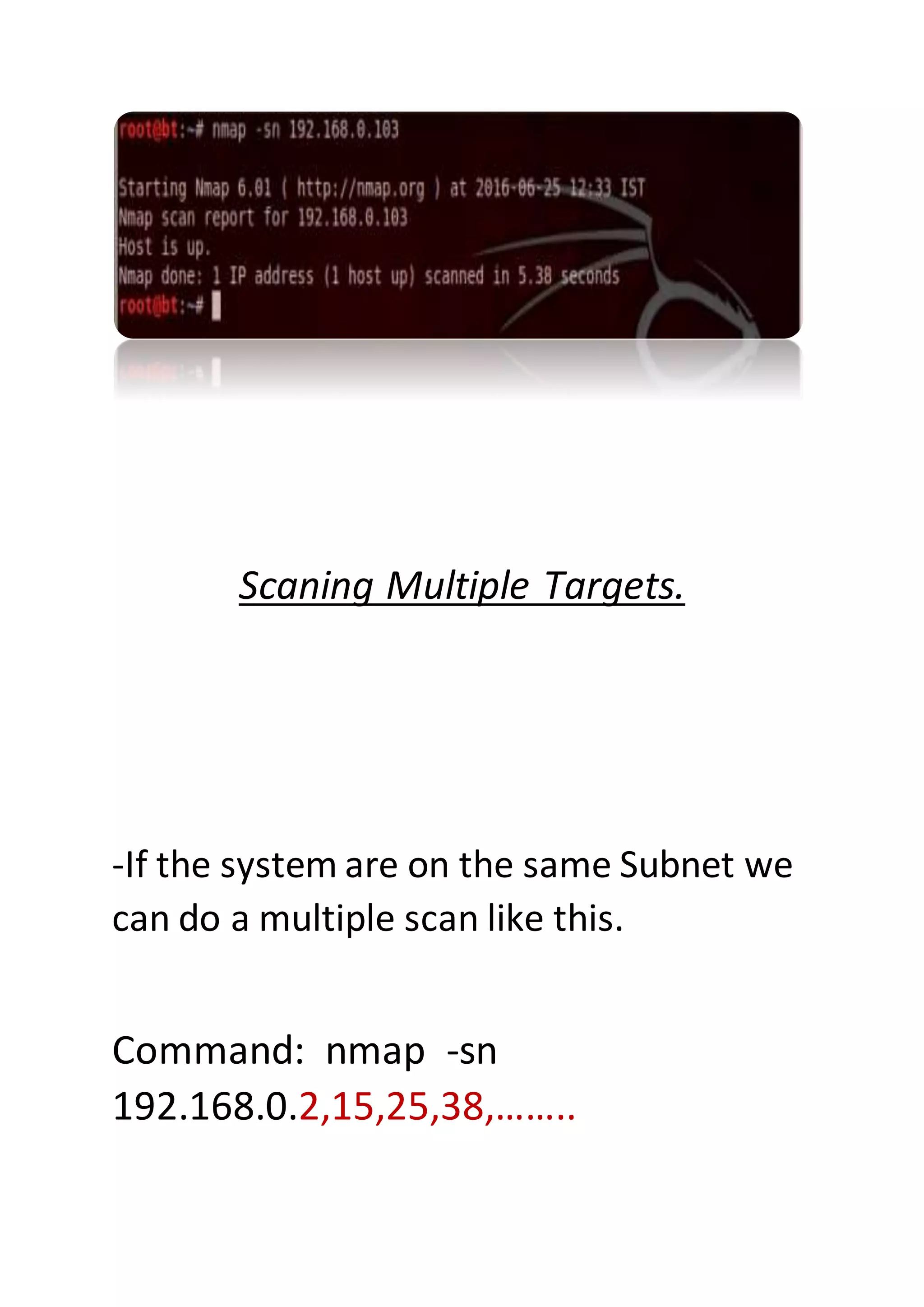
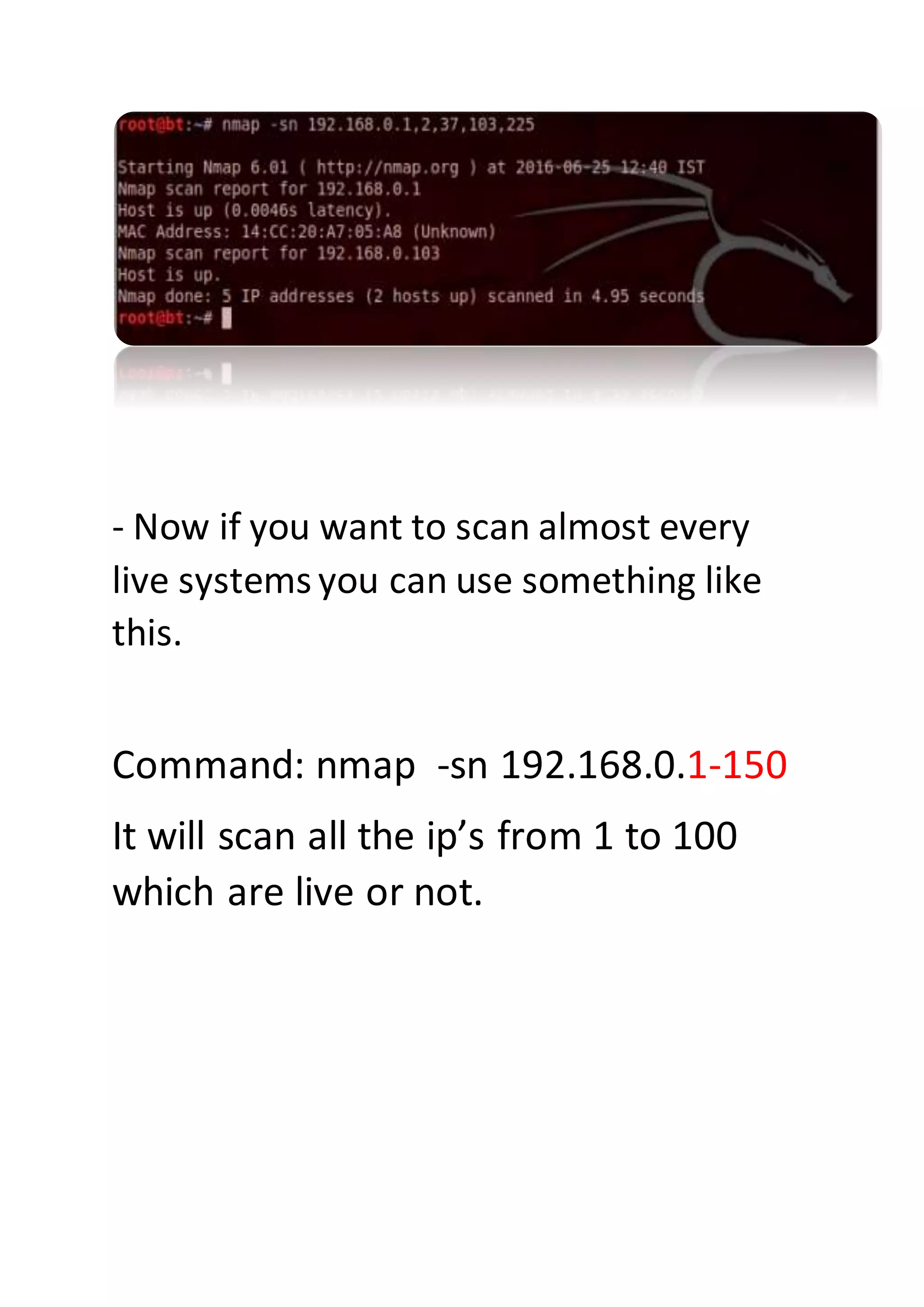
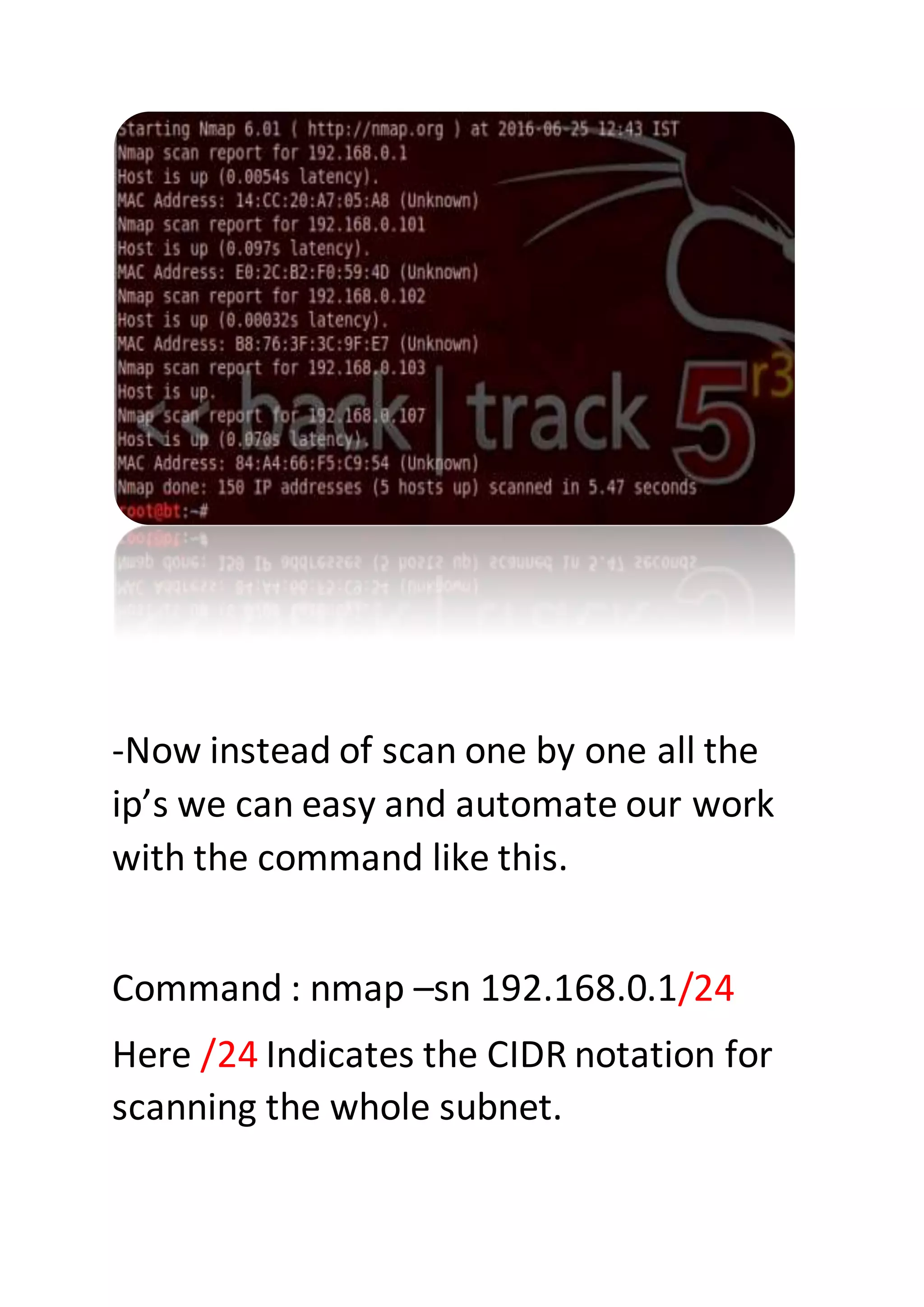
