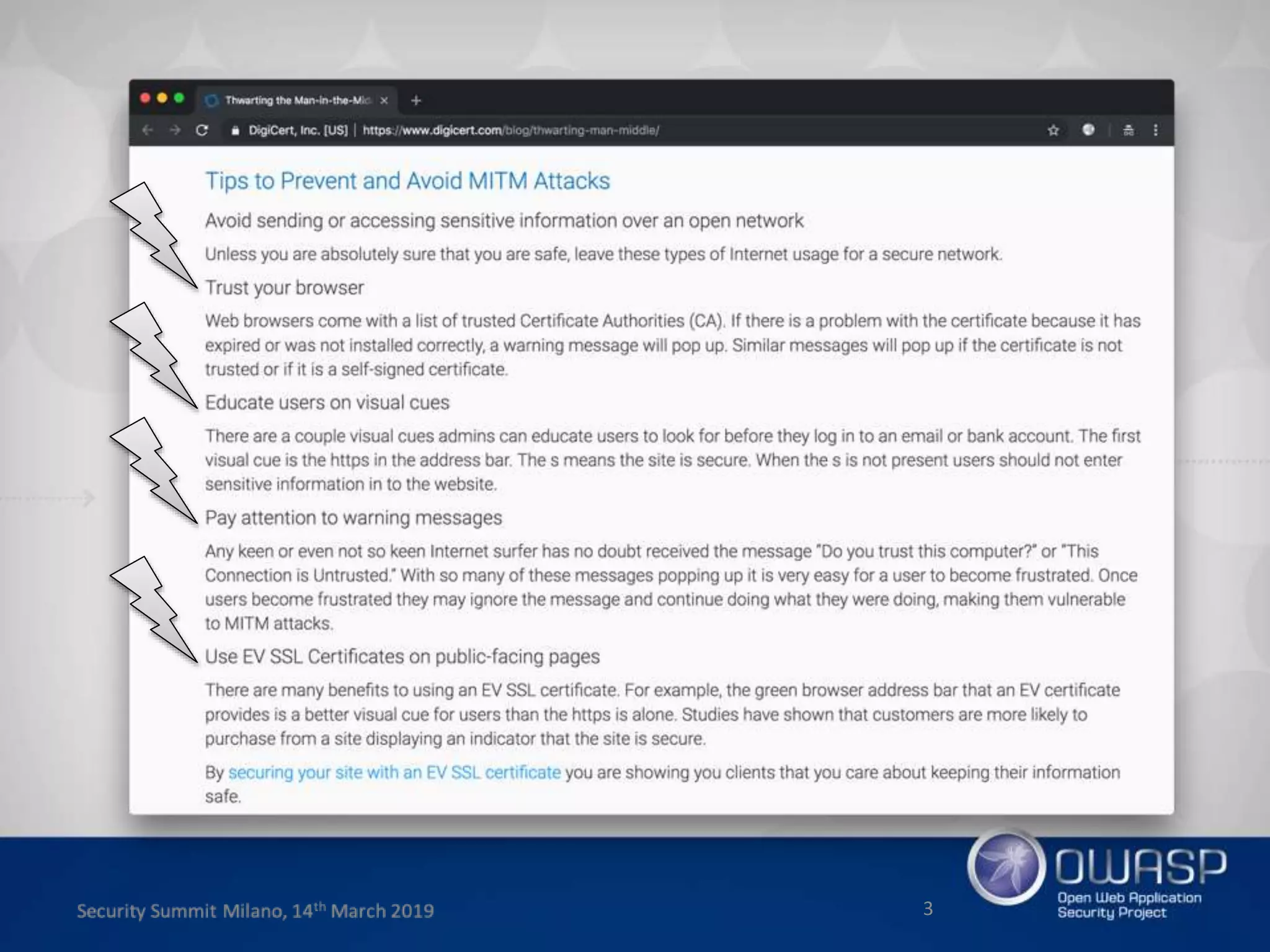
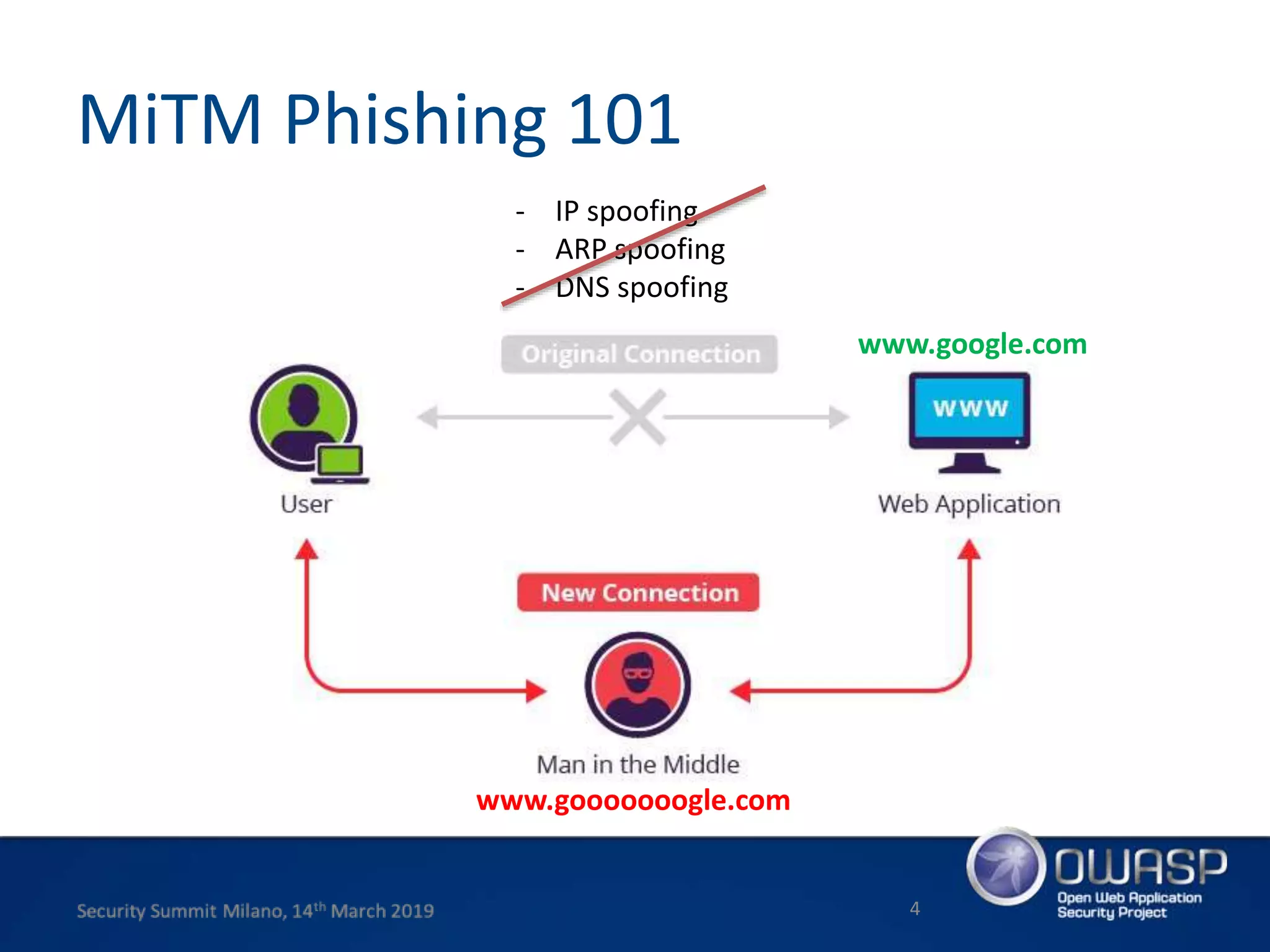
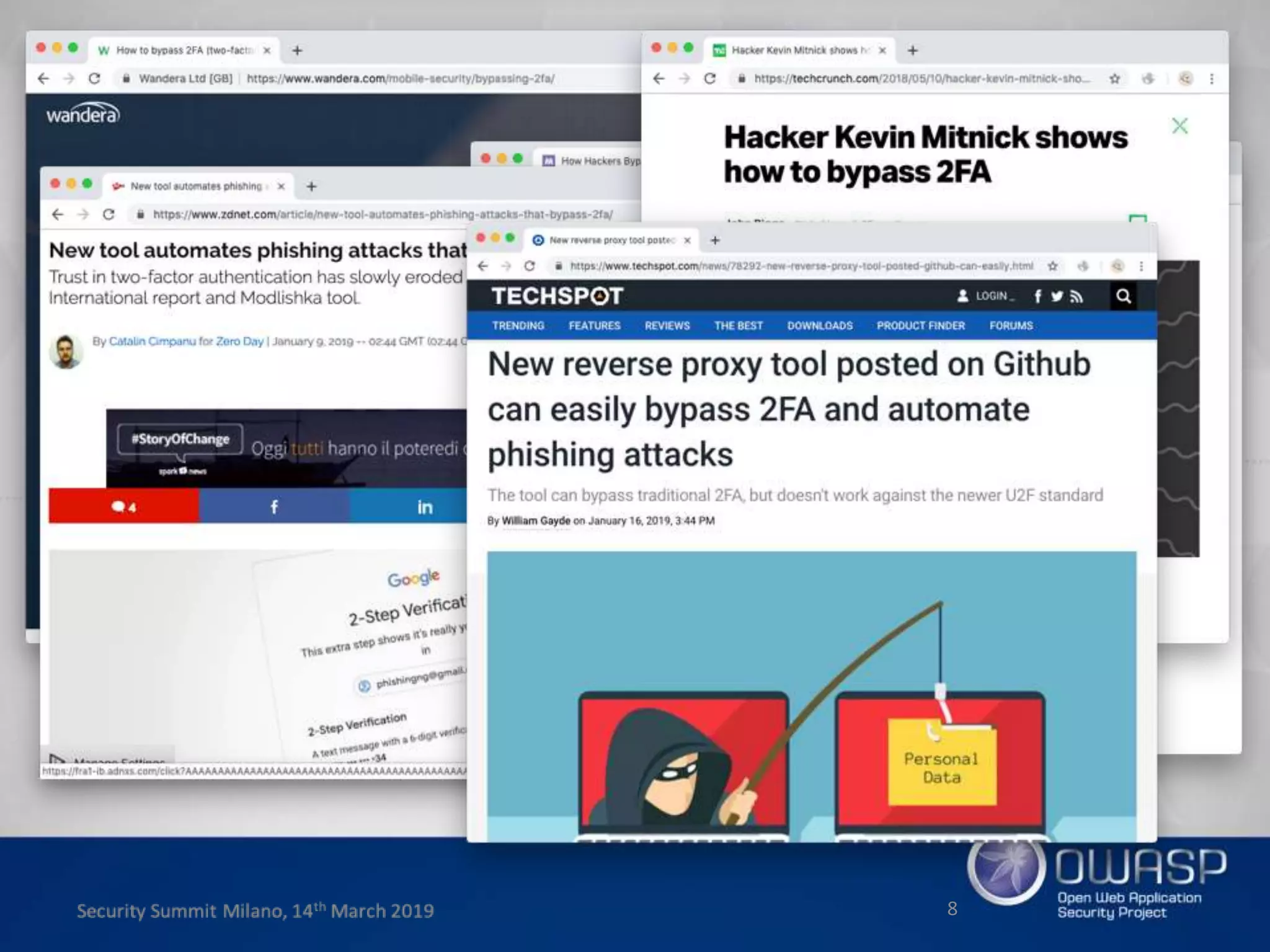
