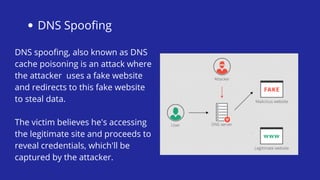
This document provides an overview of social engineering attacks. It defines social engineering as manipulating people into giving up confidential information through deception and manipulation. Various social engineering principles are described, including authority, social proof, urgency, and scarcity, which attackers use to carry out successful attacks. Different types of social engineering attacks are also outlined, such as phishing, spear phishing, baiting, DNS spoofing, honey traps, tailgating, shoulder surfing, and impersonation attacks.