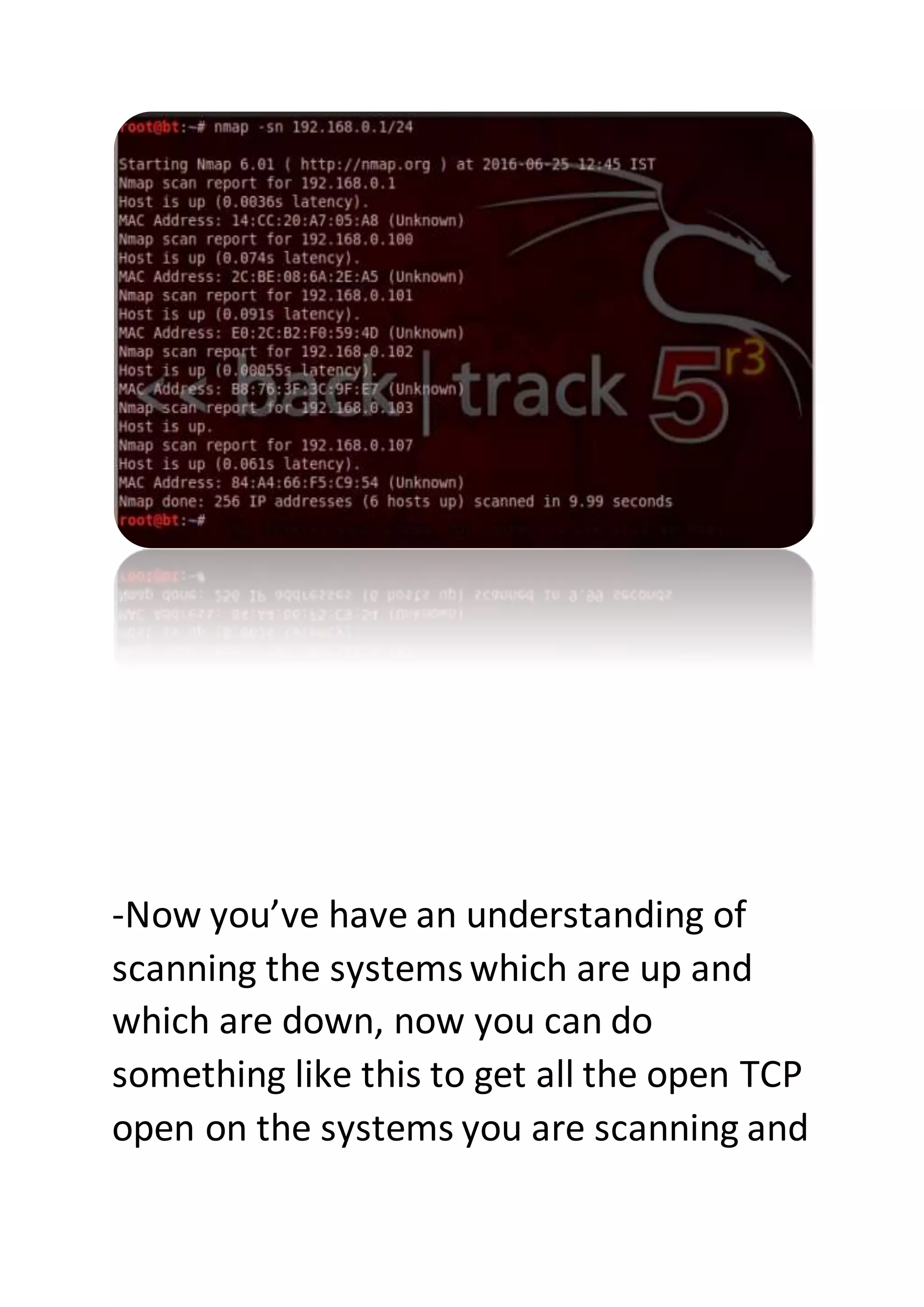
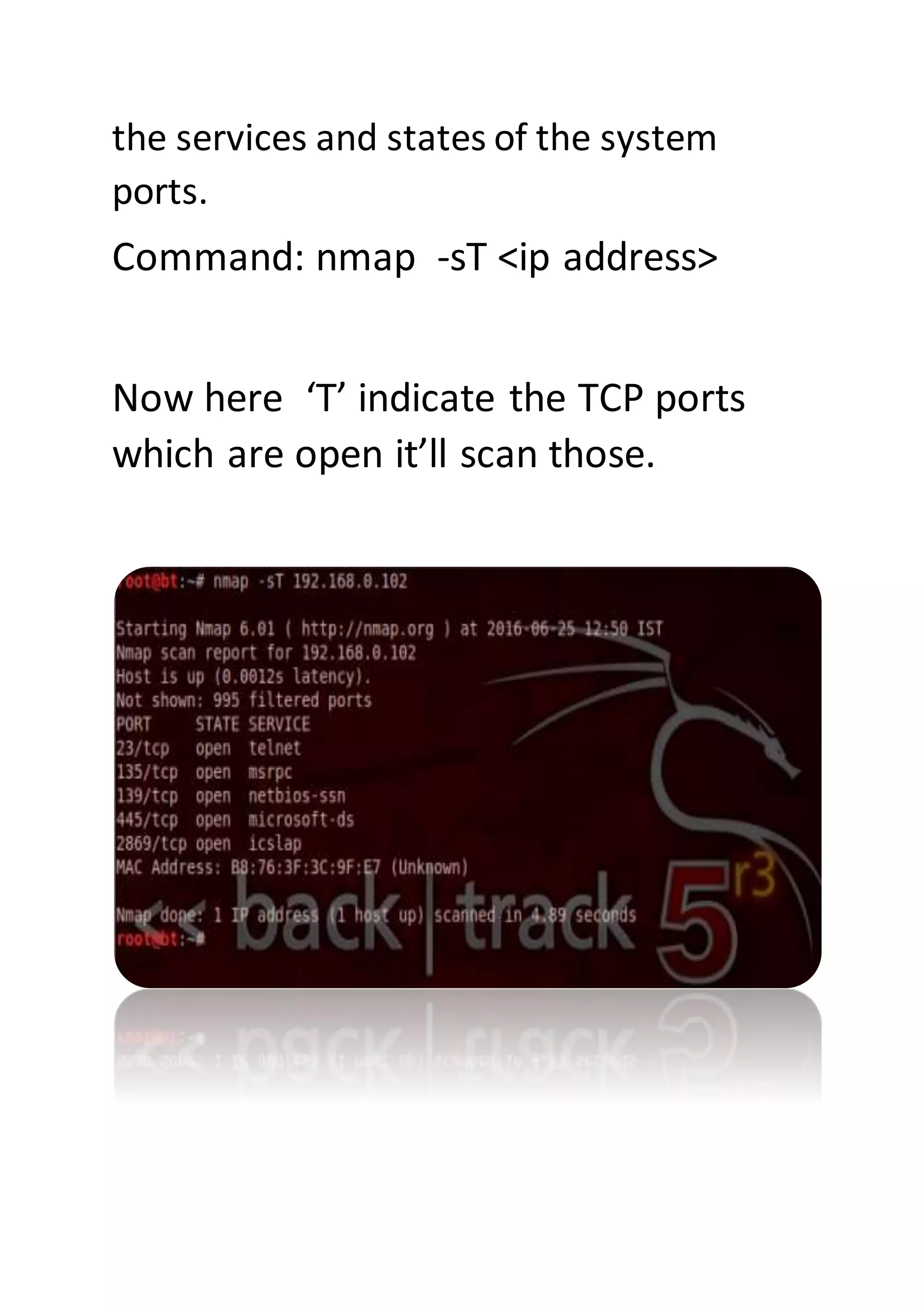
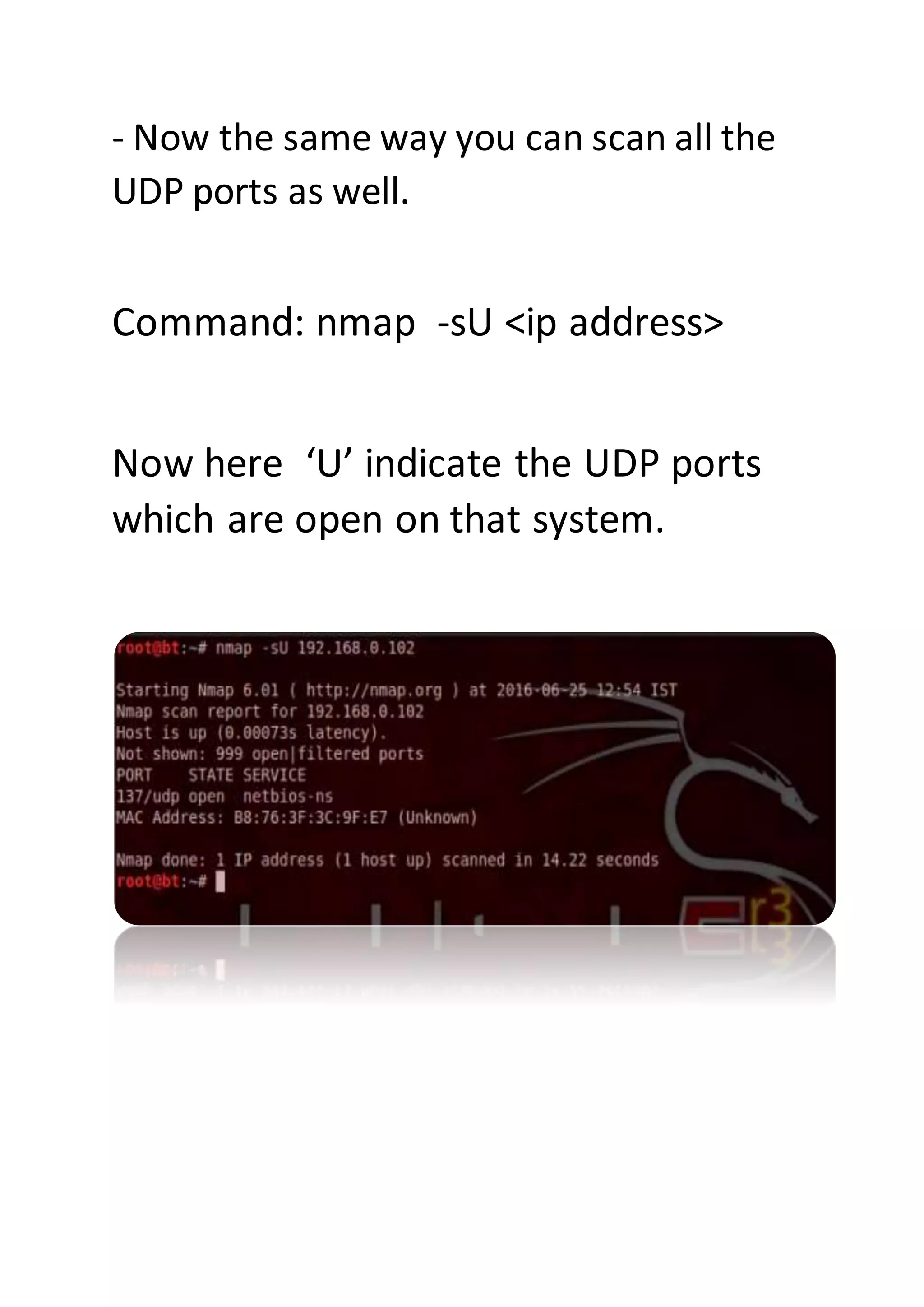
