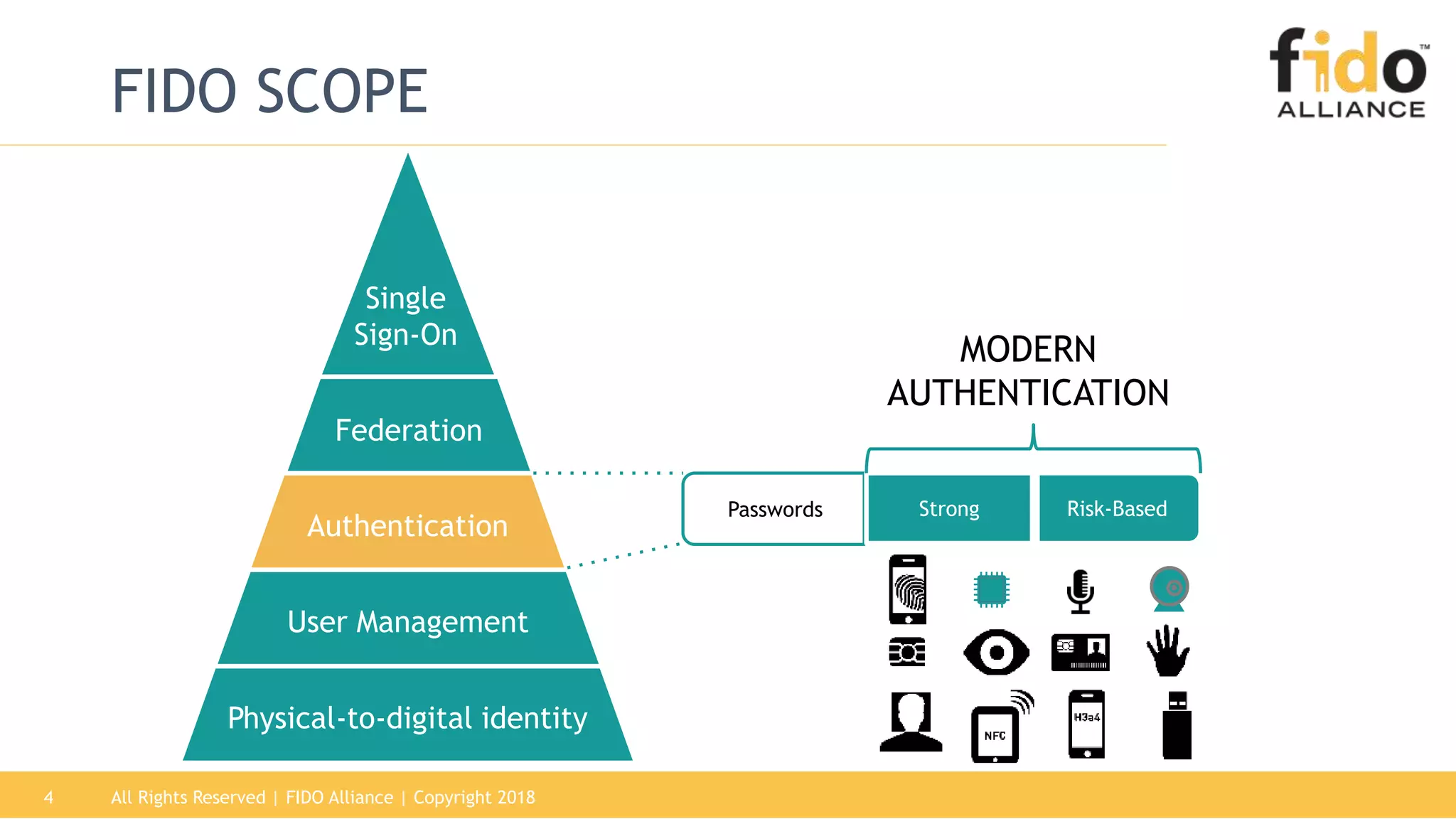
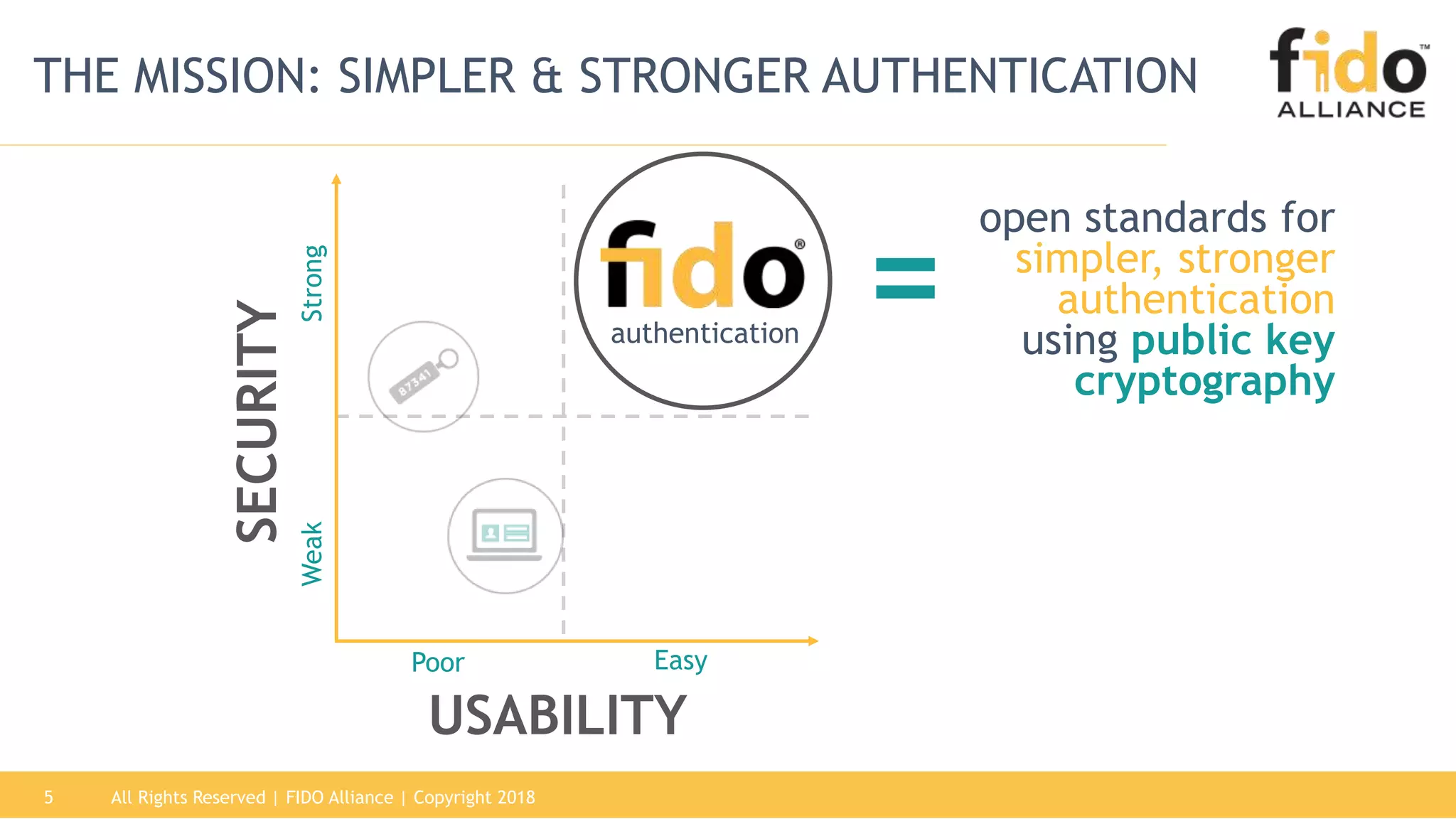
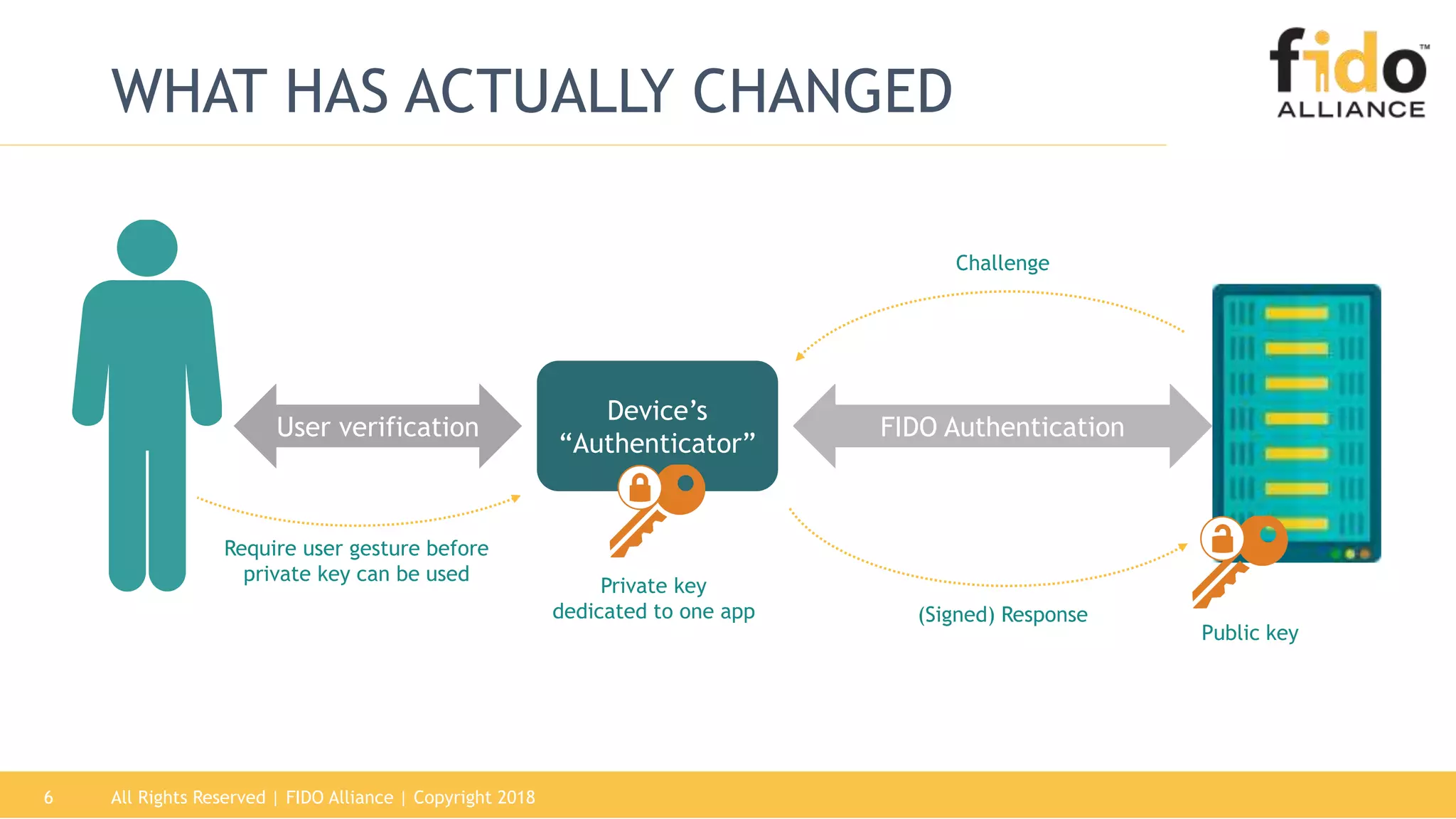
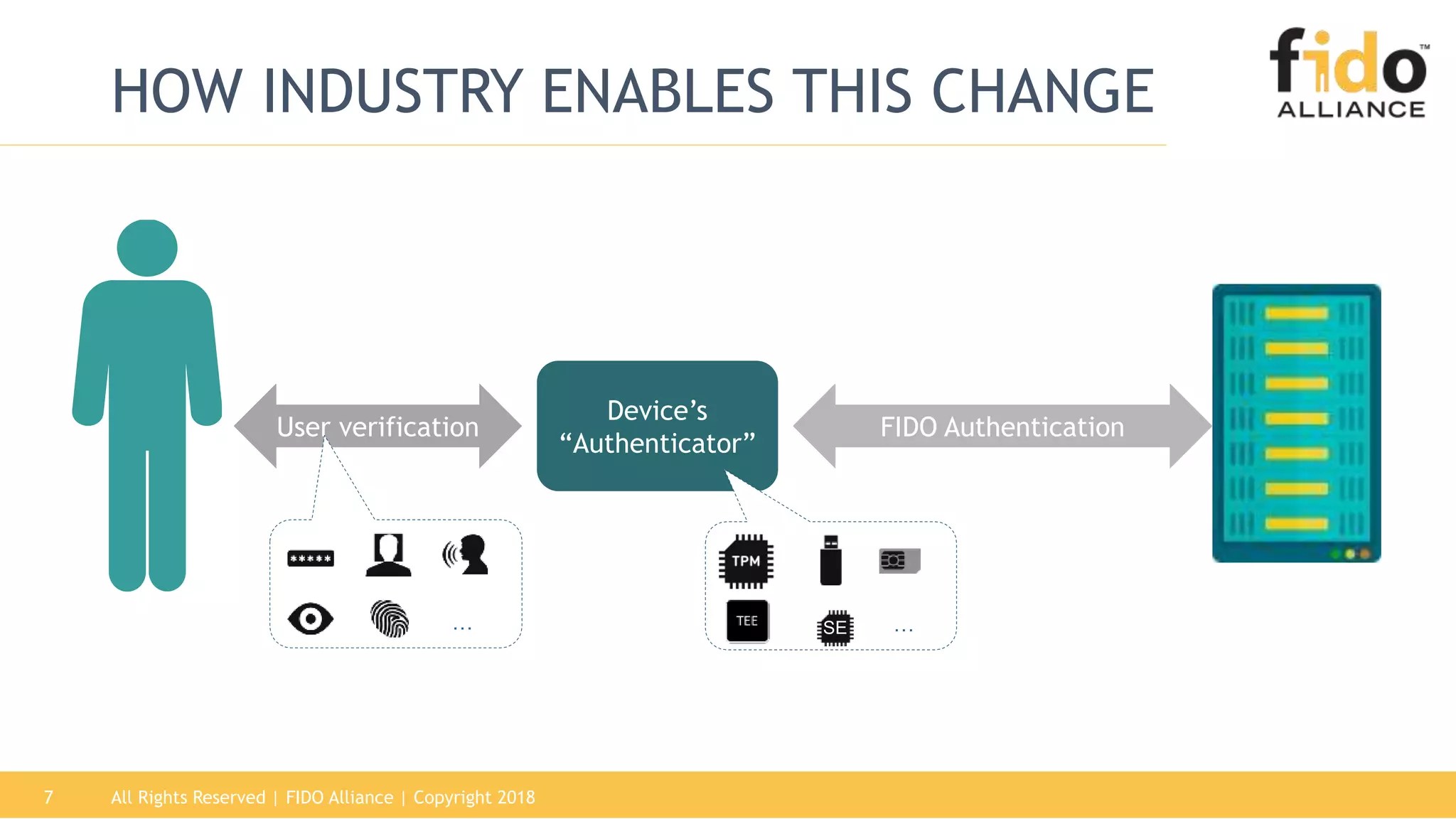
