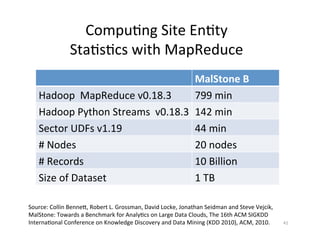
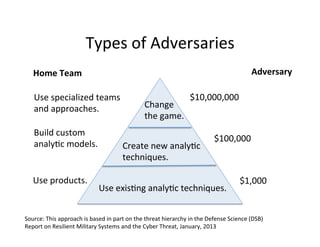
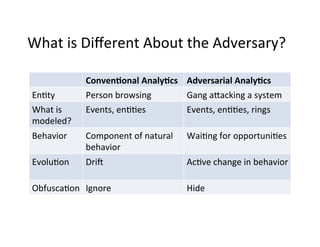
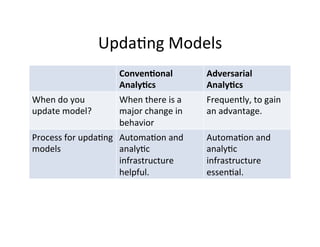
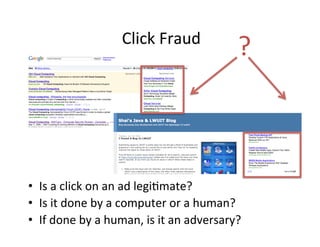
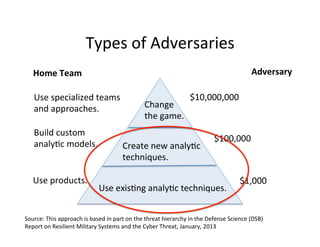
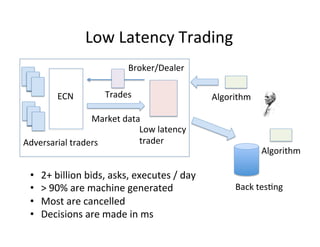
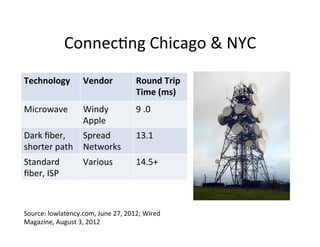
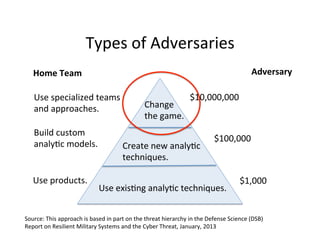
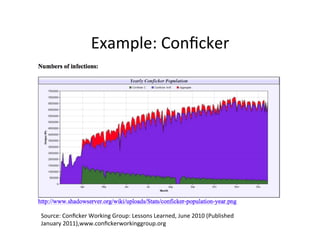
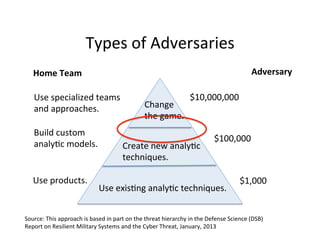
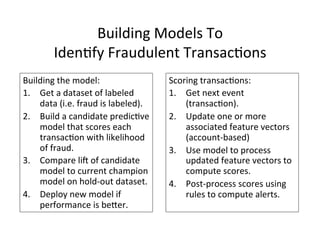
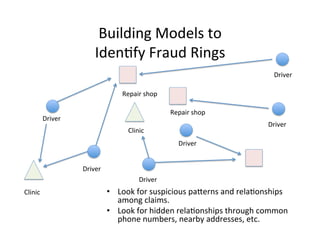
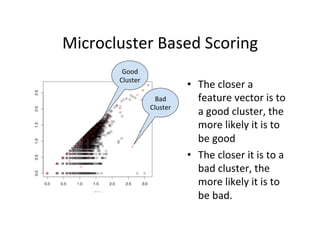
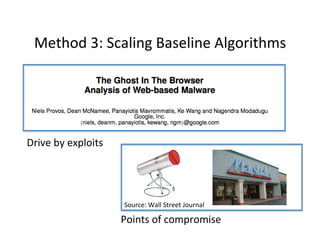
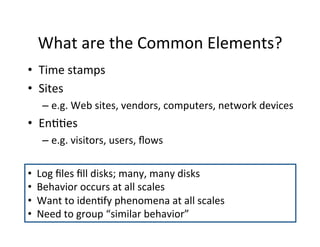
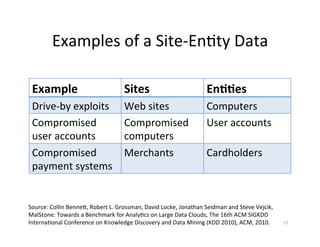
The document discusses adversarial analytics and its differences compared to conventional analytics, highlighting the tactics used by groups or criminal rings to exploit vulnerabilities for financial gain. Examples such as the TJX compromise illustrate how large datasets complicate fraud detection and require tailored analytical models to identify malicious behavior. It emphasizes the need for rapid updates to strategies and models to stay ahead of adversaries in the evolving threat landscape.
















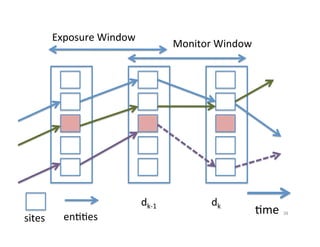

![Subsequent
Propor-on
of
Marks
• Fix
a
site
s[j]
• Let
A[j]
be
en--es
that
transact
during
ExpWin
and
if
en-ty
is
marked,
then
visit
occurs
before
mark
• Let
B[j]
be
all
en--es
in
A[j]
that
become
marked
some-me
during
the
MonWin
• Subsequent
propor-on
of
marks
is
r[j]
=
|
B[j]
|
/
|
A[j]
|
• Easily
computed
with
MapReduce.](https://image.slidesharecdn.com/grossman-adversarial-analytics-14-v4-131030193448-phpapp02/85/Adversarial-Analytics-2013-Strata-Hadoop-World-Talk-40-320.jpg)