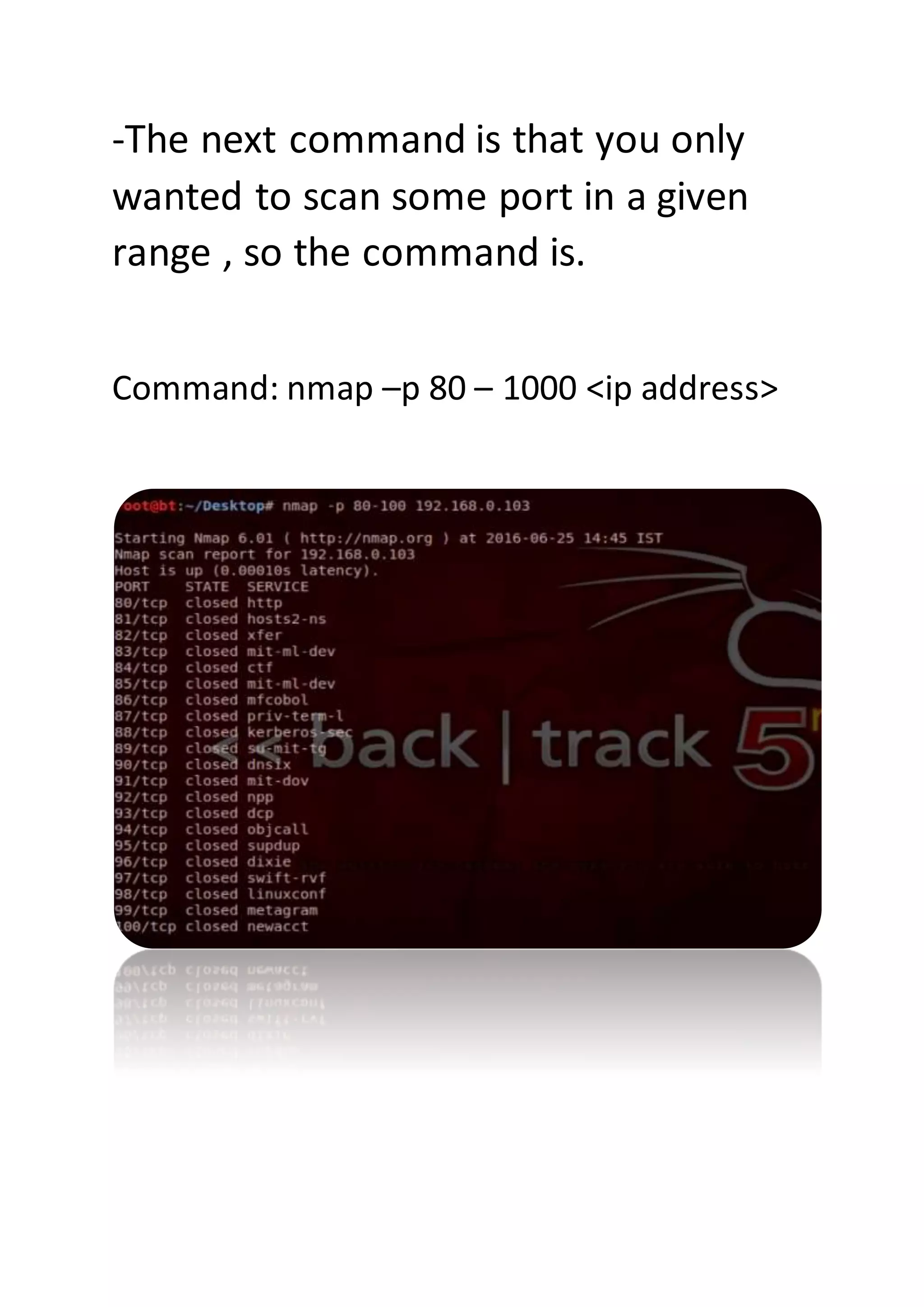
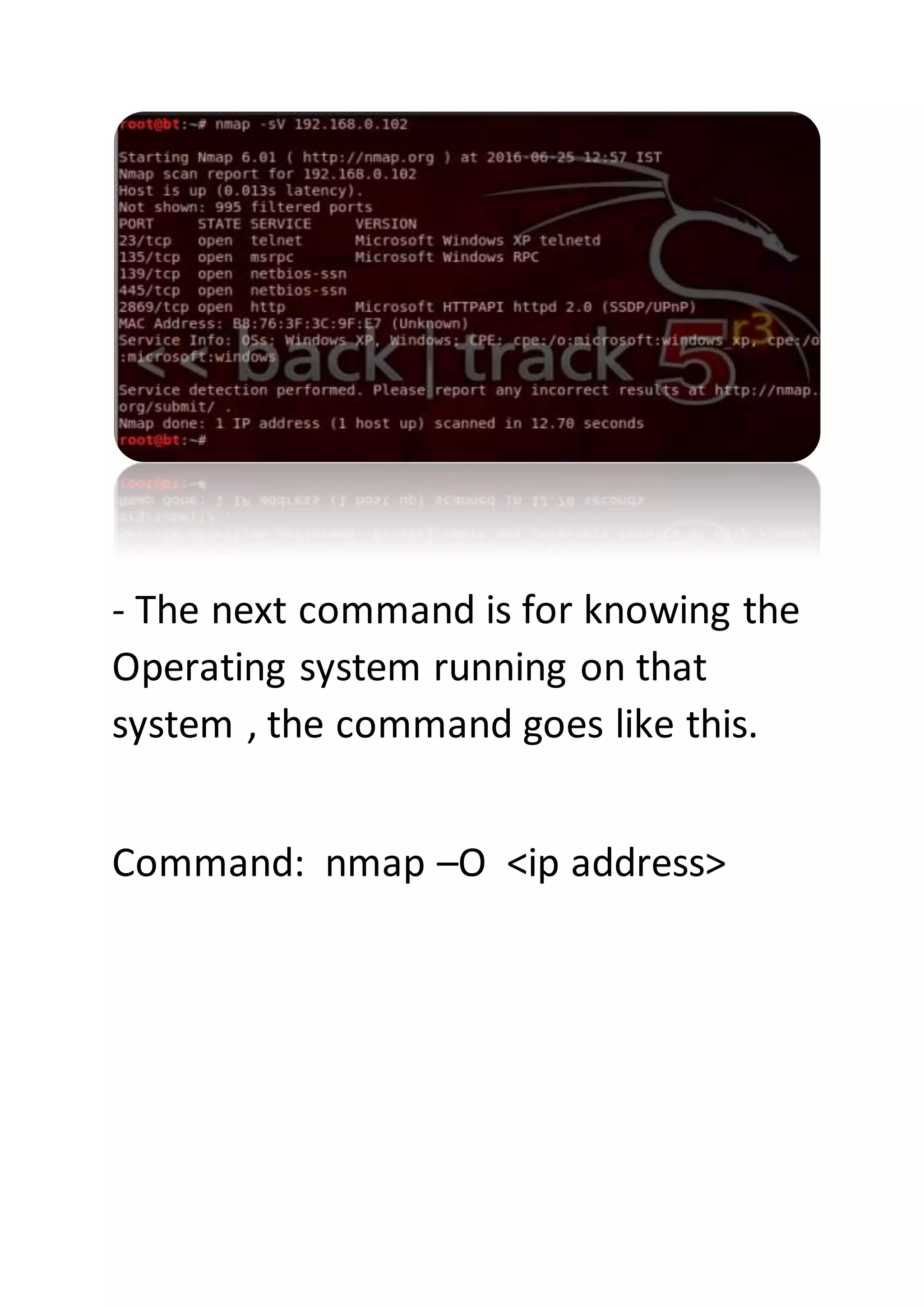
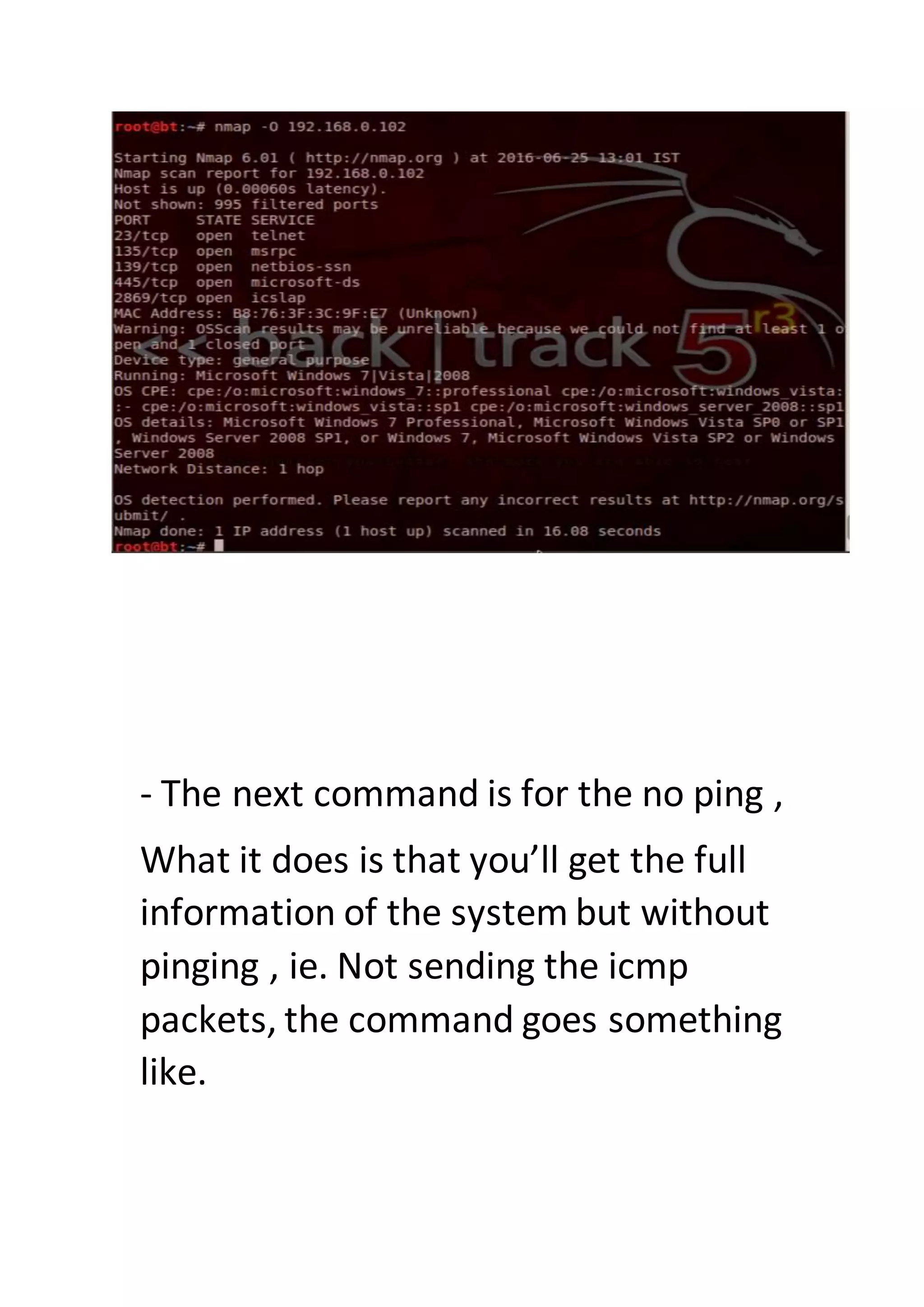
