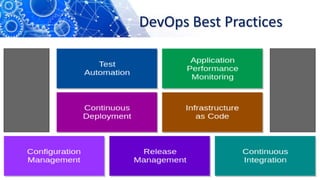
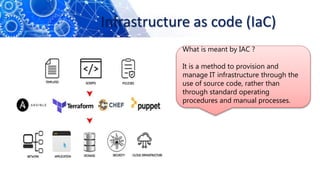
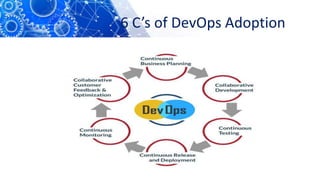
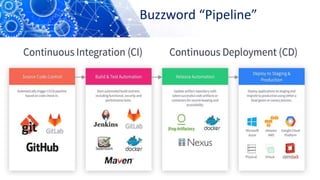
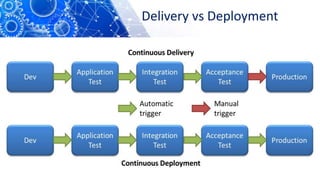
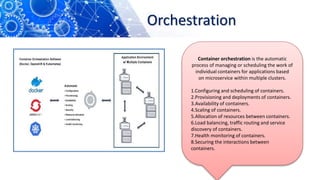
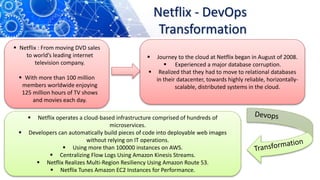
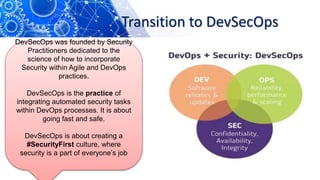
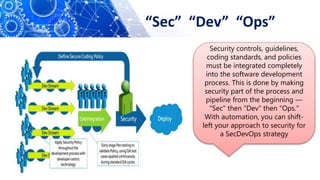
The document discusses the transition from DevOps to DevSecOps, emphasizing the integration of security into DevOps processes to create a culture of security within development teams. It outlines key concepts such as continuous delivery, containerization, and automated workflows, highlighting the significance of practices like Infrastructure as Code (IaC) and Security as Code (SAC). The case study of Netflix illustrates the successful adoption of DevOps practices that led to improved efficiency and resilience in a cloud-based infrastructure.