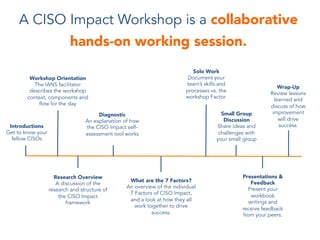
CISOs face continuous changes in threats, security technologies, and business conditions that complicate their mission to protect organizational assets. Research shows top performers engage proactively with the business through soft skills rather than just technical skills. The CISO Impact framework defines seven factors of proactive organizational engagement that CISOs can measure themselves against, including embedding information security into key business processes. Workshops help CISOs assess strengths and weaknesses, develop action plans, and discuss challenges with peers.