Strengthening Cybersecurity at the tour de france
•
3 likes•2,138 views
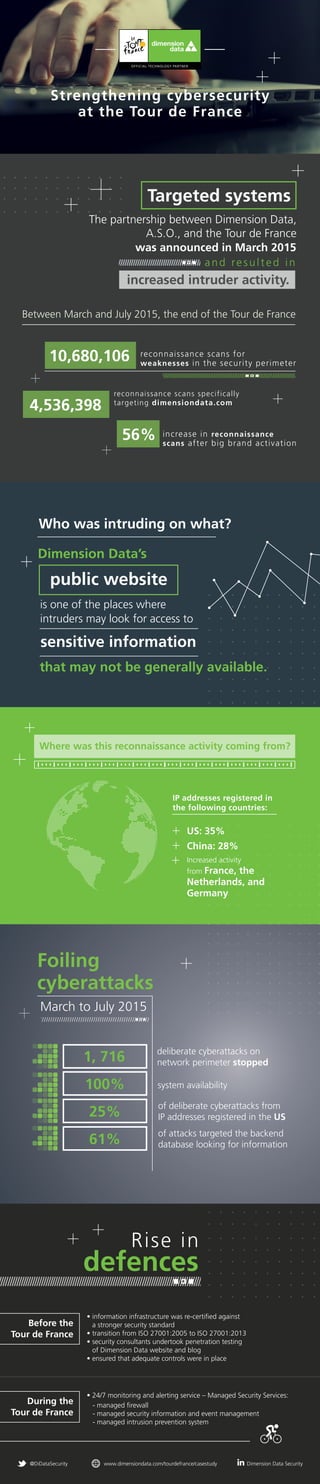
Here's a look at how we successfully thwarted all attempts to breach our perimeter, and intruder activity during the Tour de France. Between March and July 2015, we saw a 56% increase in reconnaissance scans targeting Dimension Data's website - none were successful.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
What's hot
What's hot (18)
Perspectives on Big Data & Analytics-(Doug Wolfe, CIA)

Perspectives on Big Data & Analytics-(Doug Wolfe, CIA)
MITRE ATT&CKcon 2.0: ATT&CK Updates - Cyber Analytics Repository (CAR); Ivan ...

MITRE ATT&CKcon 2.0: ATT&CK Updates - Cyber Analytics Repository (CAR); Ivan ...
2018 GIS in the Rockies Vendor Showcase (Th): Solving Real World Issues With ...

2018 GIS in the Rockies Vendor Showcase (Th): Solving Real World Issues With ...
MITRE ATT&CKcon 2.0: ATT&CK Updates - TRAM; Jackie Lasky and Sarah Yoder, MITRE

MITRE ATT&CKcon 2.0: ATT&CK Updates - TRAM; Jackie Lasky and Sarah Yoder, MITRE
MITRE ATT&CKcon 2.0: ATT&CK Updates - Sightings; John Wunder, MITRE

MITRE ATT&CKcon 2.0: ATT&CK Updates - Sightings; John Wunder, MITRE
MITRE ATT&CKcon 2.0: ATT&CK Updates - Controls Mapping; Mike Long, MITRE

MITRE ATT&CKcon 2.0: ATT&CK Updates - Controls Mapping; Mike Long, MITRE
IoT Services and Solutions - Brochure by RapidValue

IoT Services and Solutions - Brochure by RapidValue
Similar to Strengthening Cybersecurity at the tour de france
Similar to Strengthening Cybersecurity at the tour de france (20)
2015 International Workshop on Innovation for Crisis Management ( #I4CM ) Pre...

2015 International Workshop on Innovation for Crisis Management ( #I4CM ) Pre...
Federal Webinar: Leverage IT Operations Monitoring and Log Data to Reduce Ins...

Federal Webinar: Leverage IT Operations Monitoring and Log Data to Reduce Ins...
2014 BYOD and Mobile Security Survey Preliminary Results

2014 BYOD and Mobile Security Survey Preliminary Results
2015 Global Threat Intelligence Report - an analysis of global security trends

2015 Global Threat Intelligence Report - an analysis of global security trends
Ntxissacsc5 gold 4 beyond detection and prevension remediation

Ntxissacsc5 gold 4 beyond detection and prevension remediation
Future Watch: Cybersecurity market in South Africa 

Future Watch: Cybersecurity market in South Africa
Cyber Hacking in Healthcare & The Best Practices for Securing ePHI in 2015

Cyber Hacking in Healthcare & The Best Practices for Securing ePHI in 2015
Creating cyber forensic readiness in your organisation

Creating cyber forensic readiness in your organisation
06 - VMUGIT - Lecce 2018 - Rodolfo Rotondo, VMware

06 - VMUGIT - Lecce 2018 - Rodolfo Rotondo, VMware
Resume: The Complete Guide to Cybersecurity Risks and Controls

Resume: The Complete Guide to Cybersecurity Risks and Controls
{d1a164b5-f3a5-4840-96b1-16dd83ccdda9}_Wells_Fargo_GIB_Cyber_security_100615_...

