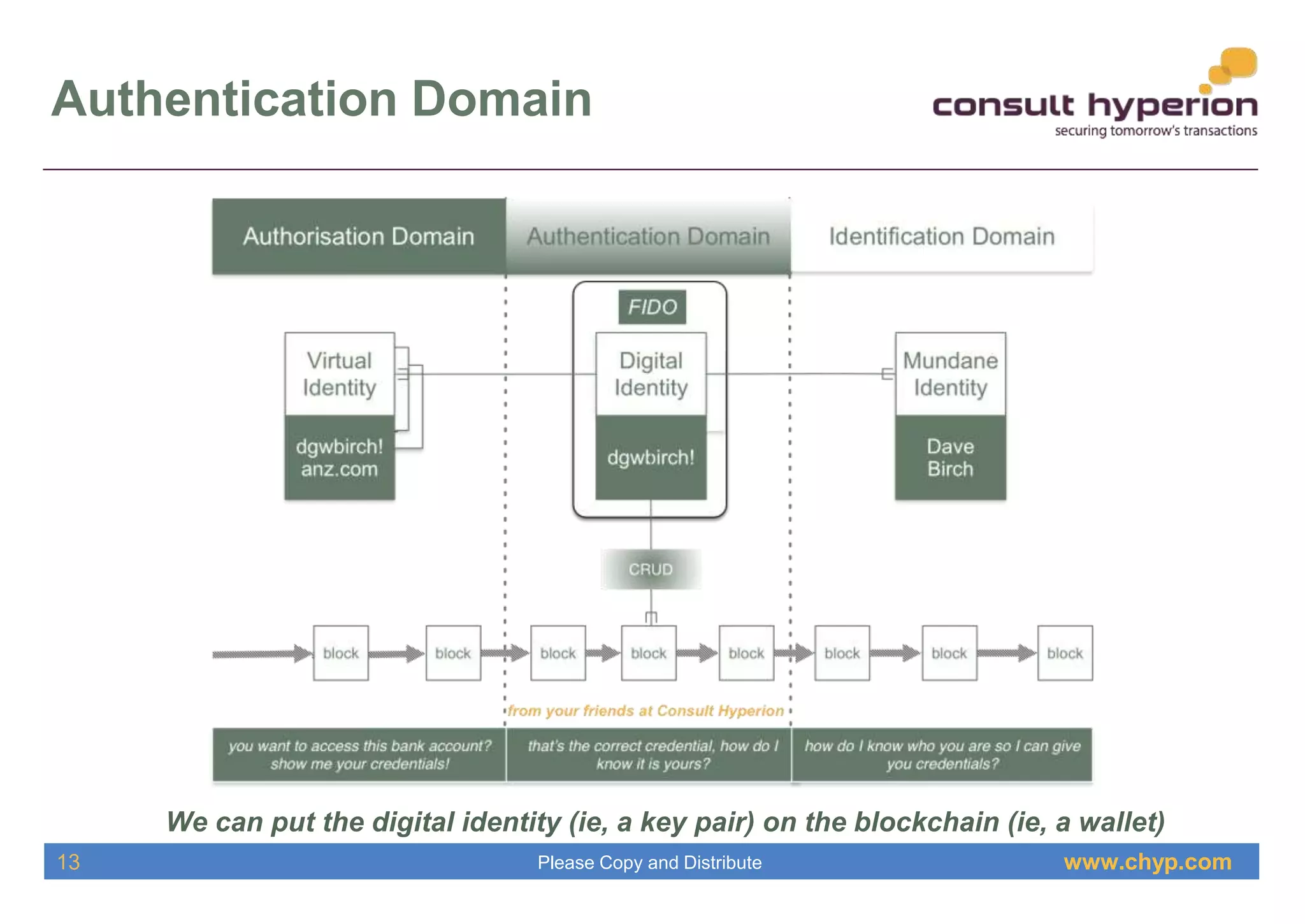
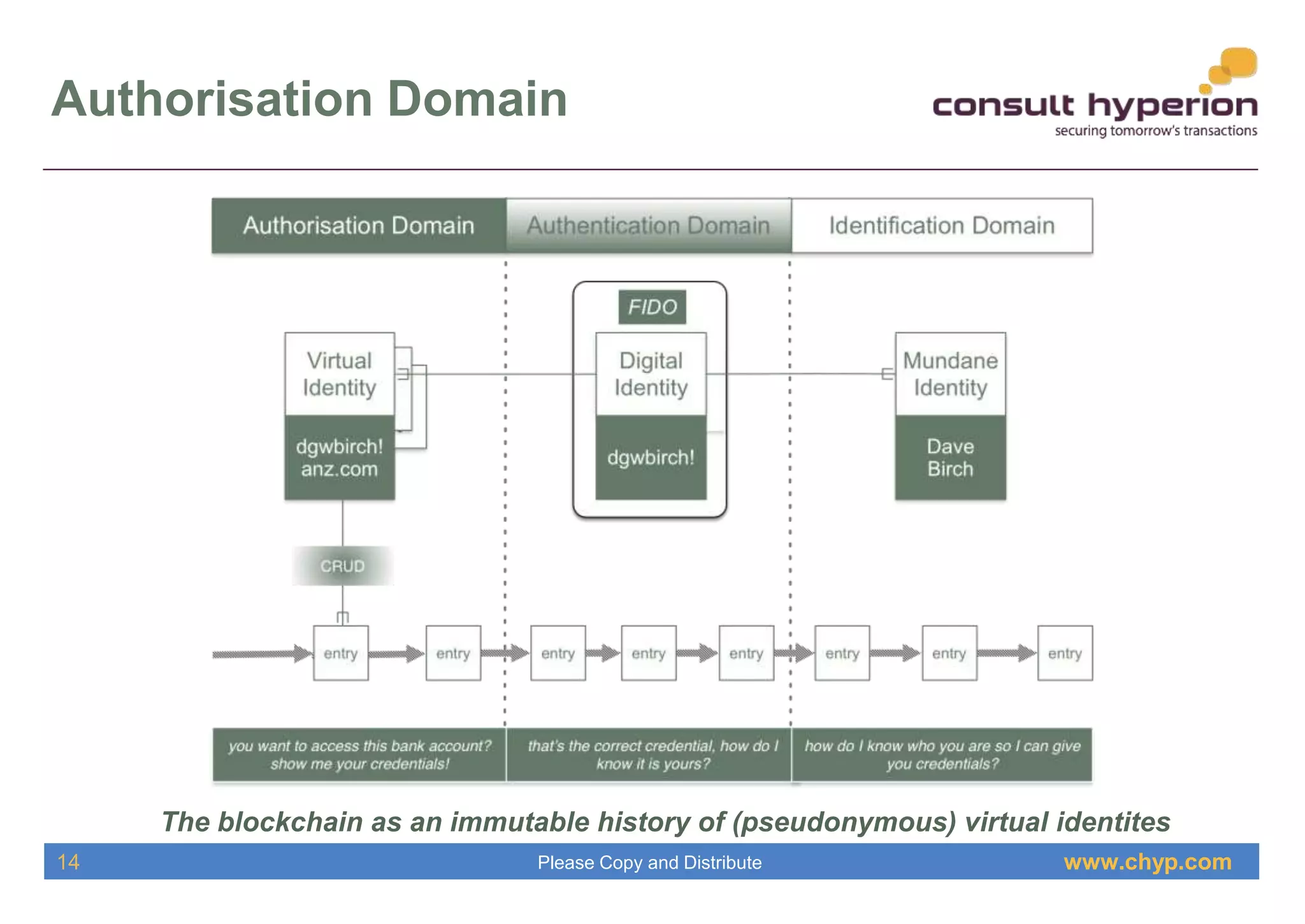
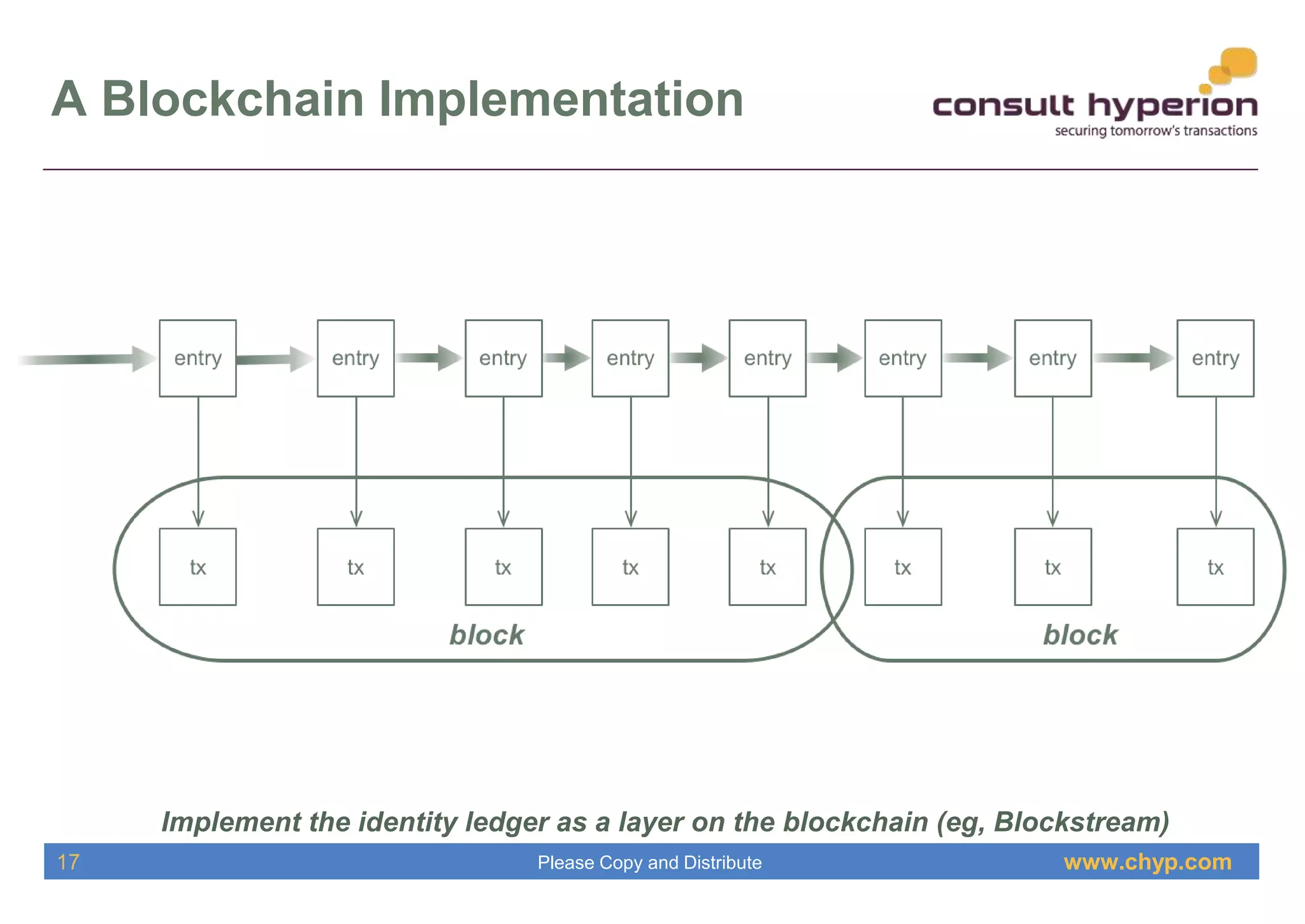
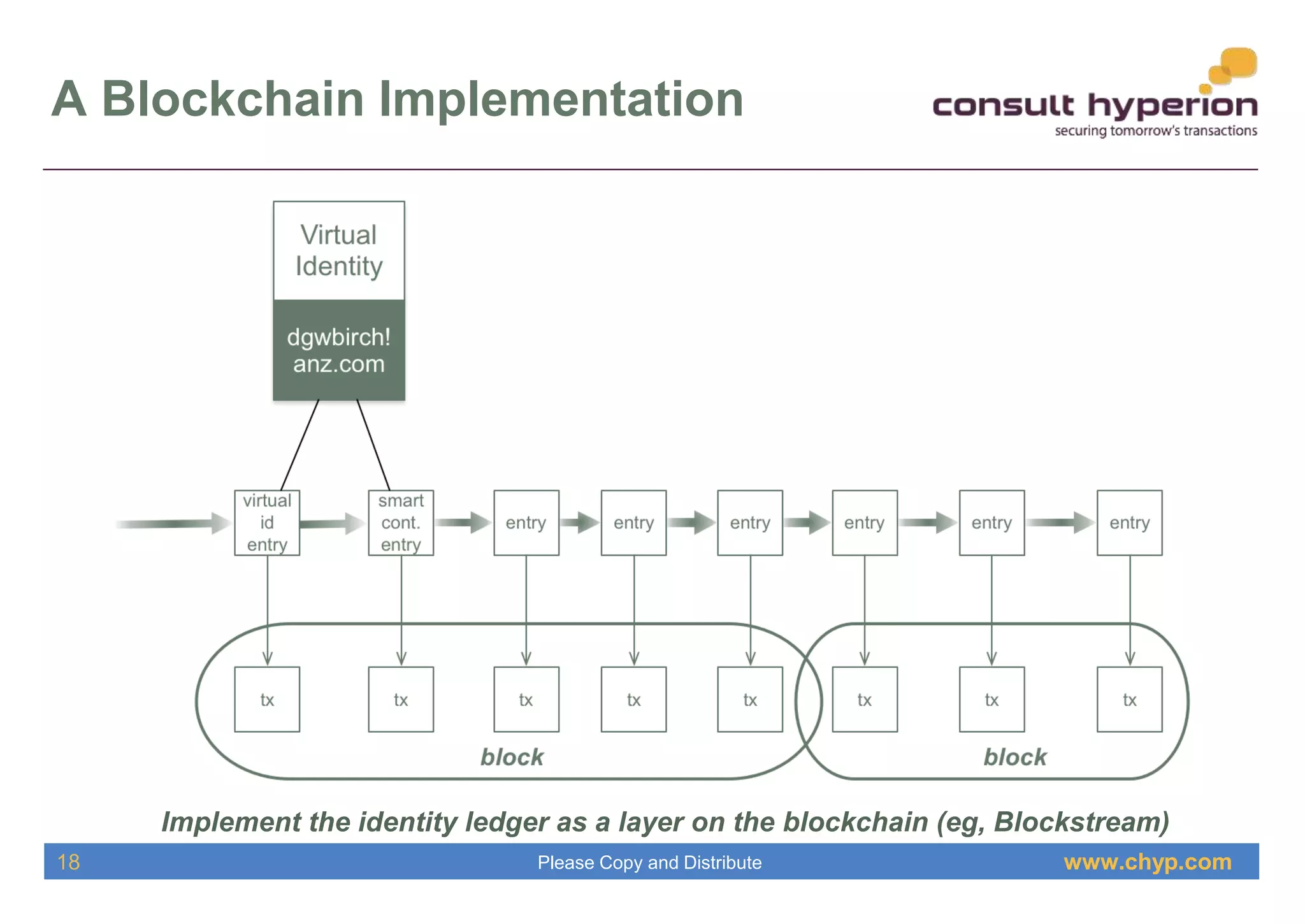
The document discusses the integration of digital identity and blockchain technology, emphasizing a three-domain model for understanding their relationship. It highlights the potential benefits of using a shared ledger for identity transactions, proposes practical implementations, and outlines how users can authenticate through blockchain-based solutions. Consult Hyperion, the authoring organization, specializes in navigating security and transaction systems in the evolving digital landscape.