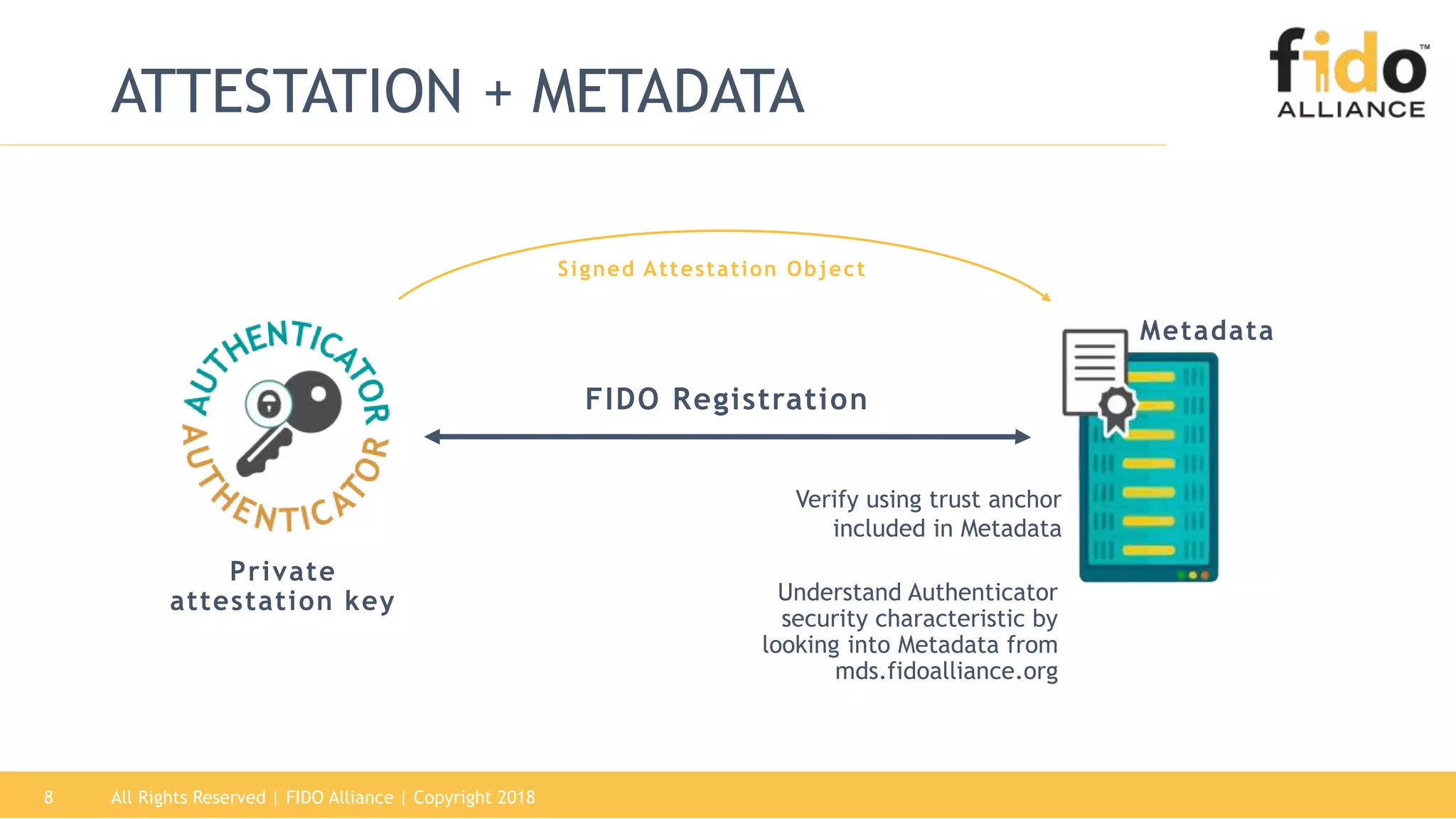
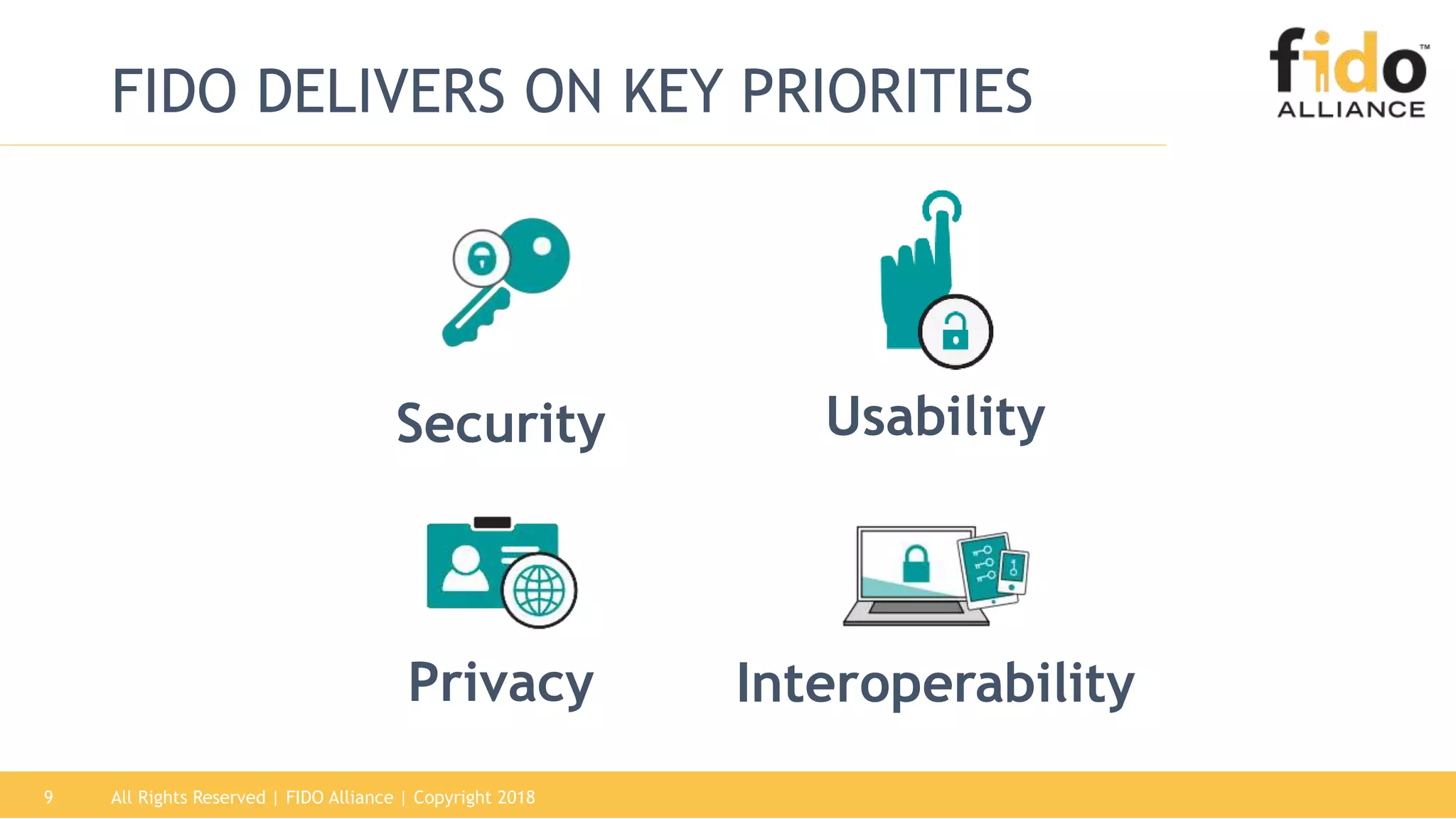
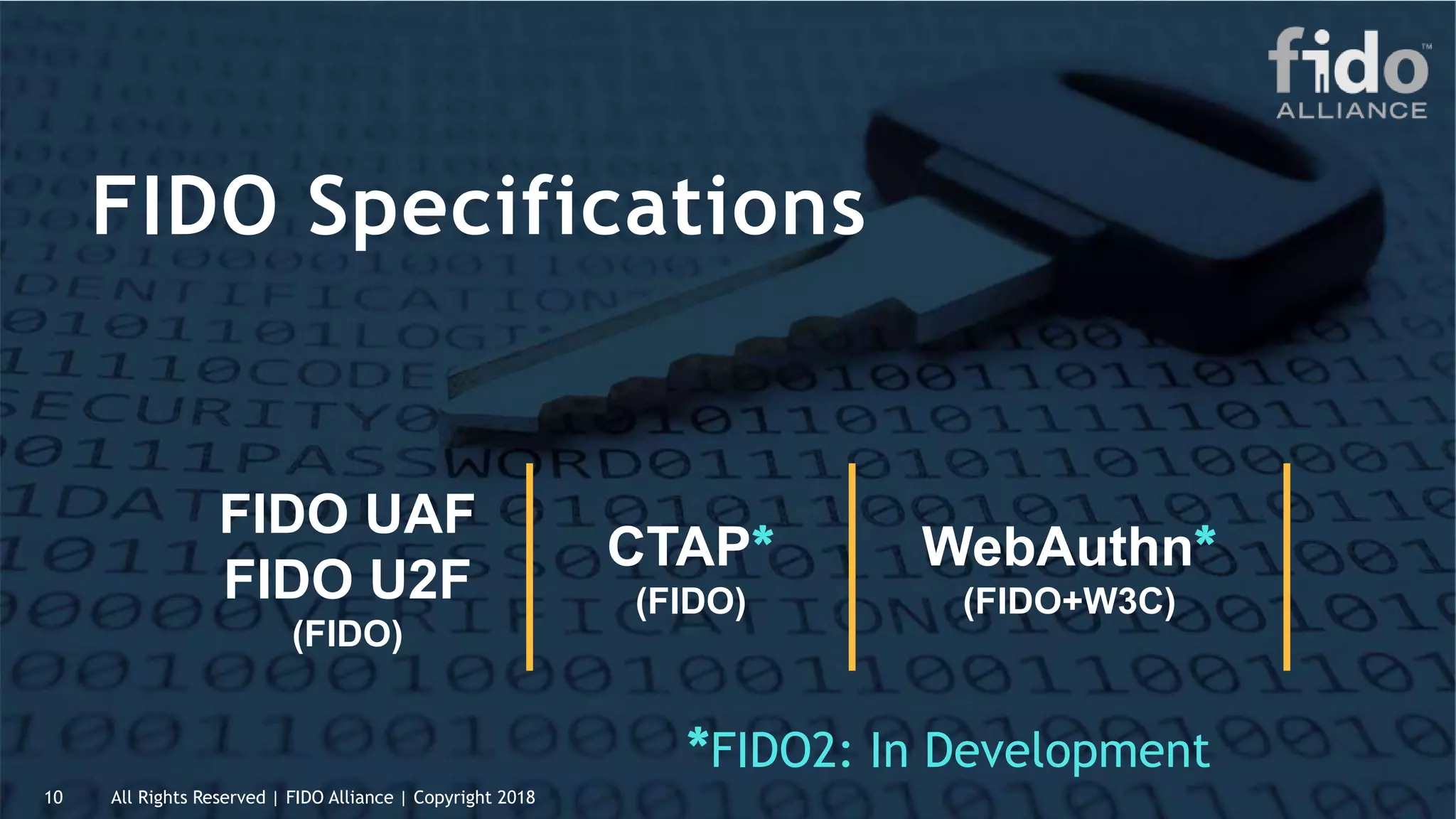
