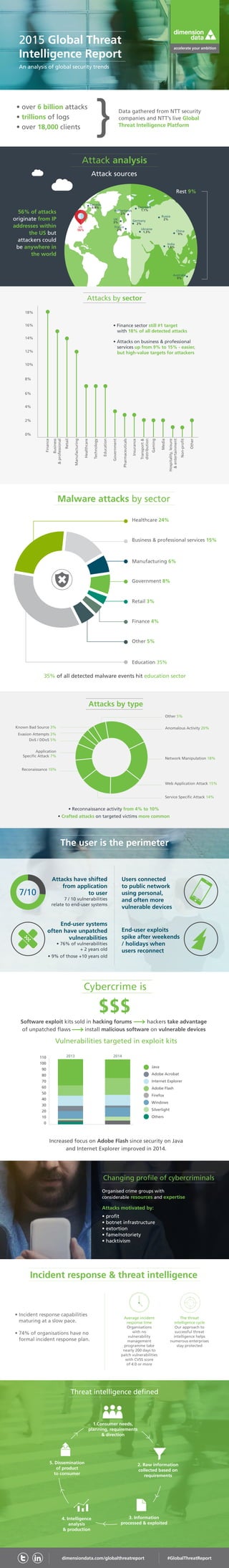
The 2015 Global Threat Intelligence Report reveals a significant rise in cyberattacks, with 56% originating from the U.S. and targeting various sectors, particularly finance and education. Most vulnerabilities are linked to end-user systems, often unpatched, with the majority of attacks occurring after weekends and holidays. Cybercriminals are increasingly organized, motivated by profit and notoriety, while incident response plans remain underdeveloped in many organizations.