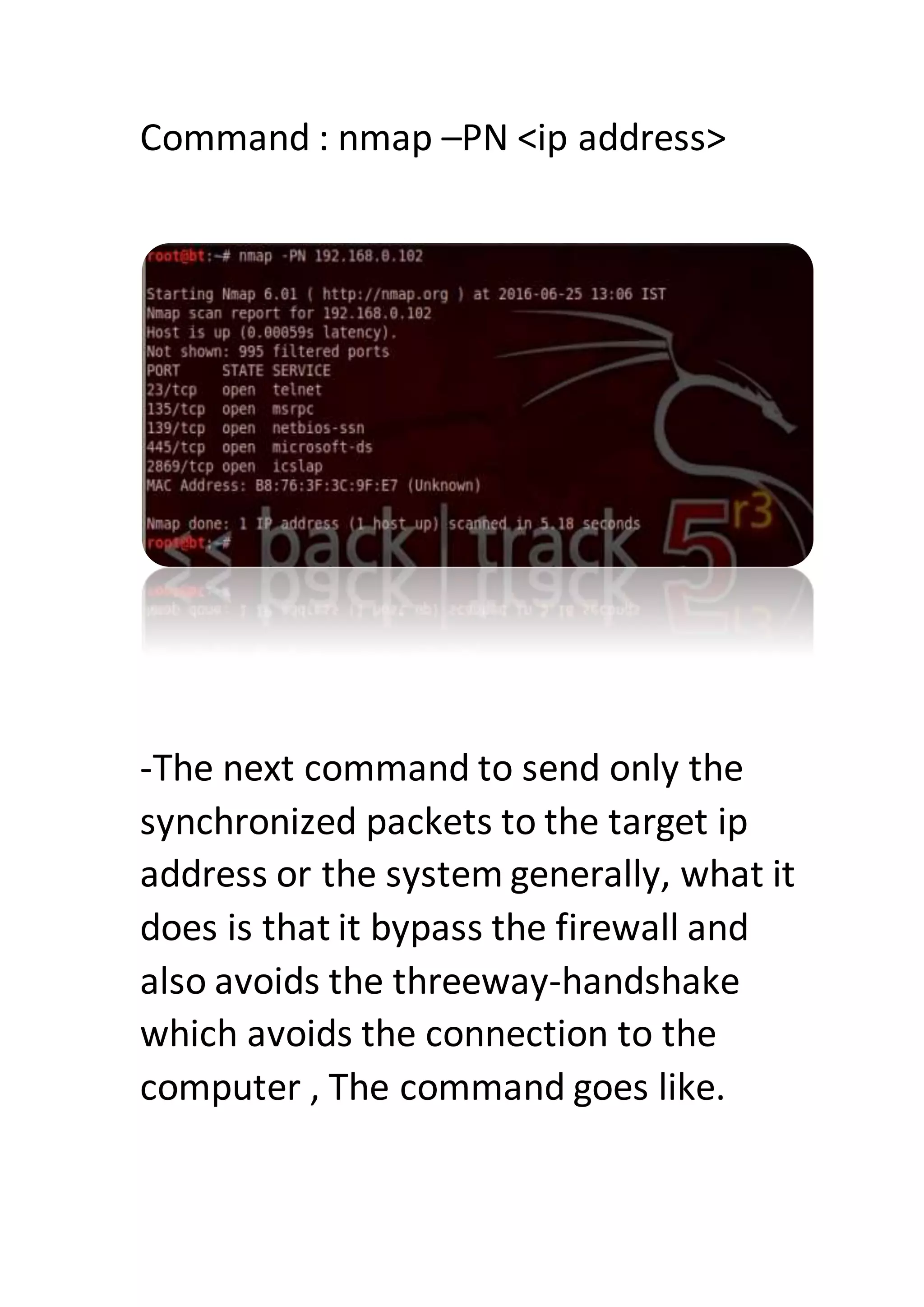
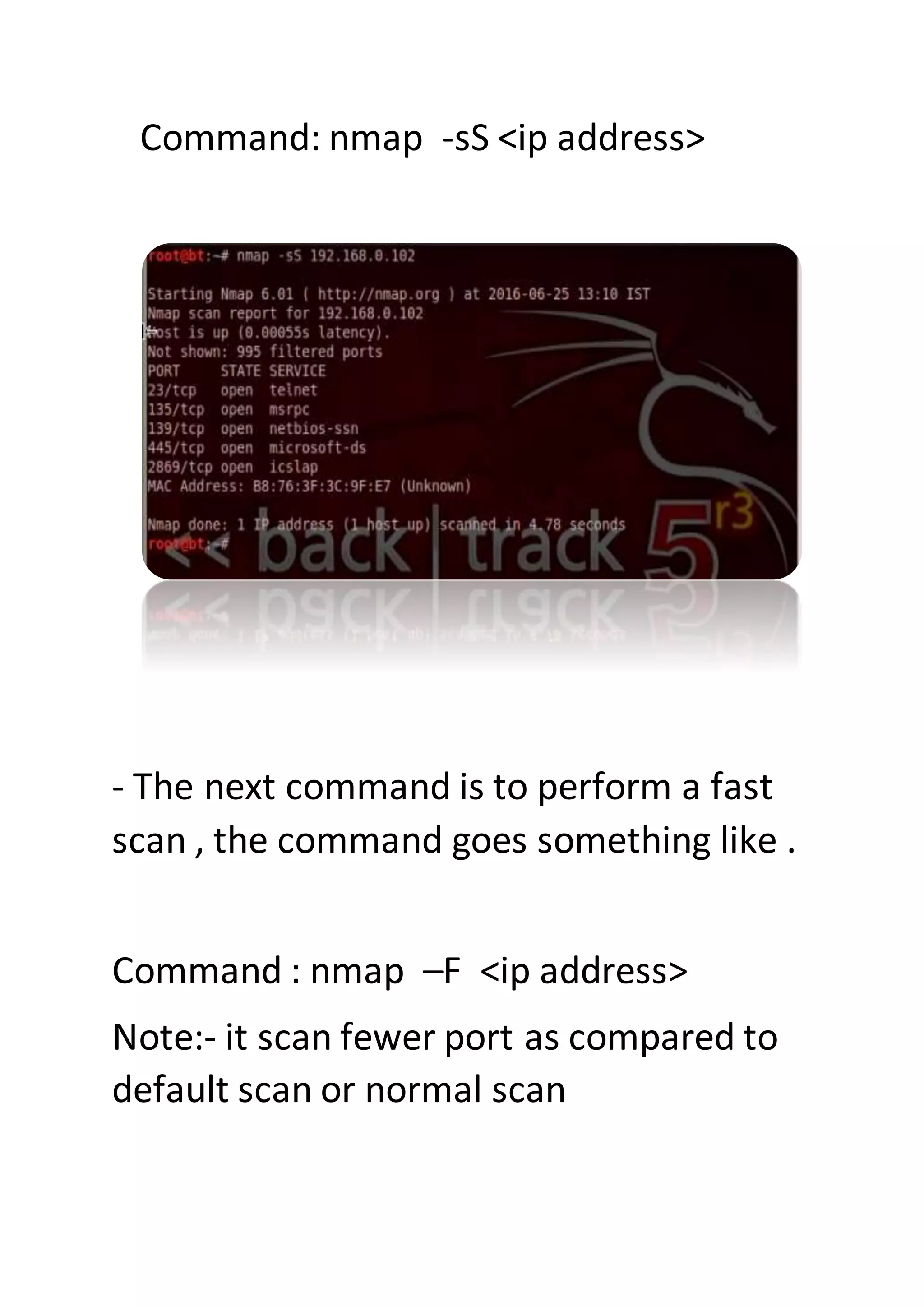
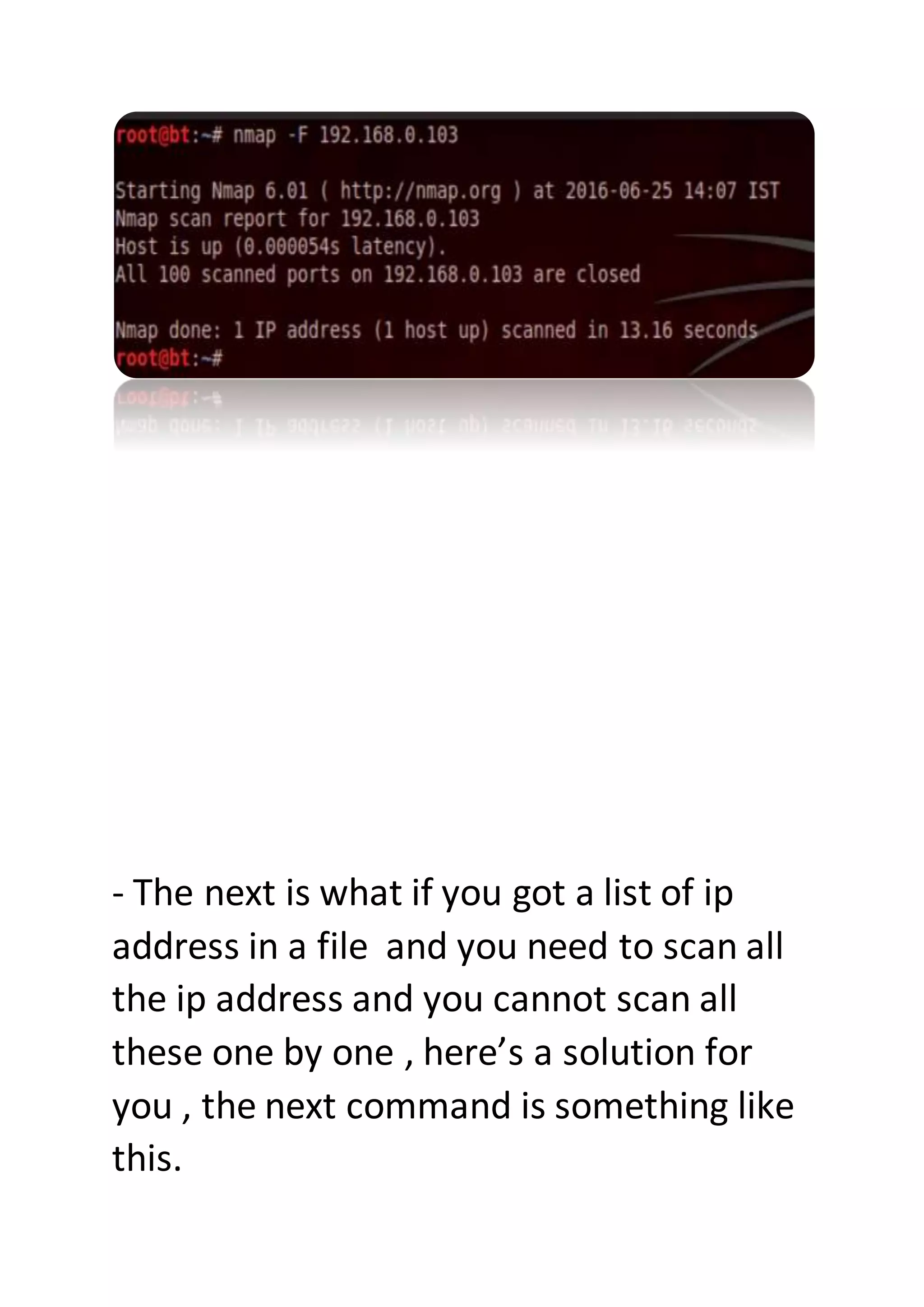