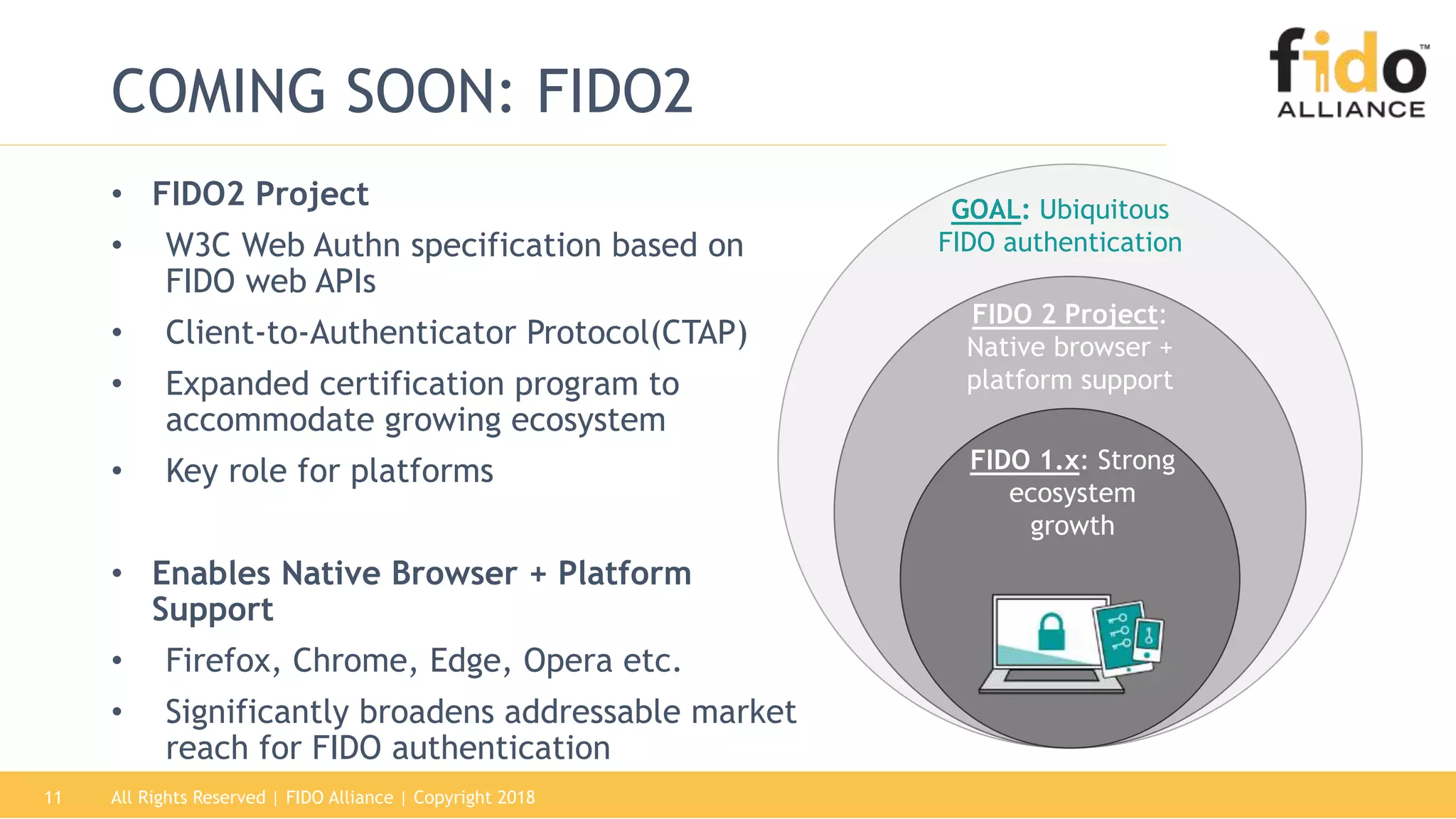
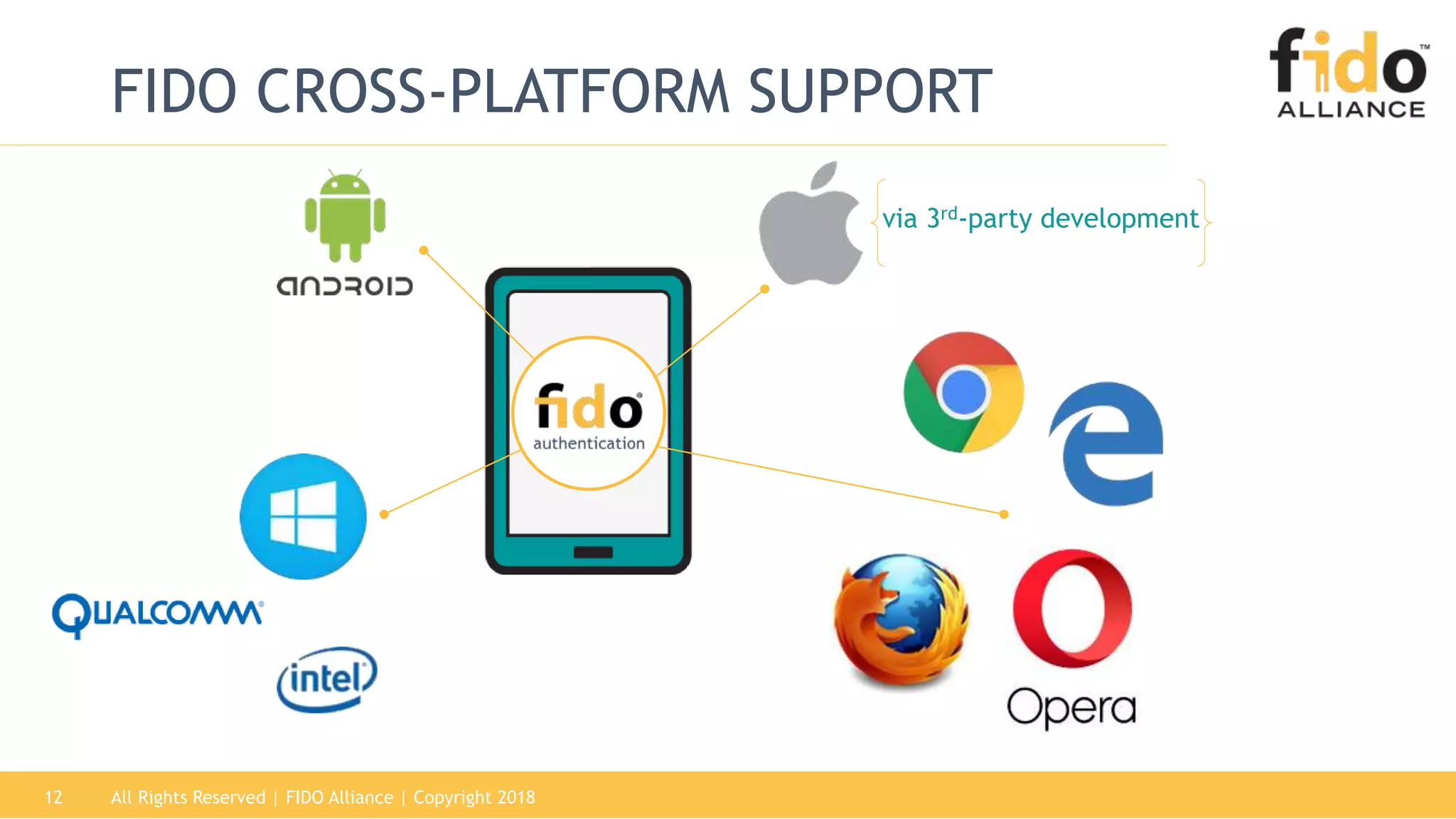
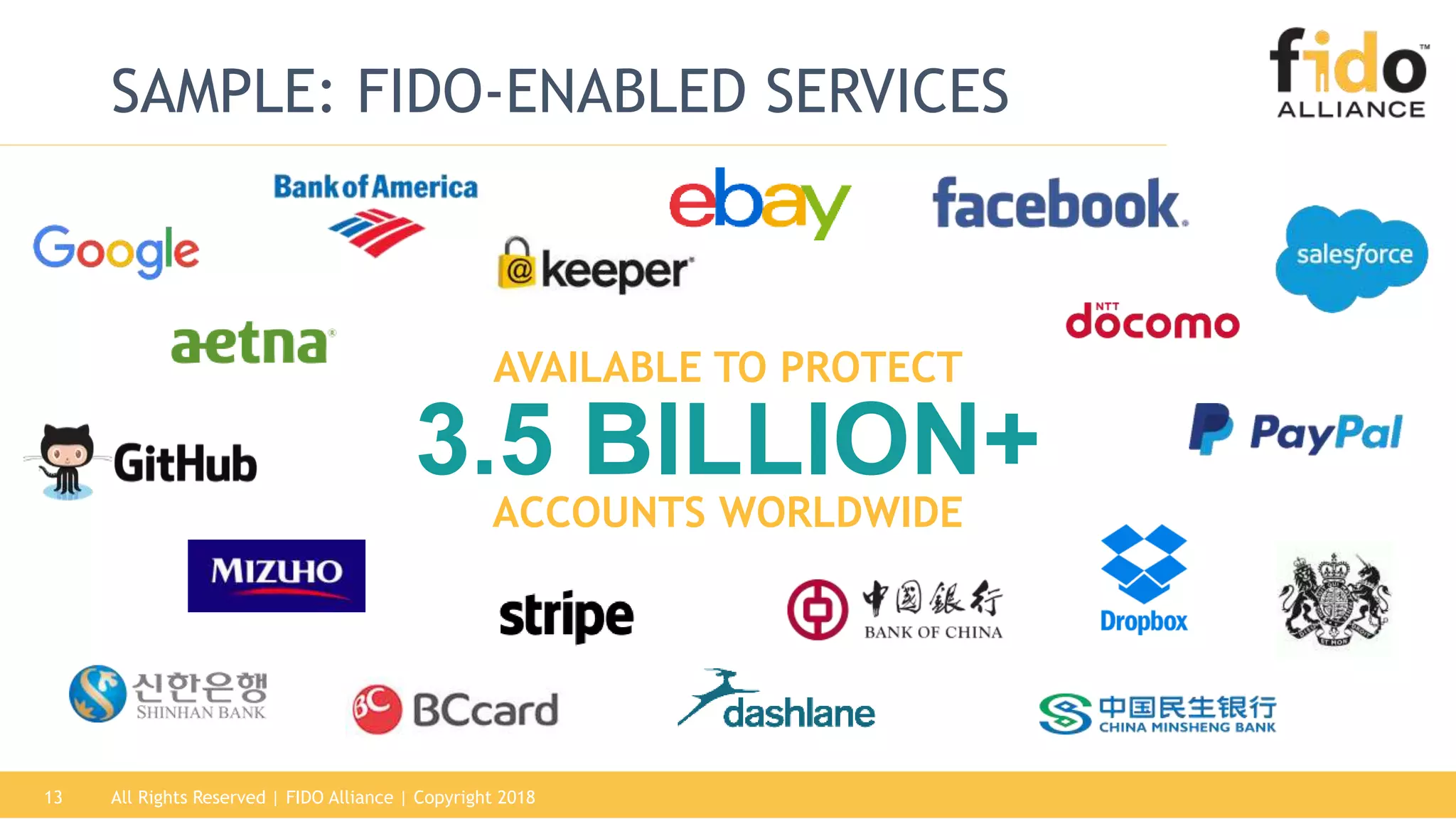
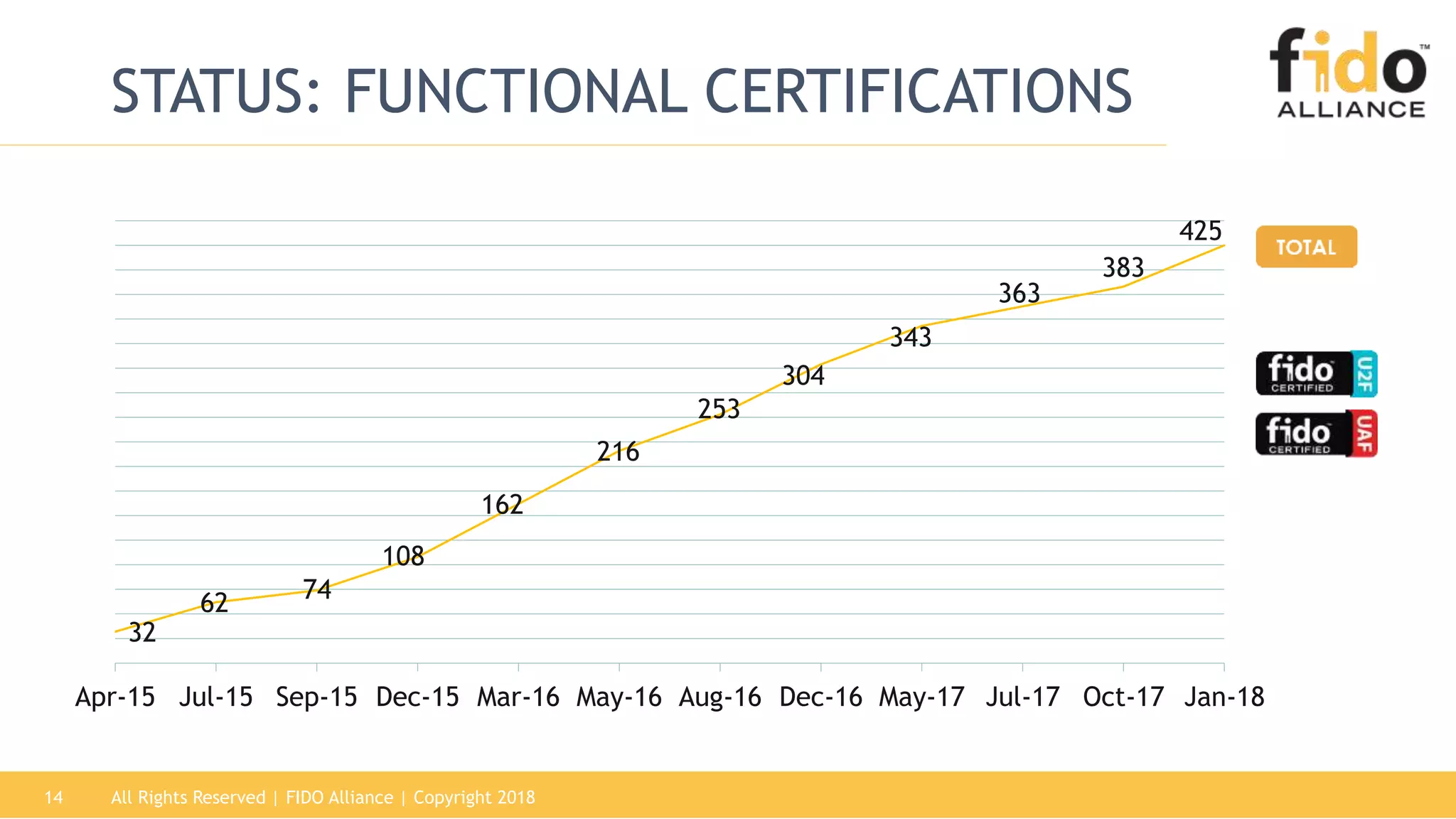