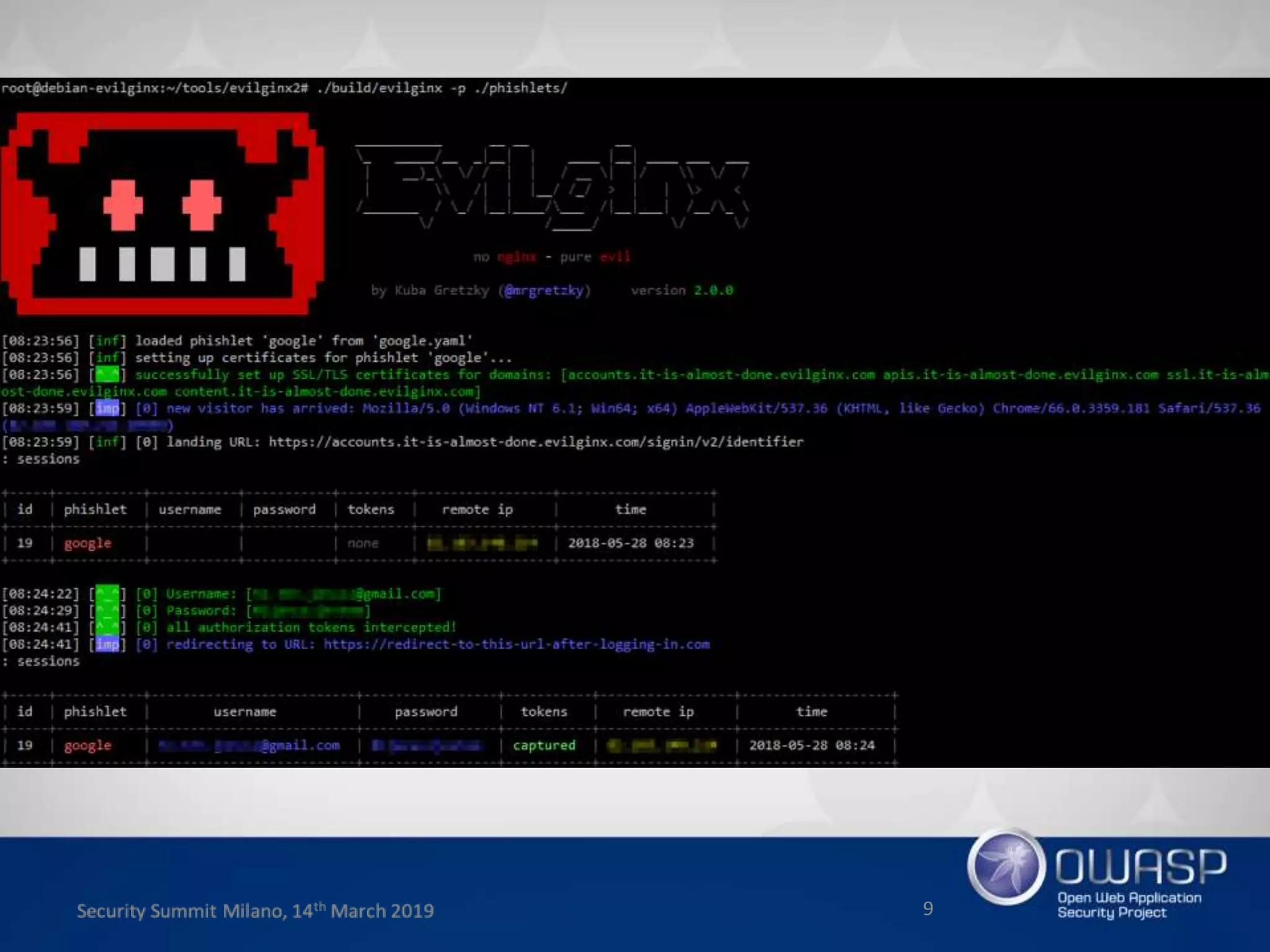
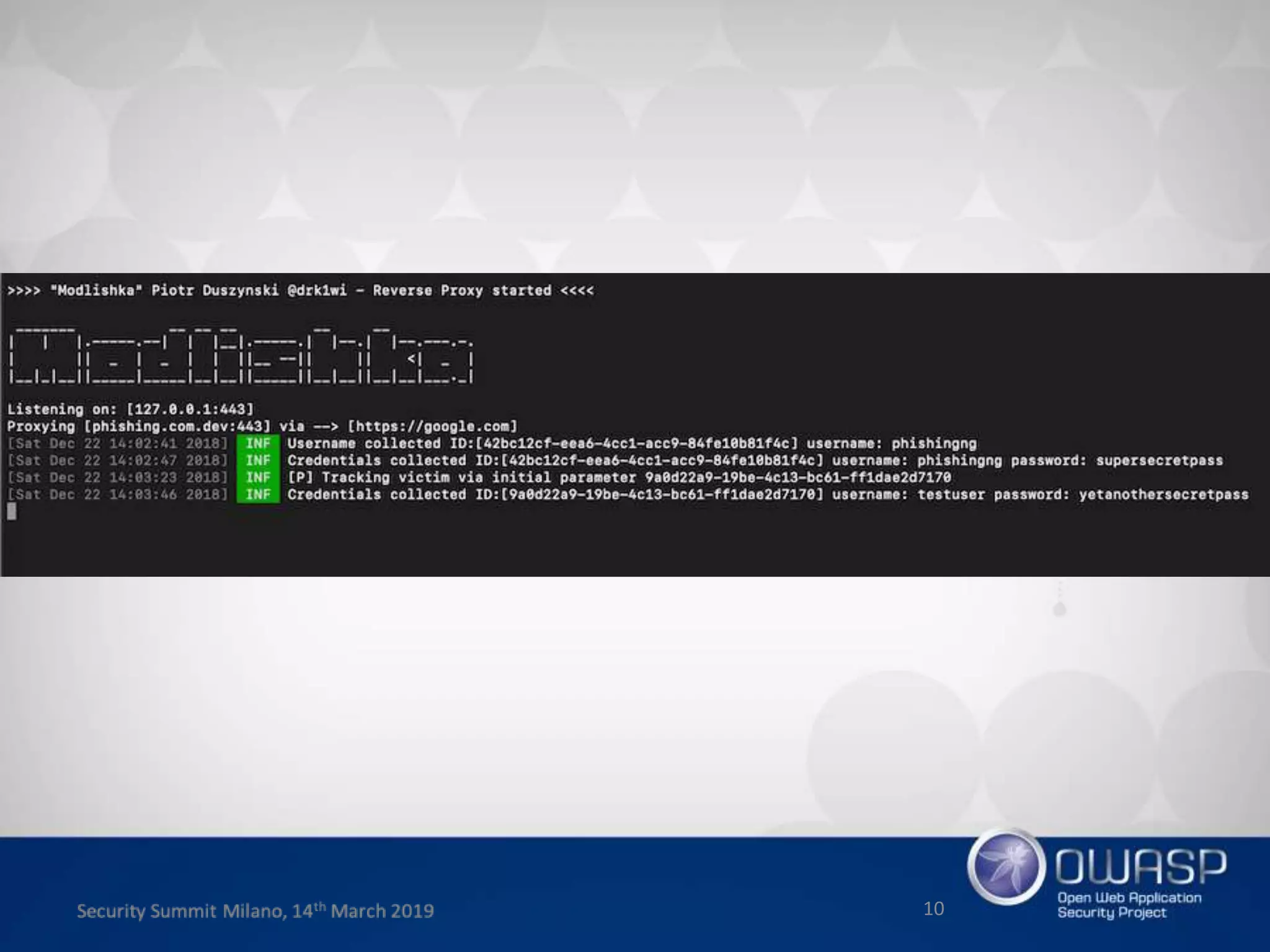
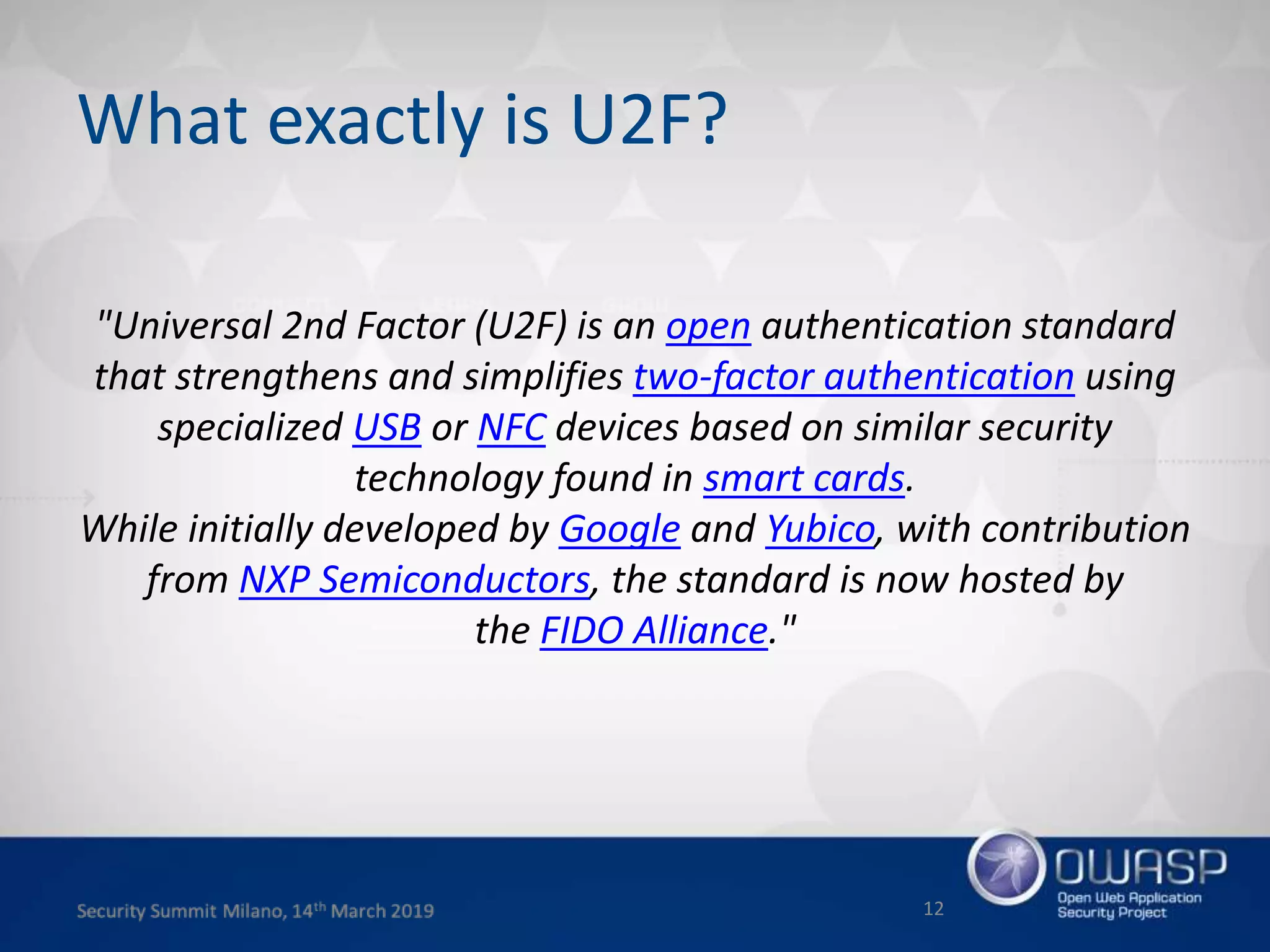
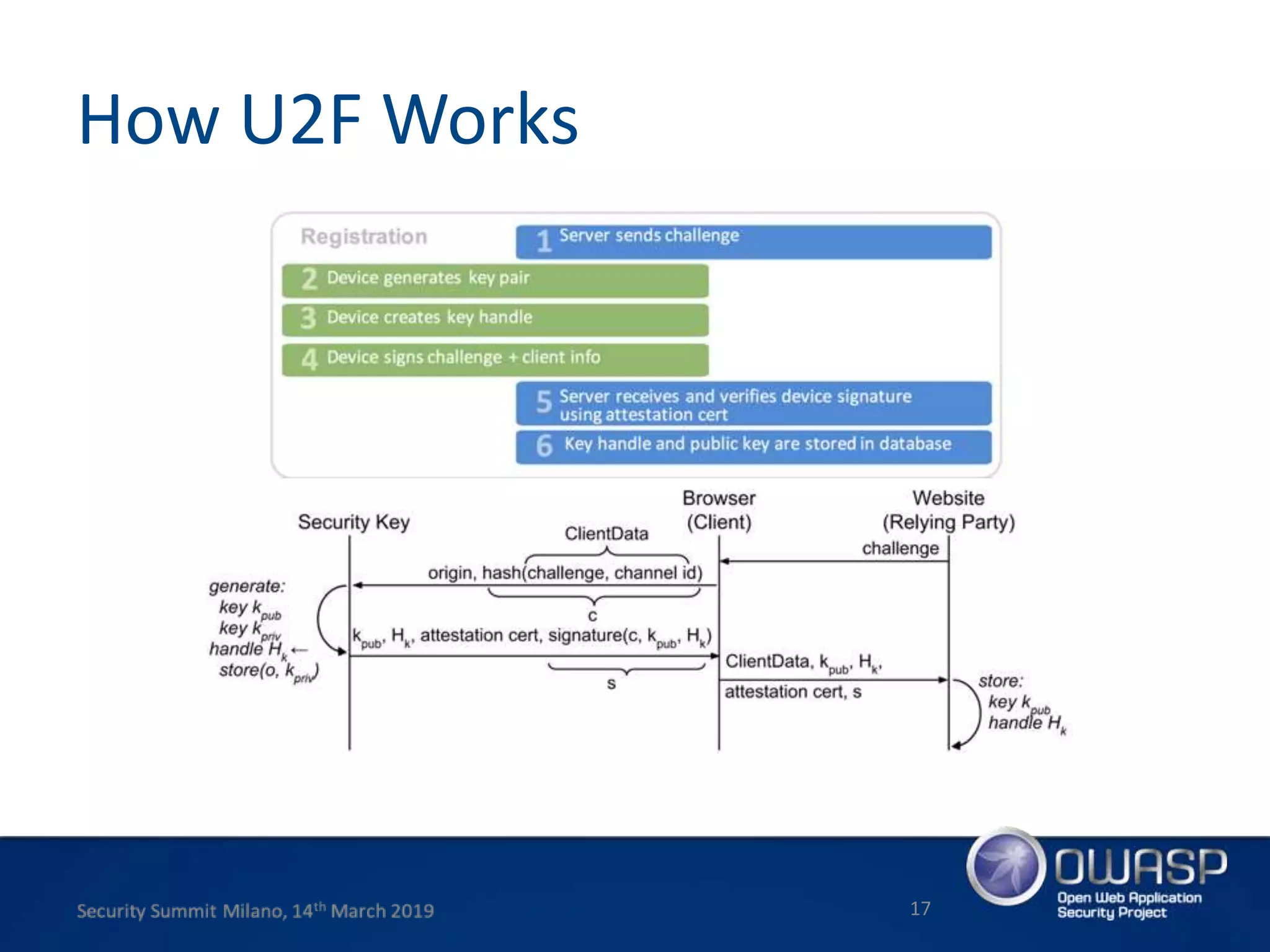