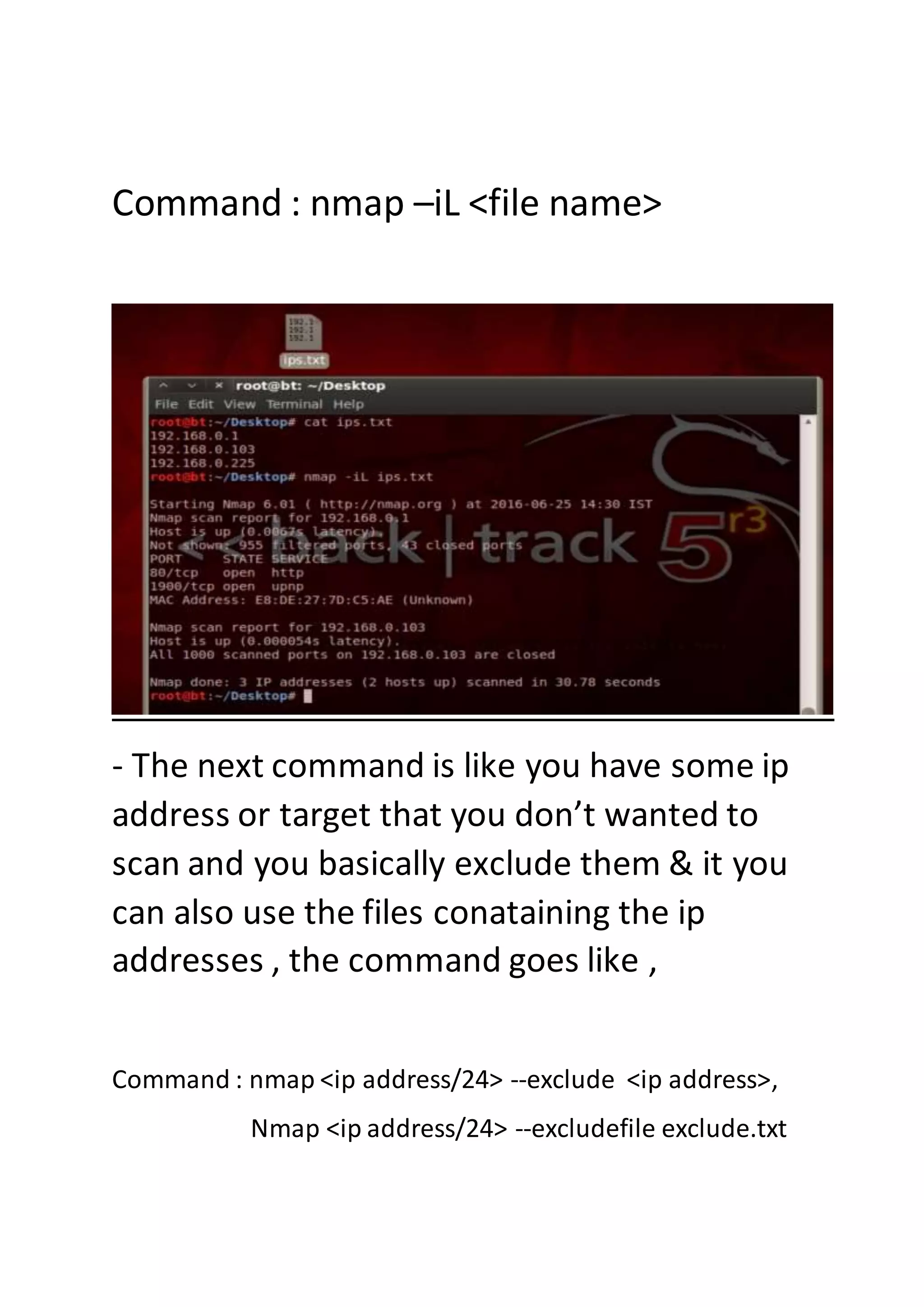
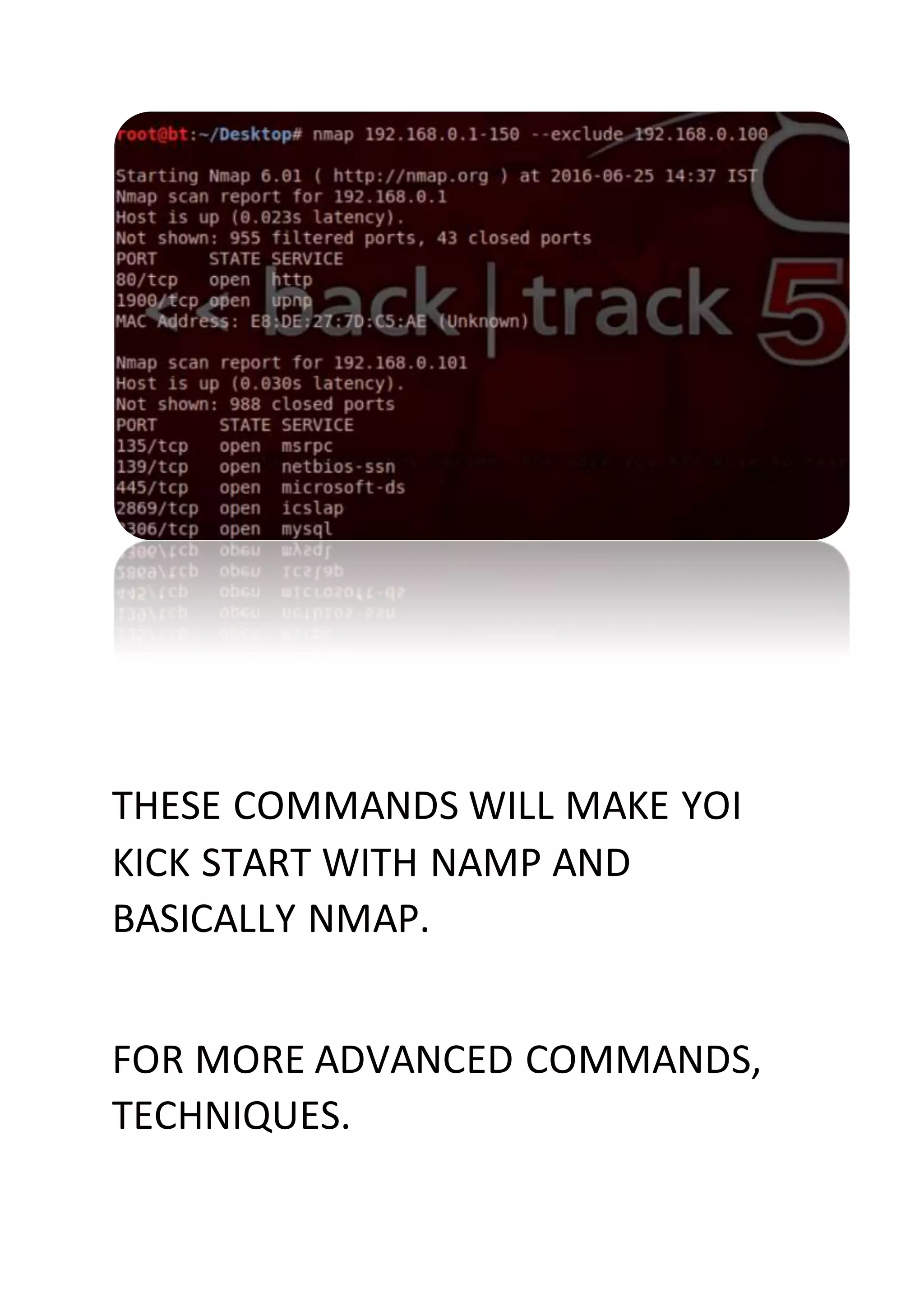
Nmap is a sophisticated network mapping tool used for scanning networks to identify online systems, their operating systems, open ports, and more. The document details various Nmap commands for different scanning purposes, including simple scans, port-specific scans, and options for scanning multiple IP addresses or subnets. Additionally, it offers insights on advanced scanning techniques and the use of both GUI and command-line interfaces.