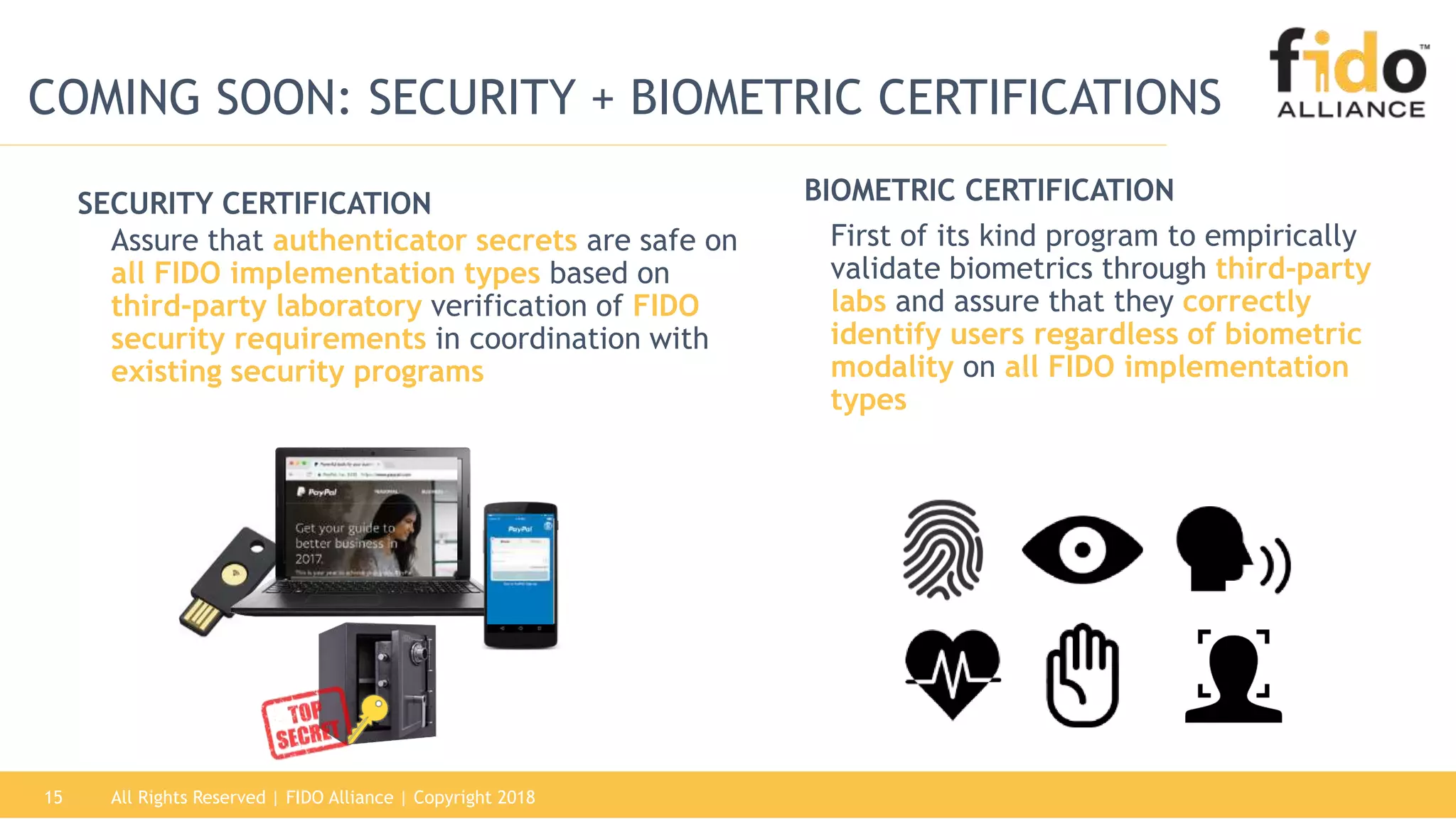
This document summarizes the FIDO Alliance's vision and status. It discusses how authentication has become a major problem and how over 250 organizations are working together through the FIDO Alliance to solve this problem by developing open standards for simpler and stronger authentication using public key cryptography. The FIDO Alliance aims to deliver security, privacy, interoperability and usability through specifications such as FIDO UAF, FIDO U2F and the upcoming FIDO2/WebAuthn specifications. The Alliance has seen strong growth in functional certifications and aims to also offer security and biometric certifications to validate authenticator safety and accurate user identification.