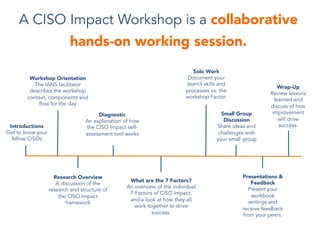
The document discusses the challenges faced by CISOs in protecting organizational assets and managing risk due to a lack of control over processes and people. It introduces the CISO Impact framework which provides a structured approach for CISOs to measure and improve their performance in proactively engaging with the organization through 7 defined factors. The framework includes a diagnostic assessment and workshops to help CISOs understand their strengths/weaknesses and develop concrete plans to advance each factor and their overall impact.