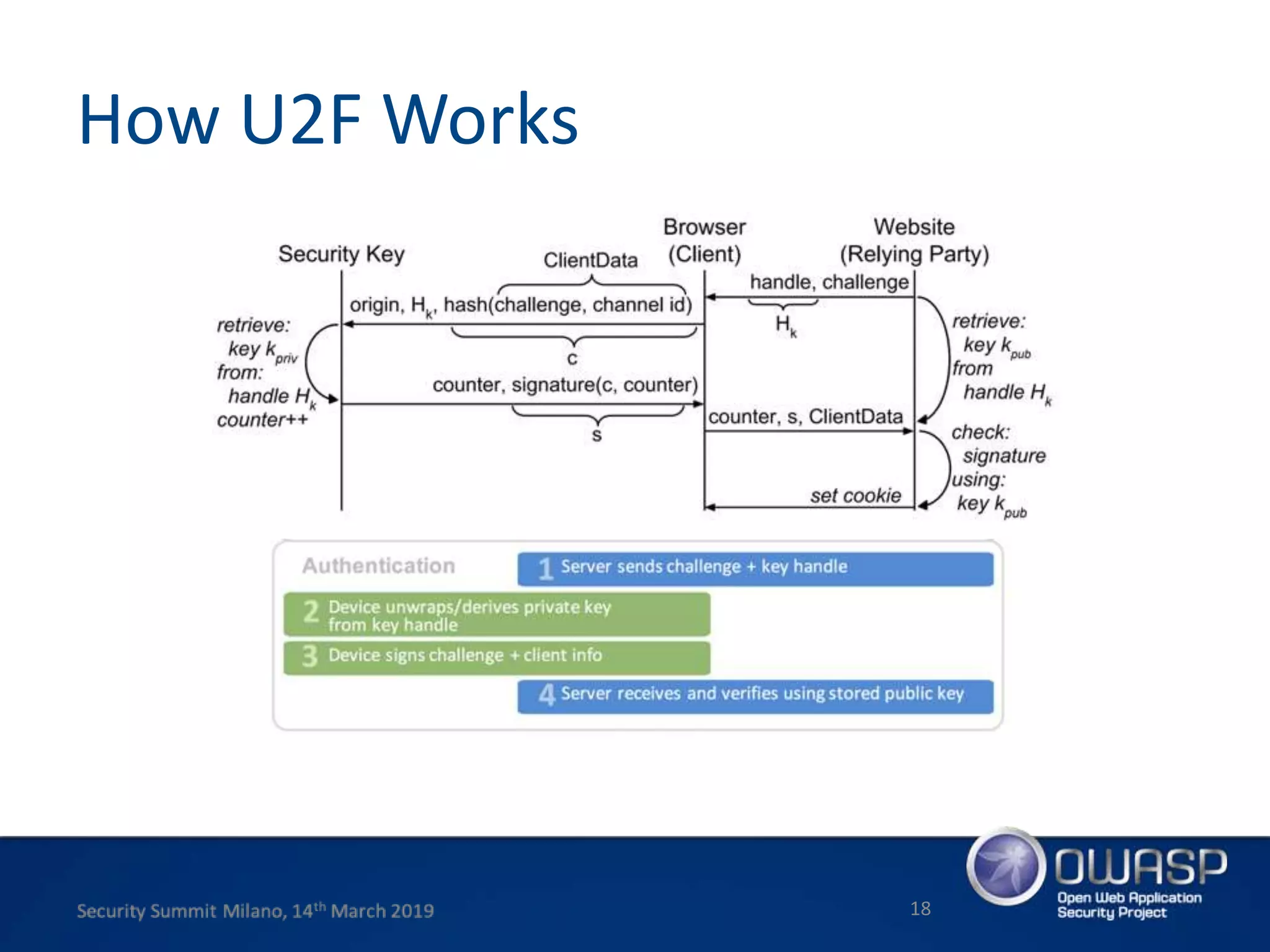
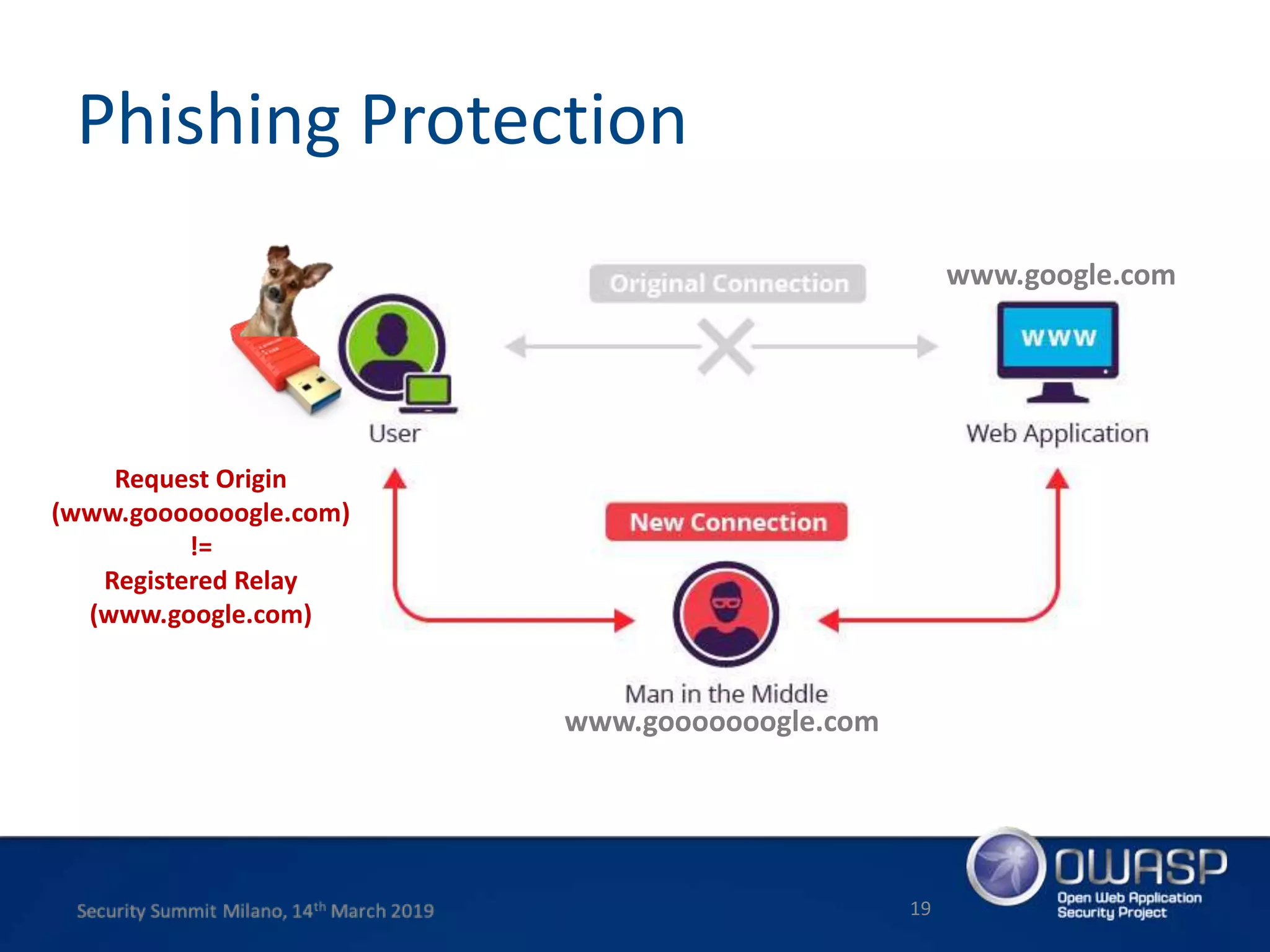
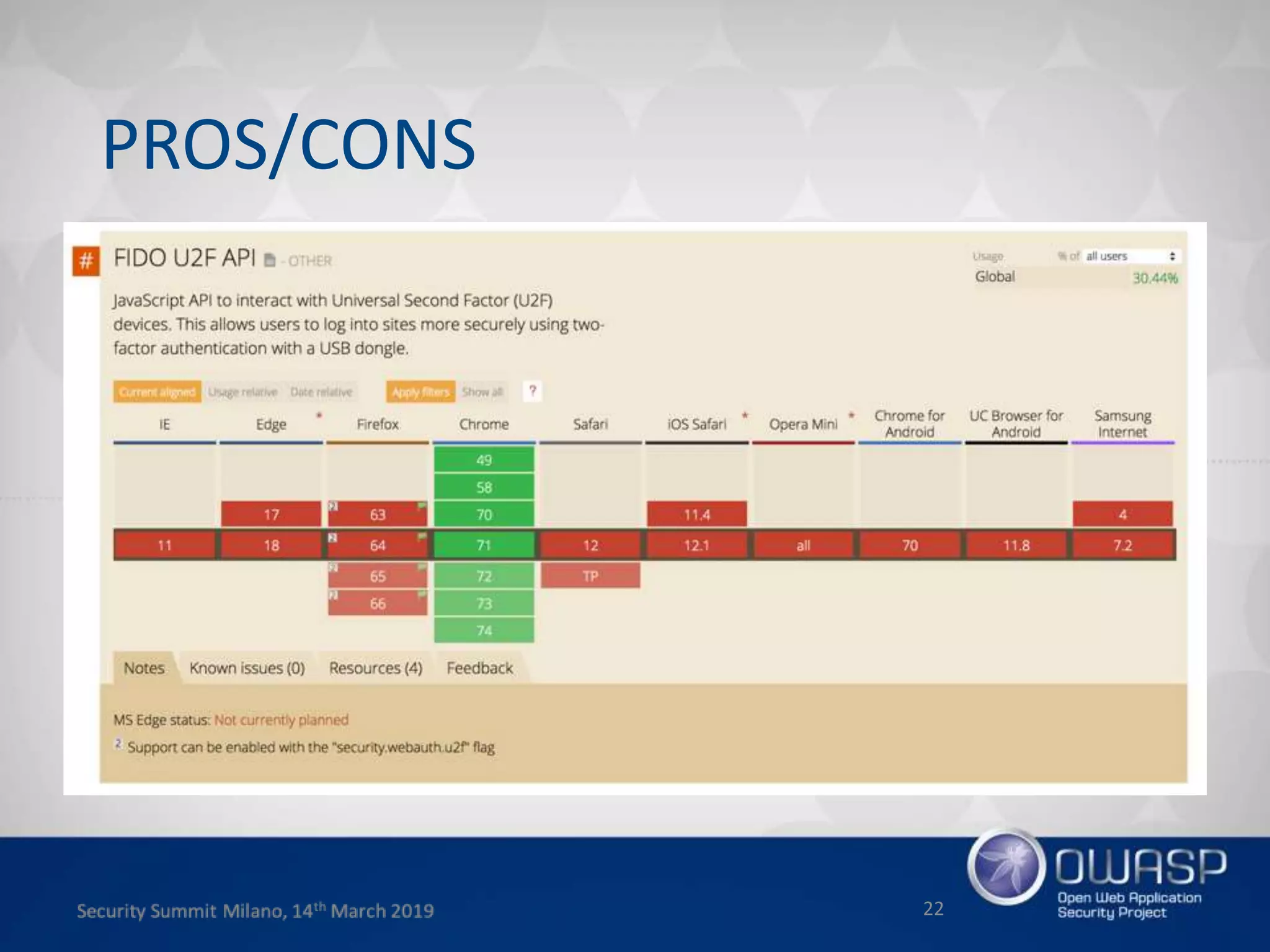
