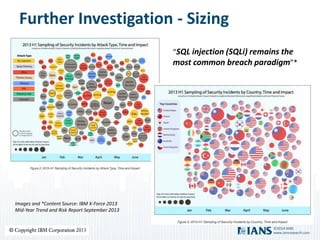
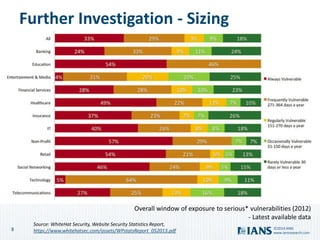
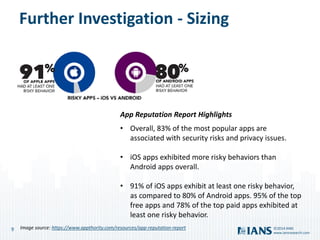
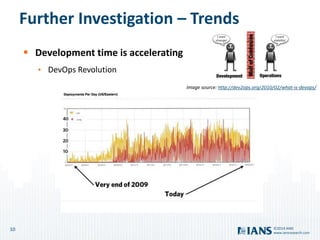
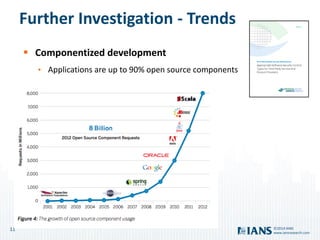
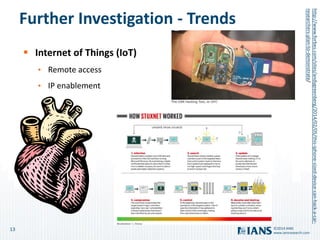
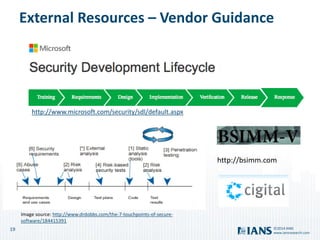
The document outlines the importance of application security, highlighting the potential costs and risks associated with inadequate measures. It discusses various approaches to bolster application security, from minimal testing to fully integrating security into the software development lifecycle (SDLC). Additionally, it emphasizes the need for continuous improvement, collaboration, and effective resource utilization to develop a robust security program.