The document discusses aggregation computation over distributed data streams, focusing on challenges like duplicate-resilient aggregates in large-scale monitoring applications. It introduces the Flajolet-Martin sketch algorithm as a probabilistic method for distinct counting in multi-sets with limited memory and processing power. Key considerations include communication, computational, and space costs associated with these algorithms in distributed environments.


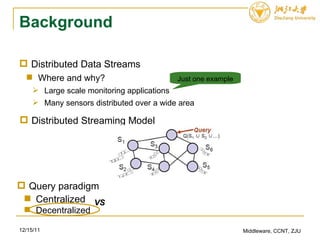


![Flajolet-Martin Sketch(Cont.) Preliminary what do we need? the Multi-set M, containing all items/records, and |M| = n the upper bound on the number of distinct items/records U, which is more than n the bitmap B, consisting of L elements, and 2 L = U the hash function h(x: item/record), transforming each items into a binary string distributed uniformly over the range of [1…2 L ], just like b 1 b 2 …b L , in which b 1 is the lowest digit, and b L is the highest the p(x), attaining the left most position of ‘1’ 12/15/11 Middleware, CCNT, ZJU counting not computing 1 1 … 0 B 0 PPT VS Whiteboard ? x record h(x) 1 L](https://image.slidesharecdn.com/aggregationcomputationoverdistributeddatastreams-111215074354-phpapp01/85/Aggregation-computation-over-distributed-data-streams-9-320.jpg)
![Flajolet-Martin Sketch(Cont.) The algorithm itself the core task: Remarking the position of which the leftmost ‘1’ of the hash value recorded by p(x) in bitmap B 12/15/11 Middleware, CCNT, ZJU for i:=1 to L do bitmap[i] :=0 for all x in M do begin index := p(hash(x)); if bitmap[index] = the bitmap[index] :=1; end Why?](https://image.slidesharecdn.com/aggregationcomputationoverdistributeddatastreams-111215074354-phpapp01/85/Aggregation-computation-over-distributed-data-streams-10-320.jpg)
![Flajolet-Martin Sketch(Cont.) The explanation The fact: bitmap[k] equals to 1 iff after execution a pattern of the form 0 k-1 1 has appeared amongst hashed values of records in M The probability: the occurrence probability of the pattern 0 k-1 1 is 1/2 k Occurrence times: so if |M| = n, then bitmap[1] is accessed approximately n/2 times, bitmap[2] approximately n/4 times Extension: bitmap[k] will almost certainly be zero if k >> log 2 (n) and one if k << log 2 (n) wit a fringe of 0 and 1 for k ≈ log 2 (n) Selection: the leftmost 0, the rightmost 1 or something else 12/15/11 Middleware, CCNT, ZJU U The most practical part is over, and the left is very complicated taken for proving and error analysis, namely all about mathematic for i:=1 to L do bitmap[i] :=0 for all x in M do begin index := p(hash(x)); if bitmap[index] = the bitmap[index] :=1; end](https://image.slidesharecdn.com/aggregationcomputationoverdistributeddatastreams-111215074354-phpapp01/85/Aggregation-computation-over-distributed-data-streams-11-320.jpg)