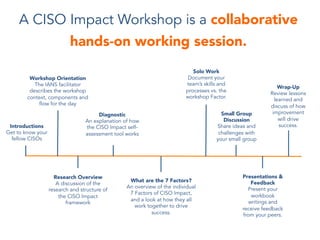
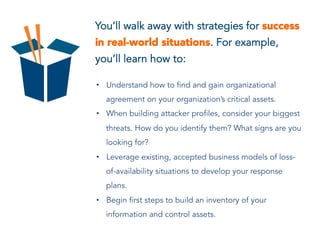
CISOs face continuous changes in threats, security technologies, and business conditions that complicate their mission to protect critical assets. While technical skills are essential, the top performing CISOs engage with the business and practice proactive organizational engagement. This document outlines the 7 Factors of CISO Impact framework, which provides a structured approach for CISOs to measure and improve their performance in areas like gaining command of facts, engaging stakeholders, and driving insight to enable action. It also describes workshops where CISOs can assess their skills, learn from peers, and develop concrete plans to strengthen areas for improvement.