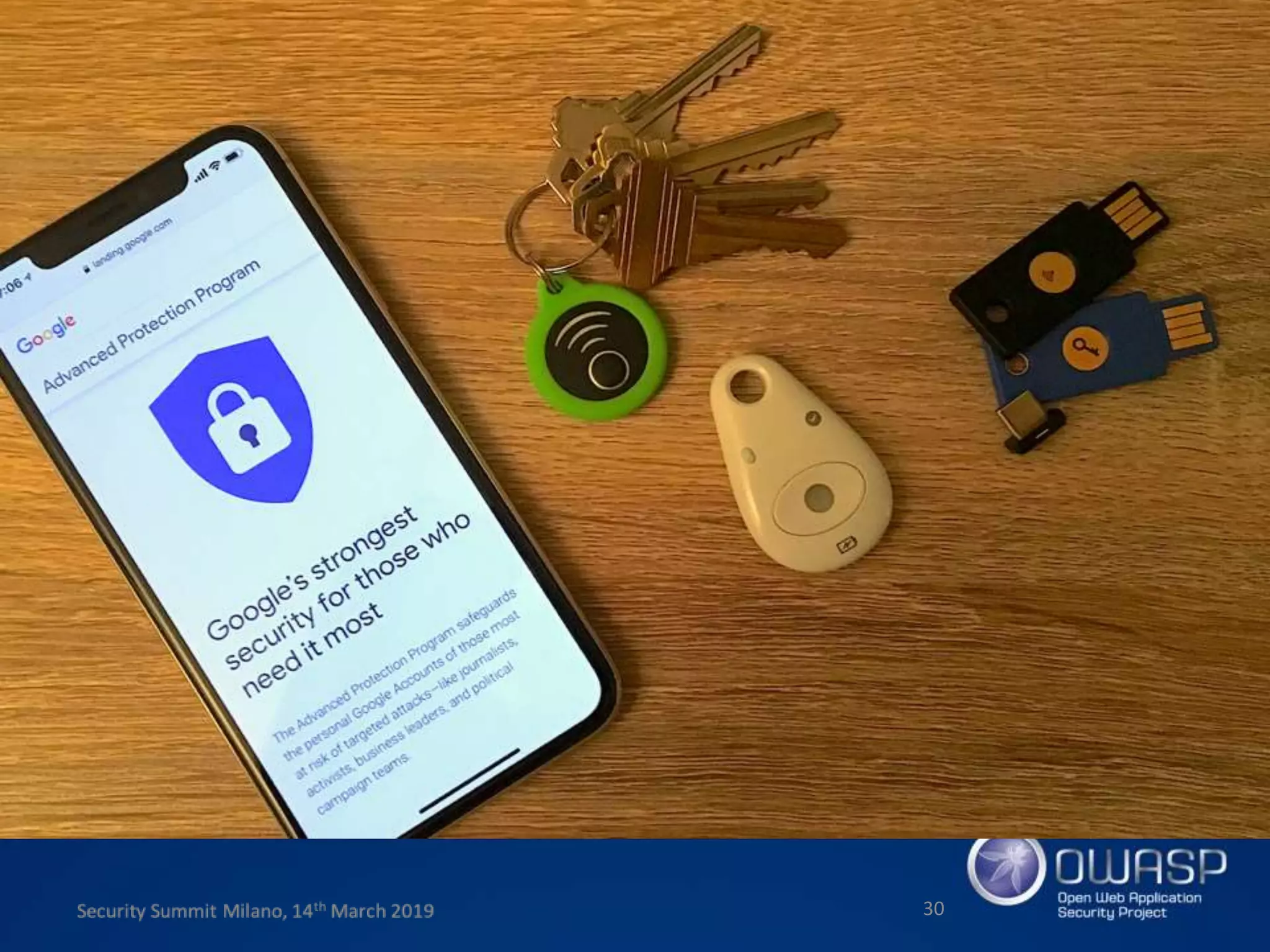
This document summarizes a presentation about new phishing techniques and the use of Universal 2nd Factor (U2F) authentication to help prevent phishing. U2F uses specialized USB or NFC devices to strengthen two-factor authentication with challenge-response authentication that cannot be spoofed. The presentation discusses how U2F provides phishing protection and privacy by involving the website origin and using public key cryptography tied to the device. It also covers how U2F has evolved into the passwordless FIDO2 standard. The presentation concludes with a reminder that phishing continues evolving and users need to be careful of URLs visited while technical solutions advance.