{d1a164b5-f3a5-4840-96b1-16dd83ccdda9}_Wells_Fargo_GIB_Cyber_security_100615_...
Using international standards to improve EU cyber security

Using international standards to improve EU cyber security
Final presentation january iia cybersecurity securing your 2016 audit plan

Final presentation january iia cybersecurity securing your 2016 audit plan
Final presentation january iia cybersecurity securing your 2016 audit plan

Final presentation january iia cybersecurity securing your 2016 audit plan
More from DImension Data
More from DImension Data (20)
End-User Computing Insights: A study of digital maturity

End-User Computing Insights: A study of digital maturity
Creating workspaces for tomorrow at the greatest cycling event in the world

Creating workspaces for tomorrow at the greatest cycling event in the world
High-performance solutions for an international university

High-performance solutions for an international university
How we helped Fujifilm keep its customers' special memories safe

How we helped Fujifilm keep its customers' special memories safe
Dimension Data Department Prime Minister and cabinet G20 case study

Dimension Data Department Prime Minister and cabinet G20 case study
2015 Global Contact Centre Benchmarking Report key findings

2015 Global Contact Centre Benchmarking Report key findings
Dimension Data has been recognised as one of only 5 Top Global Top Employers

Dimension Data has been recognised as one of only 5 Top Global Top Employers
Recently uploaded
Hot Sexy call girls in Panjabi Bagh 🔝 9953056974 🔝 Delhi escort Service

Hot Sexy call girls in Panjabi Bagh 🔝 9953056974 🔝 Delhi escort Service9953056974 Low Rate Call Girls In Saket, Delhi NCR
Recently uploaded (20)
Streamlining Python Development: A Guide to a Modern Project Setup

Streamlining Python Development: A Guide to a Modern Project Setup
"Subclassing and Composition – A Pythonic Tour of Trade-Offs", Hynek Schlawack

"Subclassing and Composition – A Pythonic Tour of Trade-Offs", Hynek Schlawack
"Debugging python applications inside k8s environment", Andrii Soldatenko

"Debugging python applications inside k8s environment", Andrii Soldatenko
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
Powerpoint exploring the locations used in television show Time Clash

Powerpoint exploring the locations used in television show Time Clash
DevEX - reference for building teams, processes, and platforms

DevEX - reference for building teams, processes, and platforms
Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics

Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics
Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)

Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)
My INSURER PTE LTD - Insurtech Innovation Award 2024

My INSURER PTE LTD - Insurtech Innovation Award 2024
"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...

"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...
Gen AI in Business - Global Trends Report 2024.pdf

Gen AI in Business - Global Trends Report 2024.pdf
SQL Database Design For Developers at php[tek] 2024![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
SQL Database Design For Developers at php[tek] 2024
Hot Sexy call girls in Panjabi Bagh 🔝 9953056974 🔝 Delhi escort Service

Hot Sexy call girls in Panjabi Bagh 🔝 9953056974 🔝 Delhi escort Service
Strengthening Cybersecurity at the tour de france
- 1. Strengthening cybersecurity at the Tour de France The partnership between Dimension Data, A.S.O., and the Tour de France was announced in March 2015 Targeted systems and resulted in increased intruder activity. reconnaissance scans for weaknesses in the security perimeter reconnaissance scans specifically targeting dimensiondata.com increase in reconnaissance scans after big brand activation 4,536,398 56% 10,680,106 is one of the places where intruders may look for access to public website sensitive information that may not be generally available. Dimension Data’s Who was intruding on what? Rise in defences Before the Tour de France During the Tour de France • information infrastructure was re-certified against a stronger security standard • transition from ISO 27001:2005 to ISO 27001:2013 • security consultants undertook penetration testing of Dimension Data website and blog • ensured that adequate controls were in place • 24/7 monitoring and alerting service – Managed Security Services: - managed firewall - managed security information and event management - managed intrusion prevention system China: 28% US: 35% Where was this reconnaissance activity coming from? IP addresses registered in the following countries: Between March and July 2015, the end of the Tour de France @DiDataSecurity www.dimensiondata.com/tourdefrance/casestudy Dimension Data Security Foiling cyberattacks March to July 2015 1, 716 deliberate cyberattacks on network perimeter stopped 100% system availability 25% of deliberate cyberattacks from IP addresses registered in the US 61% of attacks targeted the backend database looking for information China: 28%China: 28%China: 28% Increased activity from France, the Netherlands, and Germany
